As many as 43% of online login attempts globally are made by bots that are used for evil ends, as attackers are increasingly leveraging the automated tools for credential abuse, a report by Akamai has revealed.
Focusing on data for November, 2017, the content delivery network provider found that 3.6 billion out of 8.3 billion login requests during that month were malicious, specifically “attempts to log in to an account using password guessing or account details gathered from elsewhere on the Internet”.
A breakdown of the figures shows that the websites of retailers handled the highest number of login requests in November – 2.8 billion. “Only” 36% of them were intended to break into the accounts, according to Akamai’s Fourth Quarter 2017 State of the Internet / Security Report.
Meanwhile, the hospitality industry had to contend with the highest concentration of bad bots. A staggering 82% of nearly 1 billion login attempts on the websites of airlines, hotels and online travel agencies were found to be malicious.
Swarms of villain bots also swooped on the sites of high-tech businesses, with 57% out of 1.4 billion login attempts deemed malevolent.
The data was obtained by Akamai’s identifying “IP addresses that make multiple attempts to log into accounts using leaked credentials with no other activity to the target site”.
The data set covers mainly websites that use email addresses as login names. As a result, Akamai cautioned that the figures may understate the extent of the problem in industries in which email addresses are not used as user IDs, notably the financial industry.
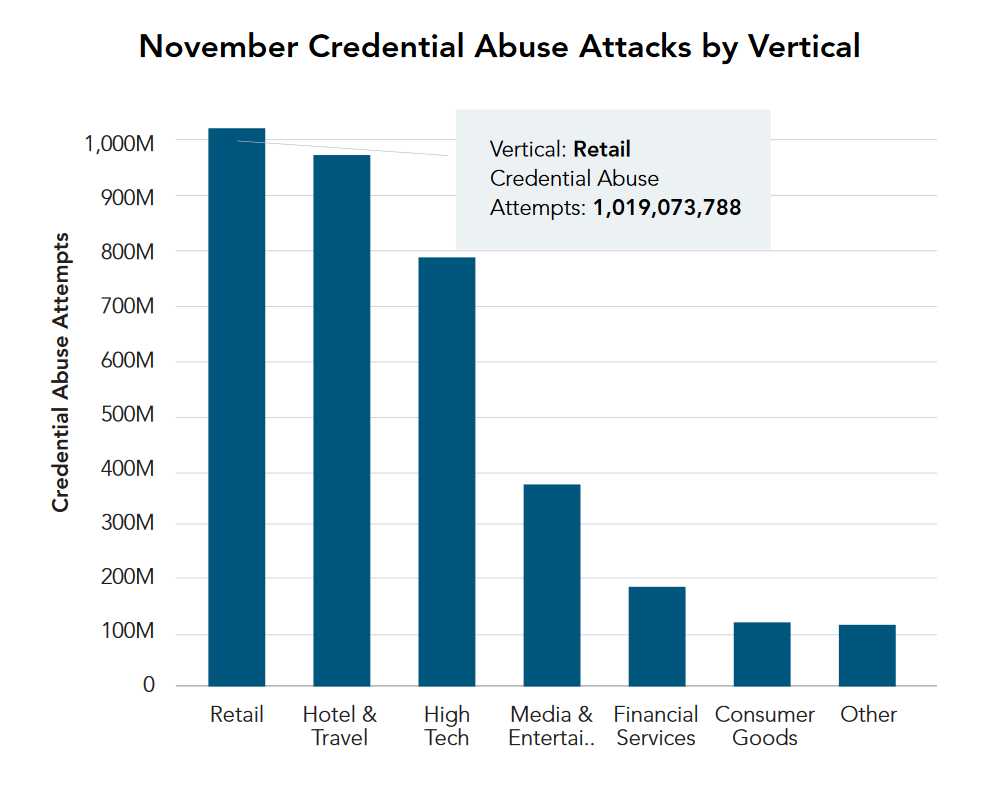
Credential abuse attempts according to selected industries (Source: Akamai, Fourth Quarter 2017 State of the Internet / Security Report)
Bots that traverse the internet on behalf of their human operators can fulfill both legitimate and malicious automated tasks. Statistics indicate that bot-driven internet traffic, by helper and harmful bots combined, surpasses human traffic.
"Increased automation and data mining have caused a massive flood of bot traffic to impact websites and Internet services. Although most of that traffic is useful for Internet businesses, cybercriminals are looking to manipulate the powerful volume of bots for nefarious gains," Akamai’s senior security advocate Martin McKeay is quoted as saying.
"Enterprises need to watch who is accessing their sites to differentiate actual humans from both legitimate and malicious bots. Not all web traffic and not all bots are created equal," he added.
In an automated technique known as ‘credential stuffing’, criminals leverage stolen or leaked access credentials that belong to one account in order to break into other – often higher-value – accounts. This tactic has been found to pay dividends in anywhere between 0.1% and 2% of attempts, owing its success primarily to the fact that many netizens recycle their credentials across multiple accounts. Databases with reams of stolen username and password pairs can be easily bought online.
DDoS traffic
After several quarters of increases, the number of distributed denial-of-service (DDoS) attacks dropped by less than 1% in the fourth quarter of 2017 compared to the third quarter. On an annual basis, however, the attacks were up 14%, according to Akamai’s stats.
The gaming industry bore the brunt of the onslaughts, suffering 79% of all DDoS traffic. Germany and China between themselves accounted for the majority of source IP addresses involved in the attacks.
To say that DDoS attacks aren’t going anywhere would be an understatement, nor have we seen the last of Mirai. The notorious botnet, which took the internet by storm in the fall of 2016, remains alive and kicking. This is not least because of the proliferation of hackable Internet-enabled things, coupled with attackers continuing to adapt Mirai’s source code to befit their evil intentions.
Web app attacks
The number of web application attacks decreased by 9% following a quarter-over-quarter jump of 30% in the third quarter. They still rose by one-tenth compared to the last three months of 2016, however.
This type of threat most commonly involves scans to identify vulnerable sites with the ultimate aim of data thefts or other compromises. SQL injections, which Akamai highlighted as “easily automated and scalable”, accounted for one-half of web app attacks. On 36%, local file inclusion was the second-most-frequent attack vector.
The United States is by far both the top source and top target of web app attacks. The incursions that originate in the US soared by 31% compared to the last quarter of 2016.





