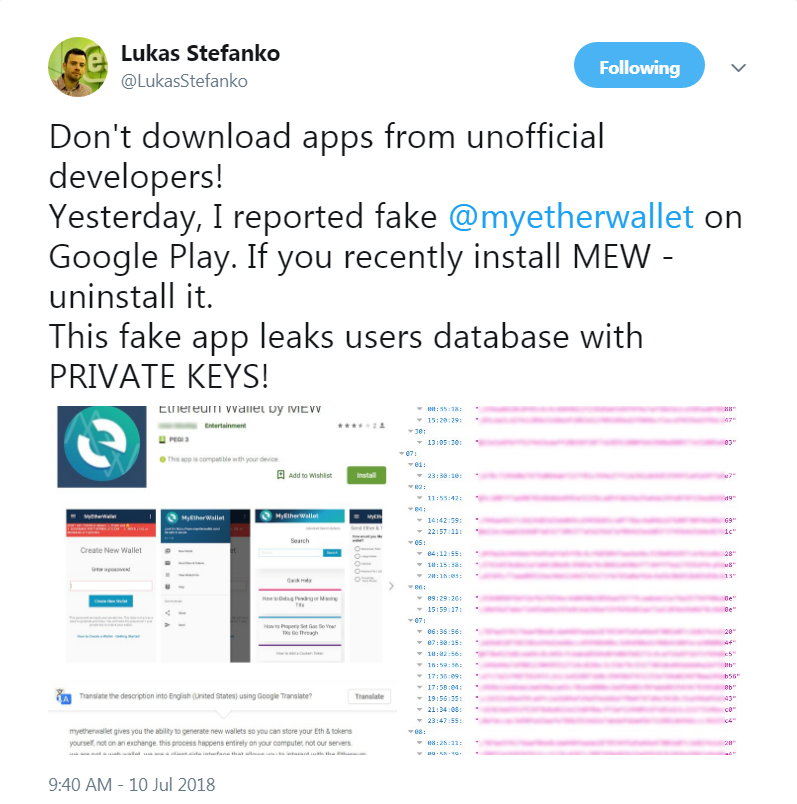
Another set of fake banking apps has found its way into the official Google Play store. Claiming to increase the credit card limit for users of three Indian banks, the malicious apps phish for credit card details and internet banking credentials using bogus forms. What’s even worse, the data stolen from the victims is leaked online, in plain text, via an exposed server.

Figure 1 – The malicious apps on Google Play
The fake apps were uploaded to Google Play in June and July 2018; when ESET notified Google, they were taken down, but by then they had been installed by hundreds of victims. The apps were uploaded under three different developer names, each impersonating a different Indian bank: however, all three apps can be traced back to a single attacker.
How do the apps operate?
