There is no doubt that criminals have found a mechanism in ransomware enabling them to obtain significant benefits with relatively little effort. And the information stored by computers is much more important than we think, although many users only realize this when they lose access.
"Jigsaw is an example of the tests that the creators of ransomware are carrying out."
For this reason, it comes as no surprise that for several months now, we have been witnessing continuous waves of ransomware variants. Some of these variants have been known for a long time, such as Cryptolocker, TeslaCrypt, and TorrentLocker, but we are continually seeing the appearance of new variants that want their slice of the pie.
Encryption and deletion of files
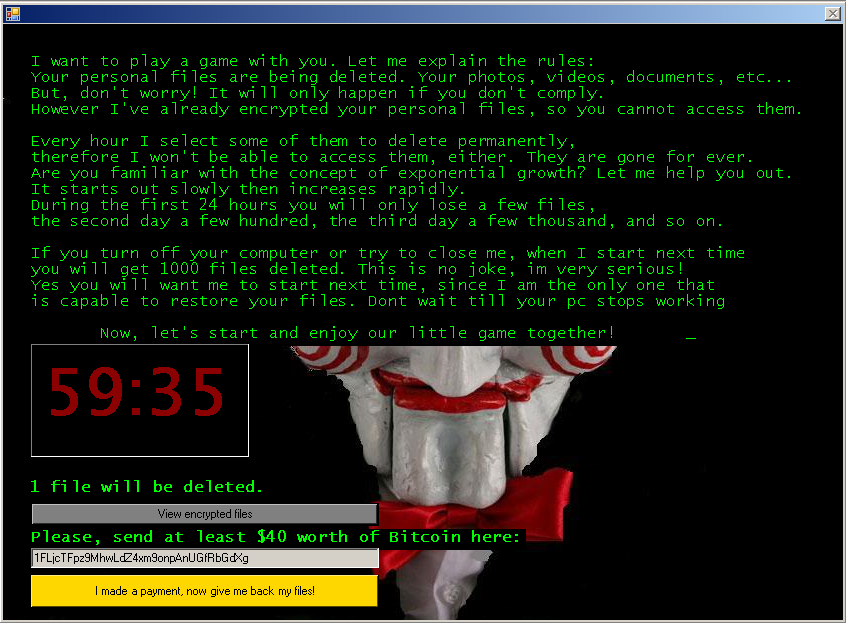
This new batch of ransomware programs includes Jigsaw, a variant detected by ESET as MSIL/Filecoder.Jigsaw, which has several peculiar features that make it stand out. To start with, the typical screen background or image informing you that files have been encrypted has been replaced by an image of the puppet Billy, one of the hallmarks of the Saw film series.
On this image is an explanation to the user of what has happened to their files, as if it were one of the tests in the well-known horror saga. There are also the necessary instructions for paying the ransom, which is 150 dollars in bitcoins.
"The real threat is that every hour some of the encrypted files are deleted."
In addition to this graphic, the real threat from this ransomware variant is that every hour some of the encrypted files are deleted. This makes time a key factor if you want to recover the files. In fact, if you try to stop the process or restart the system, Jigsaw will delete 1,000 files, thus limiting the actions that the user can take to try to recover their data without paying the ransom.
A curious fact is that, unlike other variants that give full details of how to pay the ransom in bitcoins, Jigsaw merely provides a link where you can obtain this cryptocurrency. This could lead us to believe that the author of the ransomware is less professional that those of other variants.
Luckily, for those users who have been affected by Jigsaw, a tool and instructions for restoring the encrypted files are already available. We recommend following the steps set out in these links to prevent criminals from making any money at the cost of the information stored on the users’ systems.
A continuing development
Jigsaw is only one example of the numerous tests that the creators of malware are carrying out in relation to ransomware. In this case, we encountered the novelty of file deletion in order to cause yet more alarm to their victims – looking for their threatening methods keeps producing results.
Right now, this is one of the most profitable threats for them and, owing to its aggressive nature, many companies and researchers, like us, are analyzing new variants every day to find out how to decrypt the files.
We should expect them to keep employing new strategies and even greater sophistication in certain concrete cases in the near future. Not only that, but we have seen how ransomware is spreading out of its natural habitat of Windows and Android system devices to other systems like Linux and Mac OS X, and there has even been evidence on the Internet of Things.
With the passage of time, users are becoming more conscientious and, as a result, criminals are using different techniques (other than the well-known harmful email attachment). These include the use of exploit kits on legitimate websites and even on websites visited by millions of users every day, enabling them to expand their criminal activities and find new victims.
We therefore need to be alert and look beyond the traditional means of attack so that we are prepared when faced with more ingenious techniques. Users cannot continue being the weakest link in the IT security chain, and we must anticipate the movements of criminals.
We must take steps to mitigate against threats of this kind, starting with making a backup of our most important files, having a security solution capable of detecting new ransomware variants as they appear, and implementing company security policies to prevent infected equipment from affecting shared resources on the company network.
If we apply these measures – many of them simply common sense – we will have won a large part of the battle against ransomware. But to do this, we need to start right away and keep up to date with new threats as they appear so we can successfully tackle them.




