Since early 2018, some of your WhatsApp contacts may have sent you a very interesting offer for sport shoes.
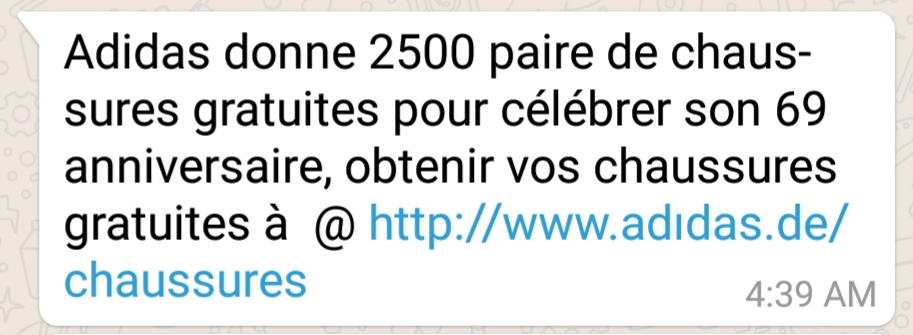
The message suggests that Adidas is offering 2,500 pairs of shoes to celebrate its 69th anniversary, followed by a link from which to obtain the promised item. If you take a closer look at the link in the image, you can see that there’s no dot above the short vertical line that should be the letter “i”. This is a homoglyph (often referred to as homograph) attack, incorporating a link that looks legitimate but is actually spoofed by replacing one character with another that looks the same to the unwary eye. This kind of attack is not new, with several articles covering the subject such as welivesecurity, thecomputerperson and Doron Segal on Medium. The structure of the message is not new either. A few similar campaigns were observed in 2016.
This phishing attack appeared fairly well structured and even had some geolocation-based redirections. As it piqued our interest, we dug a bit further.
Analysis
When browsing the website from the spammed WhatsApp message, a few checks are made to ensure that the request is made from a mobile device such as a smartphone. This is achieved by some JavaScript code that checks the browser’s window orientation property and the width of the screen. If these checks fail, the user is redirected to http://neuewfarben[.]com/404 which is just a page with a 404 error.
Should the mobile device checks succeed, the website then obtains geolocation data for the visitor’s IP address, and depending on the country the visitor may be redirected. The following list maps the country and the redirection link.
| Country | Actual Link | Representation |
|---|---|---|
| Norway, Sweden | www.xn—addas-04a[.]de/no.html | www.adıdas[.]de/no.html |
| Pakistan, Nigeria, Kenya, Macau | www.sweetfinalz[.]com/ | www.sweetfinalz[.]com |
| United States | www.xn—disneycruse-7zb[.]com | www.disneycruıse[.]com |
| Netherlands, Belgium | www.xn—addas-o4a[.]de/nl.html | www.adıdas[.]de/no.html |
| India | www.xn—jetarways-ypb[.]com | www.jetaırways[.]com |
If the visitor does not come from one of these countries, the Adidas phishing scheme leaves the starting block.
As you can see from the list above, Adidas is not the only "bait" in this phishing campaign. We will use it as an example in this article, but other brands are victims of this attack as well. The same scheme is used for different products.
