The latest episode of this series marks the halfway point in the third season and, in addition to some amazing camerawork (the entire episode is shot in one impressive long take), several examples of actions related to IT security crop up, which we will cover in this article. And while this episode has been out for quite a while now, some readers may not have seen it yet, so if you are one of them, we recommend that you stop reading at this point and come back once you have seen it.
Warning: the following contains spoilers
A new week begins
The episode opens with Elliot making his way to his workstation like any other worker, while rambling to himself about the meaning of a “runtime error”, which is a message that pops up when you try to execute a program but it stops because of one or more lines of code prevent it from running correctly.
Elliot sits down at his cubicle and tries to log in to his computer, but something is amiss: his credentials won't let him access the system and Elliot suspects that someone has either unsuccessfully tried to login as him too many times, or has directly blocked his account.
At this point he turns to his colleague in the next cubicle to ask if he can use his computer/account to check something quickly, which brings us to the first point to consider in this episode. User accounts are mostly designed to be non-transferable, which means that user groups can be defined with different permissions and access rights. If someone uses another user's account with or without permission, it is usually the latter who has to deal with any culpability that this may entail, so it is generally not a good idea to freely give others your account credentials or access to your user sessions.
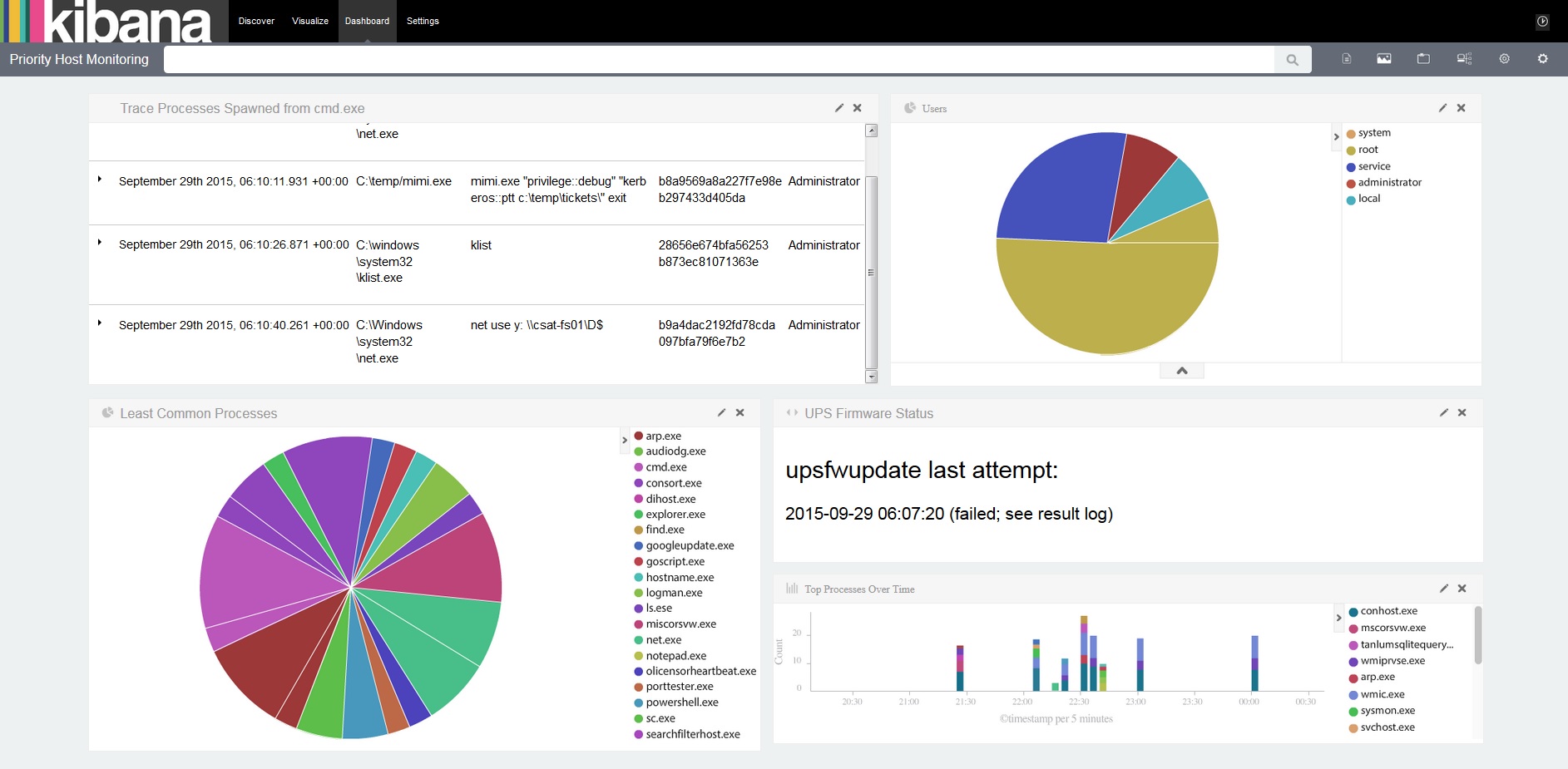
Once Elliot gets a valid user session, the first thing he does is check the status of the server used for monitoring the UPS power systems that he had dedicated so much care to in previous episodes. He does this by using Kibana. And, lo and behold, he discovers that someone had tried to update them with an unsigned modified firmware but thanks to the security policies he implemented, they had not been able to do so. Even so, it is just a matter of time until they get in using an alternative route, so he has to move fast.
On top of that, security staff are on the lookout for him in order to escort him to the door, which hinders his movements somewhat.
Elliot's escape
The situation becomes fraught at times, since Elliot deduces that the plan being hatched by the Dark Army is to physically access the hardware security modules (HSMs). This would allow them to create a firmware update that is signed in such a way that the security protocols implemented by Elliot would read it as valid, even though their intention is to cause the UPS to malfunction and, ultimately, cause a fire that would destroy the warehouses where E-Corp stores paper records for all data on its accounts and customers.
