We recently published a blogpost about Telekopye, a Telegram bot that helps cybercriminals scam people in online marketplaces. Telekopye can craft phishing websites, emails, SMS messages, and more.
In the first part, we wrote about technical details of Telekopye and hinted at hierarchical structure of its operational groups. In this second part, we focus on what we were able to learn about Neanderthals, the scammers who operate Telekopye, their internal onboarding process, different tricks of trade that Neanderthals use, and more.
Key points of this blogpost:
- How aspiring Neanderthals join Telekopye groups.
- Detailed view of the whole scamming operation from the Neanderthals’ perspective.
- Analysis of the scam scenarios and what each Neanderthal has to do in order to be successful.
- The tools utilized by senior Neanderthals.
- Insights into tricks that Neanderthals use to lure their victims.
- Highlights from an interview with one of the Telekopye administrators.
Overview
Recently, we published an analysis of Telekopye; in this follow-up blogpost, we focus on the Neanderthals’ tactics and modus operandi. Our information comes from three main sources:
- source code of the bot itself,
- analysis of Neanderthals’ conversations from scamming groups we’ve infiltrated, and
- our analysis of Neanderthals’ internal documentation – a collection of documents, graphs, pictures, and more – that they use as their own personal knowledge base. Such information is provided to newcomers to aid them with onboarding.
We would also like to thank Flare, who helped us in our research.
Joining a group
Telekopye groups recruit new Neanderthals via advertisements in many different channels, including underground forums. These advertisements clearly state the purpose: to scam online marketplace users, as seen in Figure 1.
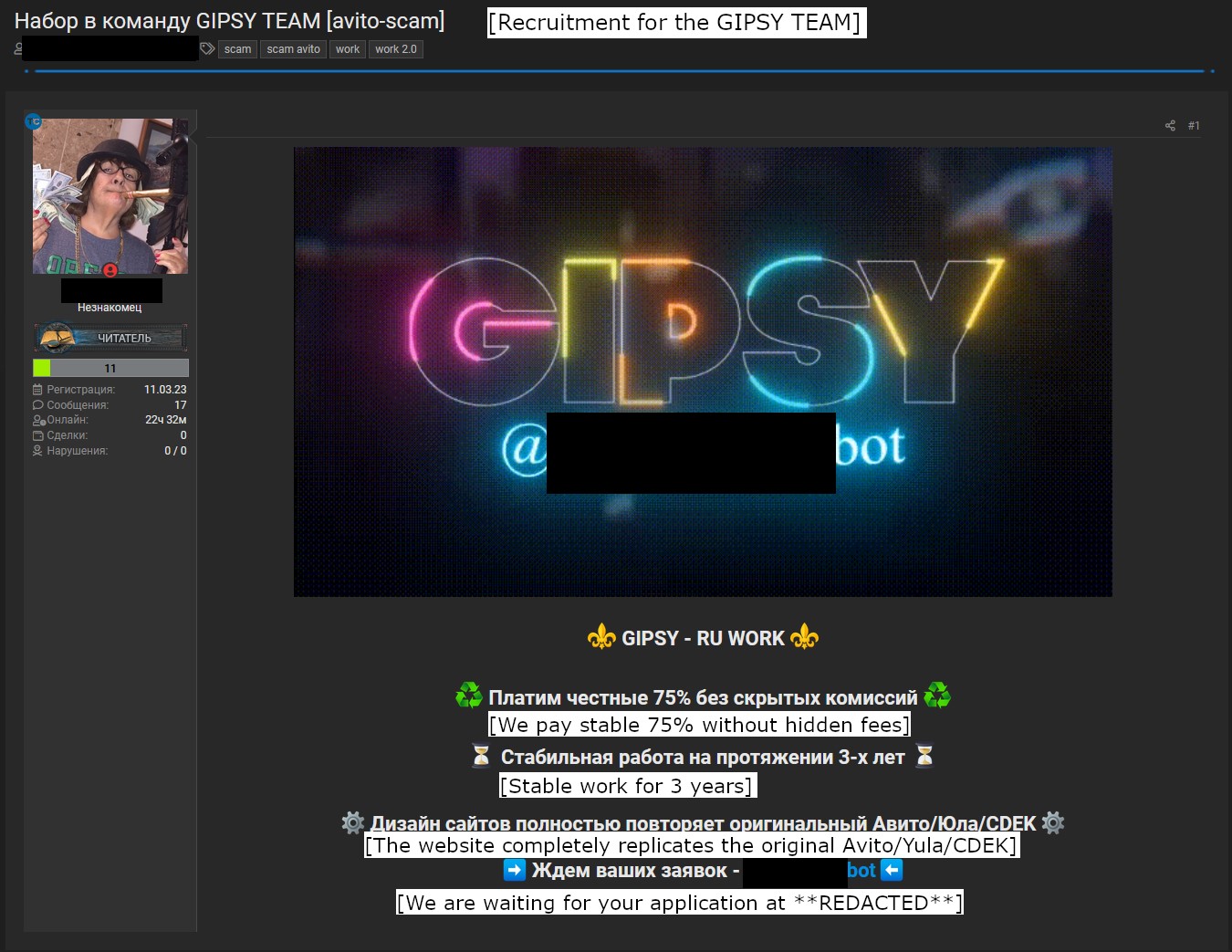
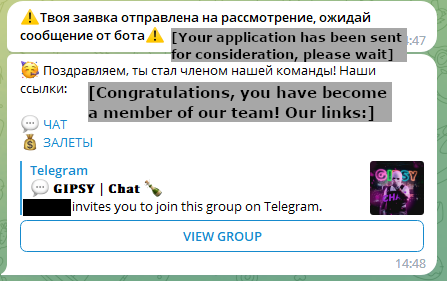
Aspiring Neanderthals are required to fill out an application, answering basic questions like where they learned about the group and what experience they have in this line of “work”. If approved by existing group members with sufficiently high role, the new Neanderthals can start using Telekopye to its full extent. Furthermore, every Neanderthal is required to join two channels: a group chat where Neanderthals communicate and where rules and manuals are kept, and a separate channel where transaction logs are kept. The process is demonstrated in Figure 2.
