In mid-January, researcher Troy Hunt revealed that a list was floating around in the storage space of the MEGA cloud as well as in several hacking forums. Going by the name of Collection#1, it contains the largest theft of passwords organized into a list to date, comprising more than 700 million email addresses and more than 20 million passwords.
Once we hear about something like this, it is only natural that we might wonder if our own email addresses and/or the passwords we use to access our accounts are among them, or if they have been snatched as part of any other infiltration or security breach. Discovering if our credentials have been robbed or not can also give us an idea of whether the passwords we are choosing when we register with a new service, or when we update our password, are sufficiently secure. In this article we will tell you how to find out if your email address or password has been stolen and to check if the passwords you are choosing are secure or not.
The first service we are going to look at is Have I Been Pwned. This service allows users to check if our email address has been stolen and included in any of the various lists of email and password information circulating online. Furthermore, their database is kept up to date and includes the emails and passwords which were stolen recently.
Upon entering the site a visitor will be able to view a database of more than 6 billion accounts which have at some point been stolen.
We decided to check an email address and saw that unfortunately the address we entered had indeed been stolen at some point. Scrolling down the page, we saw more details of the types of services that compromised the email address that we checked.
As the image of the page shows, the information is ordered by date and by the hacked sites where our information was stolen. For example, there are well-known cases such as the LinkedIn and Taringa data breaches, as well as some of the lists which regularly do the rounds and contain data collated from various websites.
Once we know this, what can we do? It goes without saying that we should change our passwords on the websites mentioned, but as it is also very common for people to use the same credentials for more than one website or service, we need to change the stolen password on all the websites we use it on, because once our password is in someone else's hands, we can't know how many different websites they might try and log in to with those credentials.
When it comes to choosing a new password we recommend another very useful tool on the same website.
This time, the website tells you how many times the password you enter has been used and subsequently stolen.
If we try entering some of the passwords that tend to appear in the rankings of most-used passwords, as incredible as it might seem, we get the following results:
|
Password |
Number of times known to have been stolen |
| 123456 | 23,174,662 |
| password | 3,645,804 |
| qwerty | 3,810,555 |
| 111111 | 3,093,220 |
| 183,778 | |
| 64,811 | |
| a3Z6!B:9#s.2 | 0 |
As we can see, if we try a completely random password, there is a good chance it is not related to any of the data leaks, and therefore it probably has not been used or has not been decrypted. This gives us a good idea of what makes a password secure, or at least less likely to end up in someone else's hands.
Another important thing to keep in mind when choosing a secure password, besides checking if it appears in any database of stolen passwords, is to follow good practices.
- Use a combination of alphanumeric characters
- Use special characters
- It should be at least 8 characters long (and more than 10 will give you even more security against a brute force attack)
- In addition, consider using two-factor authentication, which adds a second layer of security on top of your chosen password.
But the most important thing is for it to be easy for us to remember, because if racking our brains to think of it results in us writing it down on a piece of paper or, even worse, sticking it to the bottom of the monitor—or indeed any of the other myriad solutions we have come across—then all the security measures we have used will prove to be worthless.
For users who use a password manager such as KeePass, which allows you to generate more secure combinations and store them encrypted within the password manager itself, there is the option to compare all the passwords you have stored in it against the Have I Been Pwned database, thanks to a tool published on GitHub.
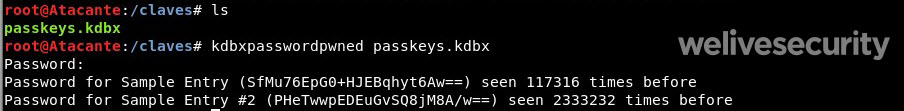
The application is called kdbxpasswordpwned and it allows you to automatically compare all the passwords you have stored in KeePass versus the database of stolen passwords.
While the application is aimed at users with above-average technical knowledge, the following step-by-step instructions should help make it simpler to use.
First, install the application on your system (which must already have Python installed) by using the following command line:
$ pip install kdbxpasswordpwned
Once installed, go to the directory where your .kdbx file is located (.kdbx is the file format for the KeePass password manager) and run the following command:
Kdbxpasswordpwned passkeys.kdbx
As you might expect, it will ask you for the password to your encrypted file, so it can then compare each of the passwords that you have stored in the manager. In this example, we can see that two of the sample passwords which we have stored have come up as hits. So, if these were real passwords, this should prompt us to go ahead and change them immediately on the services where we use them.
And to give one last tip in this post (because it is always worth paying attention to what cybercriminals do with the information they obtain), we should be wary if we receive emails in which the sender tries to extort money out of us on the grounds that they have our passwords. At the ESET Lab, we have seen that fake sextortion campaigns are still taking place, in which the recipient is sent an email containing their password in the message (either in the subject line or in the first few lines of body text) and is asked to pay an amount of money.
Remember to change your passwords regularly, even if the applications and services you use don't ask you to, and use two-factor authentication on the services that allow it. By doing so, you can keep your personal data more secure and reduce the chances of someone else gaining access to it.