Earlier this week coordinated law enforcement action took down the Avalanche fast-flux network. For several years, this network has allowed various botnet operators to benefit from an extra layer of protection against takedown and domain blacklisting.
Today, this network has suffered a serious blow. Coordinated efforts from law enforcement around the world succeeded in taking down some of its essential domains. However, there is one crucial task left to do: cleaning up in the aftermath, and ESET has been asked to help in this effort. Even if you don’t use an ESET product, you can run our free ESET Online Scanner tool, which is able to detect and clean malware families that either were distributed by or made use of this fast-flux network. Our tool can also be found on the US-CERT website.
ESET always strives to support law enforcement operations, since it advances one of our core goals: making the internet safer. Experience shows that this type of disruption effort is one of the most effective ways in which to hurt criminals by reducing their profitability and can even lead to arrests. As such, it is an efficient way to make lasting, positive changes to the security ecosystem. While these types of operation require a lot of time and effort, they are well worth it when the day of the takedown comes. As our recent efforts against Dorkbot and Mumblehard illustrate, we are always happy to join forces in concerted efforts against some of the worst plagues of the internet.
Fast-flux network you say?
A fast-flux network, such as the one operated by the Avalanche group, can be defined as “a DNS technique used by botnets to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts acting as proxies”.
To illustrate this concept, let’s use Win32/Wauchos (aka Andromeda), as we know that some of its C&Cs have been using this network. If a security company wanted to map the attacker’s infrastructure to try to disrupt it eventually, the fact that it is hidden by different layers of proxies will make finding the true C&C all the more challenging.
Who is using this network?
This week’s operation targeted various botnets that have made use of the Avalanche network. Here are a few malware families known to be active or past users of this service:
- TeslaCrypt
- Nymaim
- CoreBot
- GetTiny
- Matsnu
- Rovnix
- URLZone
- QakBot (aka Qbot, PinkSlip Bot)
There are many different types of malware using this service, but most are credential stealers, ransomware and banking trojans. The variety of malware families listed above is a clear indicator that this fast-flux network is sold as a service to other cybercriminals.
How can I clean my computer?
If you are worried that your computer might have been affected by one of the botnets using this fast-flux network, you can download and run the ESET Online Scanner. It will scan your computer and remove anything found that might harm your computer. The use of the online scanner is entirely free, and the process will only take a few minutes if you follow the steps below:
1. Download and launch ESET Online Scanner
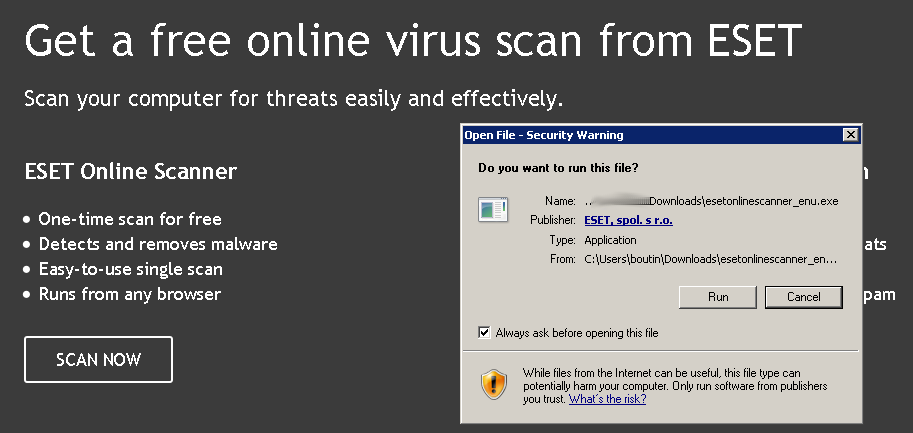
2. Accept the terms of use
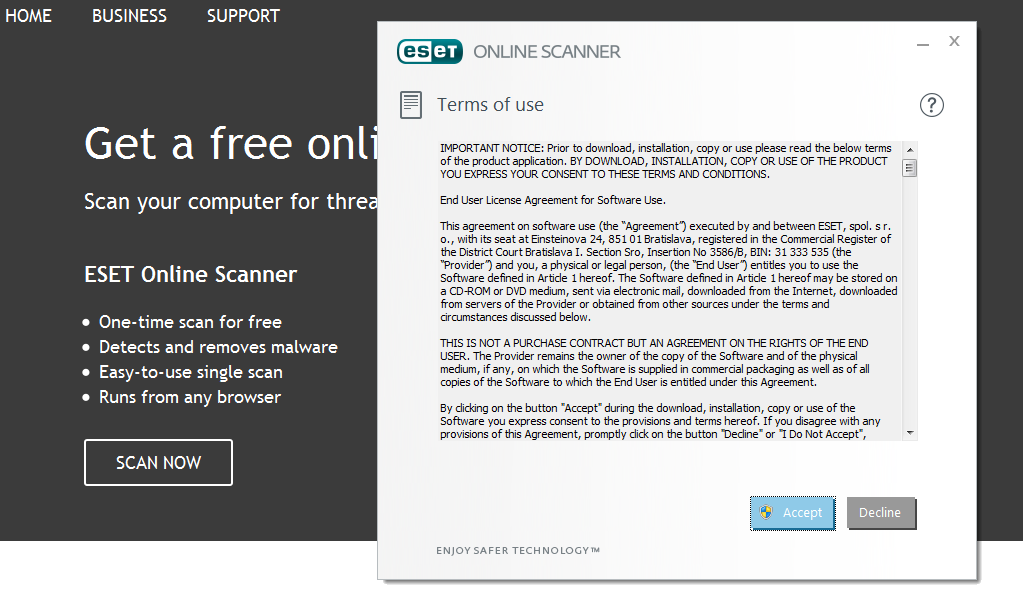
3. Click Scan and wait until the operation completes
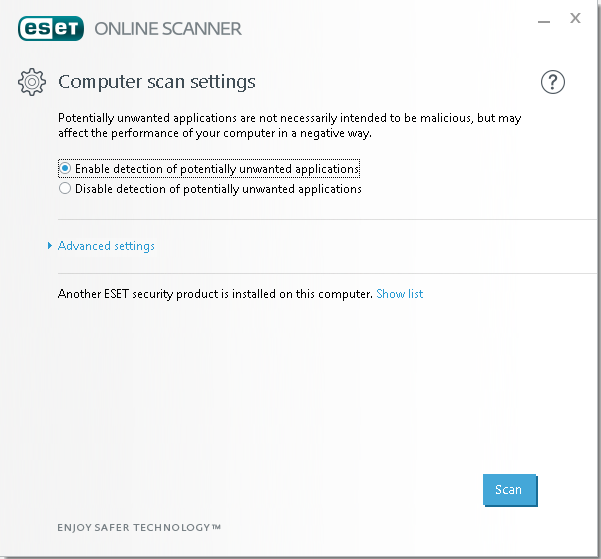
More information about how to use the ESET online scanner may be found here.