Types of scams
There are three main scam scenarios:
1. Seller, internally referred to as 1.0.
2. Buyer, internally referred to as 2.0.
3. Refund.
Figure 3 is the creation menu for the first two scam scenarios, where column 1 at the bottom represents Seller scams (1.0). The Refund scam scenario is then tied to each scam scenario individually. These scam types are described in the following subsections.
Seller scam
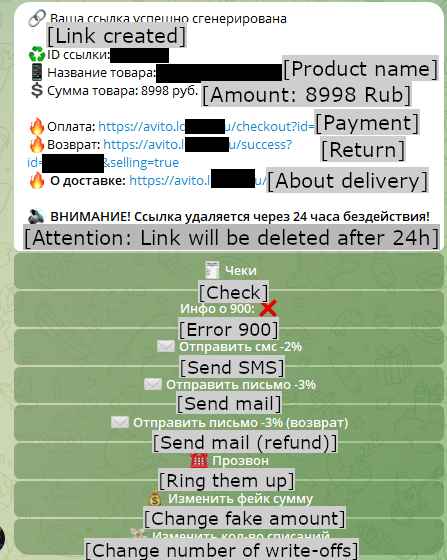
In this scenario, Neanderthals pose as sellers and try to lure unsuspecting Mammoths into buying some non-existent item. When a Mammoth shows interest in the item, the Neanderthal persuades the Mammoth to pay online rather than in person. If the Mammoth agrees, the Neanderthal provides a link to a phishing website provided by Telekopye and carefully crafted to resemble the payment page of the legitimate online marketplace listing the reputed item. Unlike the legitimate web page though, this page asks for an online banking login, credit card details (sometimes including balance), or other sensitive information. If the Mammoth enters this data, the phishing website automatically steals it. Interestingly, this data does not become available to the Neanderthal offering the item for sale, but is processed by other Neanderthals. Figure 4 shows the Telekopye menu with already created phishing links and Figure 5 demonstrates the communication during this scam scenario.
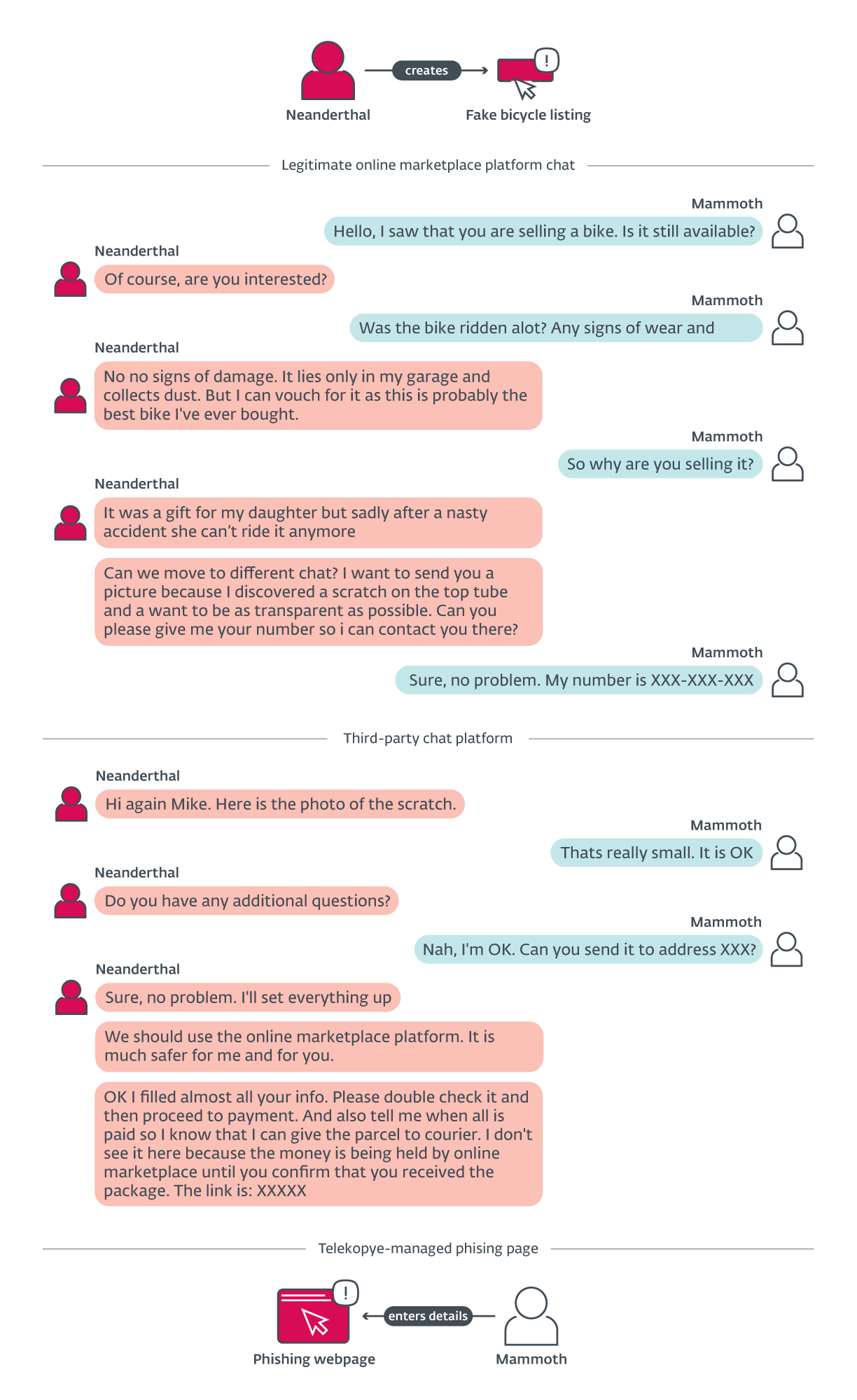
Buyer scam
In this scenario, Neanderthals pose as buyers and they research a Mammoth to target. They show interest in the item a Mammoth is selling and claim they already paid via the providing platform. The Neanderthals proceed to send the Mammoths email or SMS messages (created via Telekopye) with a link to a carefully crafted phishing website (also created via Telekopye; see Figure 6), claiming the Mammoth needs to click this link in order to receive their money from the platform. The rest of the scenario is very similar to the Seller scam with slight variations during conversation (depicted in Figure 7).
