One of the most common ways of spreading Android malware – including malware found on the official Google Play Store – is by masquerading as a legitimate popular application. The last such example that we discussed on WeLiveSecurity was a fake Dubsmash app and Android/TrojanDropper.Mapin compromising tens of thousands of users' devices. In order to help make Google Play a safer place for Android users, ESET continues to monitor the official Android app market for malicious or potentially unwanted applications.
This has led to the discovery of another threat on Google Play, which has so far been downloaded more than 200,000 times. This time the trojan impersonated the famous games Pou and Subway Surfers, each with more than hundreds of millions of downloads. The apps pose as Cheats for Pou, Guide For SubWay and Cheats For Subway, claiming to offer the same application functionality in apps. The payload of these applications was to deliver ads to users at regular intervals.
While ad-supported applications are common in the Android ecosystem, there’s a clear boundary of behaviors that ESET cannot condone. These particular AdDisplay PUAs contain specialized self-protection functionalities that not only make the removal of the app from the Android device more difficult, but also help it evade detection by Google Bouncer in the first place.
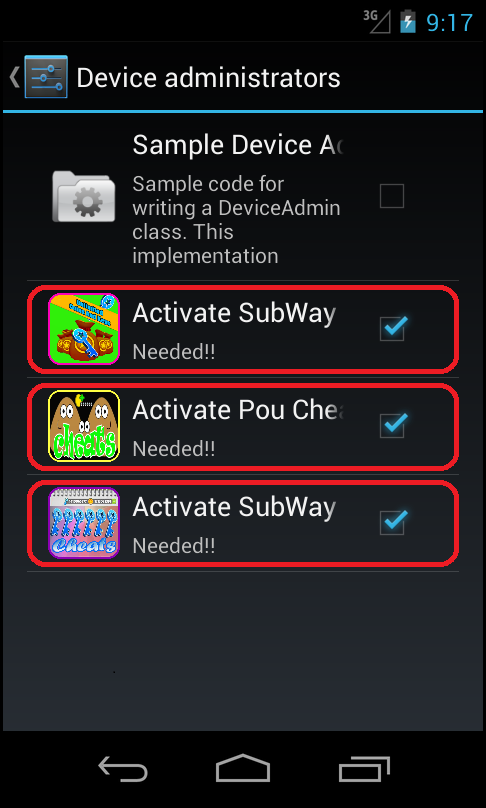
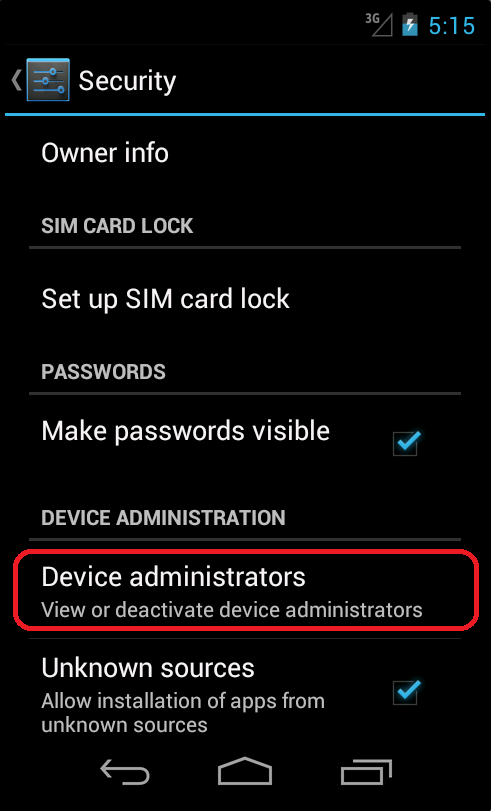
When users realize that the apps are exhibiting very unusual behavior and try to uninstall them, they will find that this is far from easy – the apps will ask the users to activate the device’s administrator rights. Thus, users may have difficulty with removing this AdDisplay threat. This PUA also uses an interesting anti-Bouncer technique to avoid being blocked by the Bouncer filter before it is released on Google Play.
