Just when we were getting over the SolarWinds supply-chain attack, we see Kaseya IT management software, commonly used in Managed Service Provider (MSP) environments, hit by another in a series of supply-chain hacks. As with the SolarWinds incident, this latest attack uses a two-step malware delivery process sliding through the back door of tech environments. Unlike SolarWinds, the cybercriminals behind this attack apparently had monetary gain rather than cyberespionage in their sights, eventually planting ransomware while exploiting the trust relationship between Kaseya and its customers.
ESET security researchers are monitoring this ransomware, which is widely attributed to the REvil gang whose malware ESET security products detect as Sodinokibi. Our preliminary analysis supports this attribution.
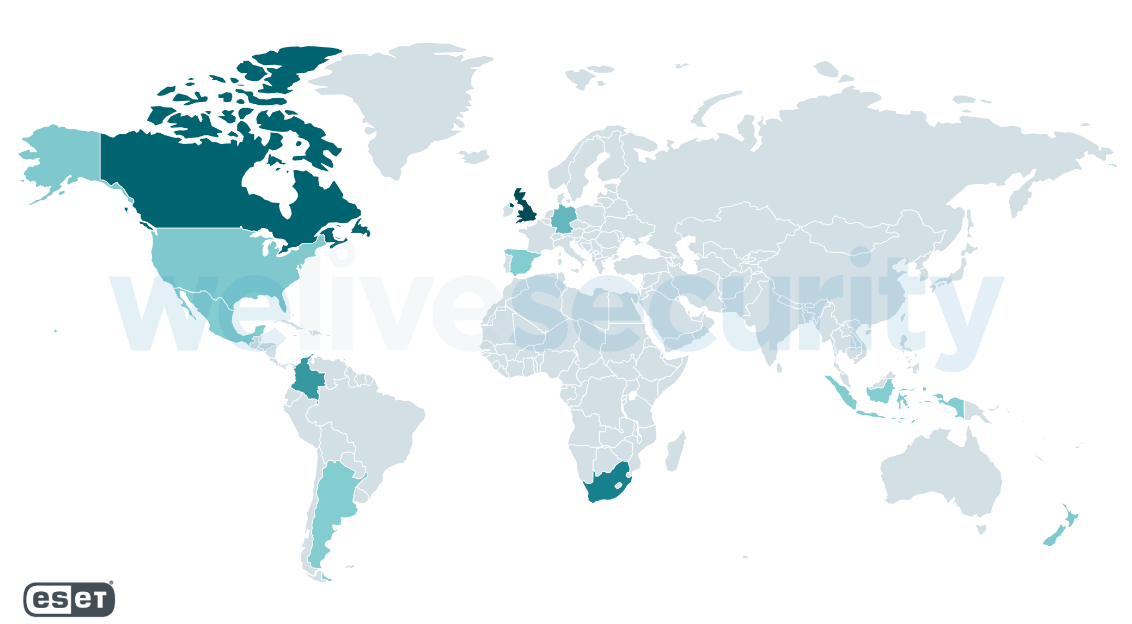
Figure 1. Victims by country
ESET added detection of this variant of the ransomware as Win32/Filecoder.Sodinokibi.N trojan on July 2nd at 3:22 PM (EDT; UTC-04:00). This detection includes both the main body of the ransomware, as well as DLLs it sideloads. ESET telemetry shows the majority of reports coming from the United Kingdom, South Africa, Canada, Germany, the United States, and Colombia.
Kaseya, for its part, has rushed to triage the incident and pushed out notifications to those potentially affected with the advice to shut potentially affected on-premises VSA servers down immediately.
That advice couldn’t come too soon. Once the server is infested, the malware shuts down administrative access and begins encrypting data, the precursor to the full ransomware attack cycle. Once the encryption process is complete, the system’s desktop wallpaper is set to an image similar to that seen in Figure 2, and the ransom note it refers to looks something like Figure 3, should a victim look for and open it.
