MITRE is a not-for-profit company set up in 1958 whose mission is to “solve problems for a safer world”. This goal is being fulfilled, in part, via the organization’s new curated knowledge base known as MITRE ATT&CK, which stands for “Adversarial Tactics, Techniques, and Common Knowledge”. It is a platform that organizes and categorizes various types of tactics, techniques, and procedures (TTPs) used by threat actors in the digital world, helping organizations pinpoint gaps in their cyber-defenses.
All the information that is collected about attacks is presented in various matrices, such as enterprise, mobile and pre-attack matrices. The Enterprise Matrix, for example, includes the following categories (or tactics):
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
Each category is divided into specific sub-categories (or techniques) corresponding to each type of attack. Also included are details about the technique, examples, references (showing which platforms can be attacked, dates on which the incidents were detected, etc.) and suggestions for the mitigation and detection of the threat.
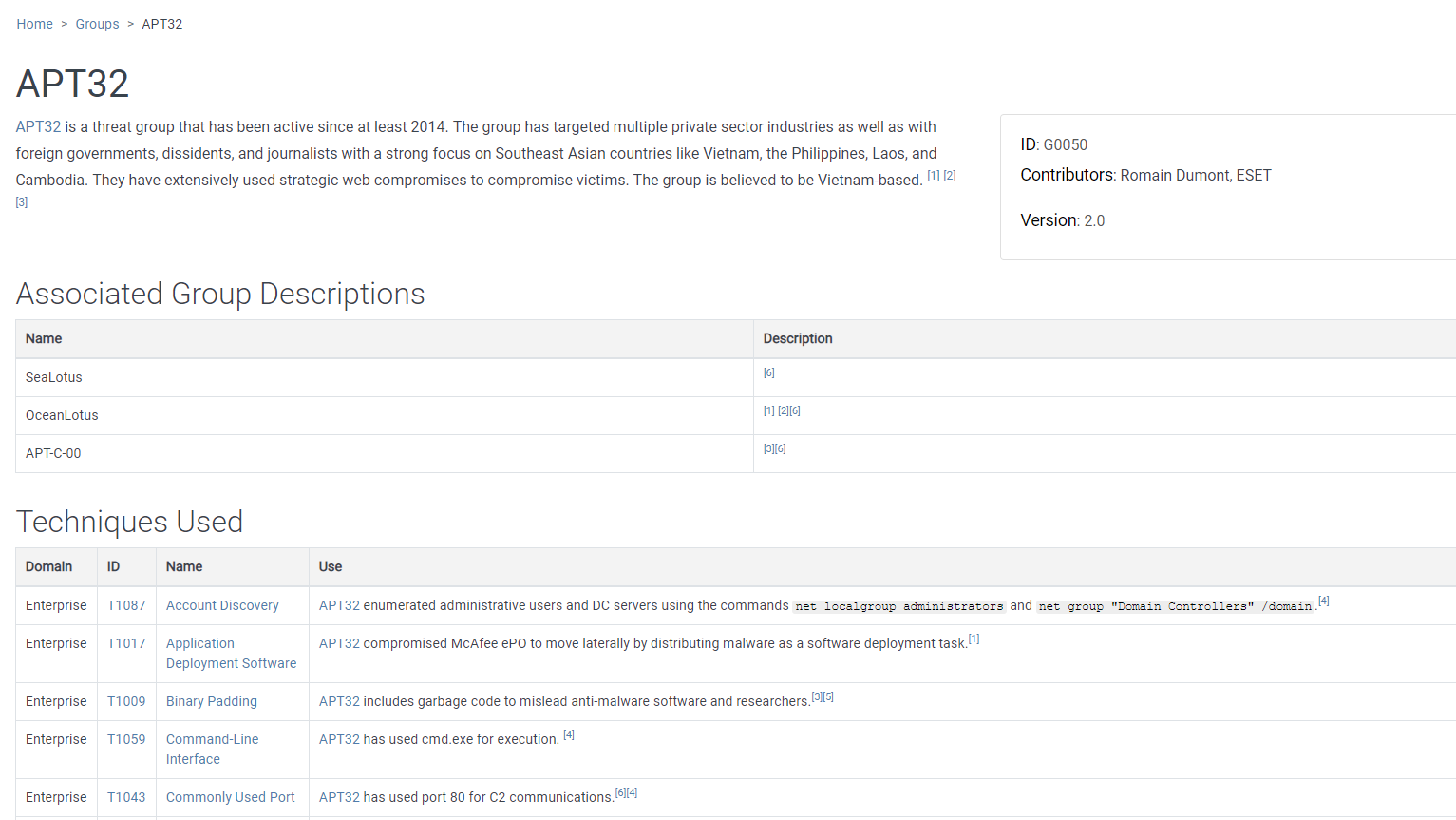
For example, the Spearphishing Link section within Initial Access contains an explanation of what this method of initial access involves. At the time of writing, this section includes 19 examples of threat actors using the technique (Figure 1 shows the entry for Ocean Lotus, aka APT32). Needless to say, this number will increase over time with new reports, complete with explanations and recommendations for how to mitigate these threats and which detection techniques are needed to stay safe(r).
