Would you like to add traffic to your YouTube channel and maybe even get paid for watching YouTube videos? Or are you looking to buy and sell bitcoin “from the comfort of your phone”?
The makers of the apps “Boost Views” and “PaxVendor” want you to believe they have just what you’re looking for. Except they don’t. They’re after your money – in whatever form they can get their hands on it.
Boost Views: Views for YouTube monetization
Under the guise of attractive YouTube-related services, the PayPal credential stealer “Boost Views” found its way onto devices of up to 100,000 users.
The app, detected by ESET as Trojan.Android/FakeApp.FK, promises to generate earnings for watching in-app YouTube content, as well as increase YouTube traffic in exchange for purchasing credits. According to the app description, users can conveniently withdraw accumulated earnings to their PayPal account.
However, if users try to do so by entering their PayPal credentials into an “authentication” form, they will find they’ve become victims of a scam – there are no earnings to be withdrawn. Even worse, their PayPal credentials are now at the attackers’ disposal, open for misuse.

Figure 1 – Boost Views on Google Play
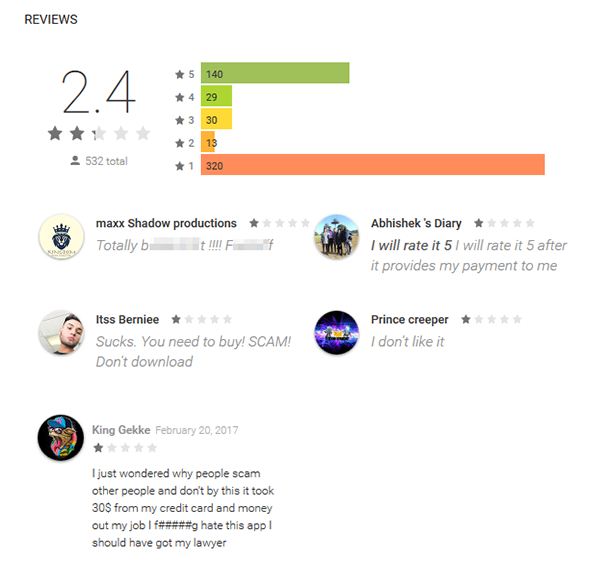
Figure 2 – Negative Boost Views reviews implying fraudulent activity
How does it operate?
