If you have recently received an unexpected email with a ZIP file attached, it could be a threat attempting to steal your banking login credentials. Its name is Waski and is detected by ESET as Win32/TrojanDownloader.Waski.
Waski is a so-called Trojan downloader. This is usually a small program that downloads additional malware that then is launched on the computer. According to our recent statistics, Waski is one of the most detected threats. After detection spikes in Switzerland and Germany a few weeks ago, we now observe English-speaking regions affected with this threat, in Australia, New Zealand, Ireland, United Kingdom, Canada, and the United States, among others.
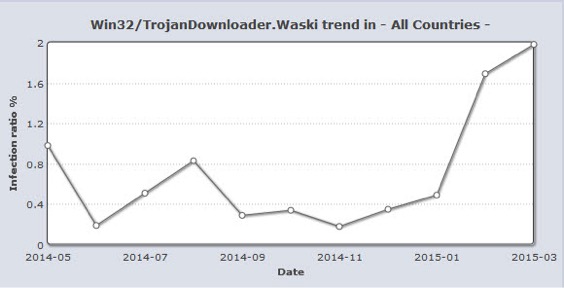
Win32/TrojanDownloader.Waski trend - Virusradar screenshot from April 2nd 2015
Since the beginning of 2015 we have seen a significant increase in these detections. This is no coincidence as more and more criminals are using Waski to spread their malware on the Internet.
It all starts with a seemingly harmless email
A potential victim receives the threat packaged in a ZIP file as an attachment to a spam email. The subject of the email is written in English, as well as the content, which often consists only of a single short sentence:
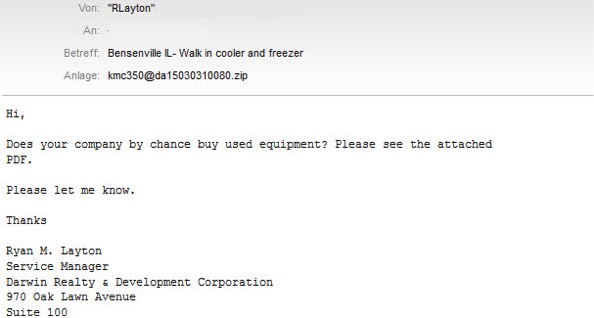
The figure above shows a typical e-mail as spread by Waski. In this case, the e-mail was allegedly sent by a company. The attachment contains a ZIP file containing Waski as an executable file. When started, it downloads other malicious software from a predefined web address.
Waski downloads online banking trojan
Waski is widely used by criminals to spread their malware and thus downloads a variety of malware. The particular one we investigated here downloads the banking Trojan Battdil, which is detected by ESET as Win32/Battdil or Win64/Battdil. We have also written earlier here at We Live Security about this banking Trojan targeting users of the Bank of America, and about other phishing emails against British users; such similar attacks have also been described at Phishme.com.
Waski comes in the form of an executable file with the icon of a PDF file. Once it’s started, the malware first checks the victim's public IP address by requesting it from checkip.dyndns. Using the IP and other information of the victim's computer (computer name, Windows version, and service pack number), a unique identification number is calculated and then sent to the Waski command-and-control server (C&C).
Then Waski downloads an encrypted file (usually from a compromised website) that has a PDF file extension. But it is not a true PDF file; instead, it is a merge of two files: the malware Win32/Battdil and a regular PDF file. After that, Waski again contacts its C&C server and reports the successful compromise.
What does Battdil do?
Win32/Battdil consists of two parts: an injector and a payload. The injector consists of an EXE file, and the payload contains a DLL file that is stored in the original file. Often, the task of the injector is to inject the payload using DLL injection into a Windows process, as we see here with Win32/Battdil.
The payload of Win32/Battdil now begins its work. It has the ability of intercept the login credentials for online banking in many of major browsers like Internet Explorer, Firefox, Chrome, etc. In addition, the websites of banks can be manipulated so that the victim does not get to see the original website, but a modified version. Therefore when they visit the website, some additional information is required such as the PIN Number from the credit card, which is then sent to the attacker. The collected information is sent encrypted via SSL to the C&C server. Win32/Battdil also has the ability to connect to its C&C server anonymously using the Invisible Internet Project (I2P).
Conclusion
Waski was first discovered at the end of 2013 and has become increasingly popular because criminals can use it to spread their threats in Europe and North America. So if you are receiving emails with attachments of unknown sources, avoid opening them and always use a security software in order to keep your computer safer. Finally, keep in mind that Waski is the Trojan Downloader that is used to compromise your system with other threats. That said, attackers can use different malware in their attempt to target users, which means stealing banking credentials would be only one of many actions they could take in a compromised computer.
Hashes
Win32/Waski
1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7 (SHA-256)
Win32/Battdil
Injector: 9b313e9c79921b22b488a11344b280d4cec9dd09c2201f9e5aaf08a115650b25 (SHA-256)
Payload: f8eccfebda8a1e0caabbe23a8b94d7ced980353a9b3673a4173e24958a3bdbb9 (SHA-256)
Research collaboration from Dominik Reichel