Two weeks ago WordPress 4.7.2 was released, and website administrators running self-hosted versions of the hugely popular CMS and blogging platform were advised to update their systems as a matter of urgency.
What we didn't know at the time was just how important that WordPress update was.
Last week, WordPress revealed that 4.7.2 had secretly included a fix for an undisclosed critical vulnerability.
If left unpatched, the vulnerability could allow a malicious attacker to modify the content of any post or page on a WordPress site.
The reason the vulnerability wasn't made public at the time of WordPress 4.7.2's release was the very real worry that malicious hackers might race to exploit the flaw, attacking millions of blogs and company websites.
Security researchers and major WordPress-hosting firms put mitigations in place ahead of the public disclosure in order to mitigate attacks, and it looked as though a bullet might have been dodged - assisted by the fact that many WordPress sites are configured to automatically update themselves, or offer simple one-click updates.
Now, however, things are not looking quite so positive. Evidence has emerged that malicious hackers did not take long to strike after news of the vulnerability was made public, with researchers reporting that multiple public exploits were being shared and posted online within 48 hours.
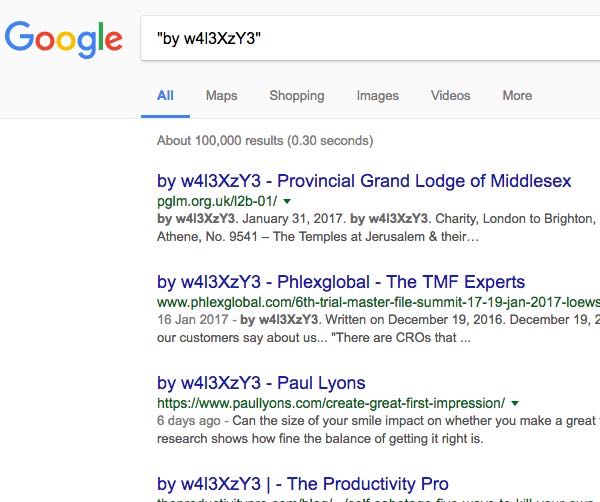
Researchers at Sucuri have detailed a number of defacement campaigns they have seen, including one which has sprayed the words "by w4l3XzY3" across a large number of vulnerable websites.
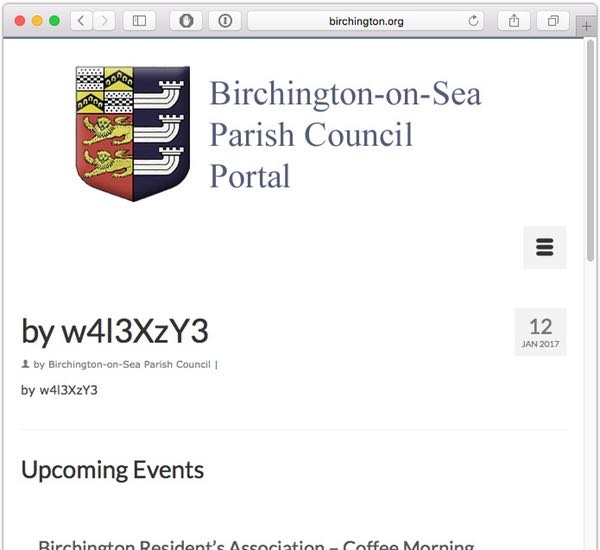
According to Google search results, something in the region of 100,000 webpages may have suffered from this particular defacement.
In all likelihood, there are SEO spam gangs who will be keen to exploit this vulnerability in an attempt to meddle with Google search results for their own financial benefit.
If you run a WordPress website, you have to take security seriously. That means, amongst other things, ensuring that you are running the latest version of the software and keeping an eye on the latest security alerts.
Even if you aren't in a position to automatically roll out WordPress updates on your live website you should build an infrastructure which allows you to test new versions of WordPress safely, and work towards ensuring that your live site is updated in a timely fashion.
If you don't, you're running the risk that attackers might exploit a security hole that you really should already have patched against.