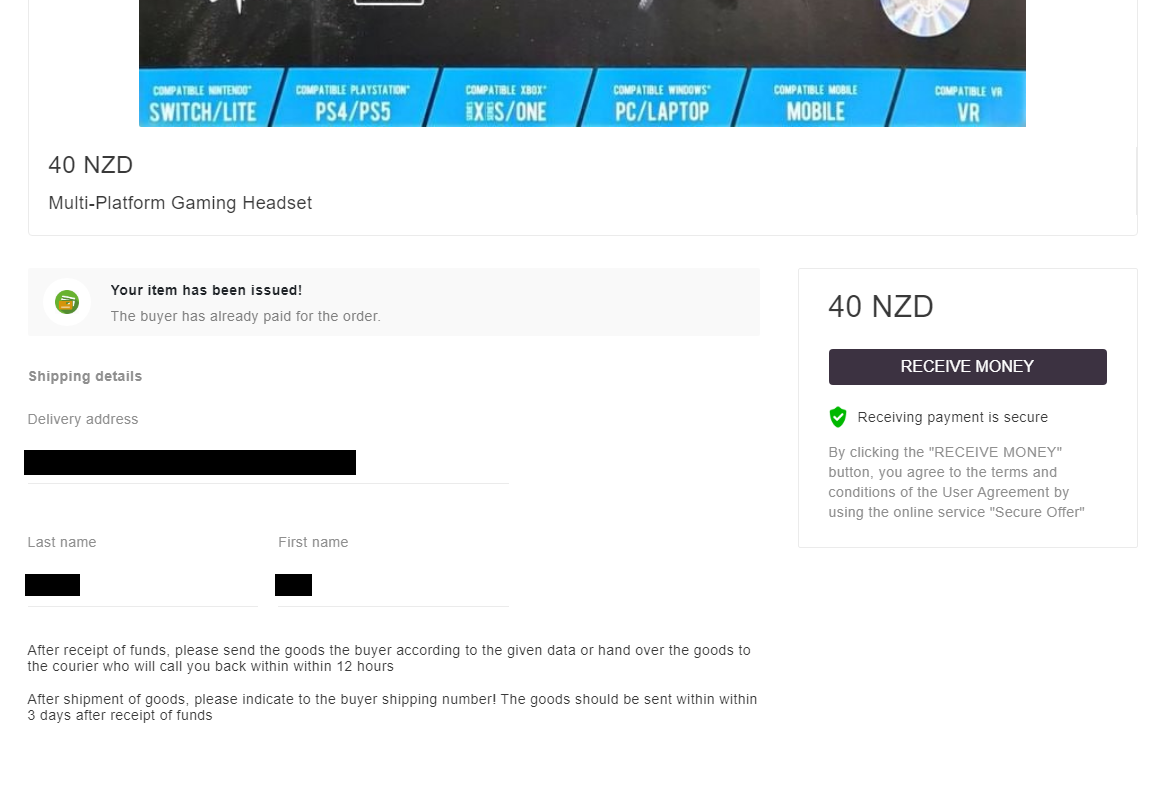
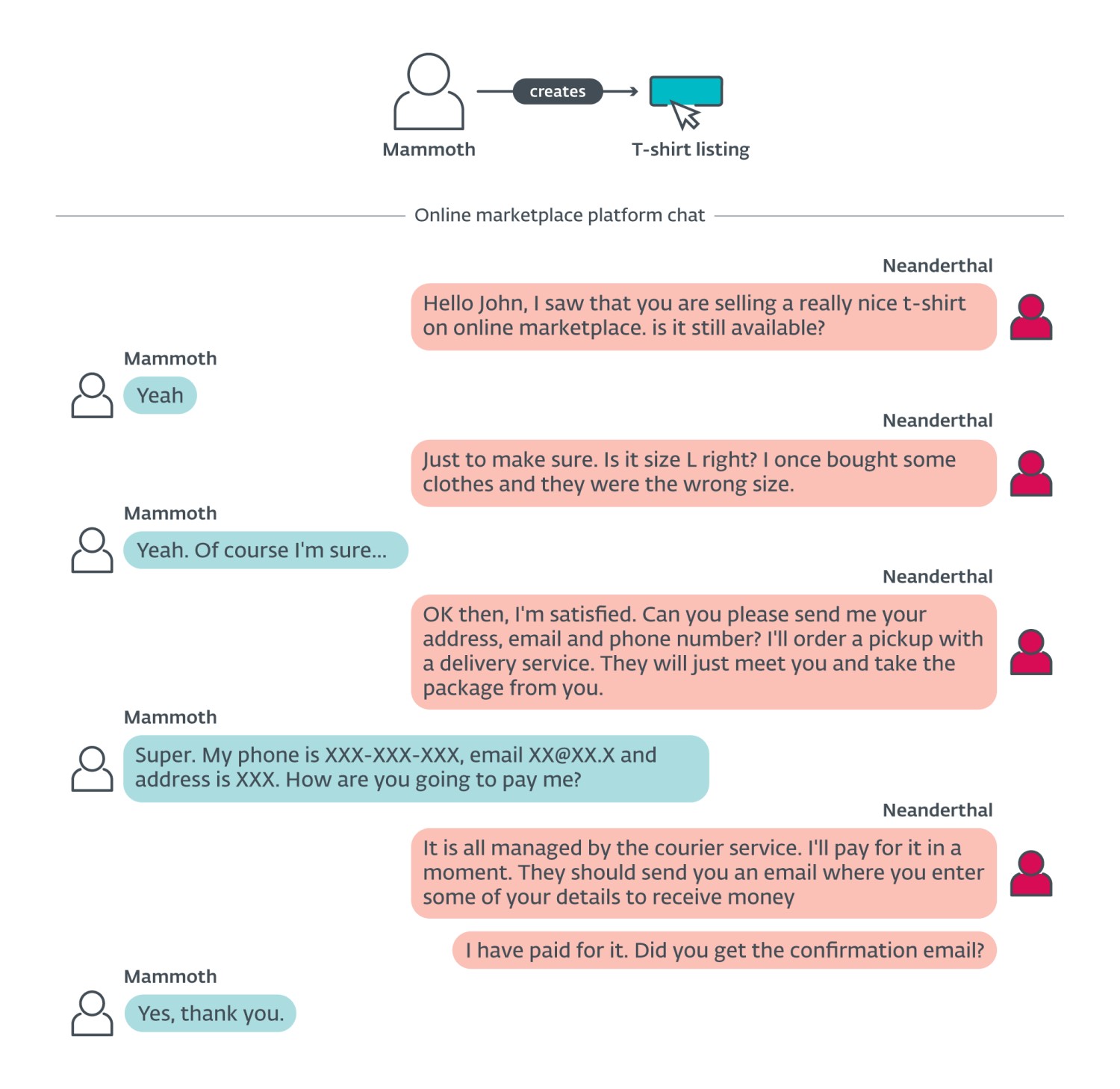
Refund scam
In this scenario, Neanderthals create a situation where the Mammoth is expecting a refund and then sends them a phishing email with a link to the phishing website, once more serving the same purpose. Neanderthals either send such emails to Mammoths they didn’t contact earlier, counting on them getting greedy and trying to get this “refund” or they combine it with the Seller scam scenario – when Mammoths complain that they didn’t receive their goods, Neanderthals send them refund phishing emails in an attempt to scam them for a second time.
Modus operandi
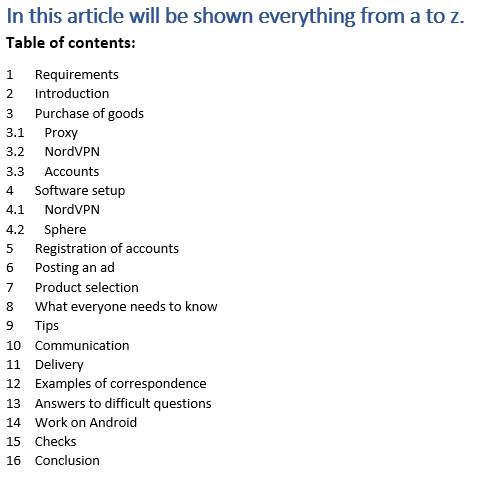
Now that we have described the different scam scenarios, let’s look at what knowledge the Neanderthals have gathered throughout the years of their operation. Their internal documentation consists of images, graphs, short guides, and even complex documents – the table of contents of one such document is illustrated in Figure 8.
We also discovered that there are two kinds of Neanderthals. The first kind writes to every possible Mammoth and the other one is much pickier when it comes to looking for a potential Mammoth. There is a bit of rivalry between them as the more cautious kind argues that the “reckless” behavior of the less cautious scammers might bring a bit more profit, but it creates much more public awareness.
Preparation
