Its been just under three weeks since February 19th, when Lenovo became entangled in a web of controversy over its preinstallation of Superfish's Visual Search adware on some of its popular consumer laptops during last year's holiday shopping season.
Previously, I have remained very quiet on this subject, not because of my position as ESET's Distinguished Researcher or because I am a Microsoft MVP, but because for the past several years I have been volunteering in my spare time to help answer questions in Lenovo's online support forum, as well as answering questions via social media. As such, I have been in a rather unusual position of being able to see what has been happening, from both the viewpoint of a computer manufacturer that had distributed adware, to that of a company dedicated to preventing it. It has also been a difficult position for me to be in: Over the past couple of weeks there have been numerous occasions where one party has shared information that would be very useful to the other, and I have been unable to inform the other party because it was shared in confidence
Last week, through having a foot in these two worlds, I had a unique opportunity to videoconference with Lenovo Group's CTO Dr. Peter Hortensius for an hour. Based on those discussions, and following Lenovo's new promise on Friday, I feel it is time to comment publicly on the issue.
Now, I am not going to delve into the technical details of this adware since my colleague Stephen Cobb has discussed the Superfish adware in detail in this blog post, and ESET's knowledgebase team has done their usual excellent job here, so what I am going to do, instead, is take a look at Lenovo's response.
Note: you can download a standalone ESET Superfish cleaner here.
Timeline
Initial reports of problems with Superfish Visual Search began to appear in Lenovo's support forum during September and October of 2014. In January, Lenovo discontinued preloading Superfish onto consumer laptops as well as disabling the connections to servers it used. This information was shared by Lenovo in their initial statement on Thursday, February 19th.
On the same day, an interview with Dr. Hortensius was posted in the Wall Street Journal's blog, in which he seemingly downplayed the risks associated with the adware, suggesting they were more "theoretical concerns" and then went on to explain that Lenovo would be doing more in the future to vet what software was preloaded on its computers. This comment ignited a firestorm of controversy amongst members of the security community, many of whom were concerned not so much with the adware per se, but that it injected the same trusted root certificate authority into every computer on which it was installed. Instructions on how to obtain the certificate manually appeared online on February 19th as well, and turned out to be from an SDK offered by another software vendor named Komodia. ESET added detection for the adware on this day, too.
On Friday, February 20th, Lenovo issued a second statement on Superfish, announcing that they were providing a tool to uninstall the adware, as well as working with both Microsoft and McAfee to provide automatic detection and remove of both the Superfish adware and its certificate. Source code that could be used to automate decryption using Superfish's certificate began to appear online as well. As of today (March 9th), we have not seen that code weaponized into malware or attack tools.
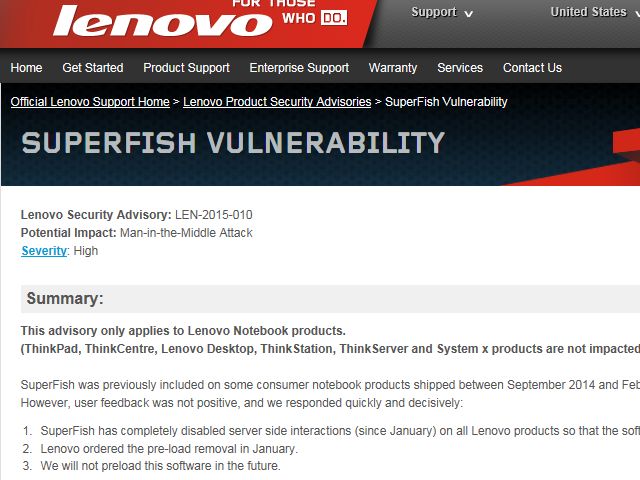
Figure 1: Lenovo PSIRT advisory
The Lenovo PSIRT (Product Security Incident Response Team) also published Lenovo Product Security advisory LEN-2015-010, Superfish Vulnerability, which focused not on the characteristics of the Superfish adware but on the risk that its self-signed root certificate could lead to HTTPS traffic interception. In conjunction with this, Superfish Uninstall Instructions were published, giving an automatic tool to uninstall the software and its certificate, as well as manual instructions to do so. Lastly, Lenovo released the source code for its automated uninstall tool under the MPL public license.
On Monday, February 23rd, Lenovo issued a third statement, an open letter from Dr. Hortensius affirming that Lenovo had ceased doing business with Superfish, that it would not preload the adware again on computers, that Symantec had updated their software to detect and remediate it, and that Lenovo was working on a plan to address these issues in the future.