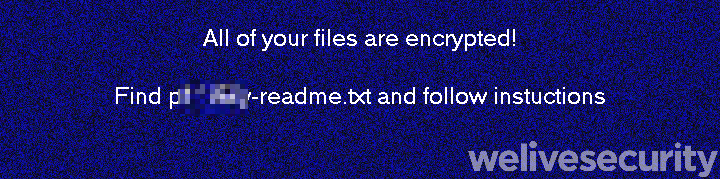
Figure 2. System wallpaper is changed to an image like this. (The second image is cropped for better readability.)
The first part of the “readme” filename is randomized.
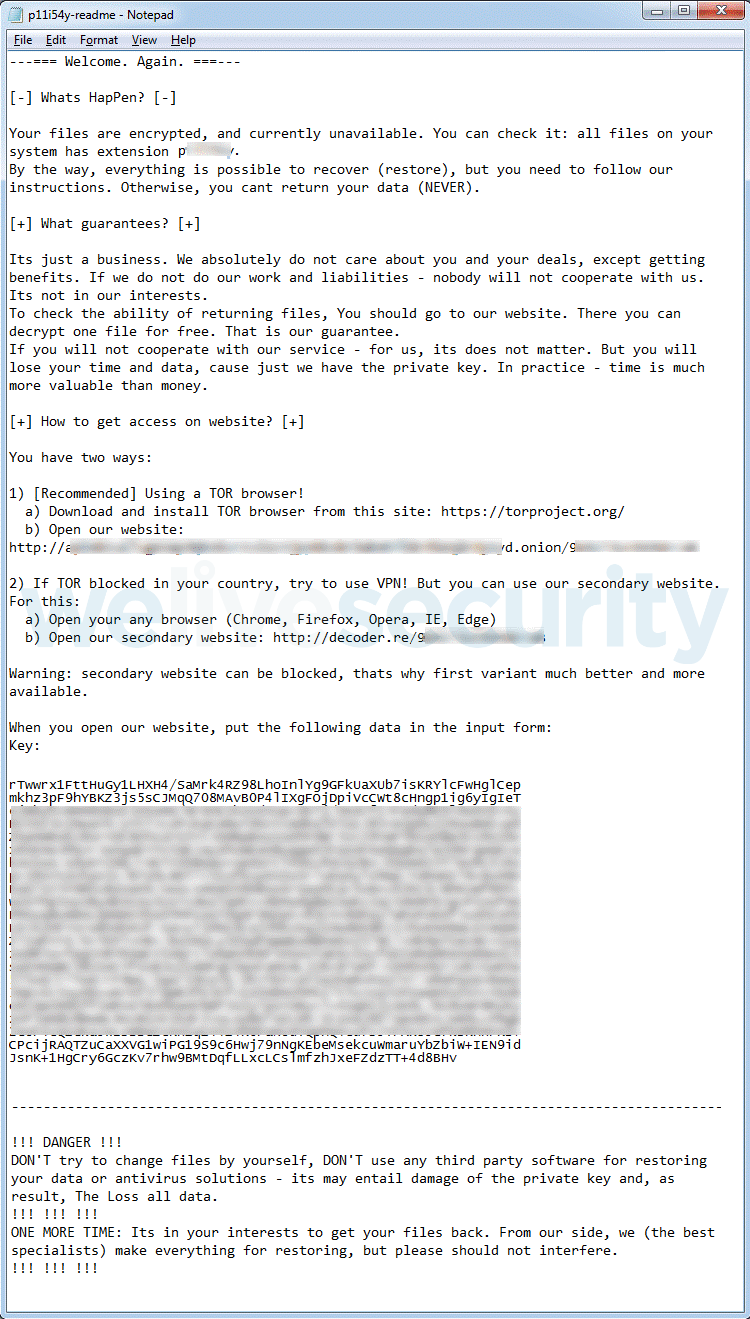
Figure 3. The ransom note (we have wrapped the text for readability)
By one report, hundreds of organizations now have encrypted data within their organizations, and are scrambling to contain and notify IT teams to act swiftly.
