Many of the components required to commit cybercrime can be bought and sold online if you know the right part of the internet in which to look. These “dark markets” also enable cybercriminals to monetize the fruits of their larcenous labors, from botnet building to credential theft.
In the first part of our cybercrime update we noted more than a dozen arrests and other law enforcement actions against cybercriminals. In this, the second part of the update, we look at some of the “takedowns” that have hit the cyber-underworld this year, beginning with botnet bashing.
Down with malware spamming
One of the commodities that criminals buy and sell online is the ability to distribute malware using spam. This enables digital nastiness like password-stealers and fake antivirus software to be spread far and wide.
But because no self-respecting internet service providers will allow their systems to be used for spam operations, spammers use your systems instead: they secretly recruit them into “botnets”— networks of compromised computers. These bots can be laptops, workstations, even phones and servers. Botnet activity is coordinated through a form of software known as C2, short for Command and Control.
"Botnets can use tens of thousands of machines at once to spew out spam."
Botnets can use tens of thousands of machines at once to spew out spam. In recent years one of the most notorious botnets was called Kelihos. ESET researchers have previously described some of the characteristics and campaigns wrought by the Kelihos botnet, and its predecessor – known as Storm – in a technical paper: Same botnet, same guys, new code.
Well, in April, the person responsible for Kelihos, a Russian programmer by the name of Pyotr Levashov, was arrested while on vacation in Spain. Levashow has long been on the radar of US cybercrime investigators, having been charged back in 2009 with operating the Storm botnet.
Shortly after the arrest, the authorities moved to disrupt and dismantle Kelihos, blocking malicious domains associated with the botnet to prohibit further infections.
While there are still shady characters who formerly were clients utilizing the services of the Kelihos botnet, the takedown is likely to reduce global spam volumes at least temporarily. Furthermore, a swift conclusion to the Levashov case and a strong sentence (prison time plus asset forfeiture) could encourage some criminal spammers to switch to more legitimate activities.