Once the app is launched, users are asked to create a Boost Views account. After logging in, users can choose one of the services seemingly offered by the app.
For viewing YouTube videos for money – one of the major features advertised by the app – there’s “Viewer”, an in-app video player. Users can view content for $0,0001-0,0005 per minute (as seen during our research), with the current earned sum shown under the video content.
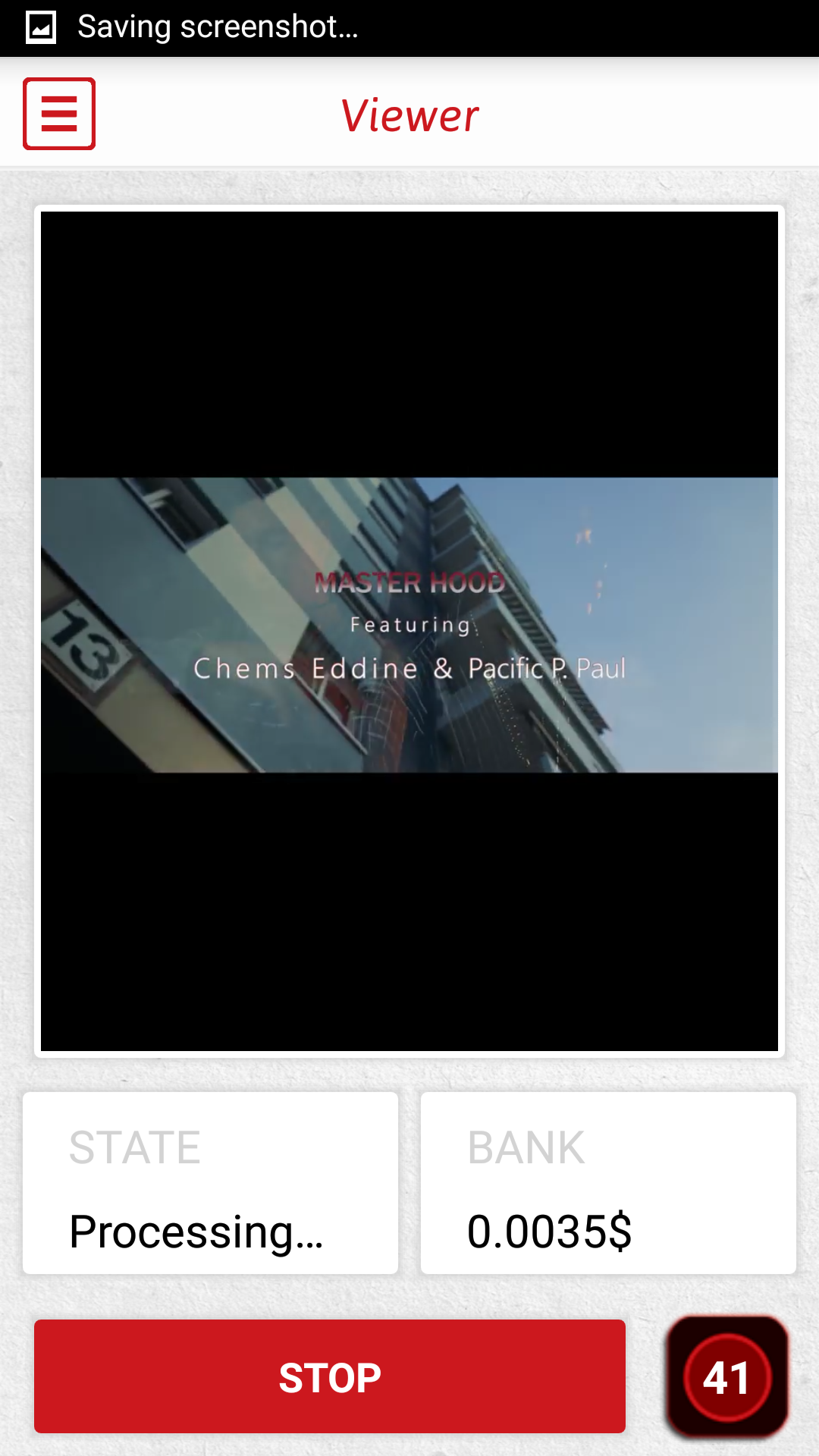
Figure 3 – In-app YouTube video viewer with earned money count
Having generated $0.09 in 16 hours of automatic video playing and having seen no mention of a minimum payout threshold, we tried to withdraw the earned amount.
In order to withdraw money, PayPal credentials must first be entered into an insecure login form for “authentication”. Once victims enter their credentials, they are confronted with an “invalid login” error message and their PayPal credentials are sent unencrypted to a developer’s server.
With the PayPal account now compromised, the victims’ PayPal and/or credit card balance are open for misuse. At the time of writing this article, PayPal hasn’t reported any suspicious activity on the account used for testing the malicious app’s features. This, however, offers little reassurance, knowing your credentials are at someone else’s disposal.
