In many ways, small businesses are the powerhouse of the U.S. economy, a reality celebrated this week by a series of events, online and offline, coordinated as part of National Small Business Week. And what powers many small businesses today, in addition to the passion and hard work of owners and employees, is digital information and communication technology. These days, that technology -- from desktop PCs to mobile apps and cloud services -- is increasingly referred to as "cyber", and protecting that technology is the task of cybersecurity.
So this week seemed an appropriate time to publish a Small Business Cybersecurity Survival Guide, to outline the biggest risks that small businesses face in the cyber realm and how best to defend against the latest cyber threats. The guide contains strategic advice from ESET security experts on what precautions small businesses should be taking to protect themselves and keep vital data from falling into the wrong hands.
Perhaps the most important single thing that small businesses need to know about cyber threats right now is that cyber criminals are actively targeting smaller firms. I realize this can be hard to imagine or accept. After all, the security breaches we hear about on the news involve big brand names, like Target, Home Depot, Sony Pictures, and Anthem. The fact is, many breaches of smaller firms simply go unreported. So I often meet small business owners who are still wondering what on earth cyber criminals could want with their company's computer systems and the data they handle. There are several answers to this.
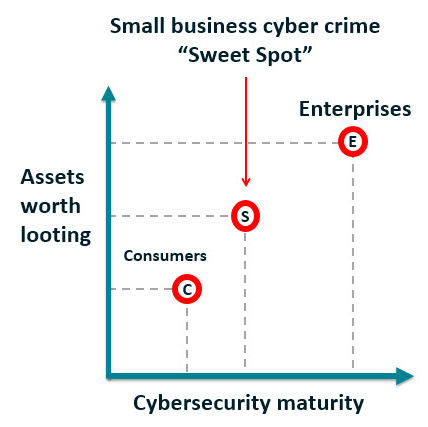 For a start, many small businesses have personal information about customers and employees that data thieves can sell on the black market. And although your small business might not have huge bankable profits at the end of the year, depending on your line of work you may handle a lot of money (for example, deposits and payments from customers that are not immediately spent on raw materials). But perhaps the easiest way to picture the current reality is something I call the "small business cyber crime sweet spot".
For a start, many small businesses have personal information about customers and employees that data thieves can sell on the black market. And although your small business might not have huge bankable profits at the end of the year, depending on your line of work you may handle a lot of money (for example, deposits and payments from customers that are not immediately spent on raw materials). But perhaps the easiest way to picture the current reality is something I call the "small business cyber crime sweet spot".
As you can see from the picture on the right, small businesses generally have more assets worth looting than consumers (whether it is bank funds, personal identity data, or intellectual property in digital format). On the other axis, you can see that small businesses generally have less maturity than large enterprises when it comes to cybersecurity. Simply put, small businesses often have a lot to lose, but a lot less protection in place than larger firms. Naturally, that combination is very appealing to some sectors of the cybercrime industry.
While cybersecurity can be intimidating, a methodical approach to addressing cybersecurity can be very effective in reducing your risk profile. The small business cybersecurity survival guide lays out an "ABC" approach that goes like this:
- Assess your assets, risks, resources – Know what you need to protect, understand the threats, and identify resources.
- Build your policy – Spell out your organization's approach to security as policy, and ensure leadership prioritizes security.
- Choose your controls – Decide what controls and tools are most appropriate to enforce your security policies.
- Deploy controls – Put controls in place.
- Educate employees, execs, vendors – Gain security buy-in from the full team and let folks know: cybersecurity is everybody's responsibility.
- Further assess, audit, test – Stay on top of security trends, conduct tests of your security, and make sure new projects are included in policy.
As you can see, getting a handle on cybersecurity is a multi-stage process, and this process is ongoing: at stage F you go back to A. This is the only way to keep up with emerging threats and the many ways in which your growth as a small company changes your exposure to cyber risks. For example, cybersecurity risk changes as you go from running the company as a one-person operation, to maybe a few trusted co-founders, to an employer of people you never met before they applied for a job with you (and when you reach the point where an employee leaves your organization, the right security policies become especially important).
You can download ESET’s comprehensive Small Business Cybersecurity Survival Guide here. We hope that you find it helpful.
Also, later this week, please join my colleague and fellow security researcher Cameron Camp on May 6, 2015 for a free webcast that explores BYOD, mobile device management and other security topics of particular concern to small businesses.




