Mobile security plays an increasingly important role in protecting information assets for both home and corporate users. In fact, with the advent of the Internet of Things and the thousands of non-traditional devices that are controlled by mobile applications, the security of our phones becomes increasingly relevant to protect the computers they connect to.
Therefore, throughout this publication we will conduct an analysis of the mobile security landscape based on statistics obtained during the first six months of the year, to assess what are the new trends in relation to the 2018 mobile security report.
Android Security
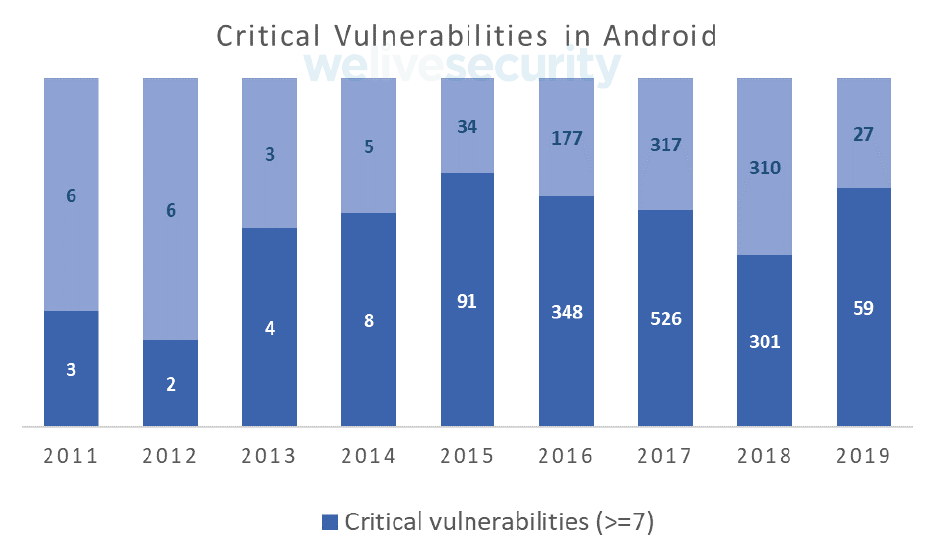
Up to June of this year 86 security bugs affecting Android have been published. In 2018, 611 CVE vulnerabilities were listed (for the whole year). With this data, it seems that in 2019 the number of vulnerabilities will decrease abruptly, compared to previous years.
However, 68% of the bugs published in 2019 were deemed critical and 29% of them allowed malicious code to be executed. This is a considerable increase over past years, where the percentage of serious bugs was lower. Therefore, it is crucial that users install security patches promptly to avoid being affected by serious vulnerabilities such as those patched by Google last July. In particular, much was said about the vulnerability CVE-2019-2107, capable of violating computers by playing videos on the victim computer, a description that reminds us of the past vulnerabilities Stagefright and Metaphor.
In terms of vulnerabilities, it is interesting to note that 90% of Android devices use versions prior to Android Pie, while 74% of Androids do not even run Oreo, according to the Android developer's platform. This could expose outdated phones to major bugs that require architectural changes to the system to be repaired.
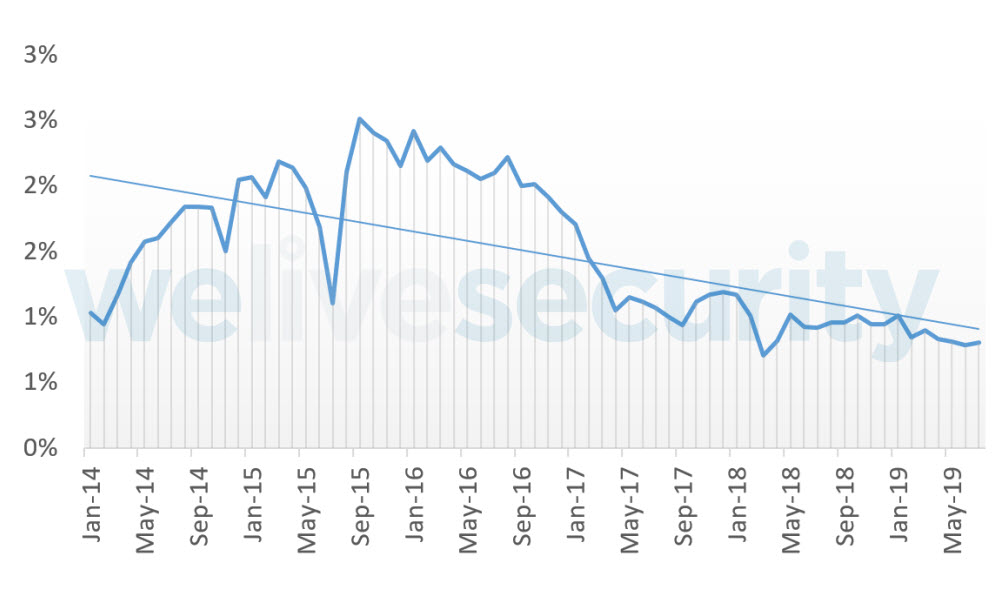
Good news: the number of malware detections decreased 8% over the first half of 2018 and 10% over the second half of last year. This might be a result of efforts by Google and security researchers to detect threats and prevent their spread.