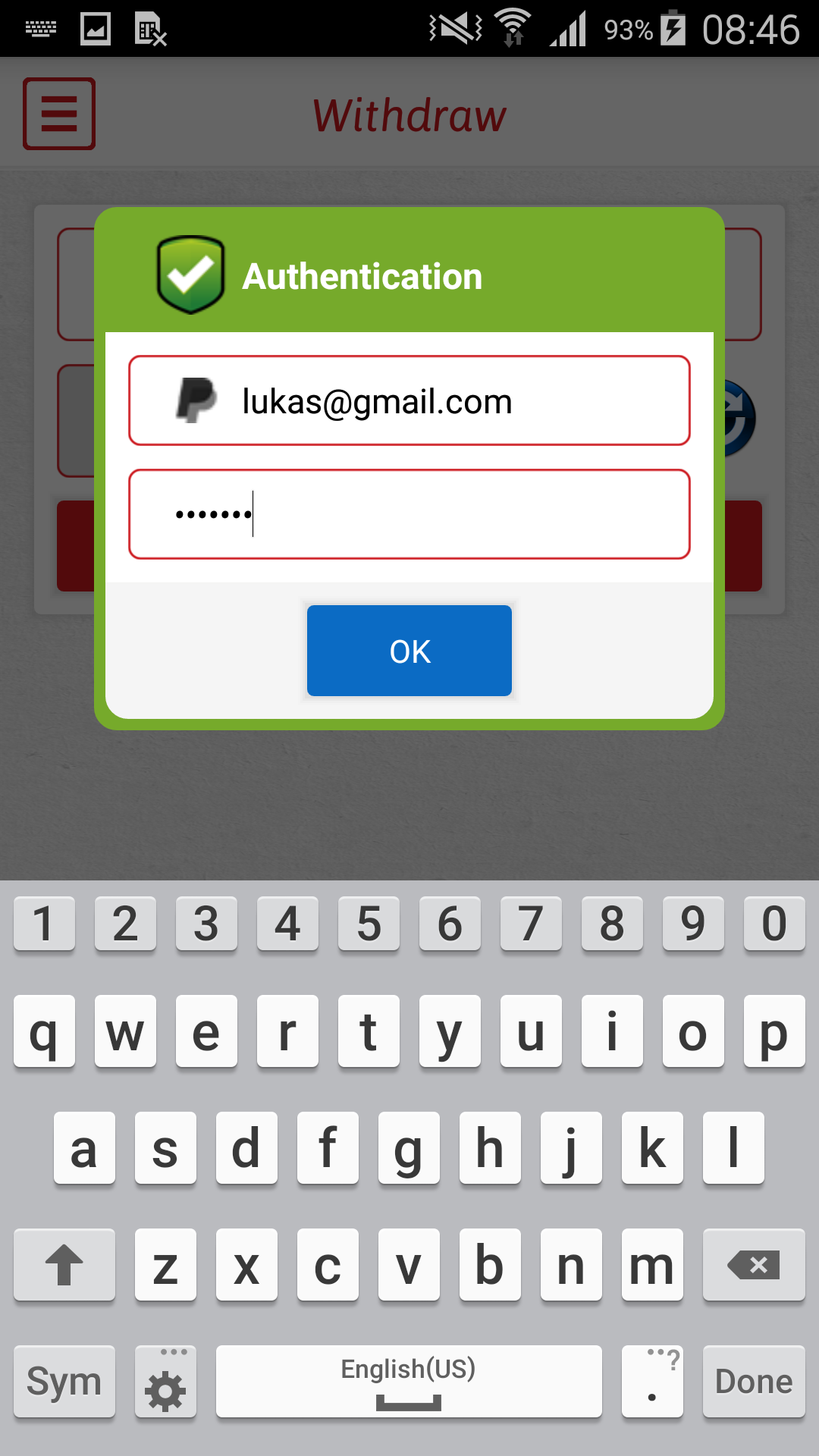
Figure 4 – Insecure login form requesting PayPal credentials
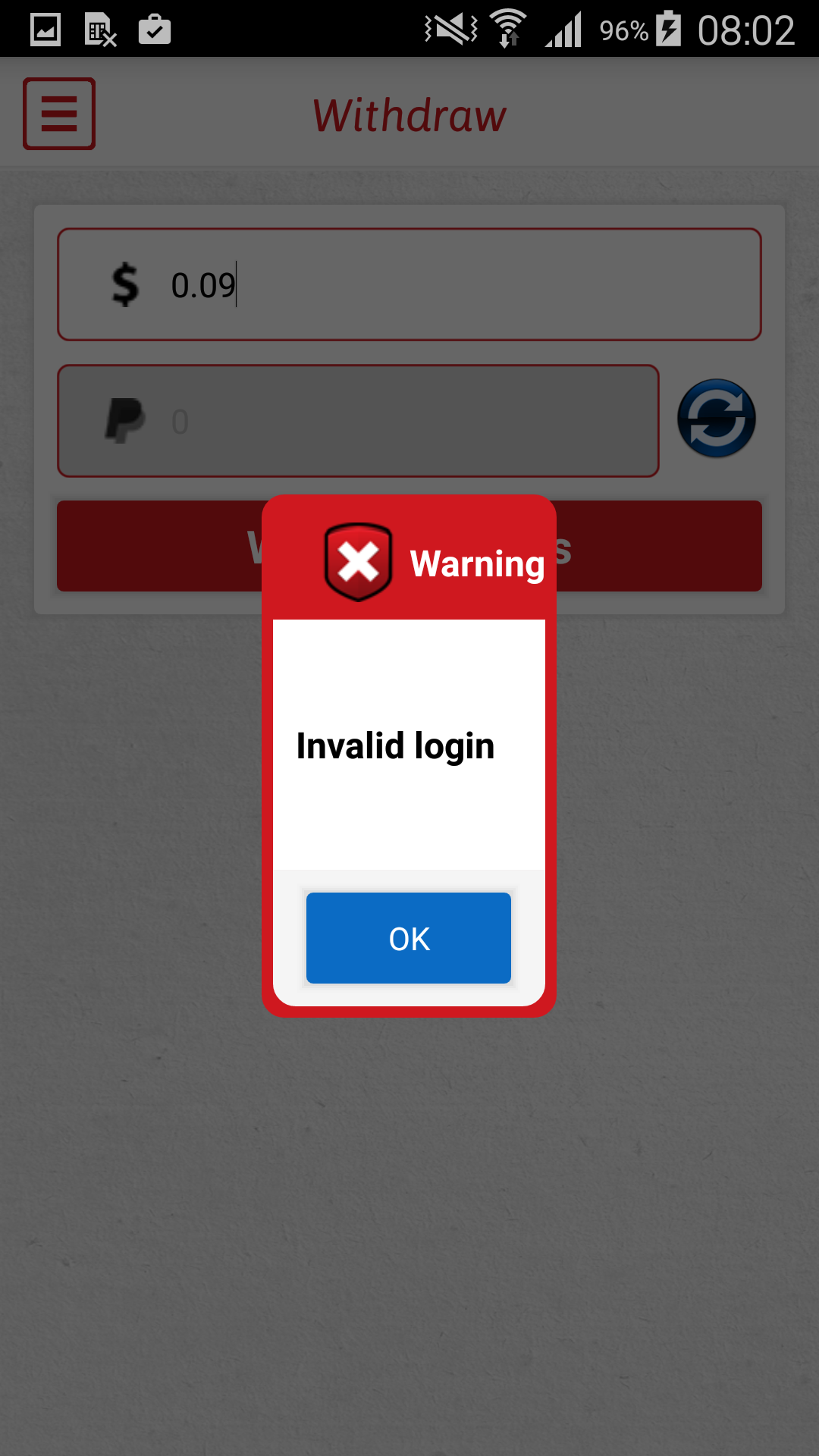
Figure 5 – Invalid login error message displayed after entering PayPal credentials
If users wish to purchase credits to exchange for YouTube views, they are offered credit packs found in the app’s shop. While this might be a logical way to use the views generated in the app’s Viewer (and could well be a real functionality), we find the deceptive behavior of the