The COVID-19 pandemic has radically changed the nature of everyday work, forcing employees to do large parts of their jobs via remote access. Cybercriminals – especially ransomware operators – are aware of the shift and attempt to exploit the new opportunities and increase their illicit earnings. ESET telemetry confirms this trend in an uptick in the number of unique clients who reported brute-force attack attempts blocked via ESET’s network attack detection technology.
Before the lockdown, most employees worked from the office and used infrastructure monitored and controlled by their IT department. But the coronavirus pandemic has brought a major shift to the status quo. Today, a huge proportion of “office” work occurs via home devices with workers accessing sensitive company systems through Windows’ Remote Desktop Protocol (RDP) – a proprietary solution created by Microsoft to allow connecting to the corporate network from remote computers.
Despite the increasing importance of RDP (as well as other remote access services), organizations often neglect its settings and protection. Employees use easy-to-guess passwords and with no additional layers of authentication or protection, there is little that can stop cybercriminals from compromising an organization’s systems.
That is probably also the reason why RDP has become such a popular attack vector in the past few years, especially among ransomware gangs. These cybercriminals typically brute-force their way into a poorly secured network, elevate their rights to admin level, disable or uninstall security solutions and then run ransomware to encrypt crucial company data.
The growing number of unique clients who have reported an RDP attack attempt is visible in data gathered by ESET telemetry (see Figure 1).
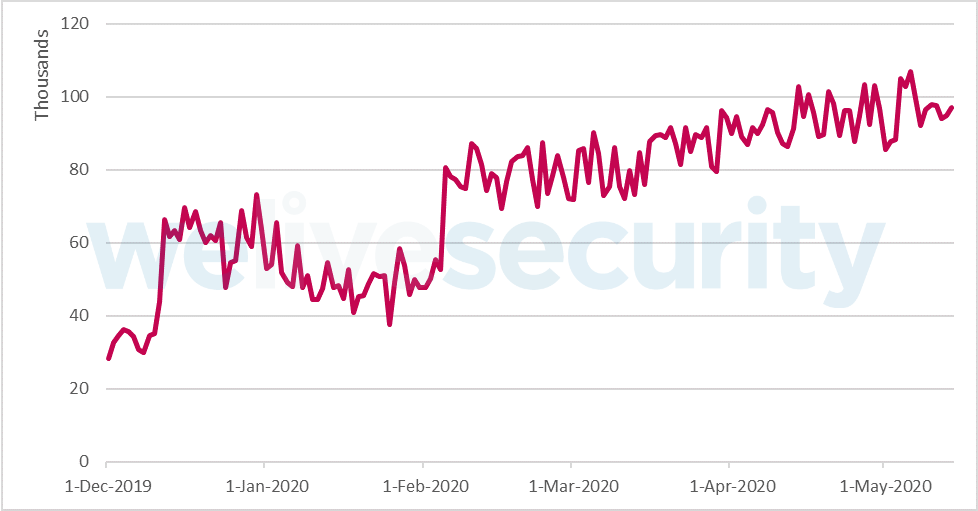
Figure 1. Trend of RDP attack attempts against unique clients (per day), detected by ESET technologies
Brute-force attack protection
To address the growing risks posed by increasing RDP use, ESET researchers have devised a new detection layer that is hidden under the hood of ESET Network Attack Protection and is designed to block incoming brute-force attacks from external IP addresses, covering RDP as well as SMB protocols.
Called ESET Brute-Force Attack Protection, this new layer detects groups of failed login attempts from external environments, which hint at an incoming brute-force attack, and then blocks further attempts. Subsequently, the biggest offenders among these IP addresses are added to a blacklist, which protects millions of devices from future attacks.
The new technology has proven to be effective against both random and targeted attacks. For it to work properly, the RDP option Network Level Authentication (NLA) on server must be enabled.
According to ESET telemetry, most of the blocked IPs in January–May 2020 were seen in the United States, China, Russia, Germany and France (see Figure 2).
