“A third of the internet is under attack.”
This blunt and sobering statement comes from a team of researchers who recently explored the threat landscape populated by denial-of-service (DoS) attacks worldwide. What they report finding is nothing short of, to use their own words, “an eye-opening statistic”.
However, before we dig our forks into the meat of their research summed up in a paper [PDF] called “Millions of Targets Under Attack: a Macroscopic Characterization of the DoS Ecosystem”, a quick explanation of DoS attacks, as well as their highly-amplified big brother, distributed denial-of-service (DDoS) attacks, is in order.
Both of these kinds of attacks are most commonly effected by inundating the target with a barrage of bogus traffic, ultimately with an eye to bringing it down and denying access to the service for legitimate users. Simple DoS attacks, which are a one-on-one affair, have been all but supplanted by DDoS attacks. The latter involve concerted campaigns from armies of devices conscripted into botnets which, as if lined up and marching in lockstep, aim to knock the unlucky target offline.
In a nod to the magnitude of the problem that DDoS attacks represent for internet stability and reliability, the six-strong team of researchers carried out a longitudinal analysis of the DDoS ecosystem “by introducing and applying a new framework to enable a macroscopic characterization of attacks, attack targets, and mitigation behaviors”. The findings of their research, which draws on data covering the period from March 2015 to February 2017, were unveiled at the Internet Measurement Conference in London earlier this month.
“One-third of all /24 networks recently estimated to be active on the internet have suffered at least one denial-of-service (DoS) attack over the last two years,” reads the number-one takeaway from the study conducted by researchers from University of Twente, the Netherlands; University of California, San Diego; and Saarland University in Germany. The suffix ‘/24’, or ‘slash 24’, indicates the number of fixed bits in a network ID.
Figures
After dissecting the two years’ worth of data, the study’s authors counted 20.9 million attacks targeting 6.34 million unique IP addresses. They observed a total of 2.19 million unique /24 network blocks that host at least one target. To put that into perspective, this makes up to just over a third of recent estimates of the actively used IPv4 address space. IPv4 is the fourth (and still prevalent) version of the Internet Protocol that enables users to connect their devices to the internet.
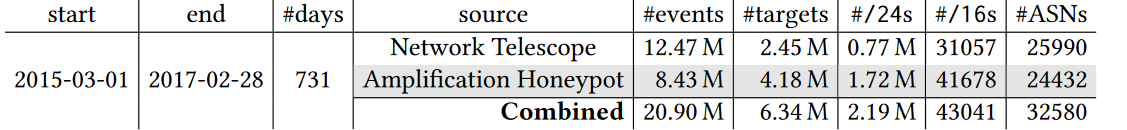
Table 1: DoS attack data from the study
Across this two year span, a daily average of nearly 30,000 attacks were observed, which one of the study’s authors, Alberto Dainotti, described as “staggering, a thousand times bigger than other reports have shown”.
And yet, fellow co-author Anna Sperotto voiced concern that this still may not paint the full picture. “Although our study employs state-of-the-art monitoring techniques, we already know we do not see some types of DoS attacks,” she is quoted as saying.
To detect attack events, the team delved into two mutually complementing raw data sources – the UCSD Network Telescope, which captures evidence of DDoS attacks involving randomly and uniformly spoofed IP addresses; and the AmpPot DDoS honeypots that track reflection and amplification DDoS attacks, which involve specific, spoofed IP addresses. Assailants use IP spoofing to disguise their identities in cyberattacks.
Targets
As might have been expected, web servers were found to be the prime targets. “[M]ost DoS attacks (e.g., about 69% for TCP-based attacks) targeted Web servers,” reads the study.
An average of 3% of web sites ending in .com, .net, and .org, were victims of attacks daily due to their being hosted on targeted IP addresses.
A number of “large parties”, including organizations providing web hosting services, were identified as frequent targets, most notably GoDaddy, Google Cloud and Wix.
Meanwhile, the by-country target ranking is largely consistent with internet address usage patterns, albeit with some notable exceptions. Using the Telescope data, the US was found to be home to over 25 percent of the targeted IP addresses. For reflection attacks, the share climbs to 29 percent, with both figures roughly on a par with the country’s address space usage. China comes second on around 10 percent for both kinds of attacks, which is also commensurate with statistics of internet address space utilization.
By contrast, Japan, while being 3rd in the number of internet addresses, is placed 14th and 25th, respectively, in DoS target numbers. On the other hand, Russia and France endure more attacks than their estimated Internet space usage would predict.
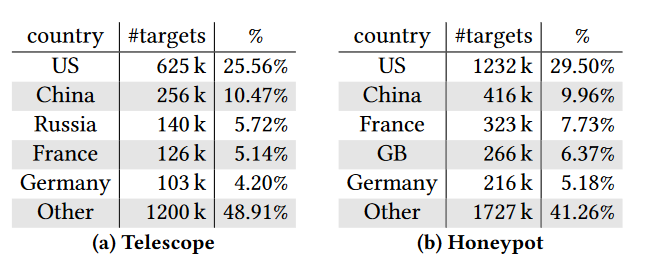
Table 2: Per-country breakdown of attacked IP addresses
Where do we go from here?
Looking beneath the surface, the researchers gave us a taste of the breadth and scale of the DoS problem, which clearly goes beyond the supremely crippling attacks that grab the headlines. The team also noted the increasing onslaughts spurred on by the rise of the DoS-as-a-Service phenomenon (aka “stressers” or “booters”), which enables any ill-intentioned netizen to orchestrate powerful attacks. The study clearly serves to highlight the need for staying ahead of the rising tide of threats emanating from DoS attacks.
The extent of damage that denial-of-service attacks may inflict courtesy of botnets was exemplified in October 2016, when a series of DDoS attacks were unleashed against systems operated by Domain Name System (DNS) provider Dyn. The attack, which made a host of high-profile online services unavailable, was enabled by utilizing thousands of compromised, inconspicuous Internet-of-Things devices in a botnet called Mirai and should serve as a stark warning of harm that denial-of-service attacks can cause.
About Writer: Tomáš Foltýn is security writer for WeLiveSecurity.