All three apps follow the same procedure. Upon launch, a form requesting credit card details is displayed (Figure 2). If users fill out the form and hit “Submit”, they are taken to a form asking for their internet banking login credentials (Figure 3). Interestingly, even though all fields are marked as "required" (*), both forms can be successfully submitted empty – a clear indicator of something fishy.
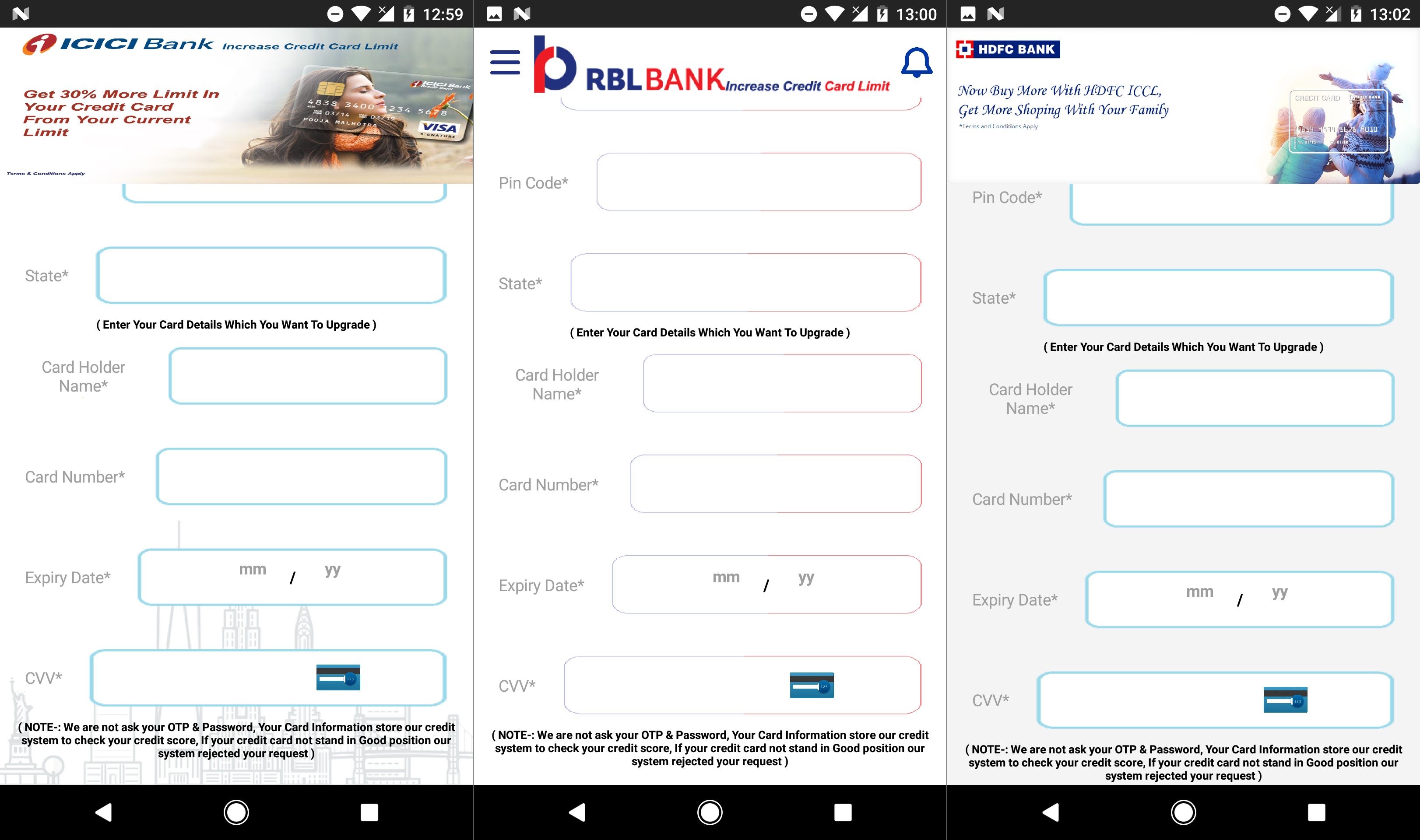
Figure 2 – Bogus forms phishing for credit card details
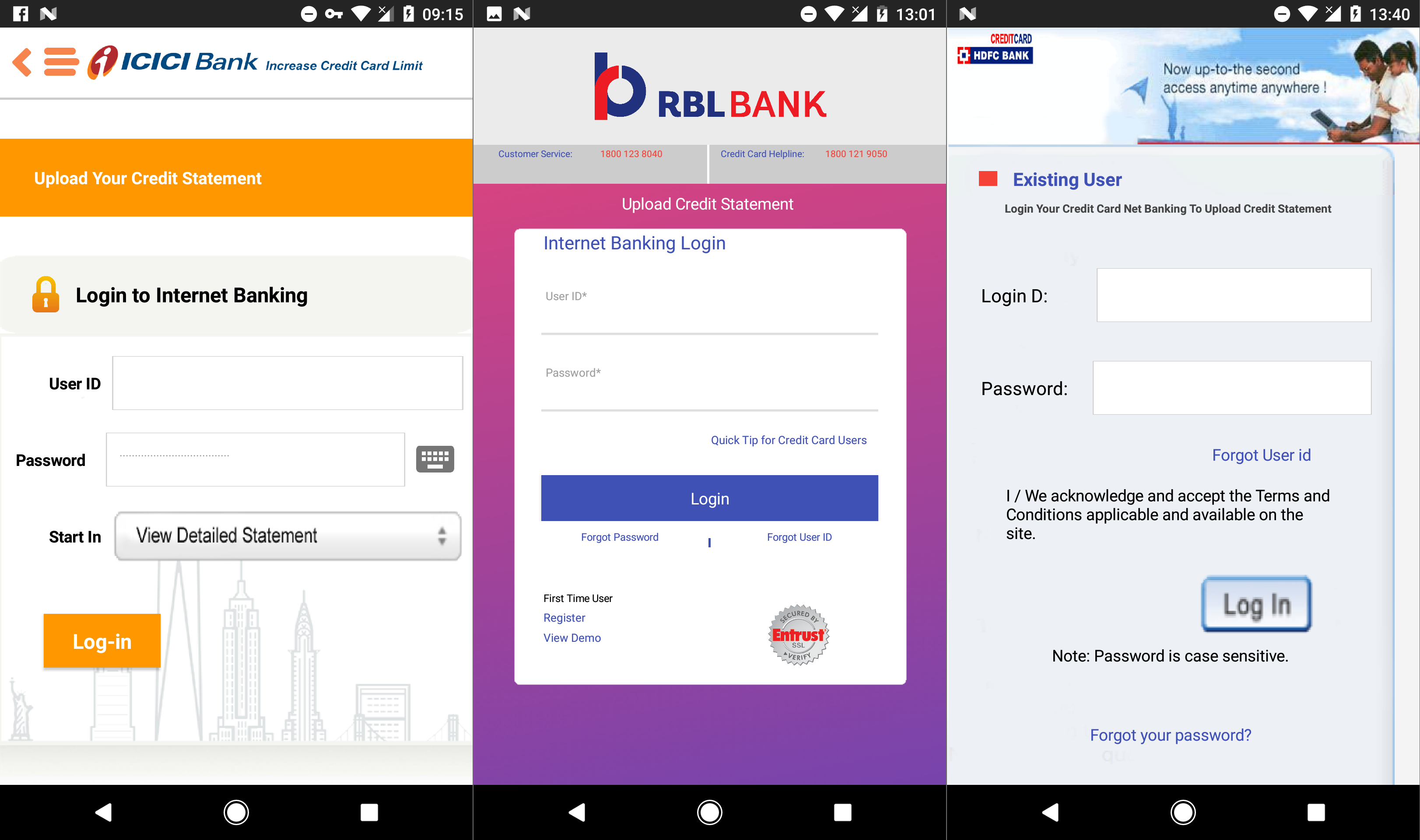
Figure 3 – Bogus forms phishing for internet banking credentials
Clicking through both forms – with or without filling them in – leads users to the third and final screen, which thanks users for their interest and informs them that a “Customer Service Executive” will be in touch shortly (Figure 4). Needless to say, no one gets in touch with the victims, and the app offers no further functionality beyond this point.