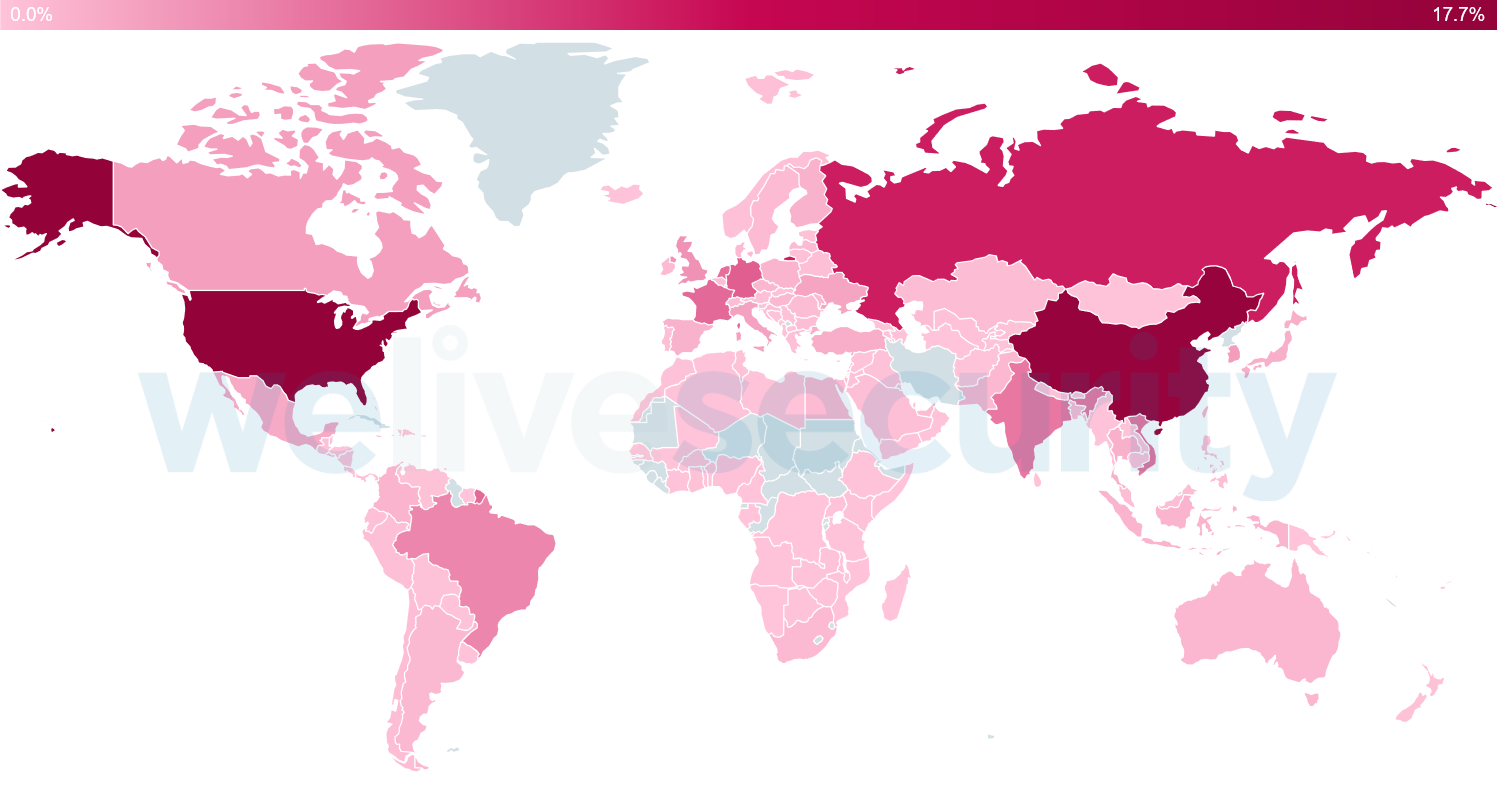
Figure 2. Countries with the largest number of all blocked IP addresses (between Jan 1 and May 31, 2020).
Countries that had the largest proportion of targeted IPs were Russia, Germany, Japan, Brazil and Hungary (see Figure 3).
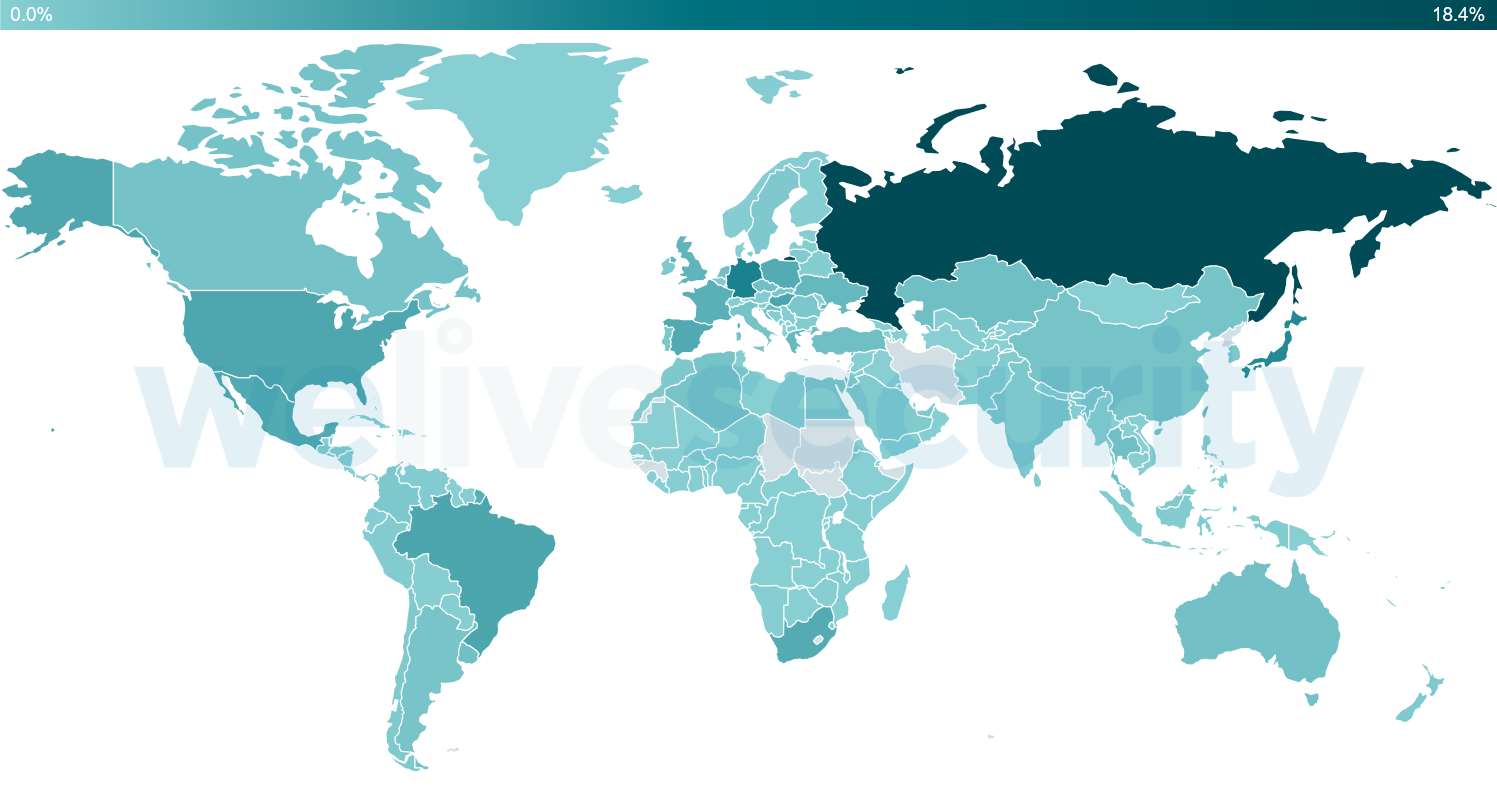
Figure 3. Countries with the most brute-force attacks reported by ESET telemetry (between Jan 1 and May 31, 2020).
How to configure remote access correctly
Yet, even with protective measures such as ESET Brute-Force Attack Protection, organizations need to keep their remote access properly configured:
- Disable internet-facing RDP. If that is not possible, minimize the number of users allowed to connect directly to the organization's servers over the internet.
- Require strong and complex passwords for all accounts that can be logged into via RDP.
- Use an additional layer of authentication (MFA/2FA).
- Install a virtual private network (VPN) gateway to broker all RDP connections from outside your local network.
- At the perimeter firewall, disallow external connections to local machines on port 3389 (TCP/UDP) or any other RDP port.
- Protect your endpoint security software from tampering or uninstallation by password-protecting its settings.
- Isolate any insecure or outdated computers that need to be accessed from the internet using RDP and replace them as soon as possible.
- For a detailed description of how to set up your RDP connection correctly, please refer to this article by ESET Distinguished Researcher Aryeh Goretsky.
- Most of these best practices apply to FTP, SMB, SSH, SQL, TeamViewer, VNC and other services as well.
Ransomware, coin miners and backdoors