Deep dark terminology
For those to whom the dark side of the internet is terra incognita, a dark market is a place to buy and sell goods online that is not readily accessible to the public. The FBI uses the following terms to describe this phenomenon. First, there is the Clear Web, the one we’re most familiar with, searchable through Google and Bing, comprising everything from news sites to social media, streaming media, and traditional ecommerce like online banking and stores such as Amazon.
In addition to the Clear Web, there is a whole bunch of internet enabled activity that is not readily searchable and cannot be reached without special software or appropriate credentials. This is the Deep Web and it includes certain member-only sites and forums that are used solely to discuss and transact illegal activity. Markets in the Deep Web are referred to as dark markets.
A subset of the Deep Web can only be accessed with special networking software (for example, the Tor browser). This part of the Deep Web is known as the DarkNet and is a haven for cybercrime. Until recently, this was where you could find two of the largest dark markets, known as AlphaBay and Hansa. Despite the FBI’s efforts to stick to this terminology, it is quite common for people to refer generically to any illicit internet activity as Dark Web (and let’s face it, these are all terms that are evolving over time, without “official” definitions).
Big trouble in dark markets
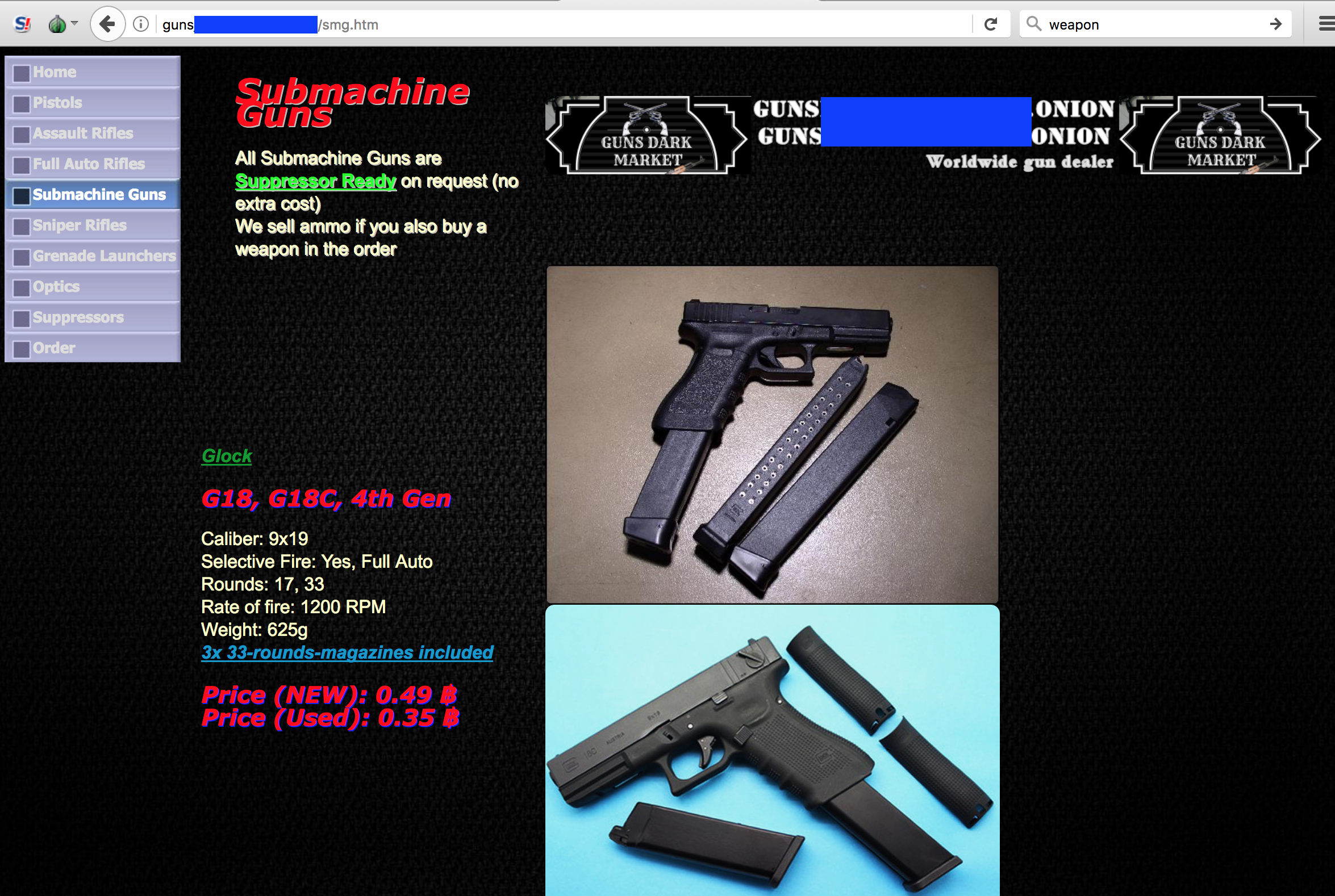
In June, a combined law enforcement effort took down AlphaBay and Hansa. So, what were the websites doing that bothered law enforcement? They were enabling people to indulge in cybercrime as they tried to buy and sell goods and services that are illegal. For example, in many countries and US states, it is illegal for citizens to own completely automatic firearms with large capacity magazines, but you can buy them in dark markets (Screenshot A).
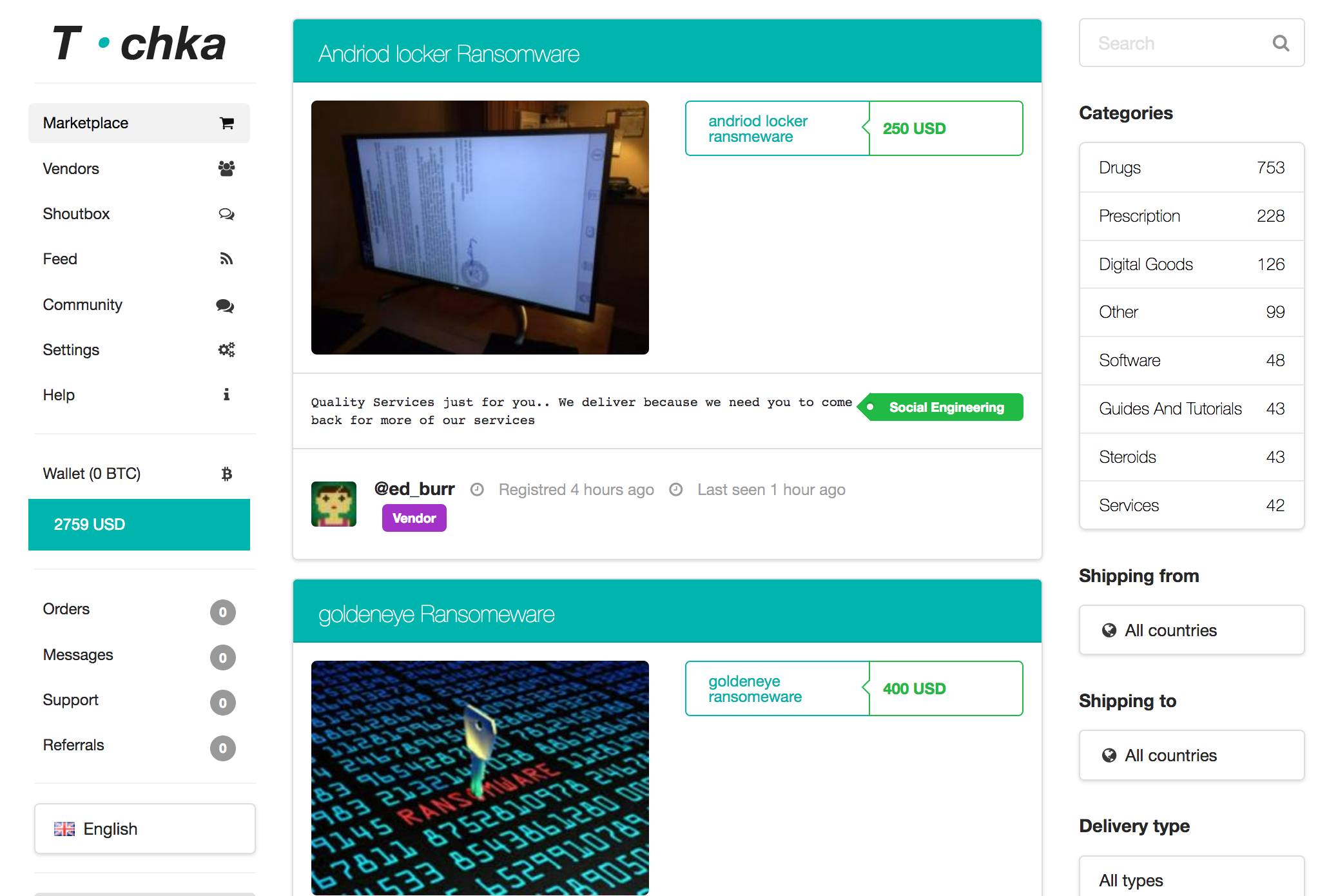
The sale and purchase of malicious code such as ransomware is also illegal in many jurisdictions, but dark markets make it possible (Screenshot B). Clearly, dark markets that traffic in these items, and others, like child pornography, banned substances, and hacking services, are crime-enabling institutions.