Preparing for a scam differs based on the chosen scenario. For the Seller scam scenario, Neanderthals are advised to prepare additional photos of the item to be ready if Mammoths ask for additional details. If Neanderthals are using pictures they downloaded online, they are supposed to edit them to make image search more difficult.
For the Buyer scam scenario, the key part of a Neanderthal’s preparation is how they choose the Mammoth. Over the years, Neanderthals have created guidelines to follow when choosing their targets – they consider gender, age, experience in online marketplaces, rating, reviews, number of completed trades, and many more indicators.
Market research
In almost every group of Neanderthals, we can find references to manuals with online market research from which Neanderthals draw their strategies and conclusions. The source of this research is usually a study from 2017 by Avito and Data Insight agency. Figure 9 illustrates the results of one such research, depicting graphs of gender, age, experience, and income distribution on a specific online marketplace.
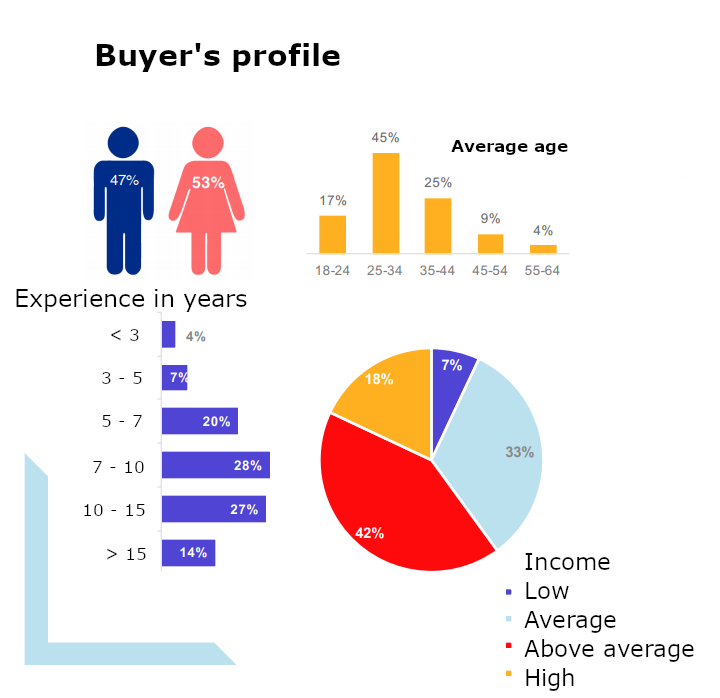
During the Buyer scam scenario, Neanderthals choose their targets based on the type of items they are selling. For instance, some groups avoid electronics completely. On the other hand, mobile devices are a valued category for other groups. The price of the item is also important – if too high, then Neanderthals will not target such Mammoths, as they believe that the Mammoths’ vigilance will be much higher by default. Manuals recommend that Neanderthals, in the Buyer scam scenario, pick items with a price between 1,000 to 30,000 rubles (€9.50 to €290 as of 20th October, 2023).