Encryption of data and subsequent extortion is in no way the only scenario that could follow an RDP compromise. Frequently the attackers try to install coin-mining malware or create a backdoor, which can be used in case their unauthorized RDP access has been identified and closed.
Other common scenarios following an RDP compromise can include:
- clearing of log files, thus removing the evidence of previous malicious activity,
- downloading and running the attacker’s choice of tools and malware on the compromised system,
- disabling of scheduled backups and shadow copies or completely erasing them, or
- exfiltrating data from the server.
Black hats have been trying to exploit RDP for years, as documented by our blogpost from 2013. Steadily growing numbers of RDP attacks over the past few years have become the subject of numerous governmental advisories including the FBI, the UK’s NCSC and Australia’s ACSC.
This only demonstrates how crucial the security of remote access has become, potentially making or breaking a company’s future. And even if the damage to an organization’s reputation can be managed, there are financial losses, stalled operations and expensive recovery efforts that need to be accounted for. This doesn’t consider the additional costs of potential penalties that can be issued by authorities under data-protective legislation such as GDPR (EU), CCPA (California) or NDB (Australia).
Whether or not there’s a pandemic, businesses should manage the risks posed by wide usage of RDP or other similar services by reinforcing their passwords and by adding other protective layers, including multi-factor authentication and a security solution that defends against attacks based on RDP and similar protocols.