The crime enablement aspect of dark markets is enhanced by the fact that they use crypto-currencies like Bitcoin which make parties to the buying and selling activity hard to trace. So, it is not surprising that law enforcement agencies in many countries are keen to take down dark markets and punish their users and operators.
Dark times for the DarkNet?
You may recall the 2013 takedown of Silk Road, a DarkNet predecessor to AlphaBay and Hansa. Headlines were made when the court imposed a life sentence on its creator and operator, Ross Ulbricht (a sentence that was recently upheld by the US Court of Appeals for the Second Circuit).
You may also know that new iterations of Silk Road soon appeared to replace the one that was taken down. This was due in part to the fact that a dark market typically hosts a collection of sellers; in other words, it is more of a dark bazaar than a dark department store. If a seller loses a stall in one market, that stall can quickly migrate to a different market.
So it is unlikely that the takedown of AlphaBay and Hansa will end the practice of selling illegal goods on the internet. However, it might well deter some aspiring criminals, particularly if the persons responsible for AlphaBay and Hansa meet the same fate at the hands of the criminal justice system as Ross Ulbricht. (In a tragic twist, the alleged creator of AlphaBay, a Canadian citizen living in Thailand, appears to have committed suicide in prison not long after his arrest.)
The AlphaBay/Hansa takedown is also likely to discourage some dark market sellers, given the way it was carried out: a sort of one-two punch. From studying past takedowns it was clear that customers quickly migrate from the closed market to the next best market that is still open.
So, here’s how law enforcement played it: the Dutch police took full control of Hansa on June 20. However, they kept it open and monitored activity until AlphaBay was closed in early July.
"According to CNET, when AlphaBay was shuttered, police saw an eight-fold spike in traffic heading to Hansa."
According to CNET, when AlphaBay was shuttered, police saw an eight-fold spike in traffic heading to Hansa. Here’s how Rob Wainwright, the Europol director put it: "We could identify and disrupt the regular criminal activity that was happening on Hansa market but also sweep up all of those new users that were displaced from AlphaBay and looking for a new trading platform for their criminal activities.”