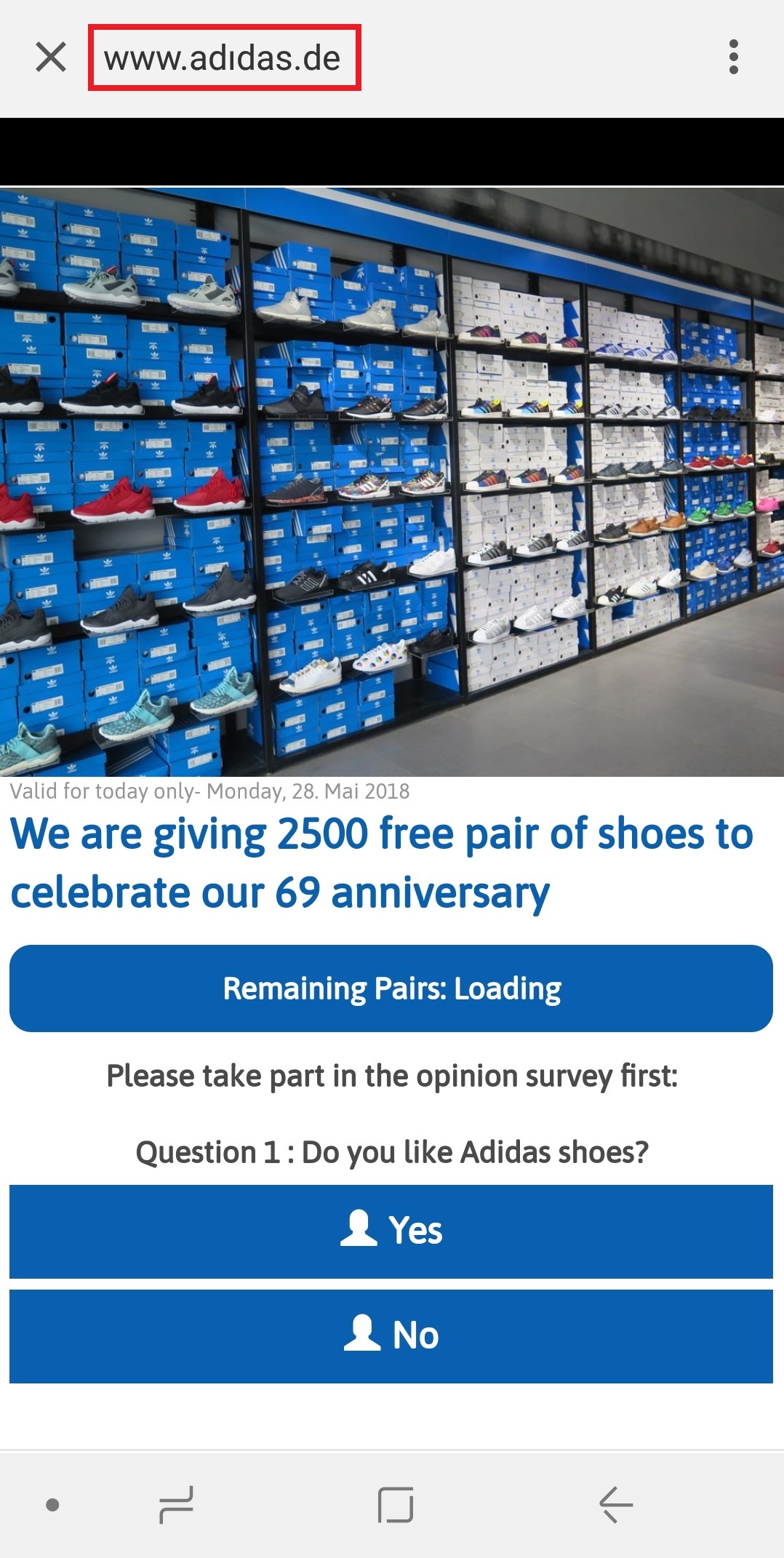
After being redirected, visitors see a four-question survey. Whatever the victims answer, they are rewarded with a message saying that they are "qualified" to get a free pair of shoes. Of course, they are told that they must share this wonderful offer to their friends on WhatsApp to get the "prize".
When tapping the WhatsApp share button, the victims see a list of their contacts, from which to choose further recipients of this “offer”. If they simply close this menu, it still counts as a “share”. If they repeat this routine 20 times, they’ll still be able to click the claim button without really sharing the “offer”. This behavior is possible because there is no way for the web page to know if the share was successful or not. Or even better, if you press your browser’s or mobile’s "return" button, you are redirected straight to the next stage.
