The notorious Syrian Electronic Army hacking outfit has once again claimed the scalp of a media outlet, hacking the Twitter account of the French newspaper Le Monde overnight.
In light of the recent killings in Paris, the message that the Syrian Electronic Army (SEA) chose to post from the newspaper's @lemondefr Twitter account couldn't have been any more inappropriate.
Here is a screenshot of what was published on the account, as reposted by the SEA:
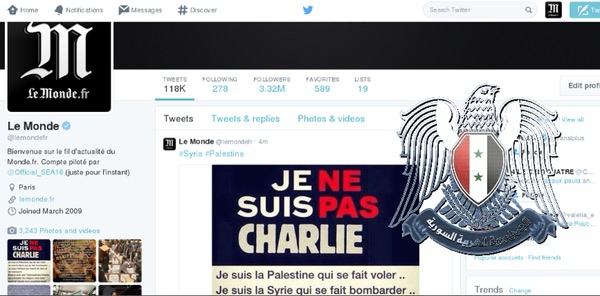
"Je Suis Charlie", of course, is the slogan adopted by free speech supporters around the world following the killings earlier this month, which saw 12 staff of the satirical newspaper Charlie Hebdo shot dead.
Another rogue tweet in French by the SEA to the Le Monde account claimed - in traditional graffiti artist fashion - that the "Syrian Electronic Army was here".

Fortunately, the messages posted by the Syrian Electronic Army were just digital graffiti. They could have easily deliberately pointed some of Le Monde's 3.1 million Twitter followers to malicious websites that could have infected their computers with malware, or attempted to phish their passwords.
Similarly, we have seen Twitter hijacks in the past, where bogus breaking news stories of explosions at the White House have actually lead to share prices falling.
I guess we should be grateful for little mercies.
According to a statement from Le Monde, the account was temporarily suspended by Twitter once it was realised that it had become compromised, and only restored a few hours later.
Apparently, on Sunday and Monday Le Monde's teams managed to counter another attempted attack by the hackers, where they attempted to publish an article and gained access to various staff's mailboxes.
Tough questions should now be asked as to why Le Monde's Twitter account wasn't better protected.
It's not as if the Syrian Electronic Army's methods for hijacking Twitter accounts are shrouded in mystery.
Their typical modus operandi is to send emails to journalists, perhaps from another publication or colleague, claiming to be a link to a breaking news story. When the intended victim clicks on the link they are taken to a page which attempts to phish their password.
Once the SEA has its paws on the journalist's password they might be able to access the journalist's email remotely, and dig out the passwords for their social media account. Alternatively, they may have simply asked for the Twitter password at the point of phishing.
Often stolen passwords will be used at a variety of social media sites, to see if the organisation has made the mistake of reusing the same password.
If you have your Twitter account protected with two factor authentication, the username/password is not enough for an unauthorised user to gain access - as they won't also know the one-time-password.
Things get more complicated, of course, if you have a large number of people logging into the same account - which is possible if you are a media organisation or representing a brand online.
All of us, whether we are working for a news outlet, a company, or simply representing ourselves online, need to be on the lookout for phishing emails and always think twice before entering our passwords on a suspicious webpage.
Where possible, use two-factor authentication and password management software to harden your accounts and make it easier to handle different passwords for different websites.