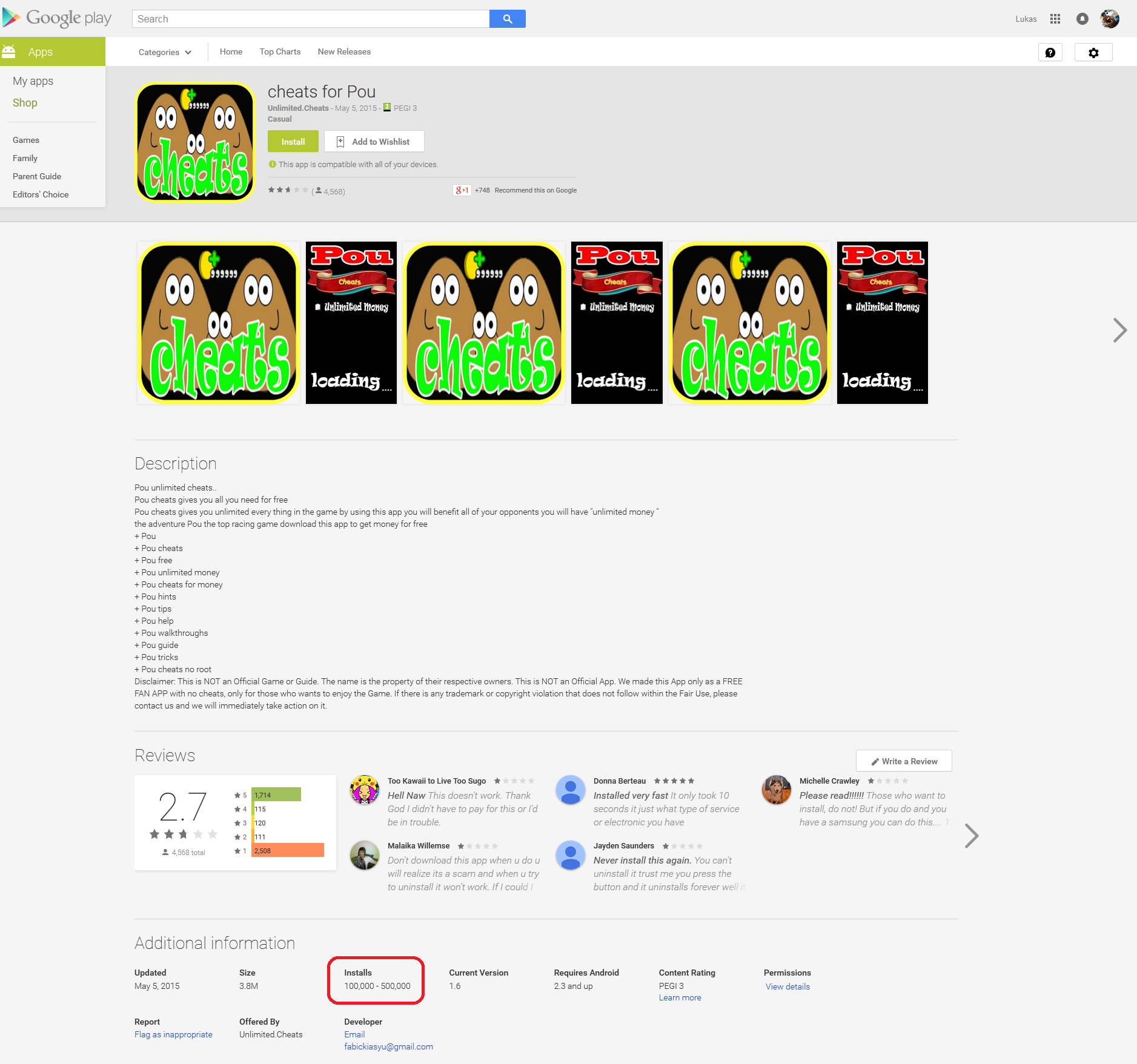
Figure 1: Malicious ‘Cheats for Pou’ from Google Play Store
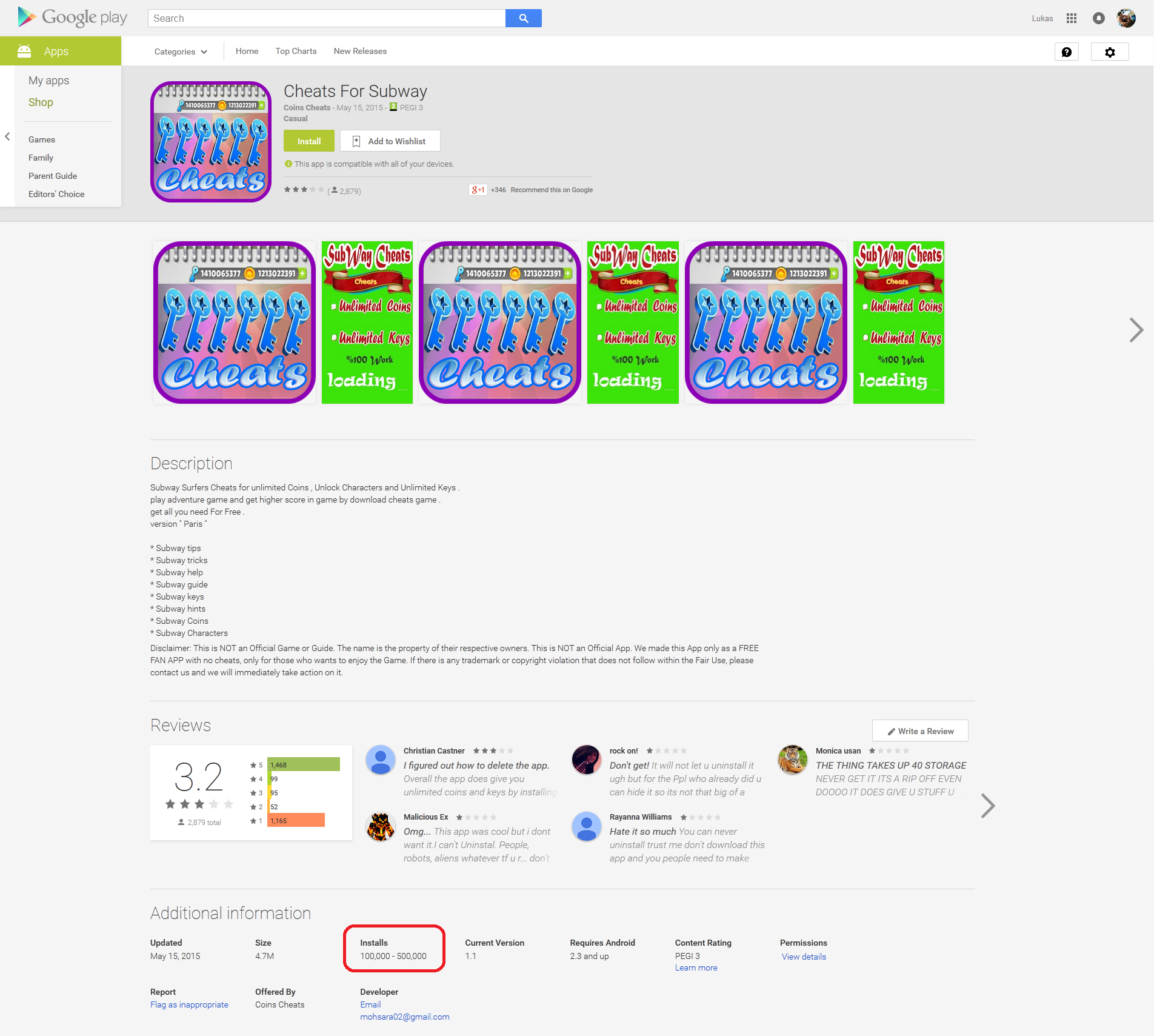
Figure 2: Malicious ‘Cheats For Subway’ from Google Play Store
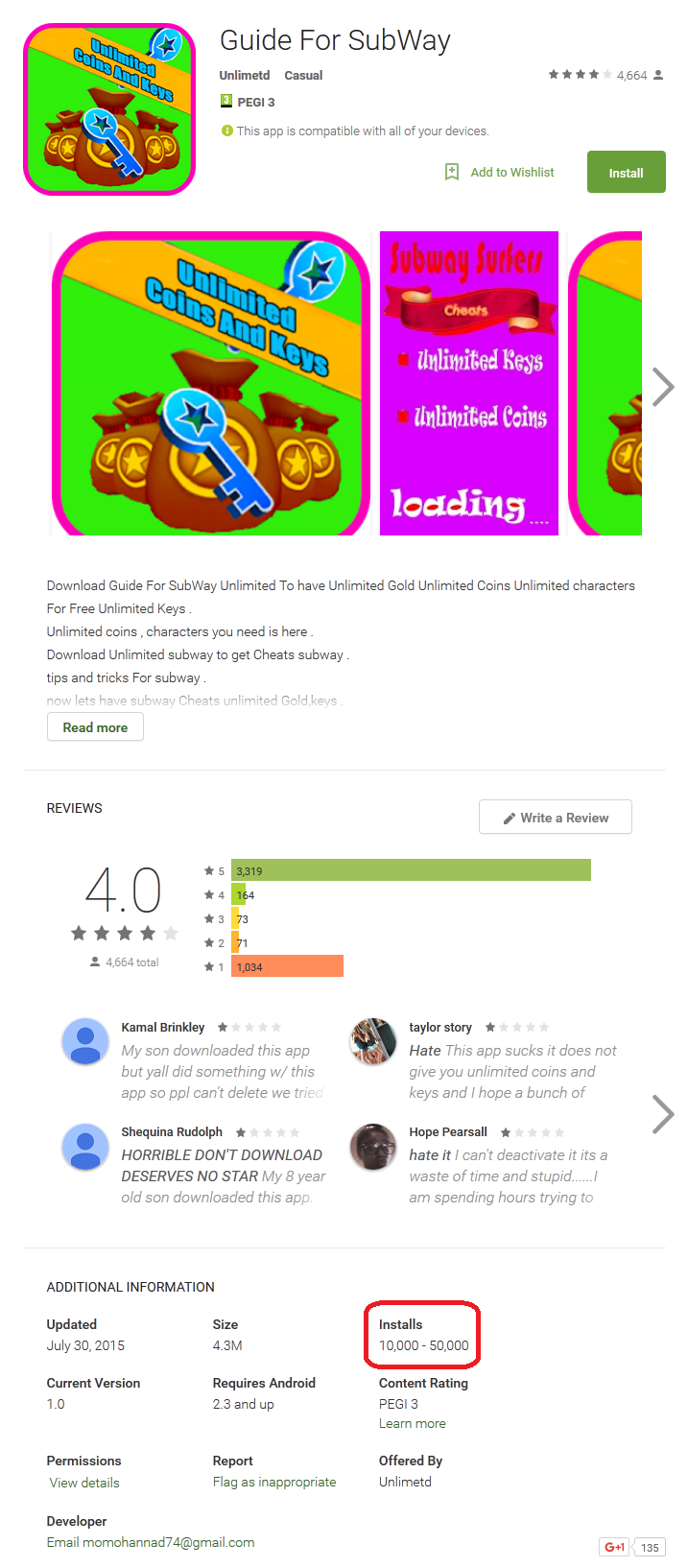
Figure 3 Malicious ‘Guide For SubWay’ from Google Play Store
These unwanted applications were removed from Google Play after we notified Google of the problem. ESET's security software detects this unwanted application as Android/AdDisplay.Cheastom.
Analysis – when WHOIS returns the string "Google", no ads will be displayed
When analyzed, AdDisplay.Cheastom turns out to be an unusual type of infiltration from more than one point of view. Because the app requests device administrator