Accompanying the decrease in the number of detections, the average number of new malware variants for Android has also decreased to 240 new variants per month compared to 300 new variants found in previous years. Another interesting fact is that Android turned out to be the architecture fourth from the top of the list of OSes with the most new malware variants, after Win32, MSIL and VBA.
One of the types of malicious code that had experienced the greatest growth during 2018 was cryptocurrency miners. An example is the Android/Coinminer. Detection of these threats has increased by 72% compared to the previous year. Fortunately, detection of this malware family has decreased by 78% in the first half of 2019.
Despite this decrease, cryptocurrencies are still in attackers' sights. Another of the methods they use to obtain them is through the theft of credentials to access online wallets through Trojans involved in the Google Play Store, as happened with these recently discovered fake cryptocurrency apps.
Meanwhile, Android banking malware has also made a name for itself. Since its inception, the number of new variants of mobile spyware and, particularly, Trojans dedicated to the theft of financial data, has been increasing. Variants of Cerberus, a malware that overlay screens to steal bank credentials, was recently sold through social networks.
With respect to this common phenomenon of malware propagation in the official app store, a study developed by ElevenPaths analyzed the length of time malicious apps remained in Google Play and revealed that these malicious apps were available for download 51 days on average before being eliminated. Some of these malicious applications were even available for up to 138 days.
For its part, Android ransomware has once again shown an advance in its complexity. From our laboratories we discovered Android/Filecoder.C: a variant that uses both symmetrical and asymmetrical encryption and is spread through SMS to the team's contact list. This represents a leap in code complexity compared to older ransomware families such as DoubleLocker.
In the first half of 2019, ESET telemetry showed malware for Android concentrated globally in Russia (16%), Iran (15%) and Ukraine (8%). The first Latin American country to appear in the international rankings is Mexico (3%) in sixth place, followed by Peru (2%) in tenth place.
iOS Security
For iOS, 155 vulnerabilities have been discovered so far in 2019, representing a 25% increase compared to 2018 and almost double those found in Android during the current year. We can therefore expect that the number of vulnerabilities for 2019 will exceed the figure obtained in 2018. However, the percentage of high critical failures is lower than Android, around 20%.