In announcing the AlphaBay takedown the US authorities left no doubt as to how serious they are about prosecuting this type of criminal activity: “The seizure and shut-down of the AlphaBay criminal marketplace and the indictment and arrest of its founder should send a clear message," said Eastern District of California U.S. Attorney Phillip A. Talbert. "If you choose to become involved in administering a site like AlphaBay on the dark web, or decide to use it to engage in criminal transactions, you will have federal law enforcement and United States Attorney offices from every District and State across the nation pursuing you.”
Dark aftermath?
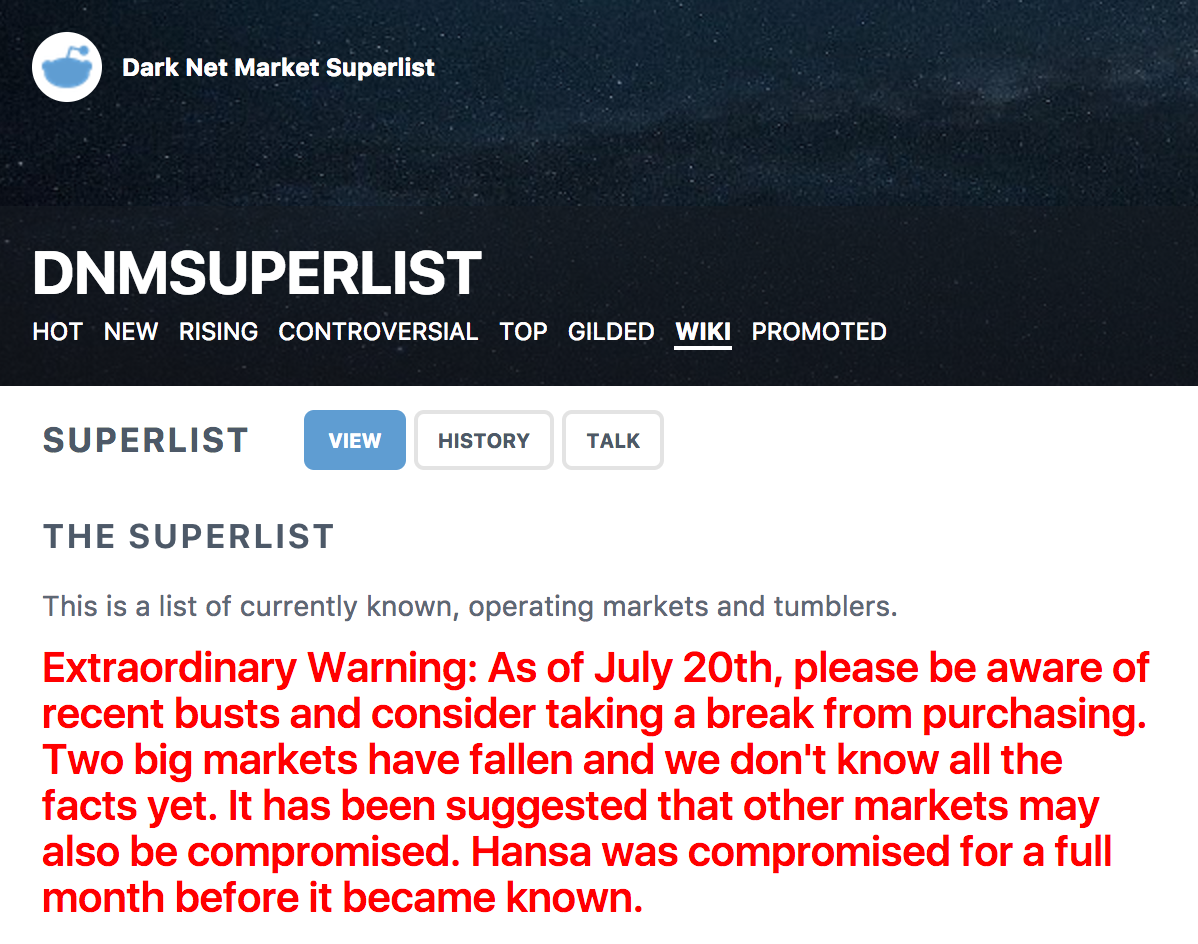
If you read what people familiar with dark markets are saying online, then it is seems that this one-two blow may have shaken what you could call “dark market confidence”. When people talk about taking an extended break from purchasing, you know there is an abundance of fear and suspicion, which was clearly one of the goals of the police action (Screenshot C).
It will be interesting to see what impact, if any, the takedowns have on malware campaigns. We know that dark markets have enabled crimeware-as-a-service operations, notably ransomware-as-a-service. Will there be a temporary reprieve? Will a significant percentage of would-be criminals decide to do something more legitimate with their time and resources? Will the more committed criminals simply move their operations to other parts of the Deep Web?