A chain of redirection is then performed to get the victim to another page. We have observed the following redirection chain:
- http://www.xn--addas-o4a[.]de/final.html
- http://track.voltrrk[.]com/0e548085-58e7-40e1-beba-b8940d6a8edc
- http://redirect.dringston-enquency[.]com:80/redirect?target=BASE64aHR0cDovL3d3dy5wYWlyb2ZzY2h1aGUuY29tL2VuLmh0bWw&ts=1527005723770&hash=qcAp4Brw4y8SYgfUl1r_-pb4RQxIqqiFf6sLXB9OU4E&rm=D
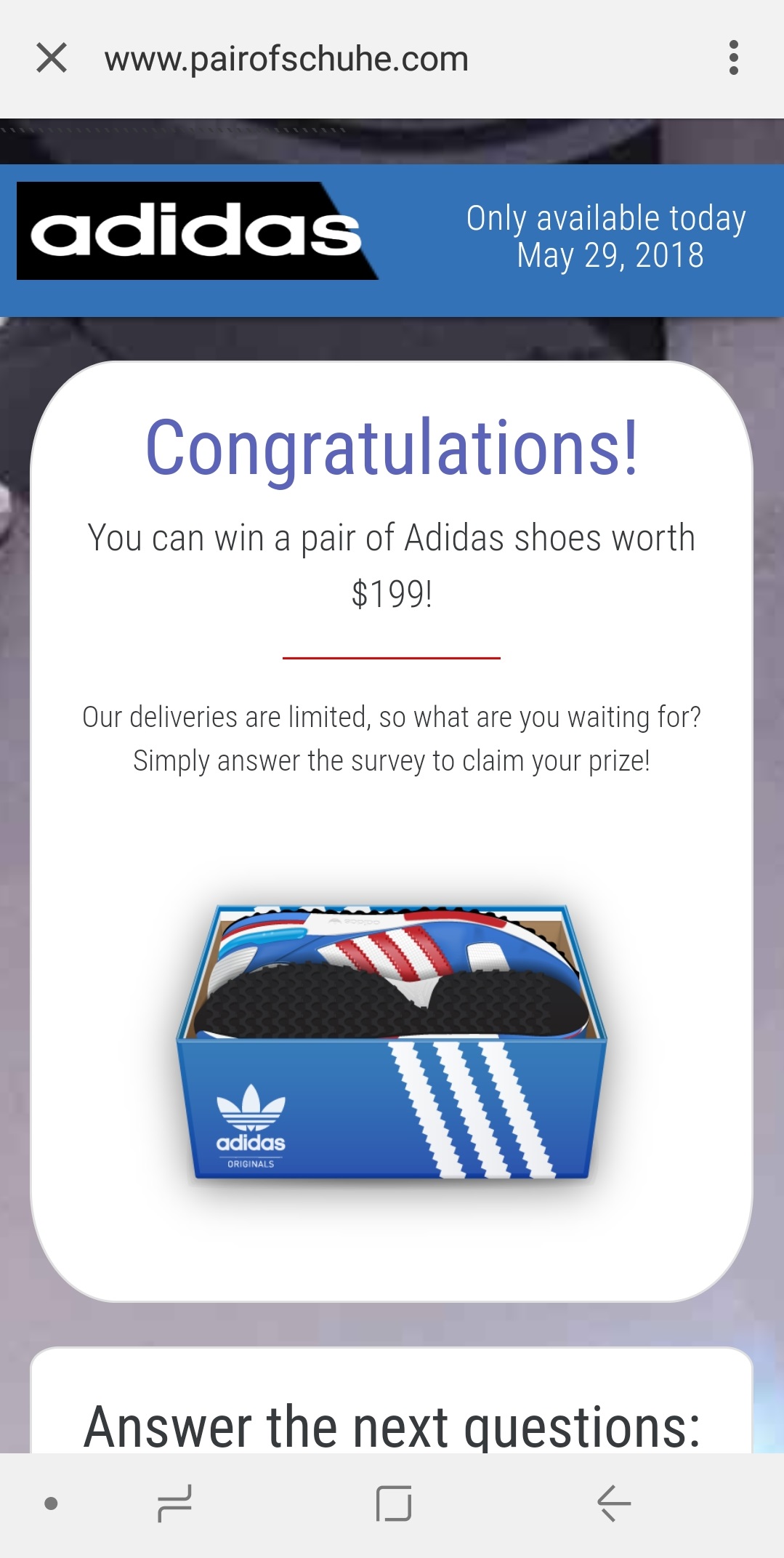
- http://www.pairofschuhe[.]com/en.html
Victims have a few (obvious?) questions to answer and are also told they have to share the ad on Facebook… or not! Here again, if victims just click on the share button without actually sharing, they will still (supposedly) be able to claim their shoes for $1.
