ESET has discovered the first ever fake lockscreen app on Google Play, named Pokemon GO Ultimate. As the title suggests, it deliberately locks the screen right after the app is started, forcing the user to restart the device. Unfortunately, in many cases a reboot is not available because the activity of the malicious app overlays all the other apps as well as system windows. The user needs to restart the device either by pulling out the battery or using Android Device Manager. After reboot, it runs in the background hidden from the victim, silently clicking on porn ads online.

Figure 1: Fake Pokemon Go Ultimate
With Pokémon GO arguably the biggest buzz the internet has seen lately, people all over the world are keen to get their hands on the app. However, as it is currently only officially available in a few countries – US, Australia, New Zealand, Germany and the UK – this comes with risks.
The bad guys are aware of this and are trying to exploit the hype by infecting Pokémon-hungry victims with malicious fake apps. Pokemon GO Ultimate serves as a perfect example, promising to allow the victim to play the original title, but instead delivering only malicious activity.
After the installation from Google Play, there was no evidence of Pokemon Go Ultimate on the devices, but instead an app using the name “PI Network” and a different icon was added.

Figure 2: Pokemon Go Ultimate after installation
When the victim runs what he thinks is a PI Network app, the app freezes immediately after startup, effectively locking the screen and forcing a restart by the removal of the device’s battery.

Figure 3: Screen locked by Pokemon Go Ultimate
After reboot, the app stays hidden from the user, with its PI Network icon removed from the app menu. Yet, the malicious app still runs in the background using this technique to click on advertisements, generating revenue for its operators.
In order to delete the app, the user needs to go to Settings -> Application manager -> PI Network; at that point it can be uninstalled manually.
This is the first observation of lockscreen functionality being successfully used in a fake app that has landed on Google Play. It is important to note that from there it takes just one small step to add a ransom message and create the first lockscreen ransomware on Google Play.
Other traps
Unfortunately, the screen locking app wasn’t the only malicious one to appear on our radar. ESET researchers also discovered bogus apps named "Guide & Cheats for Pokemon Go” and “Install Pokemongo” on Google Play. ESET Mobile Security detects them as Android/FakeApp.
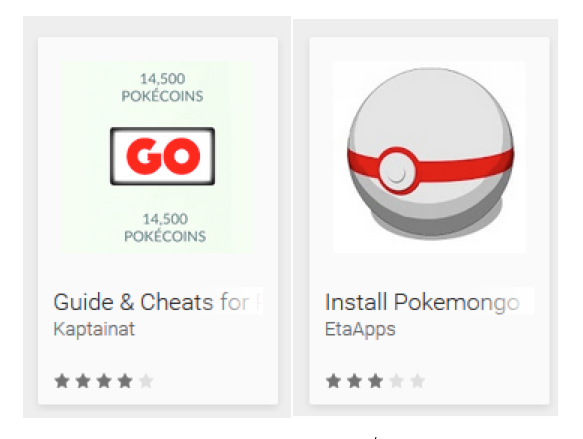
Figure 4: Scareware applications
Neither of these apps delivers on its promises; the only things they deliver are scareware ads leading users to pay for unnecessary services. Immediately following startup, the app displays bogus promises: the user can select an amount of Pokecoins, Pokeballs or Lucky Eggs to generate, in some cases up to 999,999 each day.
Before actually adding selected resources, both apps require the user to “verify his account”. Instead of any serious verification, they attempt to mislead the user into subscribing to expensive bogus services. (This is quite similar to bogus apps promising to improve the victims’ popularity on social networks.) They display various fraudulent pop-up alerts. One of them claims that the device is infected with many viruses and needs to be cleaned. Of course, the app promises to clean up the device, which could cause the user to unwillingly send a subscription SMS to bogus – yet expensive – services.
The virus removal masquerade is only one example of the apps’ scareware techniques. They can also download other applications, create surveys and display scam ads where the user has allegedly won prizes such as the new iPhone, Galaxy S7 Edge or even large amounts of money. The techniques deployed depend on the country where the user’s IP is being localized.
