Ransomware takes the cake as the most prevalent type of malicious software in Verizon's latest Data Breach Investigations Report (DBIR).
The US-based telecommunications company analyzed input from 67 organizations and examined more than 53,000 security incidents, including 2,200-odd data breaches, in 65 countries between November 2016 and October 2017.
Compared to the previous 12 months, ransomware attacks doubled – so much so that they accounted for 39% of all malware-specific security breaches. Ransomware has been experiencing a meteoric rise in recent years, having come in 22nd from among all malware-related cases in the 2014 report.
What has made this variety of malware so popular among cybercriminals? Put simply, ransomware provides attackers with an unrivaled combination of little risk or cost and a high level of effectiveness. Off-the-shelf toolkits are easy to come by, and little to no technical skills are required to deploy ransomware.
Another reason why ransomware has become a high-reward, low-risk proposition is that there’s no need to monetize stolen data. Making things even worse for the victims, attackers are increasingly setting their sights on encrypting lucrative, business-critical targets such as file servers or databases, rather than “only” user devices. That way, they can extort the victims for more money, according to Verizon.
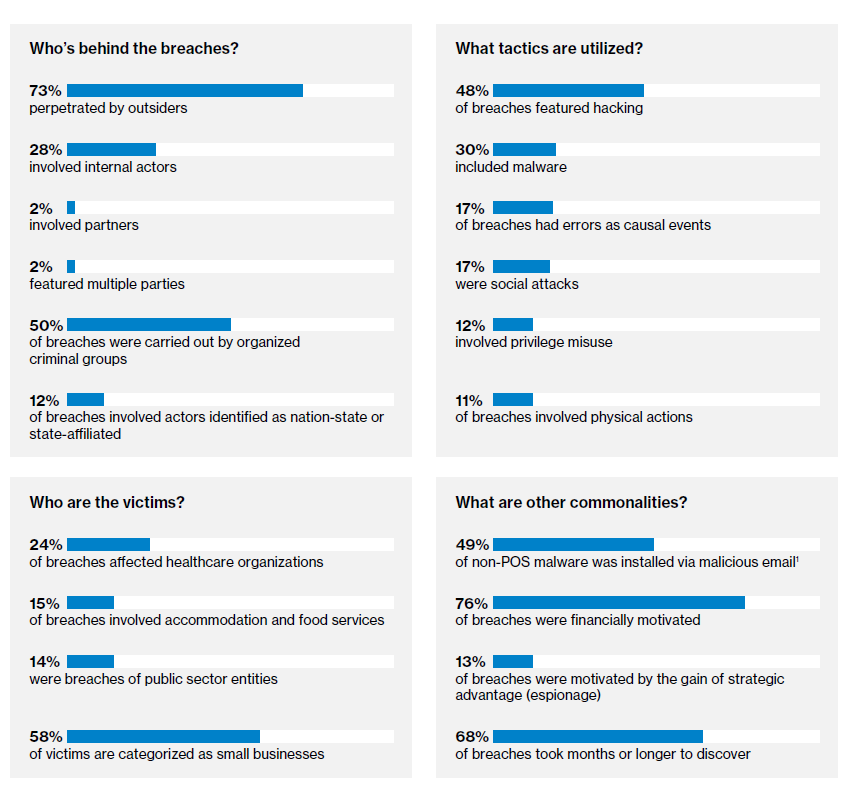
Meanwhile, it was hacking – such as through the use of stolen credentials – that was the leading method for facilitating a breach (48%). Malware in general was instrumental in 30% of breaches. Locked in a neck-to-neck race, errors and social engineering attacks (17% each) came next. Some incursions involve overlaps of attack paths.
When all kinds of security incidents are considered, i.e. events that compromise the integrity, confidentiality or availability of an information asset in some way, Verizon found denial-of-service (DoS) attacks to be the most common by far.
Who and why?
Summary of findings (credit: Verizon’s 2018 DBIR report)
Almost three-quarters (73%) of breaches were perpetrated by outsiders, while more than one in four (28%) involved insiders in some capacity. The healthcare industry was the odd man out in this respect, as the threat there is greater from inside than from outside (56% vs 43%). This involves a rather large amount of employee error and misuse of access privileges. Health care had another dubious distinction, since it was the most frequent victim of a breach (24%) from among all nine industries under review.
Financial gain remains by far the biggest motivation for intruders, having been identified behind 76% of breaches. Espionage came a distant second (13%). Verizon notes that most attacks are opportunistic and target the unprepared, rather than aiming at billion-dollar enterprises. Nearly six in ten victims are classified as small businesses.
People are people
A typical organization was found to be almost three times more likely to suffer a breach via a social engineering-based attack than via a software vulnerability. This supports a common refrain that, besides being the greatest asset of any organization, humans are also its weakest link.
Taken together, phishing and pretexting accounted for 93% of breaches that involved social engineering tactics. There was a notable increase in the prevalence of pretexting incidents in particular, with their number soaring from 61 to 170 on an annual basis.
To be sure, it’s not always easy to draw a line between phishing and pretexting, and they’re not necessarily mutually exclusive. For the purposes of the report, however, Verizon notes that pretexting usually involves some back-and-forth communication, beginning with a false narrative that is designed to acquire information or influence behavior. Malware isn’t usually deployed.
Meanwhile, phishing is more of a “fire and forget” approach and it involved malware in two out of three incidents. Either way, email was the usual attack vector, and finance and HR departments were the most common targets.
In addition, the telecom giant included some interesting data from contributing organizations that specialize in security awareness training. Phishing simulations run by the organizations found that 78% of employees didn’t click a single phish all year. On the flip side, on average 4% of people in any given phishing campaign will fall for such an email, and “the vampire only needs one person to let them in”, Verizon notes. Notably, the more phishing emails someone has clicked, the more they are likely to click again in the future.






