The “Hacking Team” security company has been hacked and more than 400 GB of confidential info has been leaked by a group of unidentified attackers.
Normally, this would be just another report talking about one intrusion among all the others that we see every day in companies around the world. Hacking Team's status as a security firm, though, makes the leak something very different.
Selling surveillance tools
Hacking Team is known for being a developer of surveillance tools, selling them to countries and organizations all around the world. It's particularly controversial, then, to see its client list (among other info) being shared freely online, already appearing on a number of internet websites.
There is no doubt that the list of Hacking Team's clients is controversial, but first it has to be proven that this data is legitimate, something that we can’t say for sure right now.
Chronology of this attack
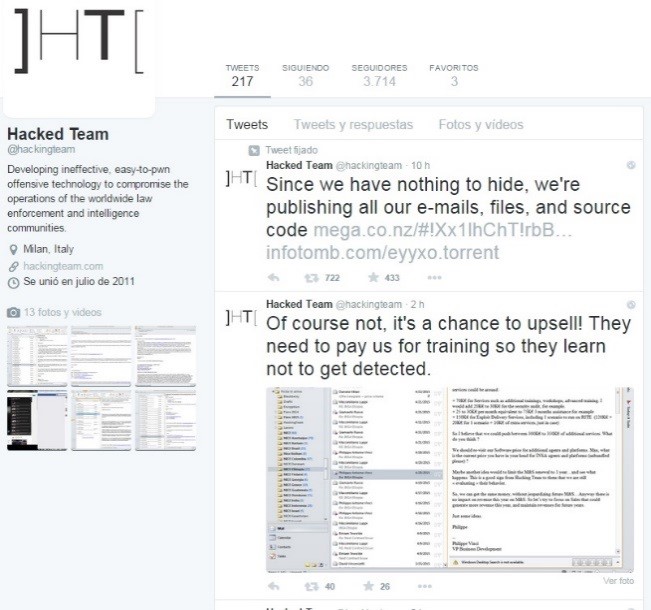
The attack apparently started last night, and it's possible that weak passwords might be responsible for the leak. Passwords are also contained in the leaked documents, including the login for the company's official Twitter account which was used by the attackers to publish confidential information. The attackers posted private emails from company employees to Twitter, as well as a link from where anybody can download the 400GB file.
Apparently, members of Hacking Team noticed the attack this morning when they woke up, including security engineer Christian Pozzi who declared, “We are awake. The people responsible for this will be arrested. We are working with the police at the moment”
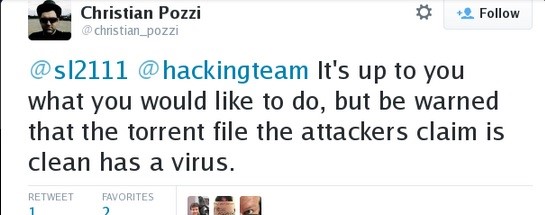
Regarding information leaked by the attackers, and quoting statements published by CSO Online, Pozzi said, “Don't believe everything you see. Most of what the attackers are claiming is simply not true...The attackers are spreading a lot of lies about our company that is simply not true. The torrent contains a virus..."
It’s not clear if Pozzi refers to this malware as something that the attackers added on purpose, or is referring to the surveillance tools themselves, that could be identified as malware. However, due to the high coverage of this news, we recommend being extra careful, and not trusting suspicious links promising access to the leaked info.
Back to Pozzi statements, he said that Hacking Team already warned its customers regarding this attack and that his company has done nothing illegal. “... We simply provide custom software solutions tailored to our customers needs...”
Conclusion
This leak proves that no company is free from suffering this kind of attack, not even if it’s working at the highest level in the IT security field. Just a mistake like using not-so-safe passwords can cause a catastrophe that undermines the trust of customers to such a low level that it may not be that easy to recover.