app is reason enough not to hand money – and possibly credit card details – to this developer.
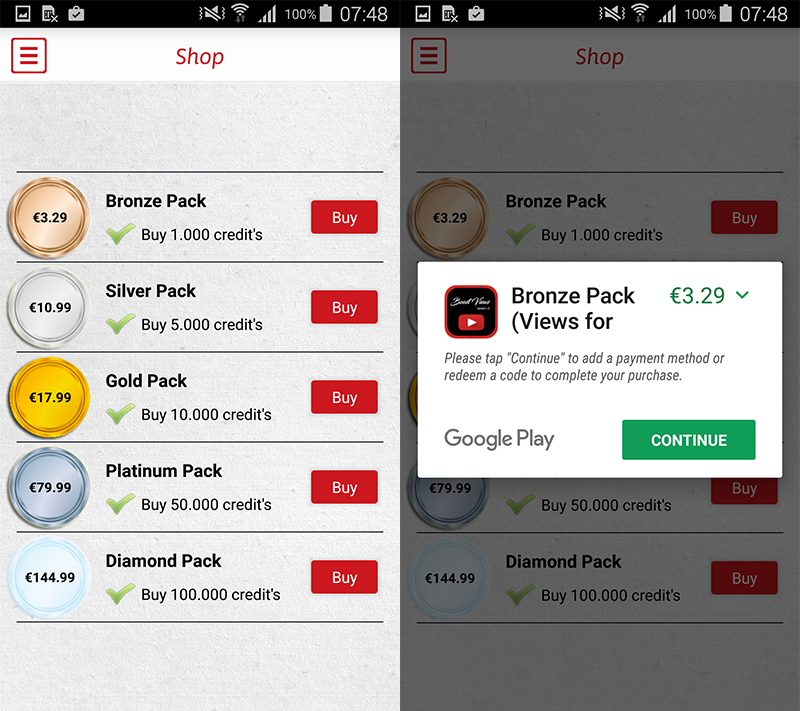
Figure 6 – In-app shop offering credit packs
Interestingly, the credit packs are also offered on the developer’s website, with different pricing and invalid hyperlinks leading back to the homepage. The website, as such, appears to be a generic template filled with marketing buzzwords rather than actual content, which only adds to the shadiness of the app observed so far.
