It took only a few days for the largest-ever distributed denial-of-service (DDoS) attack to be outstripped by an even mightier – albeit not as disruptive – assault.
DDoS mitigation service Arbor Networks has announced that an undisclosed US company has suffered an attack fueled by unsecured internet-facing Memcached servers that clocked in at 1.7 terabits per second (Tbps), beating the previous record of 1.35 Tbps.
Muddying the waters further, ransom notes have been added to this new method of DDoS attacks, reads a report by content delivery network provider Akamai. In yet another development concerning this red-hot type of attack, three instances of proof-of-concept code are apparently available for anyone who may wish to try his or her hand at DDoS attacks co-opting Memcache servers.
Meanwhile, another DDoS mitigation service, Corero, has announced that a vulnerable Memcached server can be “coaxed into divulging user data it has cached from its local network or host”. The company has also announced the discovery of a ‘kill switch’ that it says is capable of stopping a Memcache-fueled deluge of junk traffic.
Higher and higher
Last week, we reported about a barrage of bogus traffic that had struck the code repository GitHub on February 28, taking it offline for a few minutes. The assault peaked at 1.35 Tbps and quickly grabbed the headlines as the largest DDoS attack on record.
Only a few days later, Arbor Networks reported that it had detected an attack that reached 1.7 Tbps. Thanks to adequate safeguards, the target of the latter attack – a customer of a US-based service provider – reportedly suffered no outage.
“The attack was based on the same memcached reflection/amplification attack vector that made up the Github attack,” according to the firm’s announcement.
Therein lies the key feature shared by the two assaults, which are becoming a rapidly emerging trend. They both exploit unsecured Memcached servers, which are designed to speed up web applications and sites. However, the servers require no authentication and are susceptible to abuse as reflectors for amplifying traffic at a targeted service.
To launch an attack – which has come to be dubbed ‘memcrashed’ – the ne’er-do-wells send User Datagram Protocol (UDP) packets with the target’s spoofed IP address to a number of Memcached servers. The servers fire back with a vastly magnified response that bombards the hapless victim. The amplification factor can reportedly be up to 51,200.
Extortion
Money-grubbing attackers have quickly turned the latest type of DDoS attack into a way to line their pockets, serving up ransom demands to a number of targeted services. A combination of DDoS and extortion has been the go-to form of assault for many attackers before.
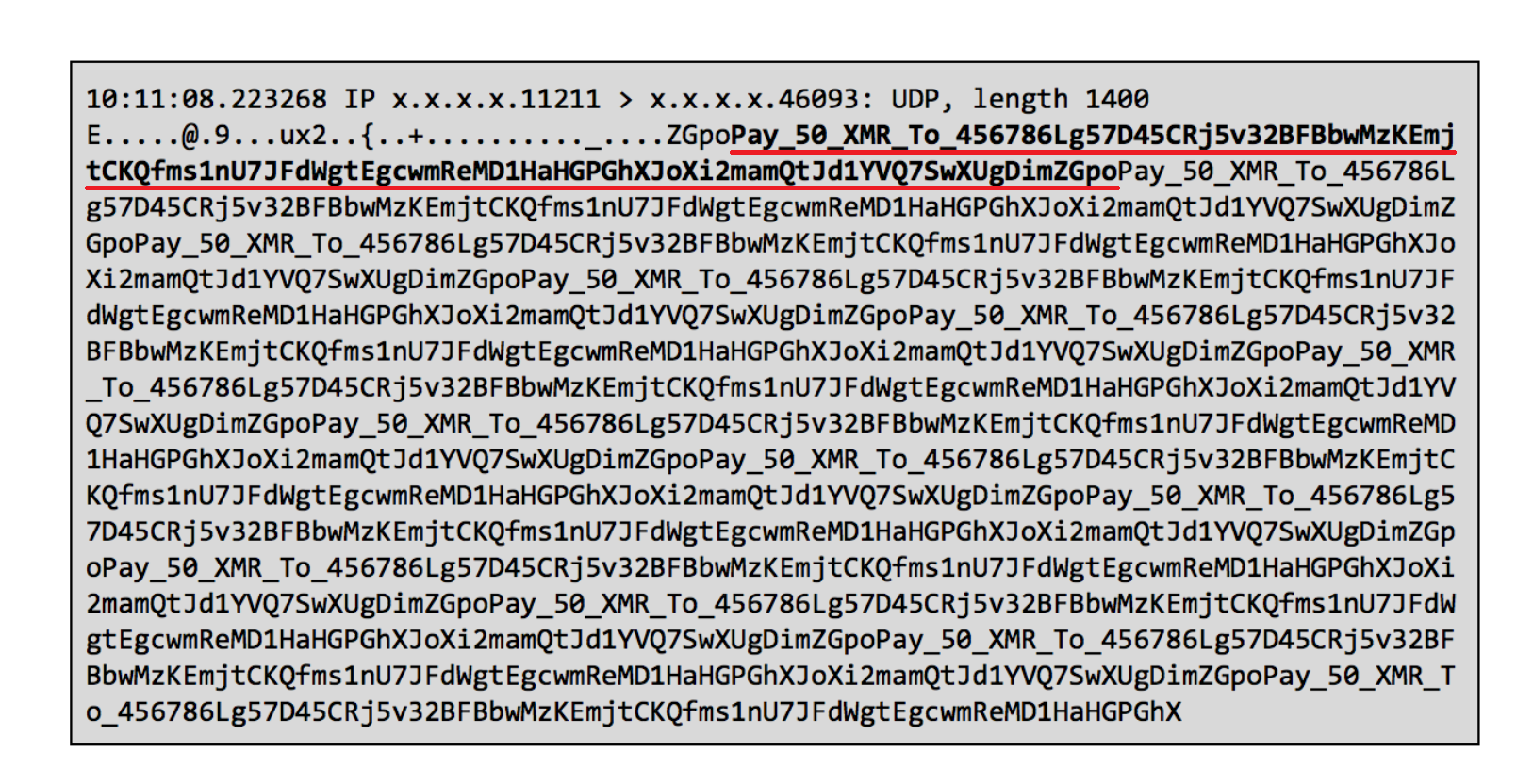
The ransom notes, stuffed within the ingress deluge of malicious traffic and repeated over and over, request the victim to fork over 50 Monero (XMR) to the specified wallet address in order to stop the clobbering. That amount of the digital currency is currently worth over $16,000.
As noted by ArsTechnica, however, all ransom notes that have been reported use the same wallet address and there is no automated way for the attackers to identify which targets have paid and which have not. This only adds to the list of other good reasons for not paying extortionists.
The recommendations for the owners of Memcached servers to address the threat include placing the servers behind a firewall, disabling UDP support if it’s not used, or applying the latest update that disables the UDP protocol by default.
The reports on the record-breaking attacks came merely days after warnings from multiple DDoS mitigation services that they had observed an uptick in the misuse of vulnerable Memcached servers.