Sony’s PlayStation Network was back online on Monday, and the information of its 53 million users was safe, despite a weekend-long cyber attack which left PSN hacked, and a reported bomb threat by the same group which caused the diversion of a flight carrying a Sony executive, according to Reuters report.
A Twitter user with the handle @LizardSquad claimed responsibility for the attack, according to ITV’s report.
Sony summed up in a blog post, “The networks were taken offline due to a distributed denial of service attack. We have seen no evidence of any intrusion to the network and no evidence of any unauthorised access to users’ personal information.”
One of @LizardSquad’s Tweets said, “"Sony, yet another large company, but they aren't spending the waves of cash they obtain on their customers' (PlayStation Network) service. End the greed,"
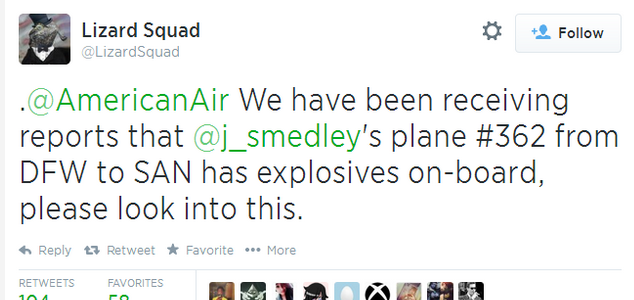
PSN hacked - and bomb threat issued
The group’s motivation for its attack was unclear. Shack News reported that the group also aimed DDoS attacks at Blizzard's Battle.net, Riot's League of Legends and Grinding Gear Games' Path of Exile.
In a series of Tweets, the group also claimed to be aiming similar attacks at Xbox Live. "We don't comment on the root cause of a specific issue, but as you can see on Xbox.com/status, the core Xbox LIVE services are up and running," Xbox spokesman David Dennis said in an interview with Reuters.
Vice commented, “Since Lizard Squad's fake threat of explosives and media coverage citing it as responsible for the ‘hack,’the group has gained over 15,000 followers on Twitter. One of those followers includes Smedley himself.
Gained 15,000 Twitter followers
In a blog post timed for Cologne’s Gamescom this year, ESET Distinguished Researcher Aryeh Goretsky said, “Computer criminals don’t just target gamers: gaming companies themselves can be targeted as well. Probably the most well-known example of this is the April 2011 breach of the Sony PlayStation Network gaming and Qriocity music streaming service, which resulted in the compromise of the names, addresses and credit card details of 77 million user accounts.
“ESET provided extensive coverage of the Sony data breach in our blog, starting from the initial report of the breach in April 2011 all the way up to the proposed settlement of a week ago. As a result, I am not going to discuss the details of the Sony breach in this article.
“Readers should be aware that this sort of problem is not unique to Sony, either. Almost exactly, two years ago, Blizzard Entertainment suffered a data breach themselves, although they responded in a different and — this author thinks — more responsible fashion.
The point here is that computer game companies and their associated services face real threats from criminals: if they charge customers for online play, the purchase of in-game items, or otherwise contain customer billing data in their computers, then those computers systems are targets for financial crime.”
A We Live Security guide to staying safe from cybercriminals while gaming online can be found here.