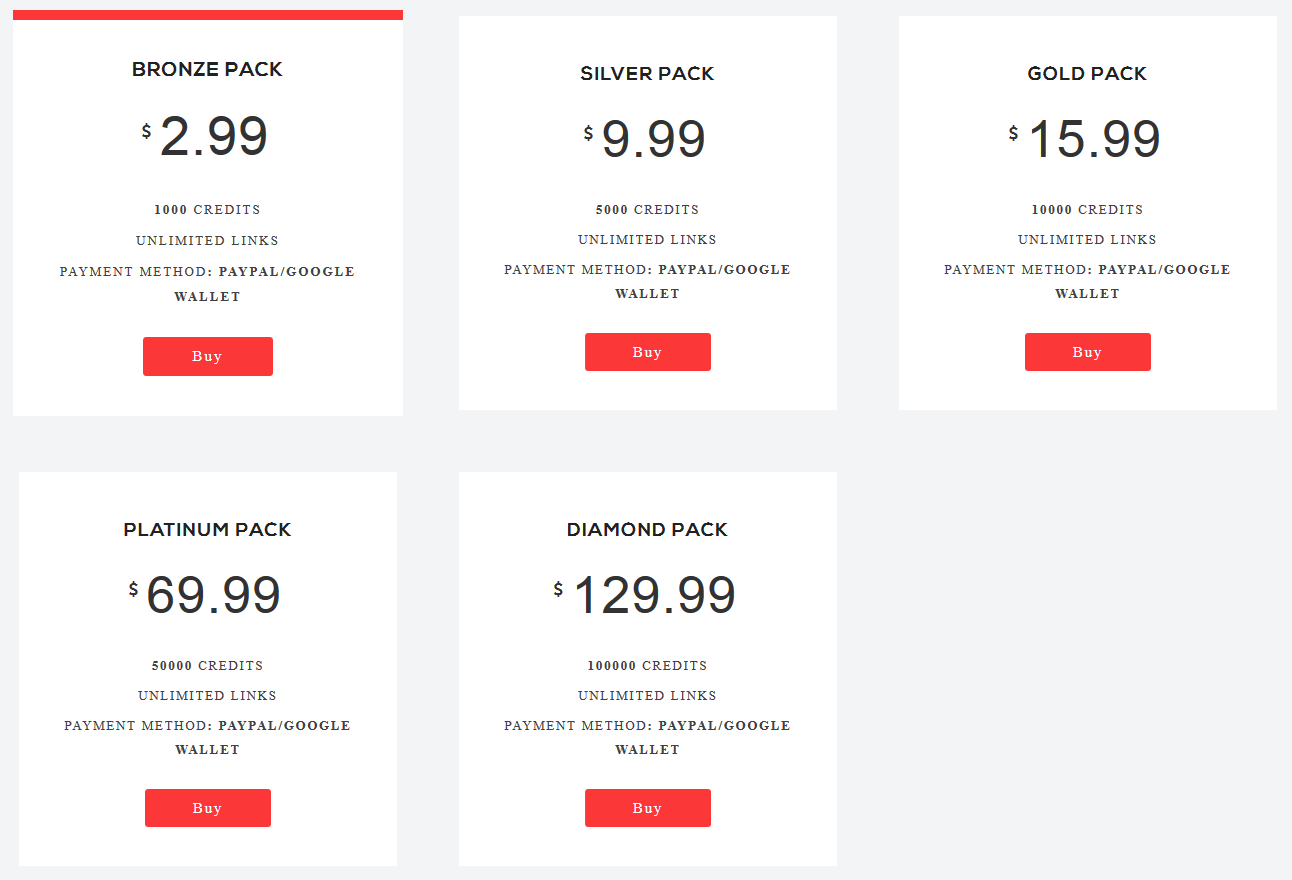
Figure 7 - Credit packs with invalid links on developer’s website
PaxVendor
While Boost Views aims to infiltrate your PayPal account, “PaxVendor” would like to have access to your bitcoins. The malicious app, detected by ESET as Android/FakeApp.FI, parasites on the legitimate Bitcoin trading marketplace Paxful, which currently only operates on desktop.