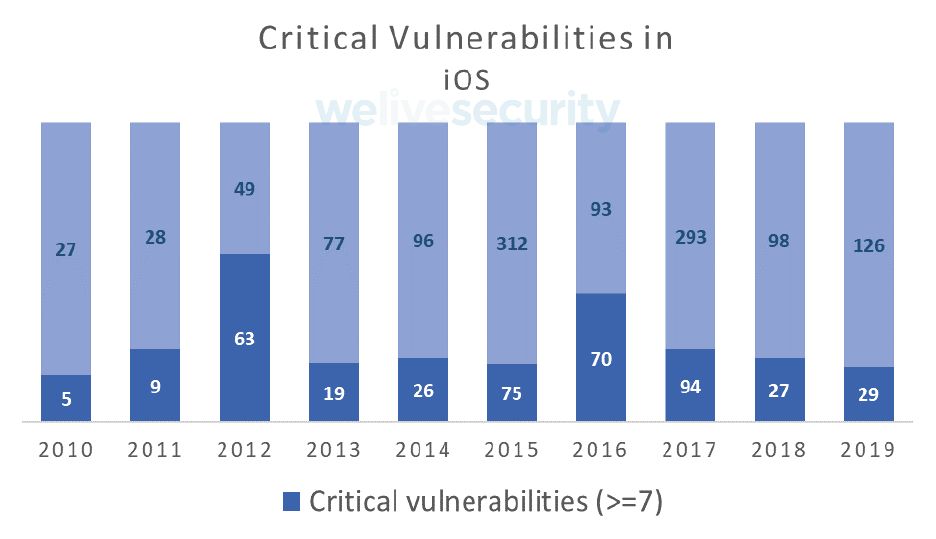
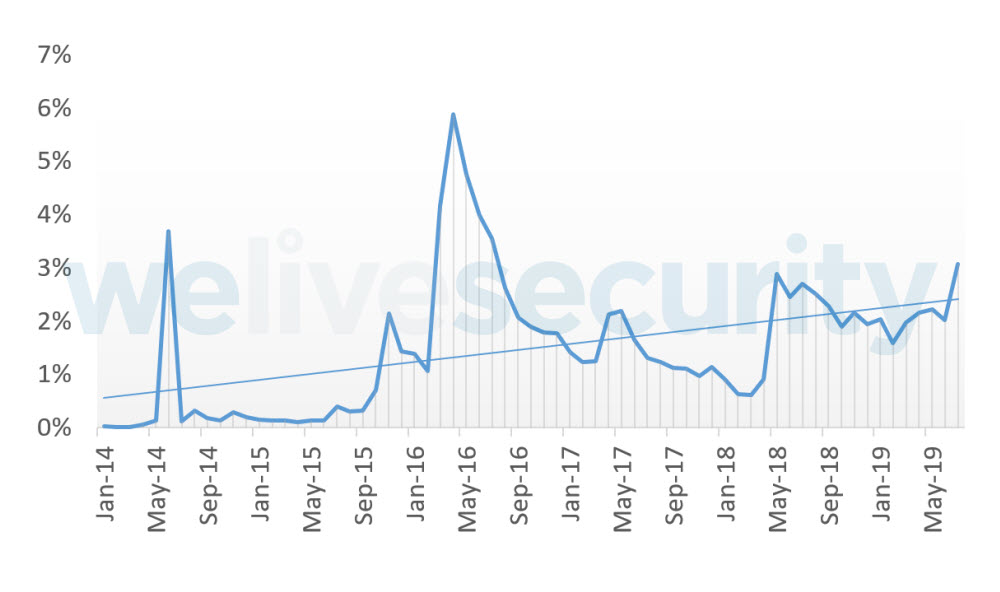
On the other hand, malware detection for iOS increased 43% over the first half of last year. The number of new malware variants remains low, indicating that cybercriminal's interest continues to rest on Android, where the largest number of users are found.
As for the geographical distribution of these detection, they are mainly concentrated in China (75%), India (7%) and Taiwan (4%). In this sense, it is interesting to note the appearance of India in the top three, displacing Hong Kong.
In this first half of the year, Apple's mobile phones were also subject to vulnerabilities that endangered their users, such as the deployment of versions that accidentally reopened previously corrected bugs and that allowed the generation of a jailbreak for version 12.4. Another example was the spying bug in the FaceTime app that allowed it to be easily exploited to spy on third parties.
Malware was not absent from this operating system either and massive spyware infections appeared around the world. A variant called Exodus caused havoc around April of this year, when several users discovered malicious activity on their computers.
In addition to all these threats created for each of the two most widely used mobile operating systems in the world, we must not forget the multiplatform risks associated with the use of third party platforms. The vulnerabilities found in user applications can be as dangerous as those in the OS, as exemplified by the recently discovered WhatsApp flaw allowed quoted text in a message to be altered.
We also have to mention the social engineering attacks that try to seduce users through cyberscams, such as this WhatsApp scam pretending to offer 1000 GB of mobile data. Trendy applications, like FaceApp, are also used by cybercriminals to spread malware and scams online.
Although mobile systems have been designed with a security perspective in mind and are sometimes safer than traditional technologies, we must not forget that the risks are still present. We must always keep in mind that no system is invulnerable and that education and prevention are essential to use mobile technologies safely.