The location of the Mammoth is also important. Neanderthals focus more on richer cities where they expect more listings and people not keeping such a close eye on their own finances.
Finally, the scammers take the day of the month into consideration too. They aim at days right after people receive their paychecks, as they naturally expect they'll have more money in their bank accounts.
Web scraping
Neanderthals utilize web scrapers to quickly go though many online marketplace listings and pick a perfect Mammoth who will fall for the scam; this is, as we have already written, a crucial initial part of the Buyer scam scenario.
We are not aware of custom web scrapers implemented by Neanderthals, but their documentation mentions a few offered as legitimate services. Neanderthals scrape the targeted marketplace for listings, details of items, and user information, which results in a CSV or XML file. Neanderthals then use the results to quickly find the right targets. We provide an example of such a file in Figure 10.
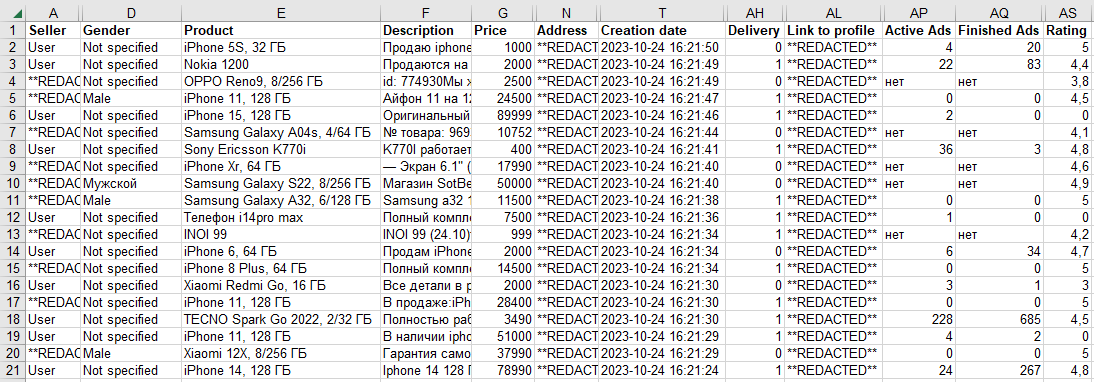
User ratings and experience are of particular interest to Neanderthals, as they use this information to avoid targets that they deem likely to spot the scam.
Avoiding in-person delivery
For safety reasons, many Mammoths prefer both in-person payment and in-person delivery for sold goods. That poses an issue for Neanderthals as they need to persuade Mammoths to agree to use a delivery service and online payment, so that they can direct them to the phishing website. Usually, they claim they are too far away or that they are leaving the city for a business trip for a few days. At the same time, they try to look very interested in the item to increase the chances that the Mammoth will agree to their suggestion.
Phishing web page link delivery
Many legitimate online marketplaces have an integrated chat feature and, alongside, moderation in place. Sending someone a link through such a chat is usually a red flag and may very well result in a ban. Neanderthals try to overcome this obstacle by persuading Mammoths to continue their conversation on a different chat platform that has less monitoring.
Their arguments are very similar to those against in-person delivery. They claim that they need to leave their home and cannot access the chat from their mobile phone, but are able to continue their talk on one of the chat apps.
By their own statistics, Neanderthals claim that about 50% of Mammoths will agree to a platform change and 20% of those will fall for the scam. This results in a 10% success rate overall.
Another favored method of delivery is using email or SMS. Telekopye is able to quickly generate convincing phishing messages. Neanderthals use tricks (some of them illustrated in Figure 11) to learn Mammoths’ email addresses or phone numbers in order to send them such messages. The advantage of this approach is that asking for a phone number or email address will likely not trigger any red flags for neither Mammoth nor chatting platform and the Neanderthal does not need to persuade the Mammoth to transfer to a different chat platform.
Communication
No AI is utilized by Telekopye. This may be surprising, but Neanderthals believe that their approach is superior and less likely to be spotted by monitoring mechanisms. As a result, the vast portion of their internal documentation is focused on communication techniques to achieve the best results.
Earning the Mammoth’s trust is crucial to the success of a scam. Neanderthals often intentionally don’t immediately reply to every message but wait (sometimes even a few hours) to create the illusion that they are busy with regular everyday life. Speaking of time: they try to adapt to the Mammoth’s time zone in order not to raise suspicion.
They often engage in chitchat first; they may even share a fake personal story. The whole purpose is to look for red flags – signs that would tell the Neanderthal that the Mammoth is too suspicious or experienced. Since Neanderthals are focused on profit, they don’t want to spend time on Mammoths who end up spotting the trap.
Another great example is that when Neanderthals utilize the Buyer scam scenario, they assure Mammoths that they have already paid for the item. This, combined with the design of the phishing email that promises quick money retrieval, results in Mammoths being less vigilant.
