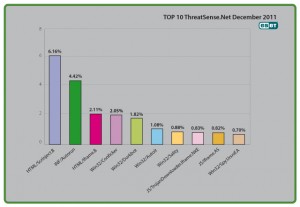
It's a little ironic. My earlier blog Autorun and Conficker not dead yet: Threat Trends Report shows that over the whole year, Conficker and INF/Autorun maintained the top two places worldwide according to our ThreatSense.Net® telemetry. This morning I got to see the ThreatSense statistics just for the month of December.
As you'd expect, INF/Autorun and Win32/Conficker are highly placed with 4.42% and 2.05%, putting them in 2nd and 4th place respectively. Not much different to November, where they were 4.38% and 2.2% respectively. And as you'd expect, both show a significant percentage reduction compared to the figures for early in 2011. 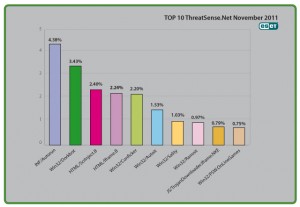
The surprise here is that HTML/Scrinject.B*, which shows a considerable spike in December that took it to the number one spot. It's actually pretty difficult to ascribe exact causes to statistical artifacts like this, because the telemetry is basically counting infection attempts out there in the cloud somewhere and ranking them by percentage share rather than analysing individual infections or infection attempts. And in fact, Scrinject.B has been prominent for a while (as have other iFrame-related detections): it's just the extent of that prominence in December that caught my eye.
Still, I asked a couple of my colleagues in the lab whether they had any thoughts on what might have affected these figures. Security Evangelist Peter Stancík wondered if it could be related to a spike in Internet Christmas usage: more shopping, more careless clicks, more hits. And certainly we've seen evidence over recent years of an interaction between increases in certain kinds of threat and the run-up to Christmas that begins in November.
Researcher Daniel Novomeský also suggested there is likely to be a connection with increased distribution of rogue software via adult-content websites: cybercriminals have for many years proved all too ready to exploit surfers actively searching for xxx content or warez. While it's not really practical to quantify the increased risk of infection to porn surfers, the fact that social engineering malware messages so often use sex (often pornographic) as a hook is certainly significant.
*Generic detection of HTML web pages containing script obfuscated or iframe tags that that automatically redirect to the malware download.
David Harley CITP FBCS CISSP
ESET Senior Research Fellow