We’ve been talking about election security for months now. With the current pre-election fever pitch in the U.S., there almost couldn’t be a stronger focus on getting it right; indeed, it could only be matched closely by the magnitude of interest from shady actors trying to make sure it doesn’t.
Officials are pulling out all the stops to deter threats, including via a Fed-sponsored $10 million bounty for information about individuals aiding election interference. That hefty amount hasn’t stopped hacking attempts, including from aspiring hackers. From accidents to low-level stunts, like changing the home address of the Florida Governor, to a tad more sophisticated attempts, here’s the current summary of how this election cycle is faring in the hands of the would-be digitally meddlesome.
First off, two tales that hit rather close to home, giving this all a touch of personal experience:
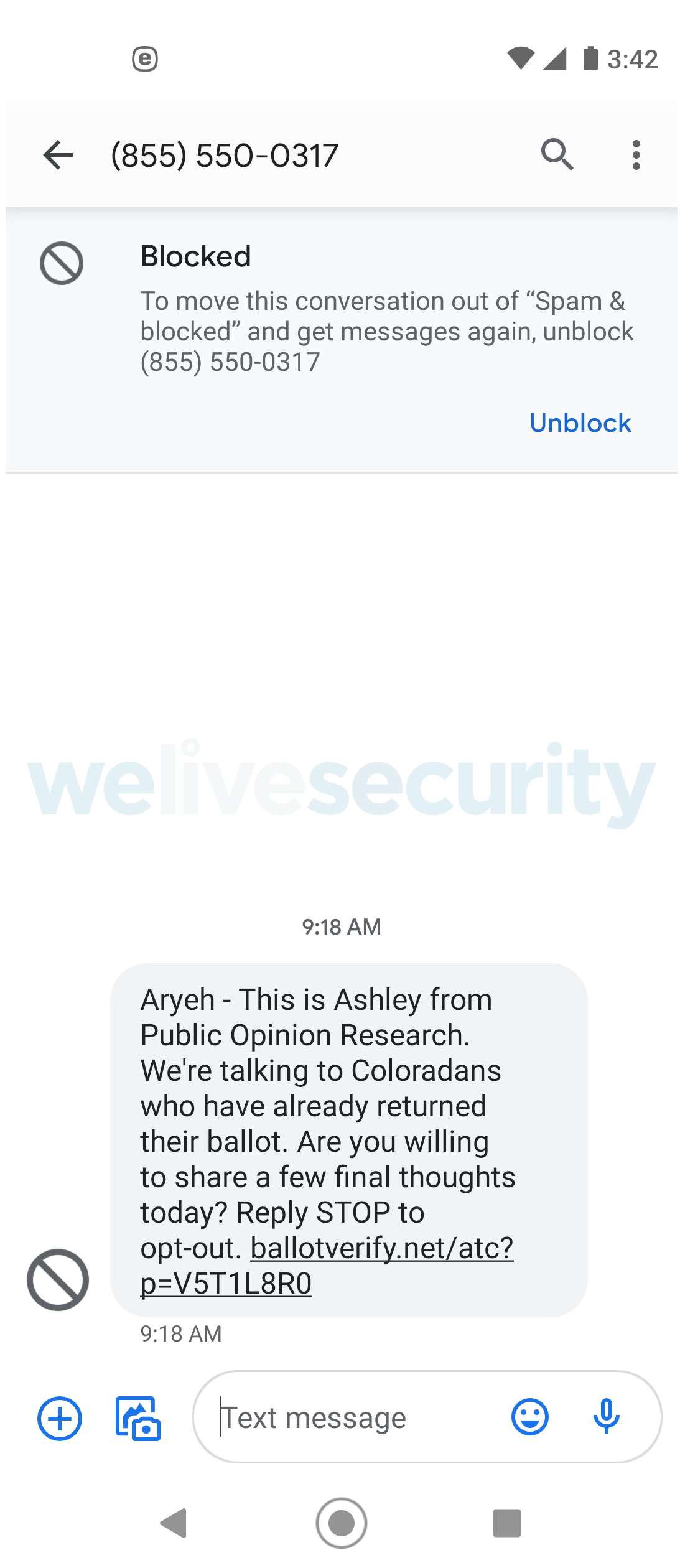
- On October 16th, less than 24 hours after submitting his ballot, ESET researcher Aryeh Goretsky received a scam text message from a non-existent company, Public Opinion Research, from a phone number that showed up as (855) 550-0317 using spoofed Caller ID. The domain mentioned in the message, ballotverify[.]net, was registered anonymously on the previous day, Thursday, October 15th, according to DomainTools. The web site is hosted at 52.72.49.79 along with over 32,000 others by Rebrandly, a link redirection service. The domain redirects to thevotersurvey[.]com, which was registered a year ago and is hosted on AWS infrastructure at 63.234.29.71 along with ten other domains, most of which contain words like “survey” or “study” in the domain name. This may be an attempt to impersonate ballottrax[.]net, a legitimate website used by county governments to confirm ballot receipt.
- My friend has received a mail-in ballot for her husband, who’s (sadly) been dead for three years now due to an illness. So there are still issues with mail-in ballots. During the last election cycle, I got two ballots in the mail in my name. I notified local election officials.
- In early October, a ransomware attack disrupted an election administration system in Hall County, Georgia. The attack took out the county’s online precinct map and a database that the county uses for verifying voter signatures on absentee ballots. As has been quite common recently, the extortionists also stole some documents before dumping a sample of them online in a bid to coerce the victim into paying up.
- In mid-October, an accidentally severed internet cable in Virginia took down the state’s website for online voter registration on what happened to be the last day for voters to register before Election Day. Everything was later back up and running, though, and the deadline was extended.
- At around the same time, the government of Chenango County, New York, suffered a ransomware attack that hit around one-half of its 400 computers, including those used by the board of elections. The incident caused potential issues with the processing of absentee ballot applications, but state officials gave assurances that voting shouldn’t be affected overall.
- Just days ago, a Florida man altered the home address of the Sunshine State’s governor Ron DeSantis in the voter registration database, preventing the governor from voting. The problem was fixed in short order and the perpetrator was charged with felony voter fraud.
- Also this week, it was reported that local election officials in several states have apparently been targeted by a wave of suspicious emails, at least some of which impersonated state elections directors and attempted to send the recipients to phishing sites.
- The FBI and CISA recently warned of campaigns that chain vulnerabilities in Windows and Virtual Private Network (VPN) services to target various government agencies, critical infrastructure and election organizations, including apparently to gain unauthorized access to elections support systems.
Indeed, the same two agencies recently put out another warning – that in order to “manipulate public opinion, sow discord, discredit the electoral process, and undermine confidence in U.S. democratic institutions”, threat actors will attempt to spread false information around hacked voter information.
This implies orchestrated efforts that often rely on social media bots acting as deliberate and serial purveyors of deception, spewing false narratives in coordinated fashion. Misleading claims can also gain traction in other ways; rumors – think the one about thousands of mail-in ballots allegedly discarded in a dumpster – can also spread like wildfires and ultimately undermine trust in the democratic process.
No matter what, next week a large chunk of the electorate will be celebrating, matched by a similarly-sized group working on a strong hangover. While we don’t have a specific recommendation for the latter, we hope this is just the start of teeing up serious and meaningful steps toward truly secure election cycles to come.
Stay tuned – chances are we haven’t seen the last of election shenanigans...