I tend to think some folks will continue to chance their hand in dark markets. A hallmark of predatory criminals is the belief that they will never be caught, and sadly only a small percentage of cybercriminals are being caught (although the list of arrests in the first part of this article was encouraging).
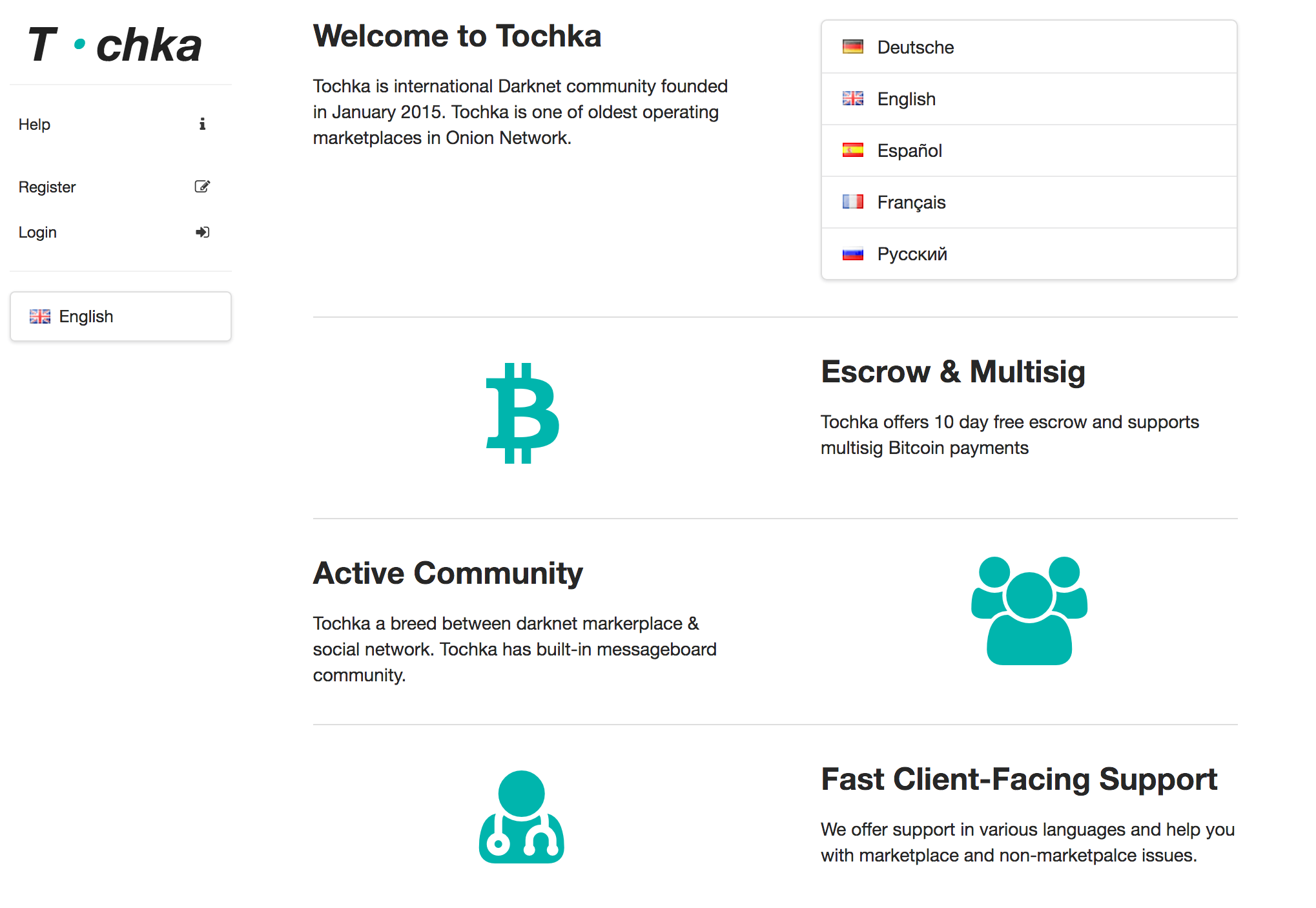
Unfortunately, if you look at how much dark markets have evolved in the last few years, offering “fast, client-facing support”, as well as escrow services and multilingual help (Screenshot D), you get the impression they are backed by some determined people.
The unanswered question is: how many of them are willing to risk a life sentence?