In recent years, hundreds of millions of homes have become “smarter” and internet-enabled using one of the popular home assistant devices. Despite the efforts of some vendors to develop these devices with security in mind, ESET Smart Home Research Team discovered that even the popular Amazon Echo – the original hardware of Amazon Alexa – was open to Key Reinstallation Attack (KRACK) vulnerabilities. This was also the case for at least one generation of the widely used Amazon Kindle e-readers.
All identified flaws were reported to – and subsequently patched by – Amazon’s security team.
KRACK attacks
In 2017, two Belgian researchers, Mathy Vanhoef and Frank Piessens, made a surprising announcement. They had found serious weaknesses in the WPA2 standard, a protocol that at that time was securing virtually all modern Wi-Fi networks. As described in their paper, KRACK attacks were mostly aimed against the four-way handshake – a mechanism used for two purposes: confirming that both the client and access point possess the correct credentials, and negotiation of the key used for encryption of the traffic.
Vanhoef’s team found that an adversary could trick a victim device into reinitializing the pair-wise key used in the current session (this is not the Wi-Fi password) by crafting and replaying cryptographic handshake messages. By exploiting this flaw, an attacker is able to gradually reconstruct the encryption XOR stream and then sniff the victim’s network traffic.
What was wrong with Alexa?
Even two years later, many Wi-Fi-enabled devices are still vulnerable to KRACK attacks. As demonstrated by the ESET Smart Home Research Team, this included multiple Amazon devices. With Amazon having sold tens of millions of Amazon Echos in the US alone, and tens of millions of Amazon Kindles, this posed a far-reaching security risk.
As part of our research, we tested the 1st generation of Amazon Echo (original hardware of Amazon Alexa) and 8th generation of Amazon Kindle. Our experiments mostly focused on the devices’ resilience against the various KRACK attacks, utilizing the scripts made available by Vanhoef’s team.
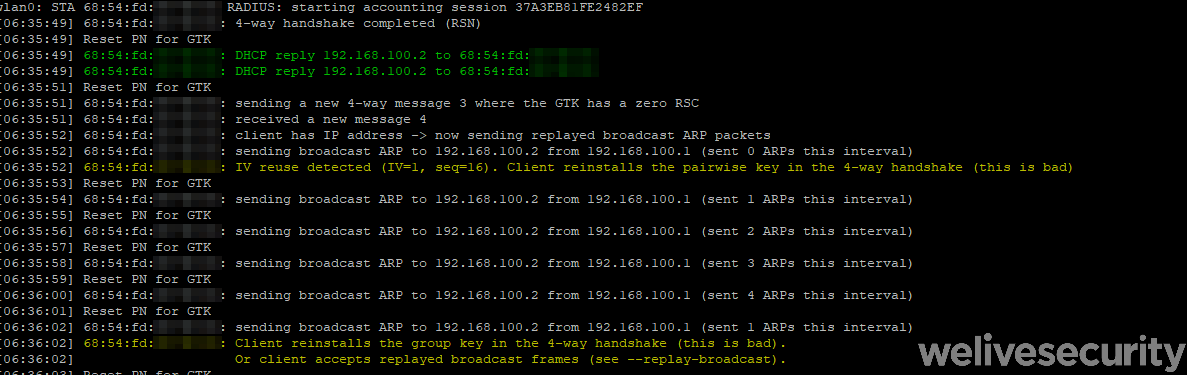
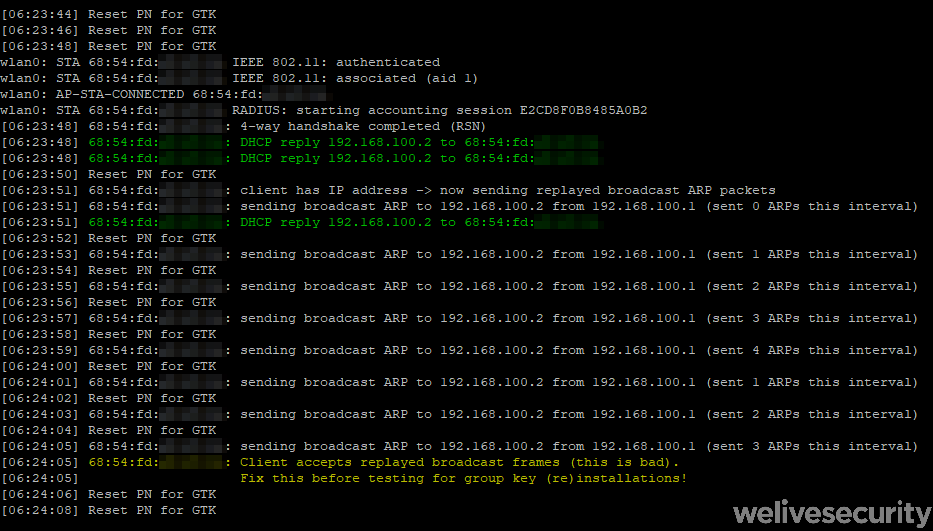
The Echo 1st generation and Amazon Kindle 8th generation devices were found to be vulnerable to two KRACK vulnerabilities. Using Vanhoef’s scripts, we were able to replicate the reinstallation of the pairwise encryption key (PTK-TK) in the four-way handshake (CVE-2017-13077) and reinstallation of the group key (GTK) in the four-way handshake (CVE-2017-13078).
These vulnerabilities are quite severe as they allow an attacker to:
- replay old packets to execute a DoS attack, disrupt network communication or replay attack
- decrypt any data or information transmited by the victim