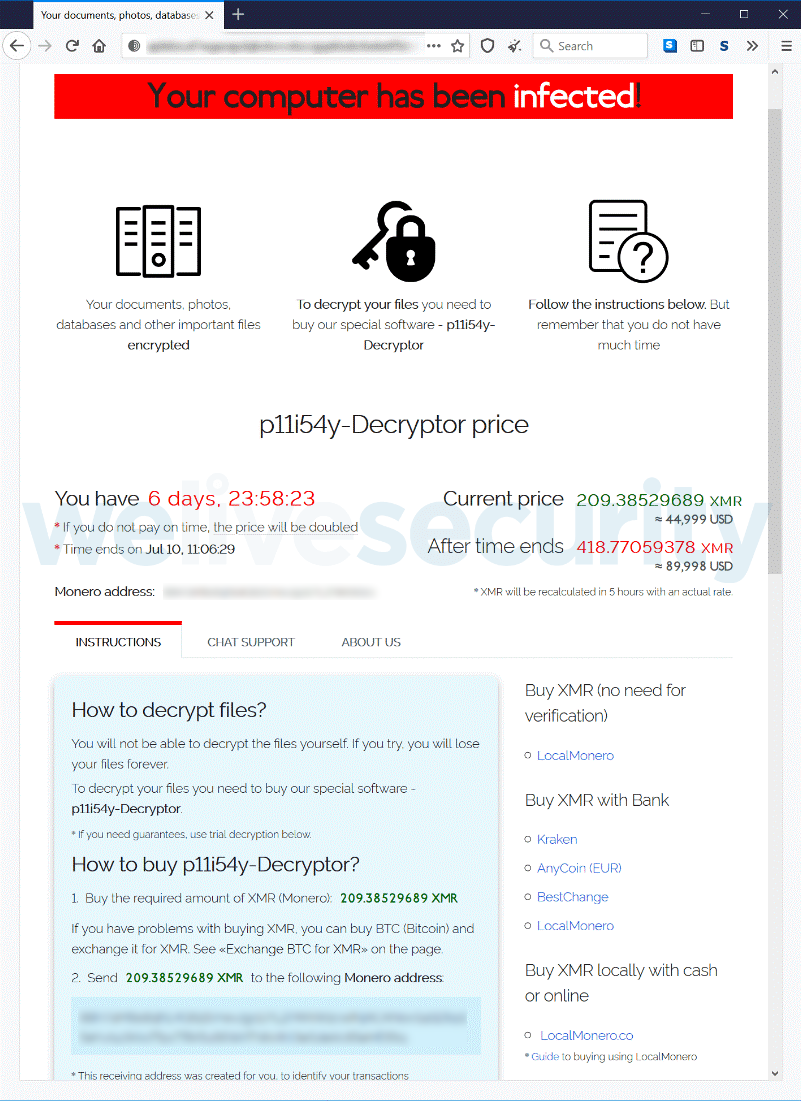
Figure 4. The page to which the victims are redirected
While vendors like ESET detect this malware, there has been a lag between when the affected servers were hit with the attacks and when support teams and software could respond, resulting in early infestations having time to do their damage.
There are several places where forthcoming information is being disseminated, including the security industry rallying, in real time, around helping customers in whatever way possible.
If you have servers that may be affected, it is critical to keep up with news as it emerges and shut down potentially vulnerable machines, or at least isolate them from the network until more information becomes available. Kaseya is also posting regular updates on its website.
Indicators of Compromise (IoCs)
The following files are associated with the Win32/Filecoder.Sodinokibi.N ransomware:
| Filename | SHA-256 hash | ESET detection name |
|---|---|---|
| agent.exe | D55F983C994CAA160EC63A59F6B4250FE67FB3E8C43A388AEC60A4A6978E9F1E | Win32/Filecoder.Sodinokibi.N |
| mpsvc.dll | E2A24AB94F865CAEACDF2C3AD015F31F23008AC6DB8312C2CBFB32E4A5466EA2 | Win32/Filecoder.Sodinokibi.N |
| mpsvc.dll | 8DD620D9AEB35960BB766458C8890EDE987C33D239CF730F93FE49D90AE759DD | Win32/Filecoder.Sodinokibi.N |