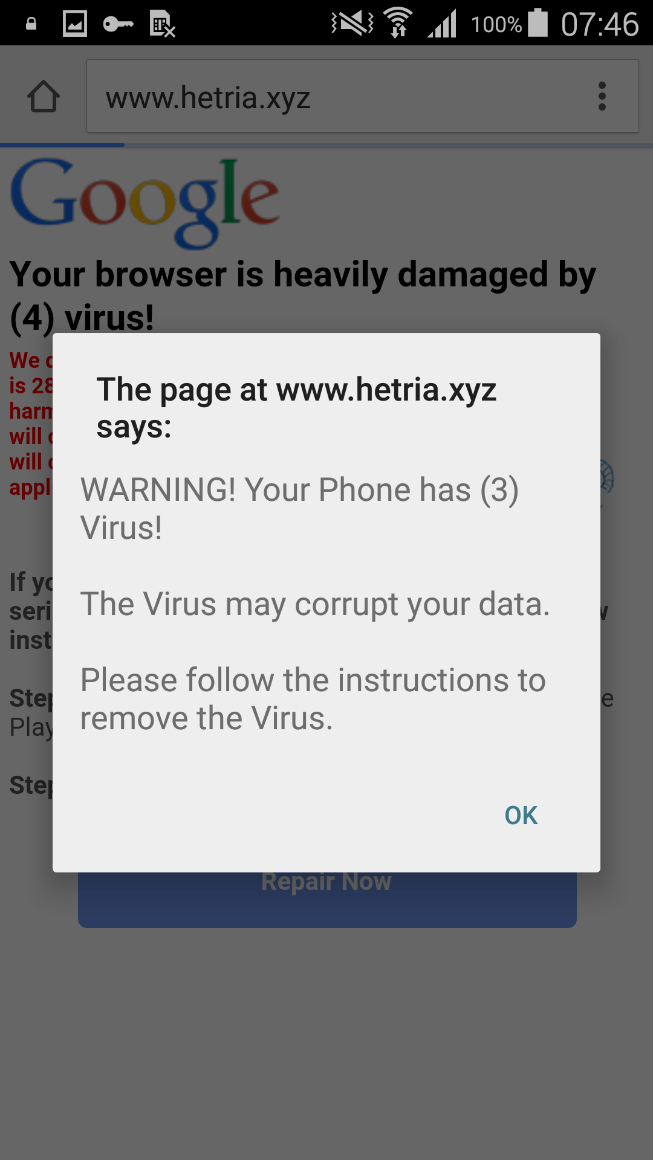
Figure 5: Scareware targeting users in US
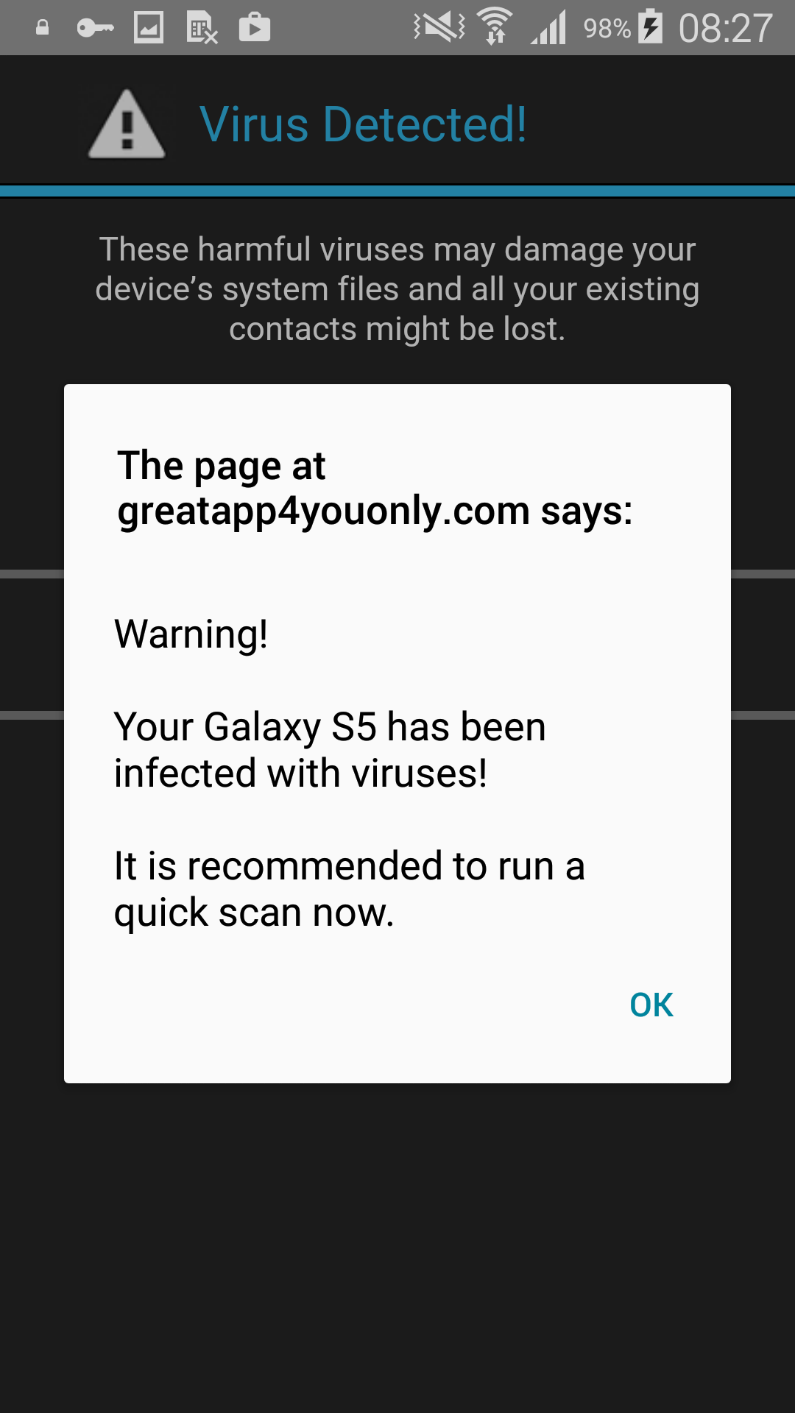
Figure 6: Scareware targeting users in Australia
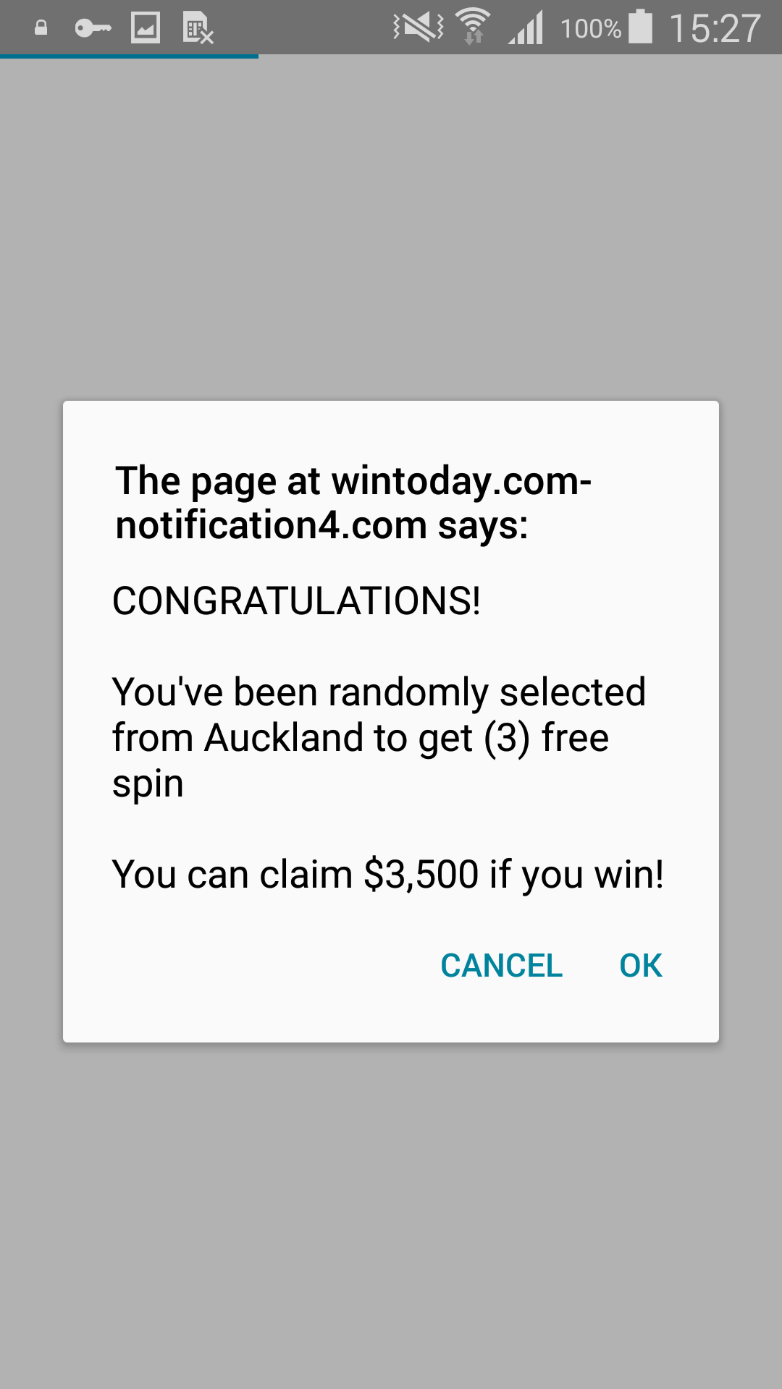
Figure 7: Scareware targeting users in New Zealand
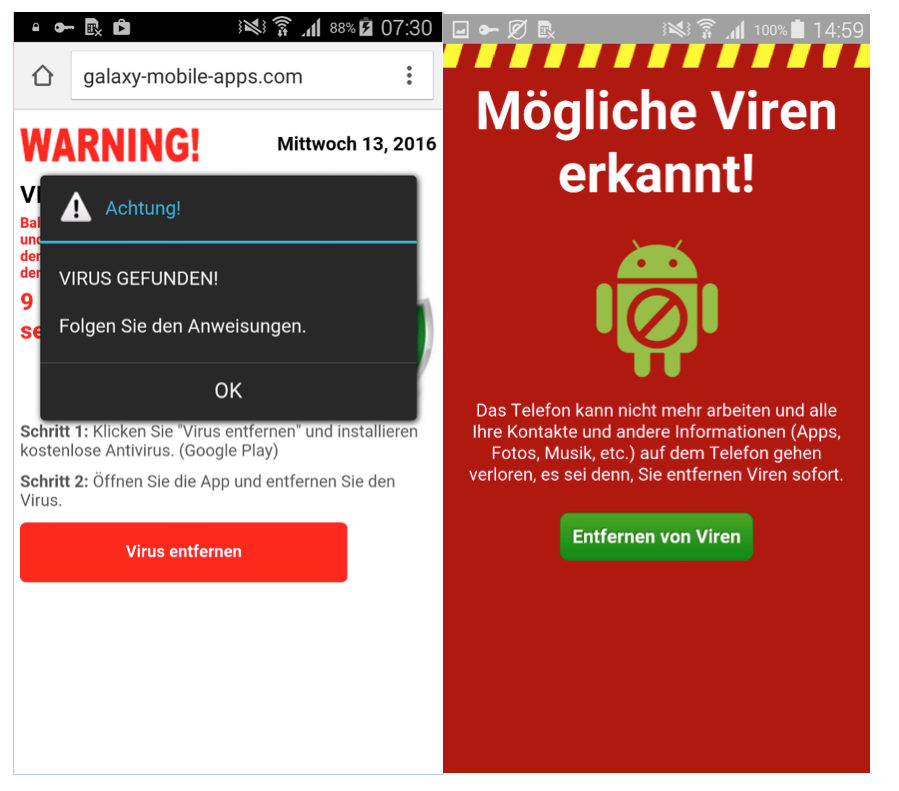
Figure 8: Scareware targeting users in Germany
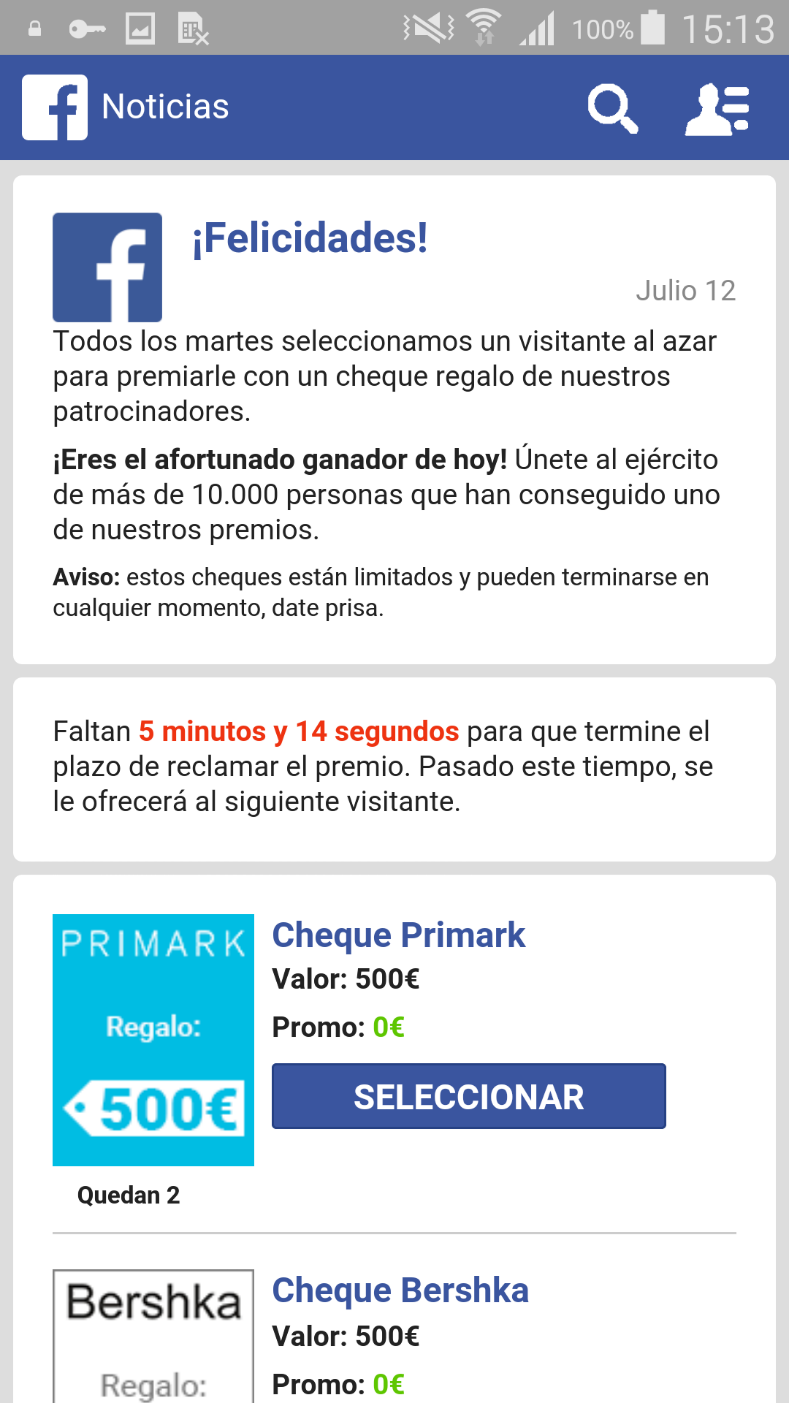