The platform provides a range of information that is useful for analysis of the entire lifecycle of a cyberattack, including the reconnaissance of the target, attack vectors, the actual intrusion, and post-breach actions.
What’s the point?
This type of repository is extremely useful to information security professionals helping to keep them updated on new attack techniques and to prevent attacks from happening in the first place.
Organizations can leverage the framework to create a map of their defense systems. While the framework does primarily describe adversarial behavior, enterprises – specifically those that design security mechanisms – can make the necessary adjustments, taking into account possible attack scenarios and, if necessary, training their staff.
ATT&CK provides details about a large number of actors and groups, including the techniques and tools which they are known for, based on open-source reporting. By enabling hostile behavior to be described in a standardized way, the ATT&CK framework can also be useful for providing intelligence about cybersecurity threats. The framework provides a guide that security teams can compare with existing operation controls with the aim of establishing strengths and identifying weaknesses before threat actors can leverage them.
Creating entries in the MITRE ATT&CK Navigator for specific actors is a good way of visualizing the strengths and weaknesses of one’s environment relating to these actors or groups. It can also be used to categorize tests carried out on an organization’s internal systems, together with their results. This navigator can be used online or downloaded for more stable and long-term use.
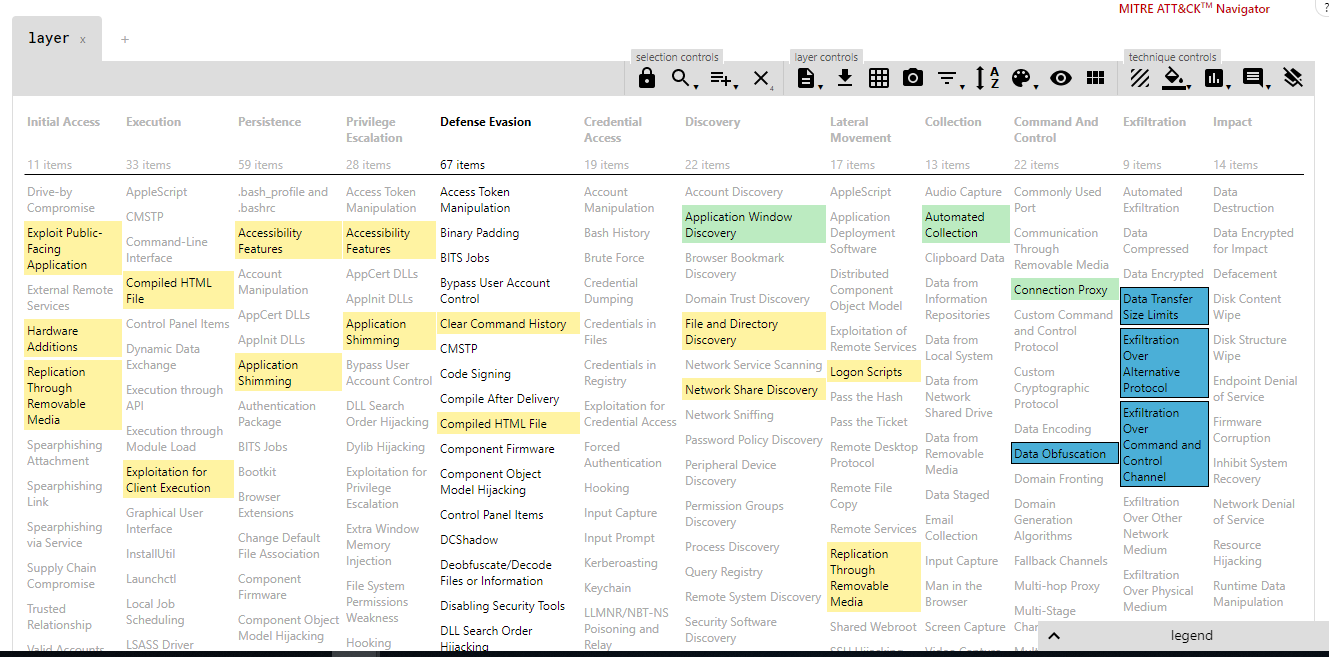
Figure 2. View of the MITRE ATT&CK Navigator and the options for categorizing and organizing the tests conducted and their results
There are additional resources that are linked to ATT&CK and that provide mechanisms to test attack techniques in simulated environments. For example, companies like Verodin, SafeBreach, and AttackIQ provide the ability to carry out an attack simulation. There are some open-source options such as MITRE Caldera, Uber Metta, Red Team Automation (RTA), or Atomic Red Team, to name just a few, which enable attack simulations to be carried out and are also linked to ATT&CK. As always, extreme care must be taken when carrying out these kinds of tests in production networks where the extent of the possible ramifications isn’t fully known. It’s always advisable to use controlled environments that are separated as much as possible from networks with production equipment holding real company data.
In summary, MITRE ATT&CK includes a raft of tools and resources to complement any security strategy. The framework provides organizations with threat intelligence and gives them an idea of how prepared they are to detect and respond to intrusions. That way, they're able to meet their cybersecurity needs and be ready if or when bad actors strike.
Needless to say, ESET Research decided earlier this year to include MITRE ATT&CK matrices in most published malware analyses.