rights, it is not easy for users to uninstall it from the device. After activation it will try to detect whether it is executed in an emulator or from Google's servers (Bouncer).
The anti-Bouncer technique used by this AdDisplay is rather interesting – It will obtain the IP address of the device and check the IP's WHOIS record. If the information returned contains the string ‘Google’, then it assumes that it is running in Bouncer. If the app detects an emulator or Bouncer environment, then the actual payload (displaying of ads) won’t be initiated. Instead, the app will continue with apparently innocuous behavior: game cheats will be displayed, as expected.
In the applications we discovered 'Cheats for Pou' and 'Cheats for Subway' are similar in functionality, even in the cheats they display. In fact, the authors were so lazy that instead of showing Pou cheats in Cheats for Pou, the app displays cheats for Subway Surfers. Based on that, it can be assume that showing cheats was not the main intention of the developer.
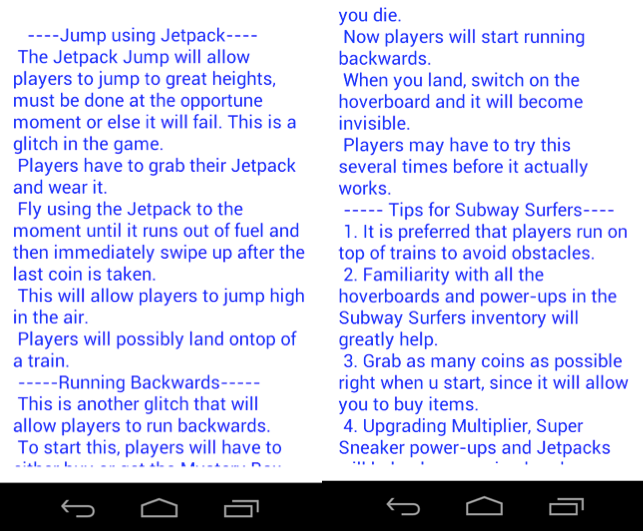
Figure 4: List of cheats displayed within apps
If a virtual environment was not detected by the apps, then they will set a scheduler for showing a full screen advertisement every 30 or 40 minutes. The functionality for displaying ads in cycles will start anyway, even if executed in an emulated environment, after the device is rebooted. After reboot though, full screen ads are shown each 45 minutes.