But unfortunately E-Corp's HSMs are located on the 23rd floor, which of course Elliot does not have access to. So he uses social engineering to access another machine that is not his by posing as an IT support technician, but the security team finally tracks him down and escorts him to the main door of the building. Incidentally, when Elliot tries out his social engineering skills on an elderly female employee (who he believes would be the perfect victim), he realizes that she has done her homework by adopting security measures above and beyond those recommended, so will not be such easy prey after all. Luckily for Elliot, though, she introduces him to a colleague who is an easy victim of his deceit.
After unsuccessfully eluding the security team, he is escorted out of the building, where he meets his sister, who informs him that she has been working with the FBI, all the while surrounded by demonstrators protesting outside the main entrance of E-Corp. At this point things really start to heat up and some of the protesters attack the security forces and enter the building, which triggers the next phase.
Angela and her vital role in accessing the HSMs
Apparently this vandalism is part of a plan hatched by the Dark Army to gain access to the HSMs and have enough time to get hold of the cryptographic keys that will allow them to run a valid install of a malicious firmware update. However, all is not as simple as it seems because in addition to gaining access to the room where the HSMs are located, a meticulous process must be followed, and any attempt to access this information by force could result in it being instantly deleted.
Initially, the plan was for Angela to contact Mr. Robot, Elliot's alter ego, and get him to get hold of the crypto keys. However, she is unable to contact him, so Angela decides to do it herself following instructions she receives in a package left at reception in her name.
After several incidents, Angela manages to gain access to the room where the HSMs are located and follows the step-by-step instructions, which were originally intended for Elliot. Apparently everything goes according to plan and Angela manages to make a copy of the crypto keys, so she then calls Irving to tell him that she has taken care of everything already and asks for new instructions.
The only instruction Irving gives her is to deliver the information she obtained to a contact who is waiting for her at the reception on her floor, which she does, and in exchange is given a mysterious bag whose contents are concealed.
Easter eggs
This episode has quite a few Easter eggs and some of them are especially interesting, so we are going to run through them below. To start with, we went to the well-known site https://www.whoismrrobot.com/ where we saw that a new folder called "Protest" had appeared on the Origin portal. This folder contains images of some of the banners carried by protesters outside the E-Corp building.