Figure 9: Scareware targeting users in Spain
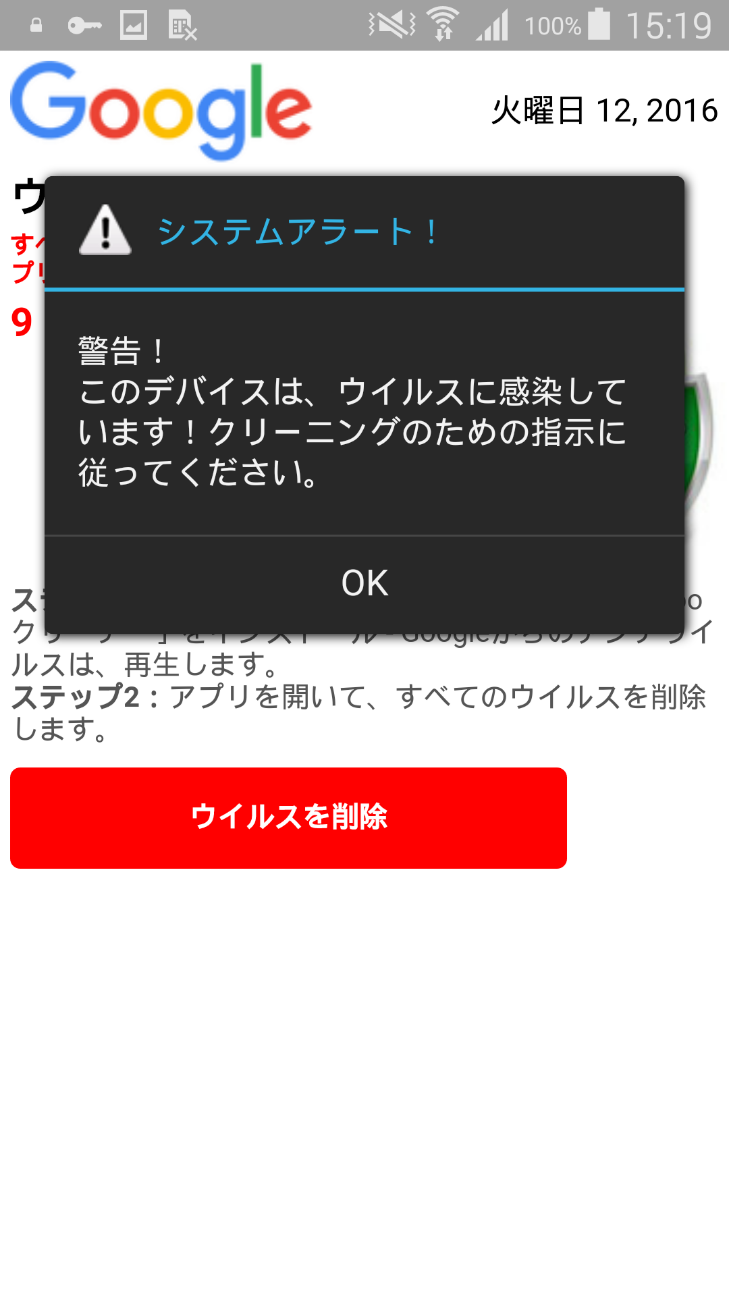
Figure 10: Scareware targeting users in Japan
Every time the user presses the “Back” button, new scareware pop-ups and advertisements appear. The only way to get rid of them is by double-clicking on the “Back” button.
Beware of them all!
All three of the malicious apps mentioned were removed from the Google Play store after being reported by ESET. Having been available on Google Play for just a short period of time, they only managed downloads numbering in the thousands. Pokemon Go Ultimate reached 500 - 1,000, Guide & Cheats for Pokemon Go reached 100 – 500 and the most successful of them, Install Pokemongo, attracted 10,000 - 50,000 victims.
Security experts – including ESET – have warned about fake versions of the Pokémon GO game’s APK and about malicious apps masquerading as Pokémon Go tutorials or cheats. Pokémon Go is so appealing that despite all of these warnings users tend to accept the risks and download everything that might help them “catch ‘em all”.
For those who really can’t resist the temptation of chasing Pokémon all around and are live outside of the approved countries, ESET experts have the following advice:
- Download from reputable sources only
- Check user reviews and focus on negative comments (keep in mind that positive ones may be fabricated)
- Read the app’s terms and conditions, focus on permissions
- Use a quality mobile security solution