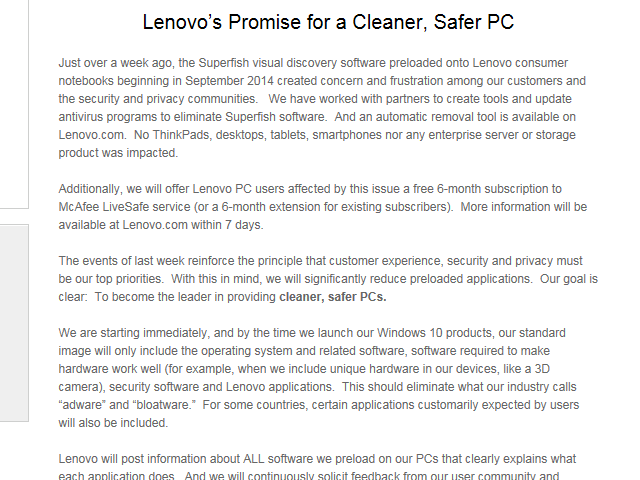
Figure 2: Lenovo's February 27th news release
On Friday, February 27th, Lenovo announced its promise for cleaner, safer PCs. In it, they announced they would begin changing their practices to preload only software necessary for the operation of the computer (the operating system, related software, device drivers, plus programs necessary to take advantage of hardware not supported by the operating system). However, third-party security software would still be preloaded onto systems, as well as programs which are a requirement for certain markets on a country-by-country basis. Microsoft is not always the preferred browser nor is Google the top search engine in some regions of the world, and Lenovo has to ship systems which reflect these realities. But most importantly, "adware" and "bloatware" would no longer be a part of the Lenovo PC experience.
Evaluating Lenovo's Response
So, how well exactly did Lenovo do with their response? Through the fourth quarter of 2014, there was no response from any part of the Lenovo community, beyond comments from users in their forum ranging from suggesting the de-installation of any unwanted software to advocating the wiping of the drive and installing a clean copy of Windows, and so forth.
While it may seem that such comments could have served as some sort of warning to Lenovo that something was amiss, it is important to note that these types of complaints and responses are not unique to Lenovo or Superfish. A quick search of the support forums of Hewlett-Packard and Dell, two of Lenovo's competitors, reveals similar complaints about their preloaded software:
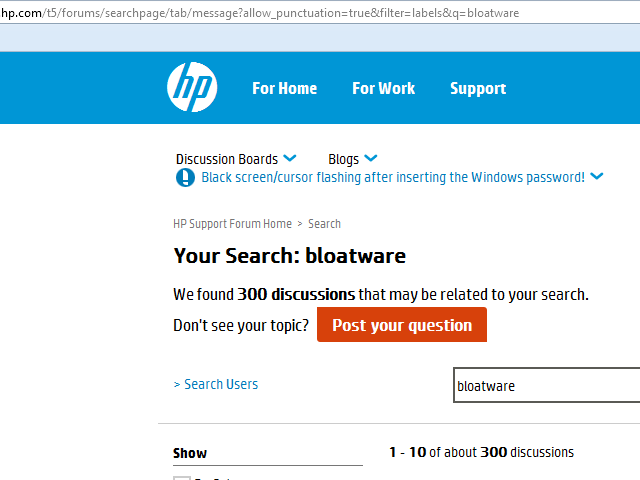
Figure 3: Search results from Hewlett-Packard
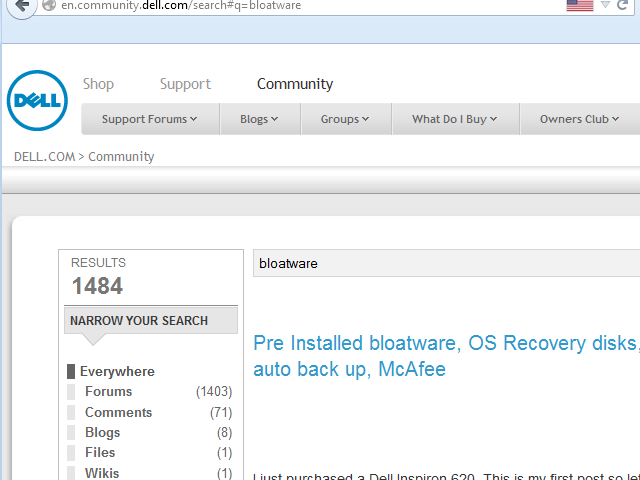
Figure 4: Search Results from Dell
It is reasonable to state that while some may consider Lenovo's initial response lackluster, it is not particularly unique unusual, either. The problem with computers being preloaded is not unique to Lenovo, but rather an industry-wide problem, dating back many years. A discussion of the reasons behind it fall out-of-scope for this article, but I would refer you to two fascinating articles by journalist Ed Bott for more information, How a decade of antitrust oversite has changed your PC and Is it time to force PC makers to disclose how much they make from crapware?. The law of unintended consequences, as Bott called it, is indeed very longlived.