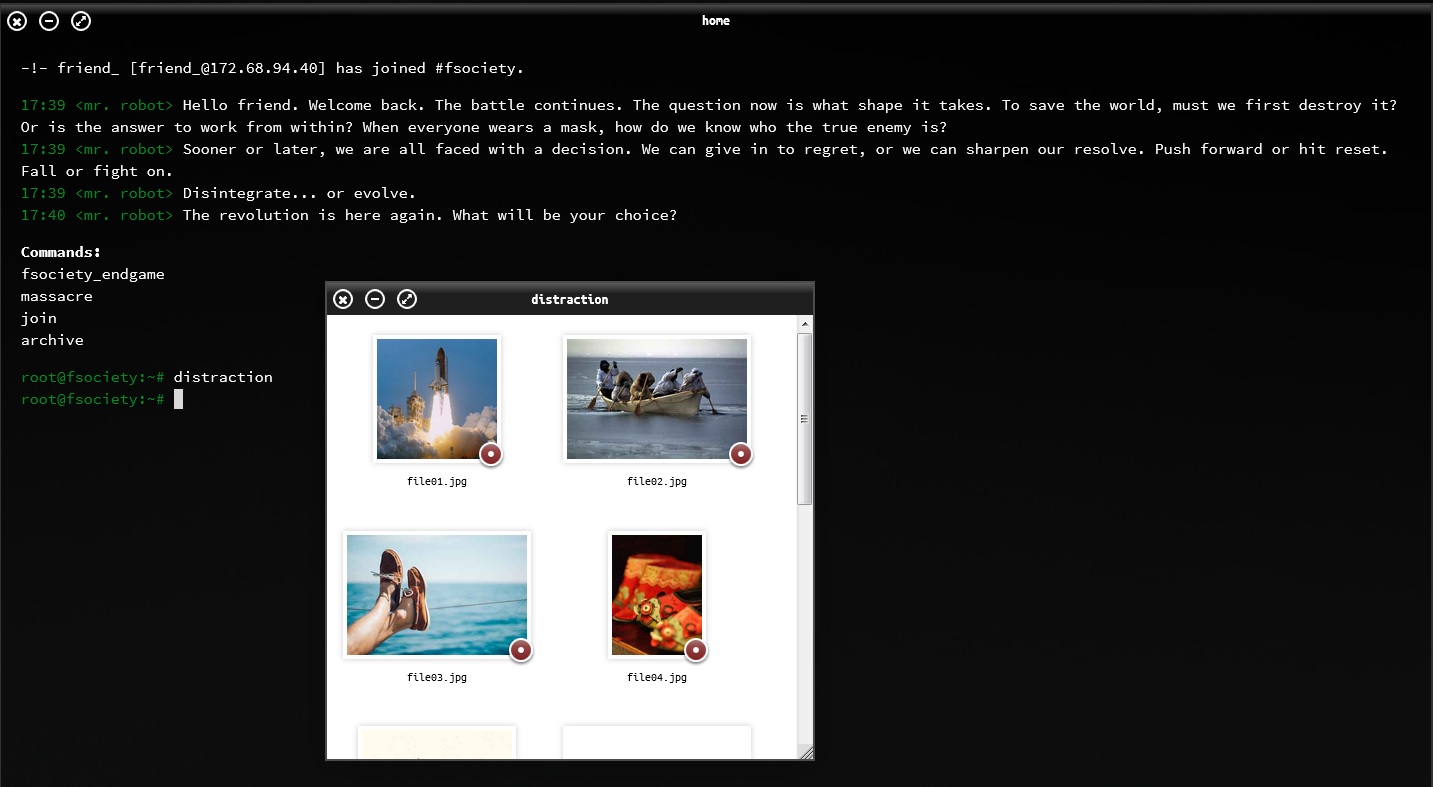
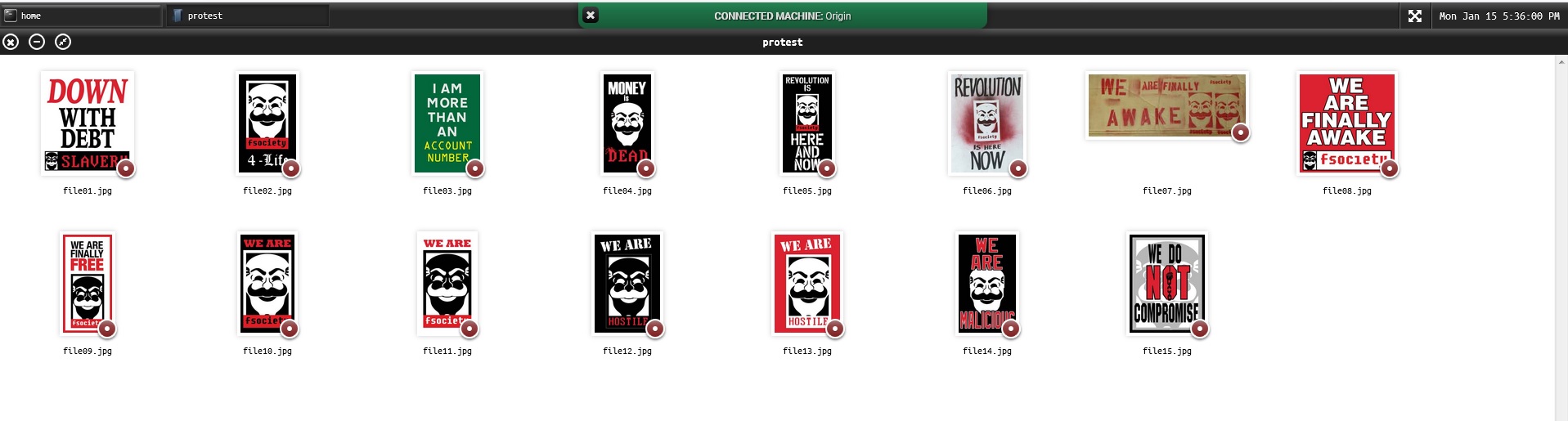 The day after the episode aired, several users registered on the mailing list received similar images but with something extra. Analyzing these images we could see how they concealed what appears to be a message, and we then deciphered this as “Distraction”, which is very likely referring to the demonstration being a distraction maneuver organized by the Dark Army to gain access to E-Corp's offices and steal the encryption keys off the HSM.
The day after the episode aired, several users registered on the mailing list received similar images but with something extra. Analyzing these images we could see how they concealed what appears to be a message, and we then deciphered this as “Distraction”, which is very likely referring to the demonstration being a distraction maneuver organized by the Dark Army to gain access to E-Corp's offices and steal the encryption keys off the HSM.
Furthermore, when we typed the word "distraction" into the console window that opens when you enter the Origin portal on the site https://www.whoismrrobot.com/ a new folder opened with images of shoes, boats and the space shuttle Challenger. Will these images mean something? According to some Reddit users, everything seems to indicate that they are stock images with no hidden information, but then again, anything is possible in this series.