Figure 5: Some of the ads displayed
After an elapsed period of time, the applications make sure the device is connected to the internet. If it is, it asks the attacker’s server whether ads should be displayed.
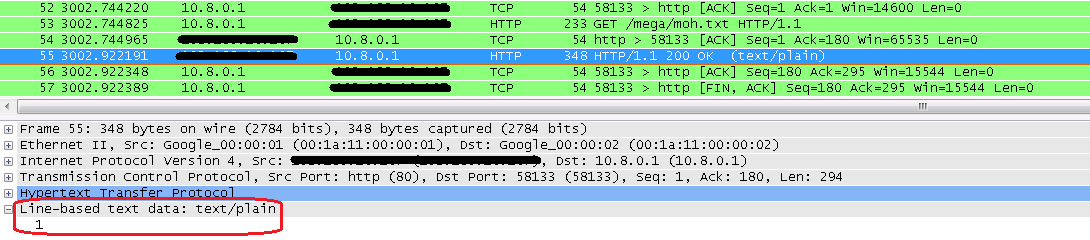
Figure 6: Communication with server
Getting rid of Android/AdDisplay.Cheastom
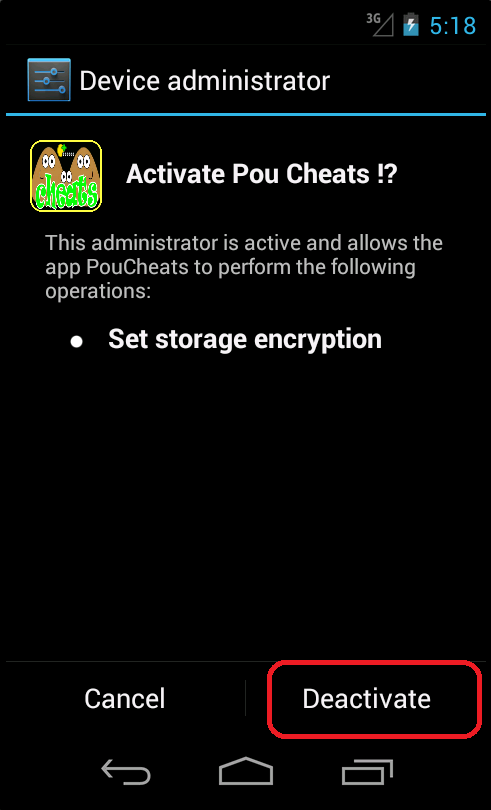
Uninstalling this application can be very difficult, as many users have mentioned in reviews. The application requests device administrator rights and can hide its own launch icon. The device user can find these apps in the application list, but it is not possible to uninstall them. When a user wants to remove these applications, they have to deactivate the device administrator before they can uninstall them.
If you are using ESET Mobile Security software on your device, it will deactivate device administrator and uninstall this threat for you, but first you need to have activated detection of Potentially Unwanted Applications from Advanced Settings. You can turn on this feature from Antivirus -> Advanced Settings -> Detect Potentially Unwanted Applications.
Figure 7: Detection of potentially unwanted applications
If you do not have security software installed, then you can deactivate and uninstall the PUA manually. The device user can apply this method not only to these apps, but to every non-system application they consider to be suspicious.
After deactivating device administrator, applications can be uninstalled by going to Settings -> Apps/Application manager -> Cheats for Pou/Cheats For Subway/Guid For SubWay.
Conclusion
These applications were designed to display advertisements, hiding themselves behind cheats for popular, heavily-downloaded applications. The interesting techniques used by these PUAs have allowed them to slip by Google Play's security filter, Bouncer. The apps’ malicious payload wasn’t activated if they detected it was running in an emulator, or on an IP address linked with Google’s WHOIS information. As a second technique for staying under the radar, the app behaved innocuously, unless the C&C server instructed the bot to display ads. This is one example when even an AdDisplay Potentially Unwanted Application could be very annoying and hard to uninstall from a device.
More information
| Package name | MD5 | ESET Detection name |
|---|---|---|
| com.Pou.cheats.coins.money | 0F30507207EF166A0939EA625FD79088 | Android/AdDisplay.Cheastom.A |
| com.SubWay.cheats.Keys.Coins.Money.Surfers | AA9F18CD5FCB2761CD83AFB1820B660F | Android/AdDisplay.Cheastom.A |
| com.sub.Gold.way.Money.Guid.apk | 5AA29495194113C39F1D34B0D49F9F52 | Android/AdDisplay.Cheastom.A |