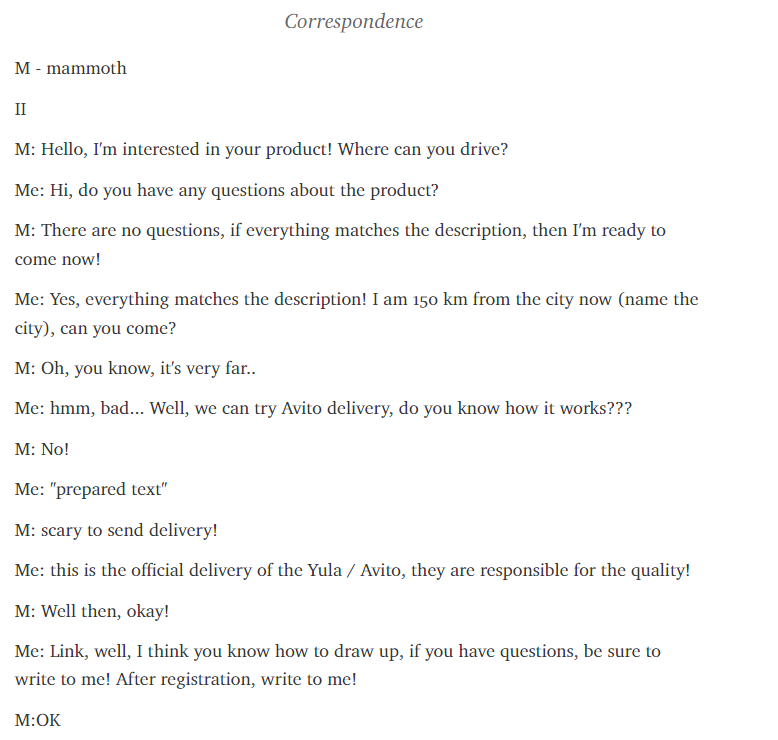
Experienced Neanderthals provide newcomers with full conversations to take inspiration in; one such example is provided in Figure 12.
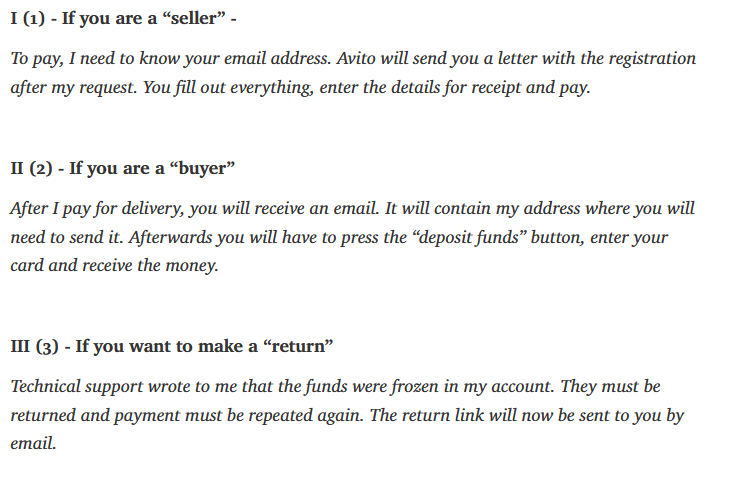
Neanderthals only tolerate a certain level of resistance from Mammoths – if they deem the scam is not likely to succeed, they move to a different target. However, if they feel like they have almost won, they are very persuasive. A perfect example is their documented approach to situations where they successfully harvest the Mammoth’s sensitive data, but either the bank blocks the transaction or there are insufficient funds. In that case, Neanderthals may go as far as asking the Mammoth to use a family member’s card or even call their bank and authorize the transfer themselves.
Neanderthals are ready to answer many unexpected questions regarding the legitimacy of their requests (see Figure 13).

Translation
As this operation targets Mammoths internationally, Neanderthals need to create the illusion that they speak the Mammoth’s language well enough. It is quite common to encounter Russian-speaking Neanderthals who can write in English. Interestingly, we were able to cross-reference the Telegram nicknames of many Neanderthals with language-learning platform profiles. These accounts usually stated that the owner speaks Russian and English. Obviously, the connection may just be coincidental.
For many years Neanderthals used Google Translate. Since at least 2021, Neanderthals moved towards other translators, such as DeepL, as (in their opinion) it understands context better.
Besides using translators, they have created many translation tables over the years, with verified translations of common phrases into multiple languages. These translations are most commonly from Russian to European languages (see Figure 14). Neanderthals just copy and paste these translated sentences into the chat with the Mammoth.