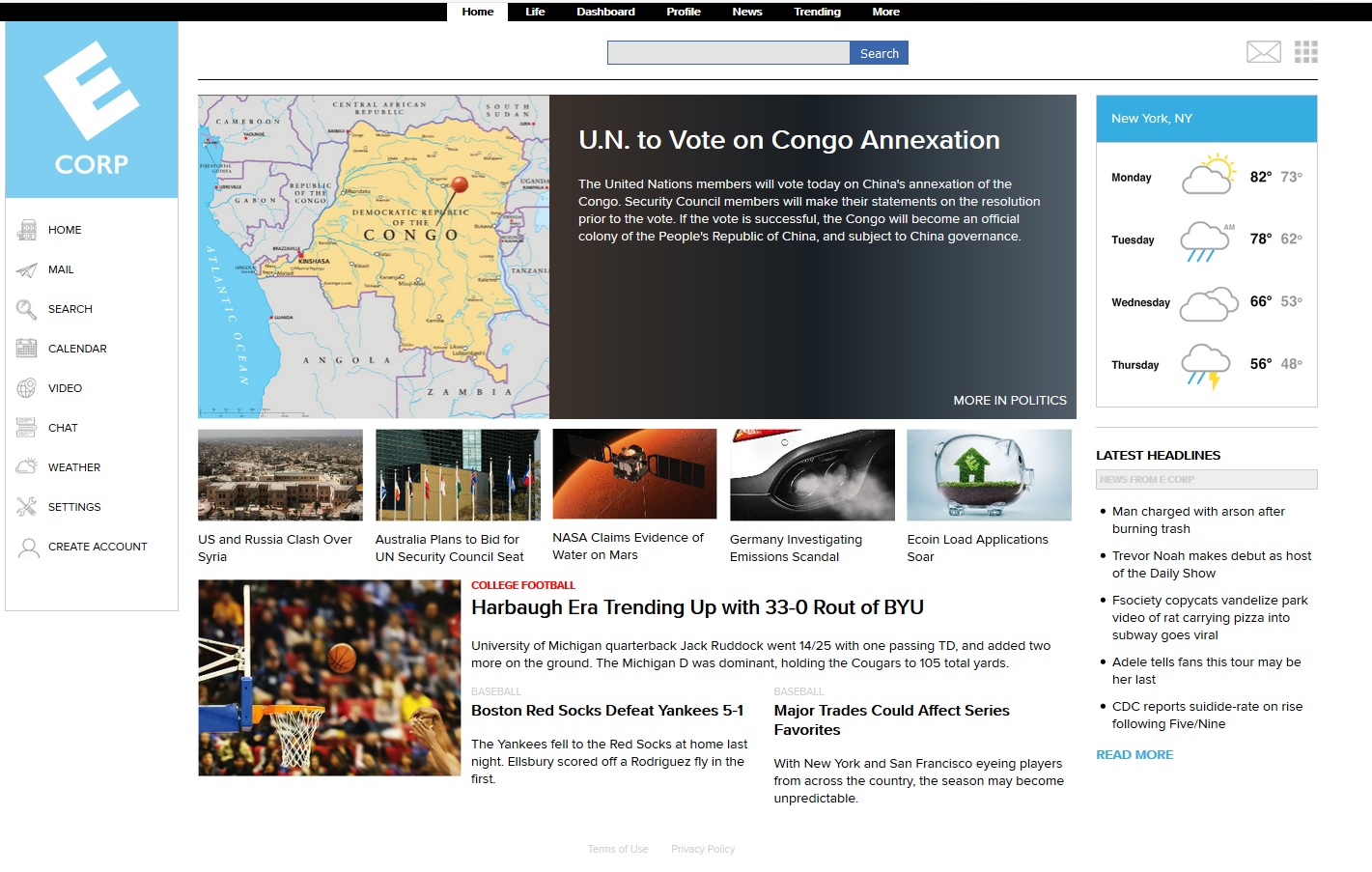
The E-Corp website has also undergone a major change of image and its home page now shows a news story about the UN voting on China's annexation of the Congo, which is a key part of the plot this season.
