ESET Senior Research Fellow David Harley credits his academic background in social sciences with his long-running interest in the social engineering behind cybercrime.
"Viruses have practically disappeared. Now that’s a very small part of the whole malware thing."Although he states that scams and social engineering have been a constant in cybercrime, in the past few years, some scams have got markedly more sophisticated, and more difficult even for a trained eye to spot.
"A lot of criminal activity makes at least partial use of social engineering. It’s been a constant all through the life of internet security." Changes in the way malware is propagated has led to an increase in the importance of social engineering, he explains.
"When I first got into this stuff, about 25 years ago, it was mostly virus management," he says. "I got pulled into dealing with the scams simply because it was something that wasn't viruses. Anti-malware was simple in concept - it looked for whether code self-replicated or not. But viruses have practically disappeared. Now that’s a very small part of the whole malware thing."
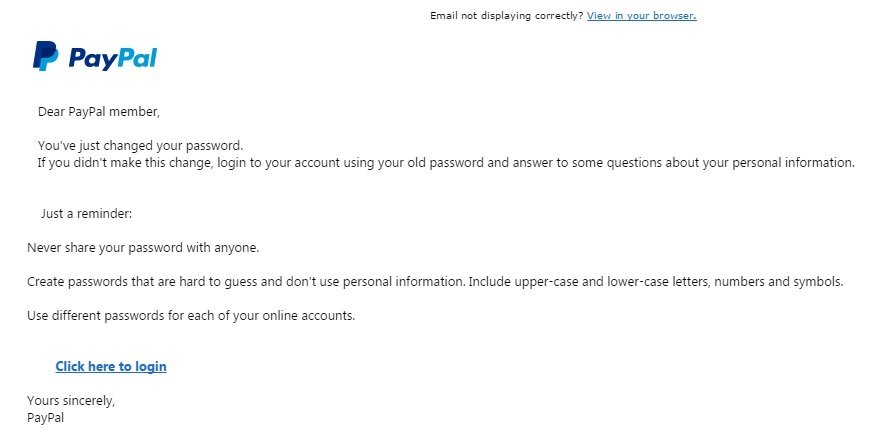
Some phishing emails even prey upon people's fear of being hacked.
"As less and less malware has been self-replicating, so it's become more important for malicious code to propagate in other ways. Social engineering is easier in a lot of ways than a technically sophisticated, code-based attacks like some drive-bys. In many cases, even a drive-by attack still has to attract people into visiting a malicious site."

Over his 25 year career, ESET's David Harley has seen scams become increasingly sophisticated.
Scammers have diversified far beyond poorly spelled, purely text-based phishing email these days, Harley says, building entire fake websites and Facebook pages as lures for campaigns. But even the humble phish email has evolved.
Harley says, "While sometimes you can still spot a phish a mile off, some phish are much more technically sophisticated. Real banks and building societies also actually make phishing easier for the scammer - by using language which scammers might use, and even adding embedded links that aren't clearly identifiable as the institution’s own domain. It makes it more difficult for a reader without experience or specialized knowledge to tell which is which."
While researching a recent blog post on cold-calling scams, Harley says he found that the scammers have changed their methods markedly in just the past few years. The ‘classic’ cold call scam where scammers pretend to be IT workers from Microsoft is now just part of the business, he says.
"Real banks and building societies actually make phishing easier for the scammer - by using language which scammers might use, and even adding embedded links that aren't clearly identifiable as the institution’s own domain."Harley says, "When it comes to support scams, you can definitely see in an increase in sophistication and diversification over the years. The change has been pretty dramatic since 2011. Rather than scammers simply calling and saying you have a problem with Windows, you can often find them seeding Facebook pages and search engine results so that someone with a problem will ring the scammer rather than vice versa. In other approaches to scamming, your phone might ring someone will say, ‘We understand you had a motor accident. We can get you compensation’ in the hope that you’ll be someone who really has had that experience.’"
Harley says that industries have grown up around the scams - including rogue website designers building ‘lures’ for the scammers’ use.
We are seeing increasing volumes of reports of websites supplying templates for pages luring people into ringing a call center - rather than the call center cold-calling a victim, people are lured in via Facebook pages, web sites and pop-up messages.’

Even scam phone callers have upped their game, using fake websites and Facebook pages to create a 'legitimate looking' online presence.
For victims, there is still little by way of a technical defense against the scammers, bar keeping one’s wits about one while using the internet - but there is a lot more information online to help, Harley says, as well as a few ways for victims to strike back.
"A lot of my data still comes from comments on blogs I have already written. You do hear about people who turn the tables and manage to keep scammers on the phone for 20 minutes or longer."Microsoft and SANS now offer forms to report scam incidents," he says. "But a lot of my data still comes from comments on blogs I have already written. You do hear about people who turn the tables and manage to keep scammers on the phone for 20 minutes or longer - it sounds like tremendous fun, but I don’t recommend that people go that route unless they know exactly what they’re doing. In particular, they shouldn't be allowing the scammer any access to their systems unless they know for sure that they can recover from any attempt to trash the system. In many cases, the scammer will do this out of sheer malice if he thinks he’s not going to get the payment he’s after."