Group specific features
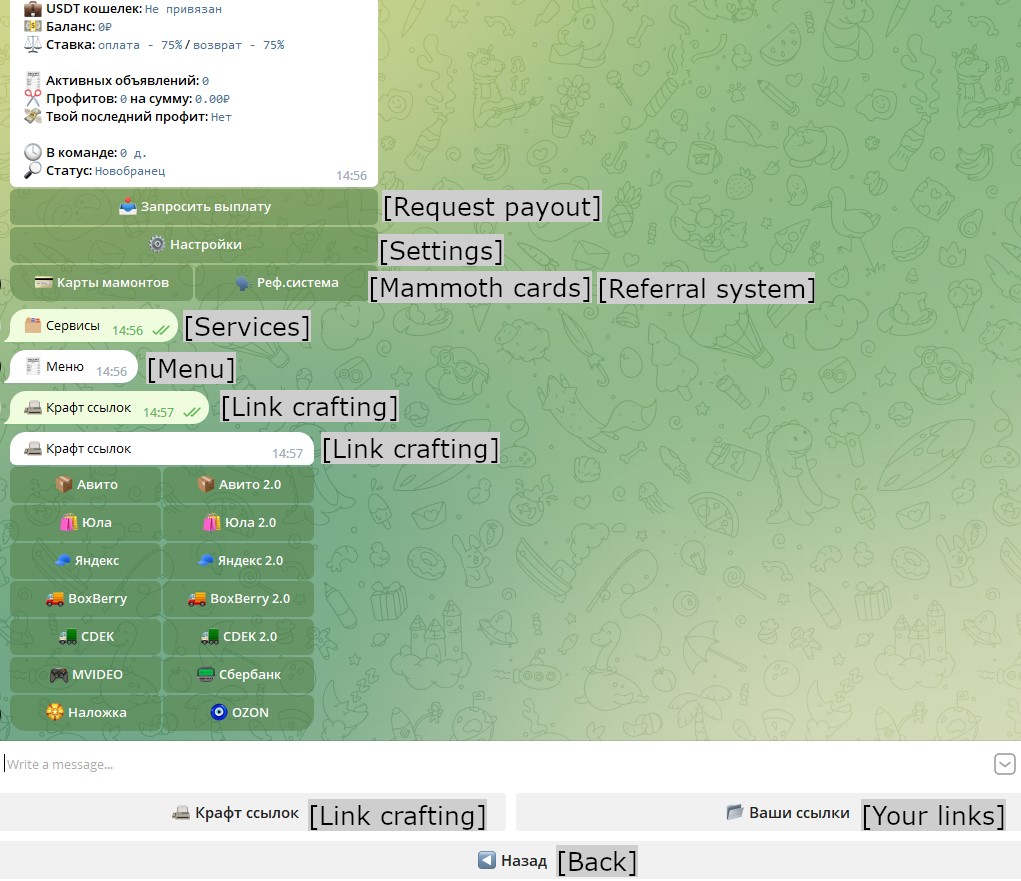
We should also mention that different groups have different quality-of-life improvements to Telekopye. For example, when generating a phishing link (a result can be seen in Figure 15), Neanderthals from one of these groups are asked several questions that enable them to have certain degree of customization of each phishing website. The most interesting is the question about manual/automatic phishing site generation. In the case of manual generation, the Neanderthal must specify all information needed to create the phishing website. For Neanderthals posing as buyers, this takes from 10 to 15 questions (Figure 16).
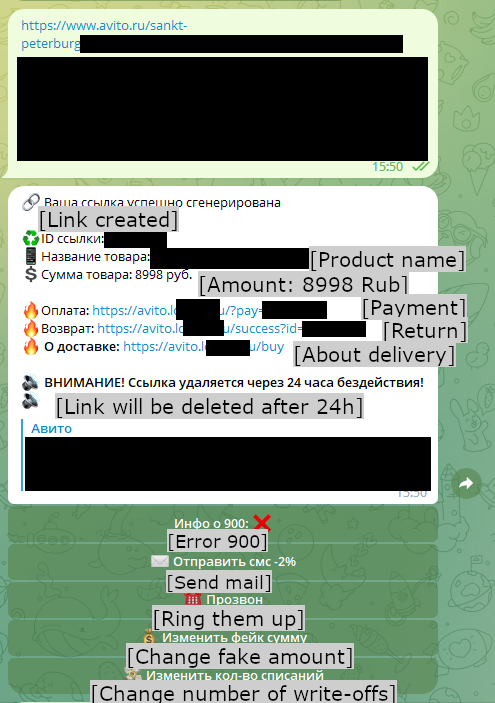
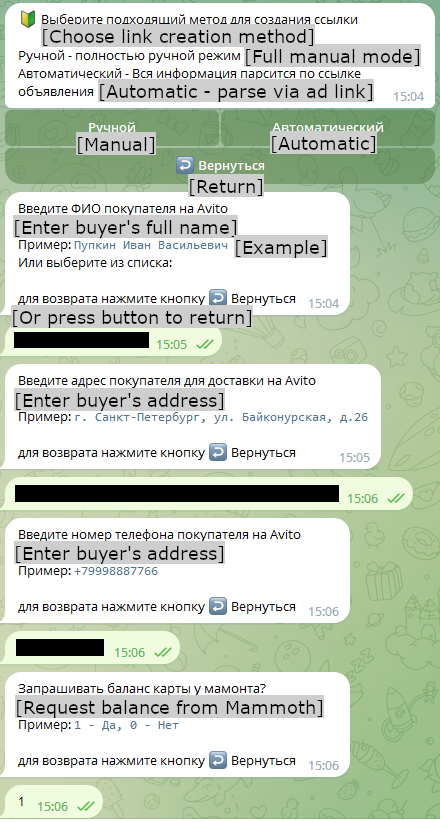
In the case of automatic page generation, the Neanderthal only needs to specify the URL of the item to “buy” and to answer five questions (like what the buyer's name and phone number are). Telekopye then scrapes all information from the website and creates the phishing website.
Anonymity and evasion
Neanderthals believe their groups are full of “rats” (for example, law enforcement or researchers). So, they religiously stick to the rules, mainly no probing for information that could identify other members of the group. Breaking such rules may very well result in being banned. The golden rule is “work more talk less”. In addition, they are encouraged to use VPNs, proxies, and TOR to stay safe. Neanderthals provide newcomers with extensive guides and even engage in heated discussions over what programs or services to use and why, including browser preferences. Some Neanderthals even utilize Orbot, a TOR variant for Android.
Money
Neanderthals need to hide not only their identities and location, but also their money. Naturally, cryptocurrencies are the answer to that. We weren’t able to draw any conclusions regarding cryptocurrency preference.
Finally, Neanderthals prefer services for which they can register using only a mobile phone number. They consider this the best approach, since it is relatively easy to buy a SIM card while not disclosing their identity.
Bypassing automatic detection
Online marketplace scams are nothing new. Over the years, the platforms providing these services have implemented a number of techniques to counter scammers and increase their customers’ security. The Neanderthals are aware of this and continue to experiment with different approaches to overcome the platforms’ moderation policies. One early and rather foolish attempt was to utilize Google Forms to phish personal information from Mammoths (as seen in Figure 17). Considering the information they targeted, the goal was to obtain a means to communicate through a different channel – email or SMS – where strict moderation wouldn’t take place.