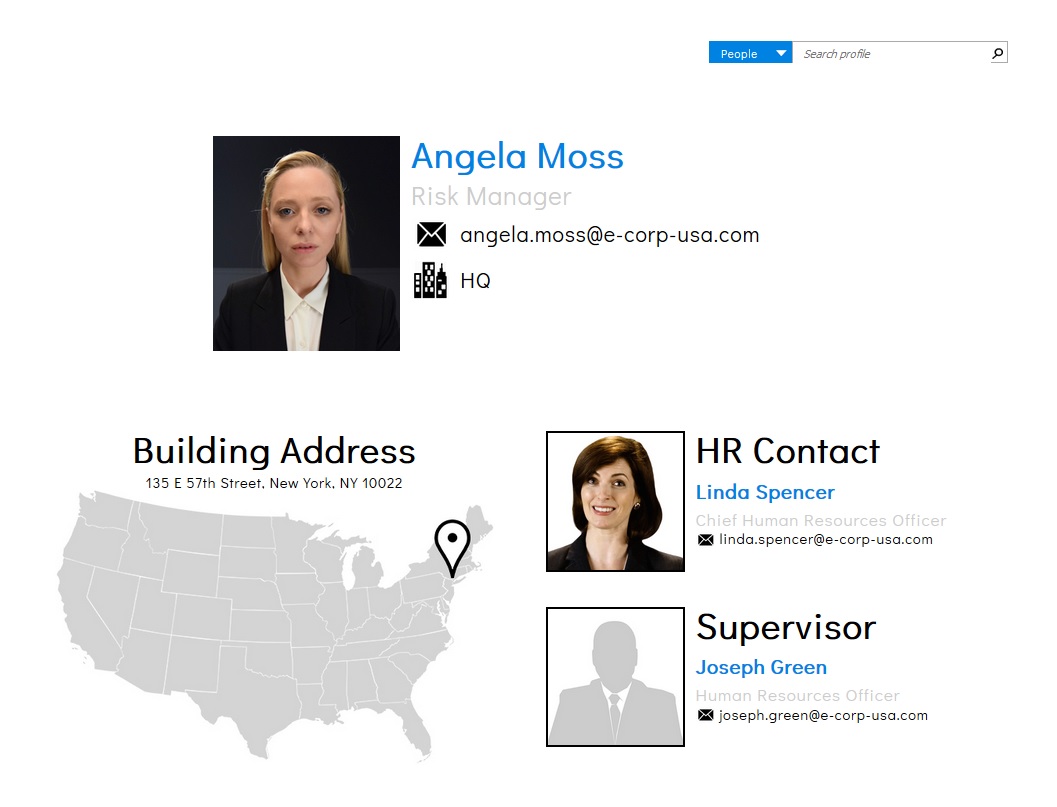
This website also show that options have been added to the corporate presence section, such as the ability to search by employee profile or zip code. This is where we found files for employees such as the person in charge of E-Corp's code-signing architecture and Elliot's cubicle mate, and the personnel file for Angela.
A page for submitting password reset requests has also gone live, although for now it only shows errors when any of the E-Corp corporate email addresses that we know of are entered.
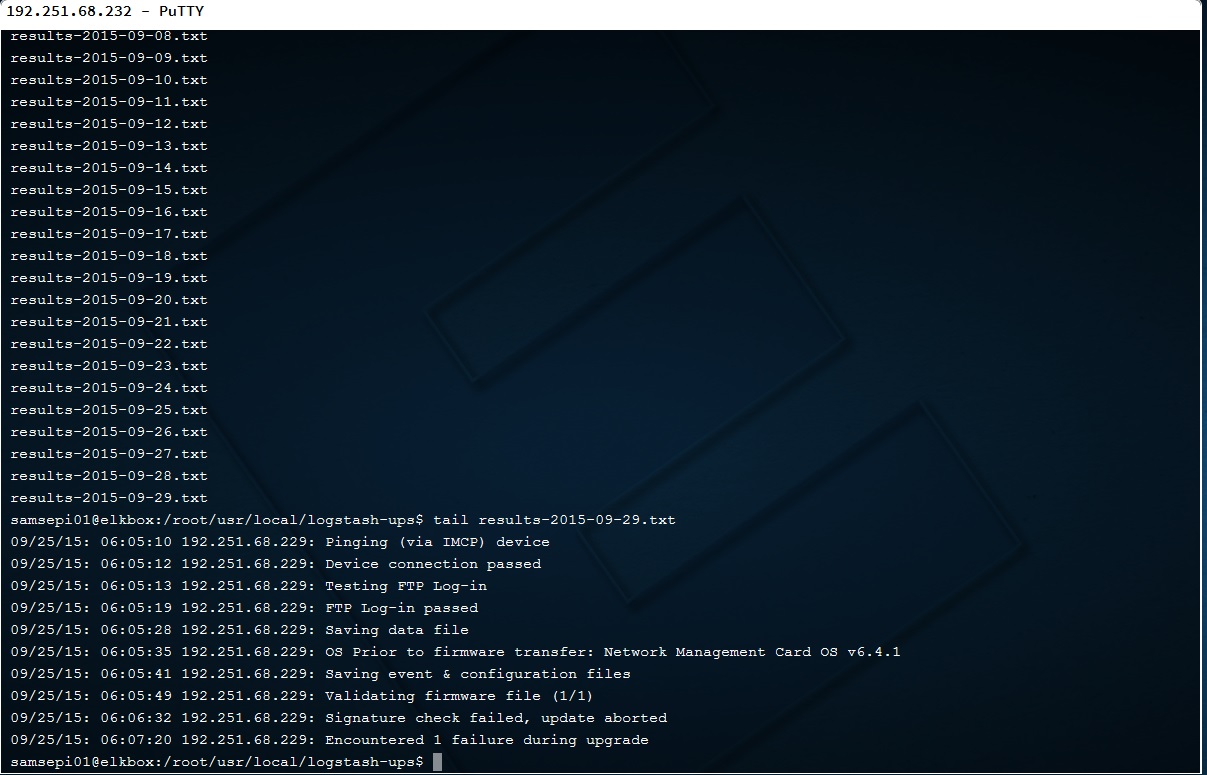
The last Easter eggs may be the most intriguing of all, however, especially for more technically-oriented fans among us. We will start with one of the URLs shown in this episode, 192.251.68.232, which is resolved at https://ycg67gca.bxjyb2jvda.net/ssh/terminal/. This loads a terminal where the event logs for the UPS monitored by Elliot can be viewed.