PaxVendor uses a bogus login screen to harvest Paxful credentials and offers its victims no real functionality. In only a week’s time, the app reached up to 500 installs, before being pulled from the store on our notice. Apart from reporting the app to Google Play security team, we also contacted Paxful to warn its users about this malicious fake.

Figure 8 – PaxVendor on Google Play
How does it operate?
Upon launch, the app instructs users to disable Google authorization or SMS authorization in their Paxful account in order to avoid potential two-factor authentication obstacles.
The fake login screen requests Paxful credentials. When submitted, the user is shown an error screen claiming the app can’t connect to their account.
In the meantime, the credentials are sent to the attackers’ server. Once the attackers get hold of the credentials, they use them to log into users’ Paxful accounts. In our case, someone signed in from Ukraine shortly after the credentials were entered.
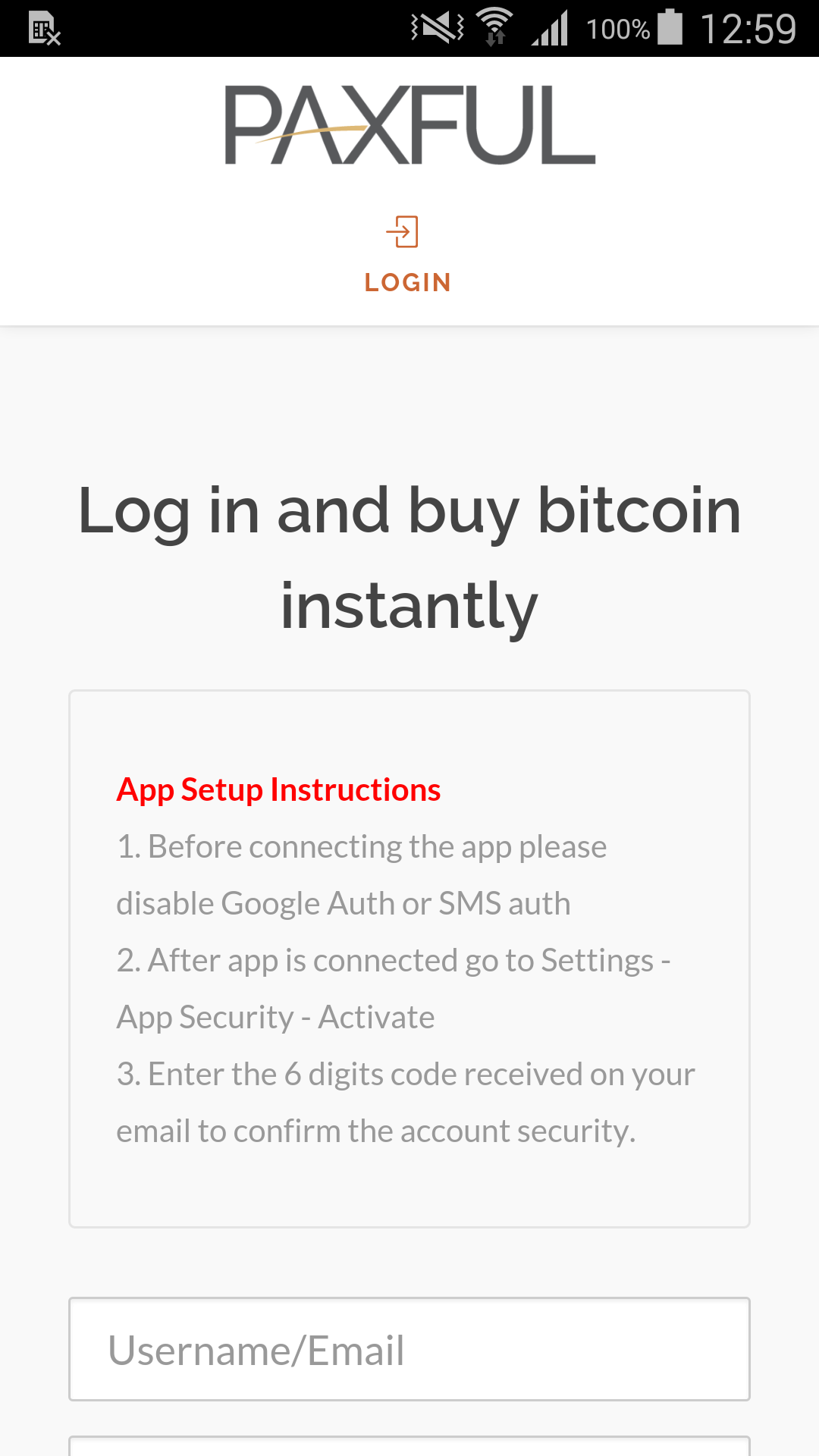
Figure 9 – Bogus login screen harvesting Paxful credentials
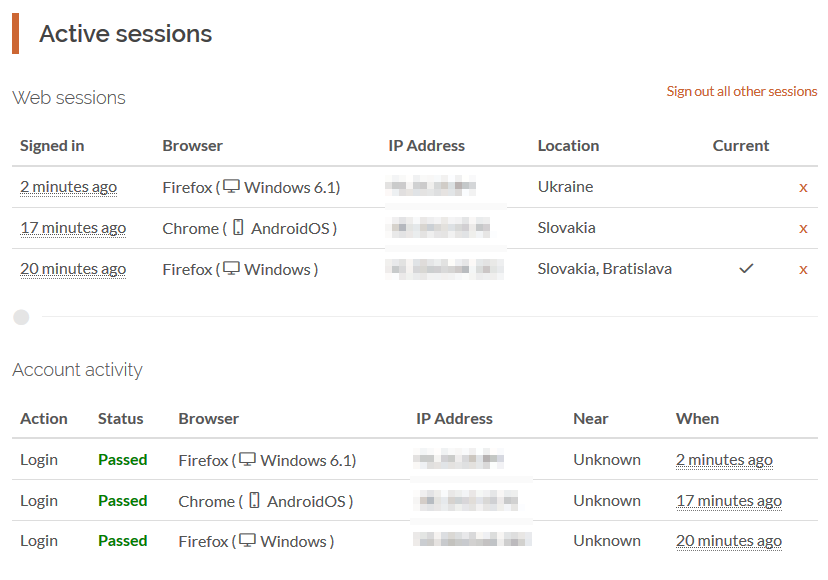
Figure 10 – Stolen credentials used to log into victim’s Paxful account
How to protect yourself?
If you have downloaded Boost Views and tried to withdraw money via PayPal, we strongly suggest you change your PayPal password immediately. While you’re at it, check your account for suspicious activity and report potential issues to PayPal. You might also want to uninstall the malicious app, found under Settings >Application manager/Apps > Boost Views.
As for PaxVendor, change your Paxful password and review the activity on your account, reporting anything unusual. Proceed with uninstalling the fake app by going to Settings > Application manager/Apps > PaxVendor.
To avoid falling victim to Android malware, there are a couple of principles to stick to when installing apps on your device.
Whenever possible, favor downloading apps from official app stores over unknown sources. Although not flawless, Google Play does employ advanced security mechanisms to keep malware out, which doesn’t have to be the case with alternative stores.
Exercise extra caution when downloading third-party apps offering additional functions to existing applications, as there may be a “catch” in these attractive-sounding offers. With that in mind, avoid inserting sensitive credentials into untrusted login forms of third-party apps.
To verify whether an app is to be trusted, check the popularity of the app by number of installs, ratings and, most importantly, content of reviews. When in doubt, opt for high-quality apps marked as Top Developer or found in the Editor’s Choice category.
Last but not least, use a reputable mobile security solution to protect your device from latest threats.