Clicking the "claim for 1$" button results in victims following a new chain of redirections to the last stage of this scam. The following chain of redirection has been observed:
- http://www.pairofschuhe[.]com/go
- http://track.voltrrk[.]com/c9d22249-b14d-4ddb-bc6c-59e43841cd0f
- http://redirect.dringston-enquency[.]com:80/redirect?target=BASE64aHR0cHM6Ly90cmNrci5yb2Nrcy8_YT0yMTQ5JmM9MTI4NjMmczI9d1NSNUpJTUY1VEQ0OVAzRTFSQUpIOU5B&ts=1527011060929&hash=-eeKnNtq6vinT3e8YR39UXs0Fzna-Cp4z2lTlLFhuJU&rm=D
- https://trckr[.]rocks/?a=2149&c=12863&s2=wSR5JIMF5TD49P3E1RAJH9NA
- https://redirector[.]cc/go/5312?transaction_id=12750-197928458&pub_id=2149
- https://promoztooffer[.]com/86088686/86088686_lp?lp_rid=5312&lp_sid=31&lp_did=6&lp_aid=28&forceLang=EN&a_p=33&transaction_id=12750-197928458&pub_id=2149&te=1527011136
A last form is presented to the victims, asking for their contact details. There’s also something worth noticing on this page: in the footer, one can see the following message:
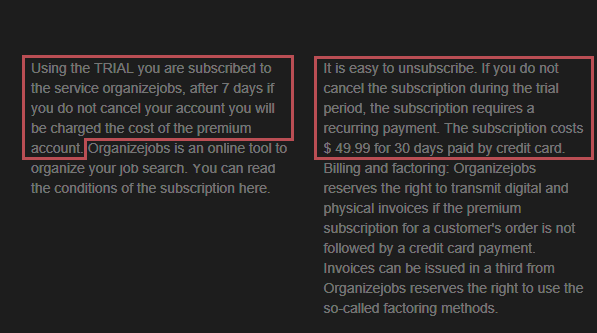
The completion of this purchase will subscribe you to the "organizejobs" service and they will charge you the cost of a premium account, which is $49.99 per month. This service has already been recognized as a scam since at least late 2017: see this article from Online Threat Alerts. After reading some comments from victims, it seems they never received what they were promised.
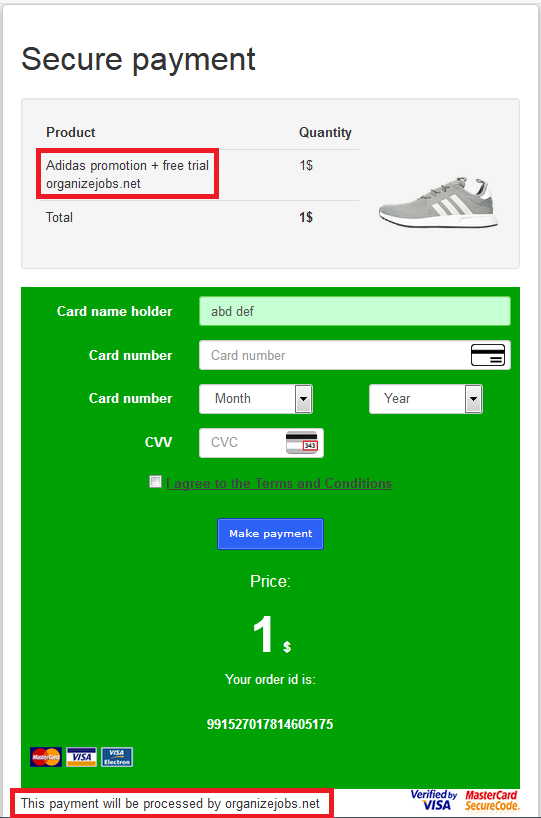
The payment page is also misleading as it says "free trial organizejobs[.]net" but $50/month doesn’t sound “free”.
Once again, there’s something fishy here. At the bottom of the page, one can see that the payment will be processed by organizejobs[.]net – which seems odd, as that site apparently has nothing to do with a shoe company.
In the end, victims will pay $1 for a pair of shoes without being able to choose the model or the size, and which the previous experience of others suggests will never be received. On top of that, victims who didn’t notice the "TRIAL" subscription text will be charged $50/month 7 days after the payment.