Figure 4 – Final screen displayed by the malicious apps
Meanwhile, the data entered into the bogus forms is sent in plain text to the attacker’s server. The listing of the stolen data on that server is accessible to anyone with the link, without requiring any authentication. For the victims, this amplifies the potential damage, since their sensitive data is not only at the attacker’s disposal, but potentially available to anyone who comes across it.
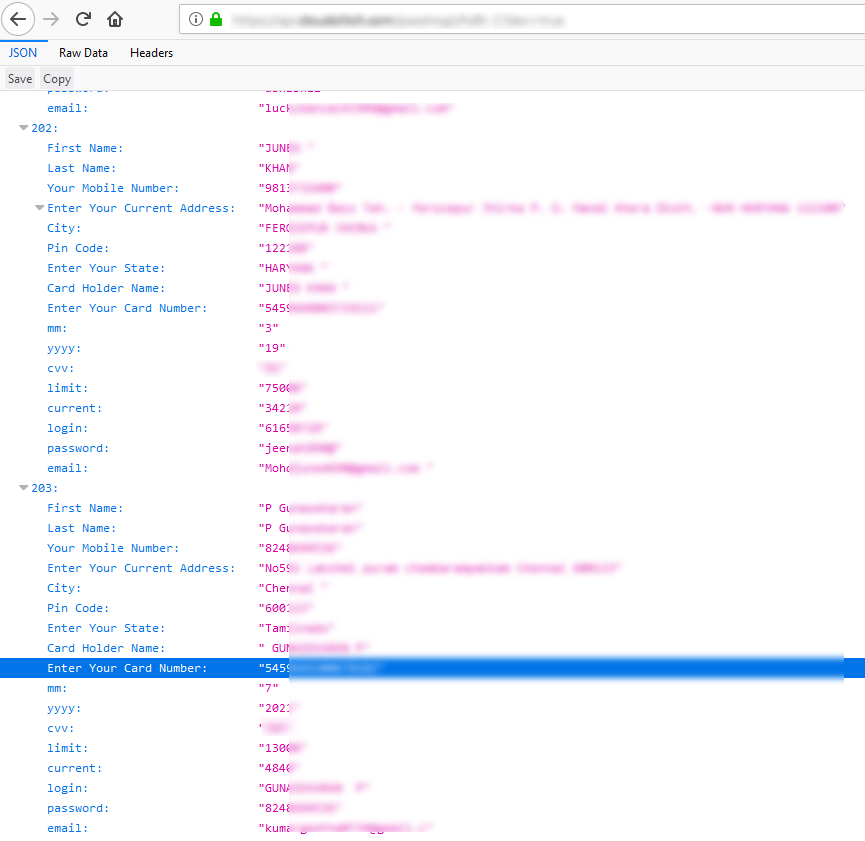
Figure 5 – Stolen banking data available in plain text on the attacker’s server
Just recently, we warned against another malicious app leaking stolen information for anyone to see – a fake MyEtherWallet app, exposing the private keys to victims’ wallets. These discoveries highlight the need for extreme caution when downloading apps related to finances – be it money in the traditional sense of the term, or cryptocurrencies.
How to stay safe
If you’ve installed and used any of these malicious apps, we advise you to uninstall them immediately. Check your bank account for suspicious activity and change your credit card pin code as well as your internet banking password.
To avoid falling victim to phishing apps, we recommend that you:
- Only trust mobile banking apps if they are linked from your bank’s official website
- Never enter your sensitive banking information into online forms if you aren’t sure of their security and legitimacy
- Pay attention to number of downloads, app ratings and reviews when downloading apps from Google Play
- Keep your Android device updated and use a reliable mobile security solution; ESET products detect these malicious apps as Android/Spy.Banker.AHR
Targeted banking apps (legitimate)
| App name | Package name |
|---|---|
| iMobile by ICICI Bank | com.csam.icici.bank.imobile |
| RBL MoBANK | com.rblbank.mobank |
| HDFC Bank MobileBanking (New) | com.hdfc.retail.banking |
IoCs
For the time being, we won’t be publishing more specific IoCs than the app identifiers, in order to avoid further exposing leaked victim data.