- depending on the network configuration: forge data packets, cause the device to dismiss packets or even inject new packets
- intercept sensitive information such as passwords or session cookies
Amazon home assistant was also susceptible to yet another network vulnerability, unrelated to KRACK: a broadcast replay attack – a network attack in which a valid broadcast transmission is fraudulently repeated and then accepted by the targeted device. It is a low tier attack that an adversary can abuse to launch a denial of service (DoS) attack or collecting packets for future cryptoanalysis or brute force attack.
Reporting and patching
ESET research reported all identified vulnerabilities in Echo and Kindle to Amazon on October 23rd, 2018 and received acknowledgment of the issue on the same date. On January 8th, 2019 ESET received confirmation that Amazon’s security team had replicated the reported issues, prepared patches and would be distributing them to users in the forthcoming weeks.
To patch CVE-2017-13077 and CVE-2017-13078 vulnerabilities in several million Echo 1st generation and Amazon Kindle 8th generation devices, Amazon issued and distributed a new version of the wpa_supplicant – a software application on the client device responsible for correct authentication to the Wi-Fi network.
Conclusion
The ESET Smart Home Research Team found that Amazon Echo 1st as well as Amazon Kindle 8th generation devices were susceptible to various KRACK attacks. We have reported all the identified issues to the manufacturer for patching.
It should be noted that KRACK attacks – similar to any other attack against Wi-Fi networks – require close proximity to be effective. This means the attacker and victim devices both must be in range of the same Wi-Fi radio network for the compromise to take place.
Attacks against Amazon – and presumably other – devices are also unlikely to significantly affect the security of the information sent over the network. This is thanks to the bulk of the sensitive data being protected by additional security measures above the standard WPA/WPA2 encryption, namely HTTPS using TLS encryption.
The exploits described above affect solely the security of WPA/WPA2. If successful, the effect would be similar to the victim using an unprotected Wi-Fi network. Thus, the practical impact would mostly pertain to data not properly protected by other network layers such as TLS – or when combined with other exploits – and are beyond the scope of this article.
In any case, we advise all Amazon users to verify – via their Echo app and Kindle settings – that they are using the latest Echo and Kindle firmware.
Acknowledgements to ESET Security Awareness Specialist Ondrej Kubovič for his help with this article.