Punycode and homoglyphs
In 2003, RFC 3492 introduced Punycode (since updated in RFC 5891); a way to encode non-ASCII characters in domain names to support Internationalized Domain Names (IDNs). This allowed all Unicode characters to be used in domain names, assuming that the top level domain allows it. Scammers saw an opportunity to create spoofed domain names very similar [or 'at first glance identical'] to a genuine brand's domain. Phishing attacks abusing this legitimate functionality start by finding a homoglyph, a character having a similar shape to another one. In the current case, the "i" of “Adidas” was replaced by "ı" (Unicode’s Latin Small Letter Dotless I; codepoint 0131). We were able to find other domains used by this group. This is a non-exhaustive list of similar domains as of May 29, 2018:
| Punycode encoding | Representation |
|---|---|
| xn—costo-7xa[.]com | costċo[.]com |
| xn—superndo-xkb[.]com | superındo[.]com |
| xn—disneycruse-7zb[.]com | disneycruıse[.]com |
| xn—jetarways-ypb[.]com | jetaırways[.]com |
| xn—bgbazaar-tkb[.]com | bıgbazaar[.]com |
| xn—garuda-indonesa-llc[.]com | garuda-indonesıa[.]com |
| xn—southwes-wyb[.]com | southwesŧ[.]com |
| xn—mlka-lza[.]com | mılka[.]com |
| xn—starucks-hpd[.]com | starɓucks[.]com |
| xn—flysa-xcc[.]com | flysaȧ[.]com |
| xn—costc-bec[.]com | costcȯ[.]com |
| xn—sngaporeair-zzb[.]com | sngaporeair[.]com |
| xn—alitala-wfb[.]com | alitalıa[.]com |
| xn—harbo-p4a[.]com | harıbo[.]com |
A couple of pieces of advice
Apart from the trivial research done by the miscreants behind these scams to find the right homoglyph, they didn’t go to great lengths to make their website look more legitimate. Here are some tips that should help you to recognize this kind of scam:
- Upon receiving such messages, ask the purported senders if they really sent them, as it could have been sent without their knowledge by malware installed on their phone.
- Search the internet for the offer. In this case, several websites mentioned the ongoing phishing attack.
- Use your favorite search engine to get a link to the company website. If the offer is not present on the site then it’s probably a scam. Mtlblog contacted the shoe company which confirmed the scam.
- If at all unsure, do not click any links and delete the message containing them or ignore it until it scrolls off your feed.
In this kind of attack, there may be quite a few details that might arouse a potential victim's suspicions. In this case, from the first page to the last page, there are a lot of things that don’t make sense:
- The first page says “Valid for today only”, not because it’s true, but because an increased sense of urgency tends to reduce the respondent’s cautiousness. In fact, in our testing, the offer was always "available", for as long as the website was up.
- The first page says "Remaining Pairs:" along with a decreasing counter, but if you come back a few minutes later, there will be more shoes. This is another tactic to make potential victims feel they need to act quickly, and hence probably less cautiously.
- The Facebook comment section is also fake. Even without looking at the code, the "comment" and "share" features don’t work. Moreover, if you reload the page, the same comments will reappear.
- Not even a single page describes which style or size is available.
- The small text at the bottom of the page implies that there will be a subscription of $49.99 a month to a company which apparently has nothing to do with the offer. In this case, organizejobs[.]net was already listed as a fraudulent website by signal-arnaques.
Additionally, since the homoglyph attack is a known issue (see IDN in Google Chrome), a couple of mitigation techniques have been implemented in web browsers. Chrome and Firefox try to guess if a domain could be a fraud by checking whether if it contains characters from multiple alphabets. Firefox lets users decide if they want the Punycode syntax to be displayed instead of the interpreted one (about:config and setting network.IDN_show_punycode).
Conclusion
This research demonstrates yet again that phishing attacks are still taking place and continuing to evolve. Of course, there are a lot of similar domains and domain name homoglyph attacks are unlikely to stop, but by being a bit careful it is possible to avoid falling for this kind of deceit.
It's not only web browsers that could prevent this kind of attack — as seen in this article, the medium used to spread this attack is a messaging application. This kind of application should show the Punycode syntax for URLs or at least let the user decide how they are displayed.
If you receive this kind of message, don’t hesitate to report it. You can notify the abused brand and you can report phishing to ESET at http://phishing.eset.com/.
IoCs
| Domain names |
|---|
| xn—addas-o4a[.]de |
| xn—costo-7xa[.]com |
| xn—superndo-xkb[.]com |
| xn—disneycruse-7zb[.]com |
| xn—jetarways-ypb[.]com |
| xn—bgbazaar-tkb[.]com |
| xn—garuda-indonesa-llc[.]com |
| xn—southwes-wyb[.]com |
| xn—mlka-lza[.]com |
| xn—starucks-hpd[.]com |
| xn—flysa-xcc[.]com |
| xn—costc-bec[.]com |
| xn—sngaporeair-zzb[.]com |
| xn—alitala-wfb[.]com |
| xn—harbo-p4a[.]com |
| sweetfinalz[.]com |
| pairofschuhe[.]com |
| track.voltrrk[.]com |
| redirect.dringston-enquency[.]com |
| trckr.rocks |
| redirector[.]cc |
| promoztooffer[.]com |