The last of these logs shows that an attempt was made to run a firmware update, but this failed because the digital signature could not be validated. Something similar can be seen in the Kibana dashboard installed by Elliot, which he accesses from another link that appears in this episode.
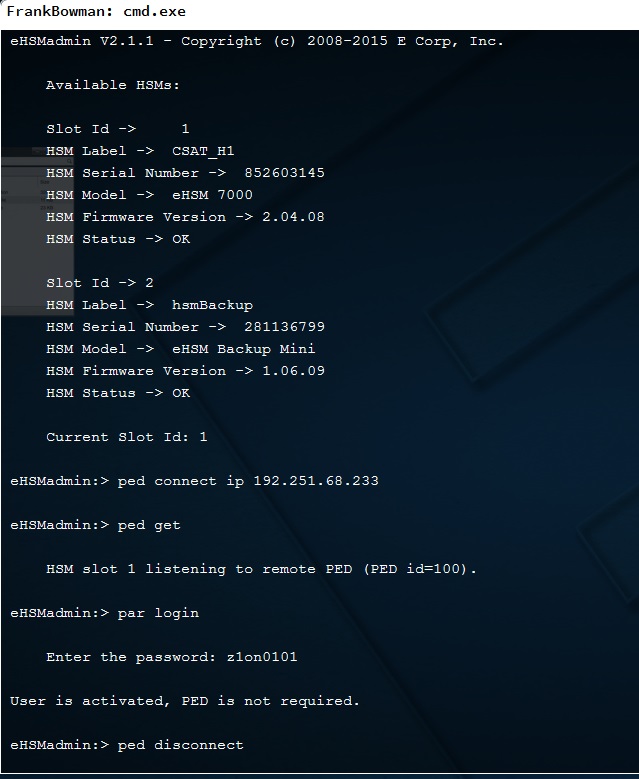
Finally, to recreate the data dump that Angela executes on E-Corp's HSMs, go to the URL 192.251.68.233, which is resolved at https://yakkqwhz.bxjyb2jvda.net/. This loads another terminal where you can get the encryption key that authorizes you to sign malicious firmware updates to run on the UPS that Elliot is trying to protect.
By entering the password z1on0101 when prompted, and then entering the code 022350 after seeing the message "Please attend to the PED.", you will see that the backup starts and at the end it shows the required encryption key: B-TUDGTDL-0112180501042508051805. And here's an interesting fact: if you take the numerical part of that key and run it through an encryption/decryption tool from numbers to letters, you will get the message “ALREADYHERE”.
Image credits: USA Network