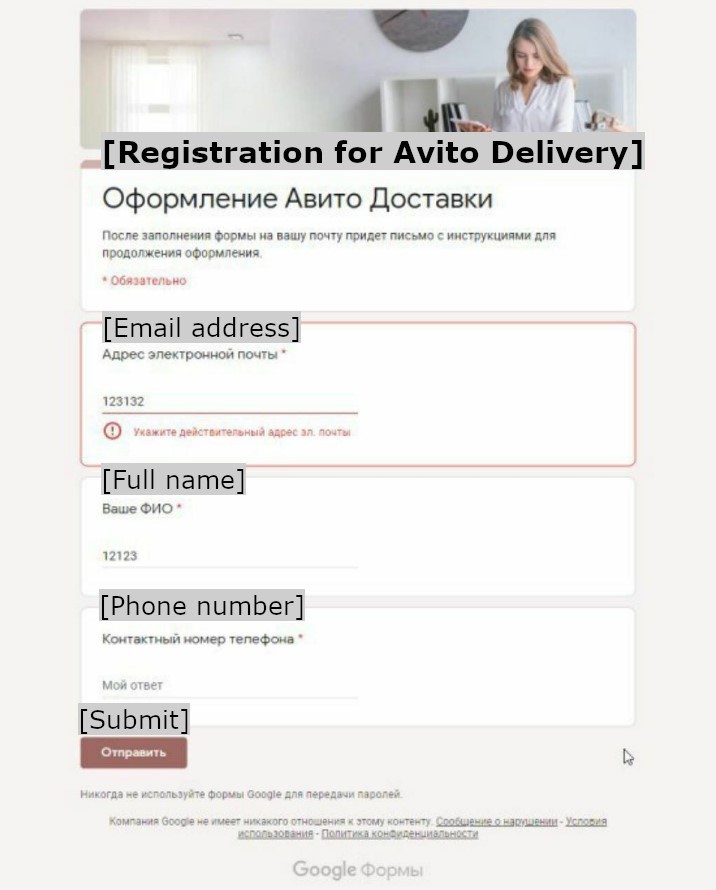
Nowadays, almost all Neanderthals try to transfer their Mammoths to less policed, legitimate chat platforms. Neanderthals choose them because they believe banning accounts there takes time. Additionally, sending various links over chat platforms is common practice rather than suspicious behavior. As a bonus, almost everybody is familiar with such applications, so Neanderthals don’t have to explain how they work.
Despite considering these platforms much safer, Neanderthals tread carefully nonetheless. They avoid sending too many messages in a short period of time and try to personalize messages for different Mammoths – Telekopye aids them greatly in this effort.
Exploring new territories: Real estate scam
Some of the Neanderthals’ groups mention a different kind of scam scenario – one that targets real estate renters. The scam works as follows. During the preparation stage, Neanderthals write to a legitimate owner of an apartment, pretending to be interested and ask for various details, such as additional pictures and what kind of neighbors the apartment has. The Neanderthals then take all this information and create their own listing on another website, offering the apartment for rent. They cut the expected market price by about 20%. The rest of the scenario is identical to Seller scam scenario – the Neanderthal waits for a Mammoth to show interest, and directs the Mammoth to pay a reservation fee via a link that, of course, actually points to a phishing website.
Thanks to ESET’s telemetry we found that the phishing websites used in this scam scenario are suspiciously similar to the ones Telekopye creates for the Buyer and Seller scenarios. This, combined with the scam being advertised by Telekopye groups, leads us to believe that there is a connection. However, we neither infiltrated any group specializing in this scenario nor obtained a Telekopye variant designed for it.
Interview
When crawling through different manuals, groups, and additional materials, we found an interview with a Telekopye administrator that was done at the end of 2020. This helped us get a unique insight into the mind of a high-ranked Neanderthal. The interviewed Telekopye administrator operated a Telekopye group specializing in teaching new Neanderthals.
The administrator is at one point asked how he sees the future of this line of “work”. To that, he responds that “Online marketplace scams will always be present. It is much harder [to scam] than it used to be thanks to banning policies on different sites. But it is just not possible to stop all phishing on these sites”. He also says that he doesn’t scam anymore. He just got tired of it and now works only as administrator/tutor and that is the reason why his group is so unique. “I don’t fear Mammoths. Every other Mammoth will threaten you when they realize they’ve been scammed. Apparently, everyone these days is a wife or a friend of a minister of internal affairs”, says the administrator.
When asked whether he is thinking about creating a new scam project, he says that he does not have time for that. He moderates two channels, has an active lifestyle, does a lot of training, and he has only four hours a day at home.
He also confesses that he is fully aware that this kind of a job isn’t honest but finds a typical excuse for himself. “… some people will constantly pay for links, and someone will constantly throw them. Whoever tries hard in life will succeed.”. On top of that he says that if he feels sorry for Mammoth, he asks himself: “Why am I scamming them in the first place? Well… I only steal from the rich (research note: Mammoths that probably have at least €200 in their account) and if my conscience were that fragile, I would go work as a delivery man”.
Conclusion
In this second installment dedicated to Telekopye, we have focused on what we learned about Neanderthals. Thanks to having access to both their internal communication and their knowledge base, we have provided not only descriptions of different scam scenarios, but mainly a unique insight into their modus operandi and mindset.
We have demonstrated how the admission process for newcomers looks like and how Telekopye aids Neanderthals in their daily work. In addition, we have shown that they probably are experimenting with real estate scams as well.
Online marketplace scams are likely not going away. As we demonstrated in the first installment, we were able to discover dozens of groups operating Telekopye. That said, by having our unique insight into the scammers' operation, we believe a lot can be learned in order to protect users of such platforms from harm.
IoCs and a MITRE ATT&CK techniques table were provided in the first part of this analysis, and are unchanged, so please refer to that article for these.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.