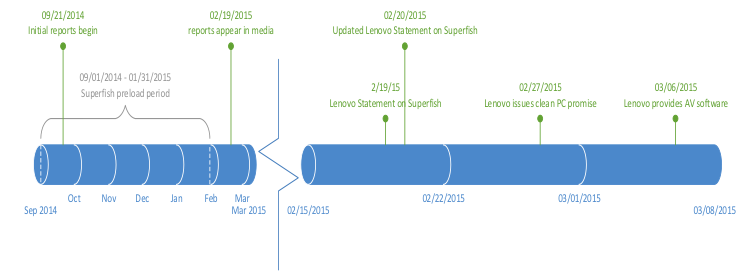
Figure 5: Lenovo timeline
Starting on February 19th, and over the course of the next eight days, Lenovo went from having seemingly fumbled its initial response, to issuing four press releases, revising its security advisory four times, and at least half-a-dozen changes to the source code for its automated removal tool, culminating in their February 27th pledge to clean up their PCs. Here are some of its highlights:
- Lenovo has worked with partners to create tools and update anti-malware programs to eliminate the Superfish adware and trusted root certificate.
- Beginning immediately with Windows 8 and going forwarding into Windows 10, Lenovo's standard computer image will contain only the operating system and related applications (device drivers, software to make use of unique hardware not supported in the operating systems, security software and Lenovo's own applications).
- Lenovo will share information with customers about all preloaded software, explaining clearly explains what each one does.
- Lenovo will continue to work with their user community and industry experts to ensure only appropriate applications are installed and that they provide the best user experience.
For a global company with over 50,000 employees, accomplishing all of these actions in eight days is impressive.
The Undiscovered Country
So, where does this leave Lenovo's current and prospective customers?
Given the way the retail channel works, it is possible there may still be a few computers out there with the Superfish adware and trusted root certificate preloaded. Customers who buy one of these machines can remove them using a variety of means, ranging from following Lenovo's own instructions to making use of anti-malware programs.
By now, almost all reputable anti-malware programs should be effective in removing the adware and certificate from affected computers, but it's important to remember that if the operating system is restored from a recovery partition or from recovery media, removal will need to be repeated after the system has been restored. While this is unlikely to be a major problem since Superfish will be caught and removed as the system updates, it will be a recurring issue for as long as the recovery image contains the Superfish adware.
For businesses (or individuals) who buy business-grade systems, such as Lenovo's Think-branded systems, this never was an issue: The Superfish adware was only preinstalled on some of Lenovo's consumer laptop offerings. Business-grade systems, whether from Lenovo, Dell, Hewlett-Packard or other manufacturers, are marketed differently than their consumer lines. They tend to have features such as more rugged construction, easy-access chassis for quick repairs, support for remote monitoring and management tools, and have a minimum amount of third-party software preloaded on them. They also cost a bit more, too, because of these features.
Just as it is important to note the models of Lenovo computer that were affected, it's also important to note that some of the affected consumer models shipped without it during the time-frame. In particular, Microsoft's own online and retail stores sell what they call Signature Edition PCs, which consist of computers from a variety of manufacturers, including Lenovo. These are sold without any preloaded third-party software, and as a result may be faster than the same models when bought from the manufacturer because fewer programs automatically run when the computer is started. They may also be priced slightly higher, too. This varies, though, based on promotions and discounts.
For consumer customers who were considering systems from Lenovo and may now be having second thoughts, all is not lost for you: As Lenovo's promise for clean PCs unfolds, you will be in a position to reap its benefits. While they will likely come preloaded with some third-party anti-malware software, if it is a brand you do not favor, you should have no trouble uninstalling and replacing it with software from your favorite security vendor.
Aryeh Goretsky, MVP, ZCSE
Distinguished Researcher
Did the last computer you purchased come with unwanted software on it? If so, what was it and how did you deal with it? What do you think of Lenovo's response? Is it enough, or are there more steps you feel they should take? Let us know in your comments, below.




