APT actors trying to use big events as a lure to compromise their targets is nothing new. Tibetan NGOs being targeted by APT actors is also nothing new. Thus, surrounding the upcoming G20 2014 summit that is held in Brisbane, Australia, we were expecting to see G20 themed threats targeted at Tibetan NGOs. A Win32/Farfli (alias Gh0st RAT) sample ultimately confirmed our suspicions.
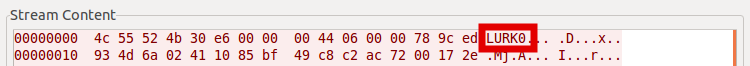
Gh0st RAT is an off-the-shelf RAT that is used by a variety of threat actors. It has been used in the past in numerous targeted campaigns as well as crimeware-like operations. The sample we were looking at had a very low number of detections amongst our users: only two hits in China. After a quick dynamic analysis, we saw that the magic word used in network communications by this sample is “LURK0”, instead of the infamous “Gh0st”. This particular magic word has been used against Tibetan groups in the past.
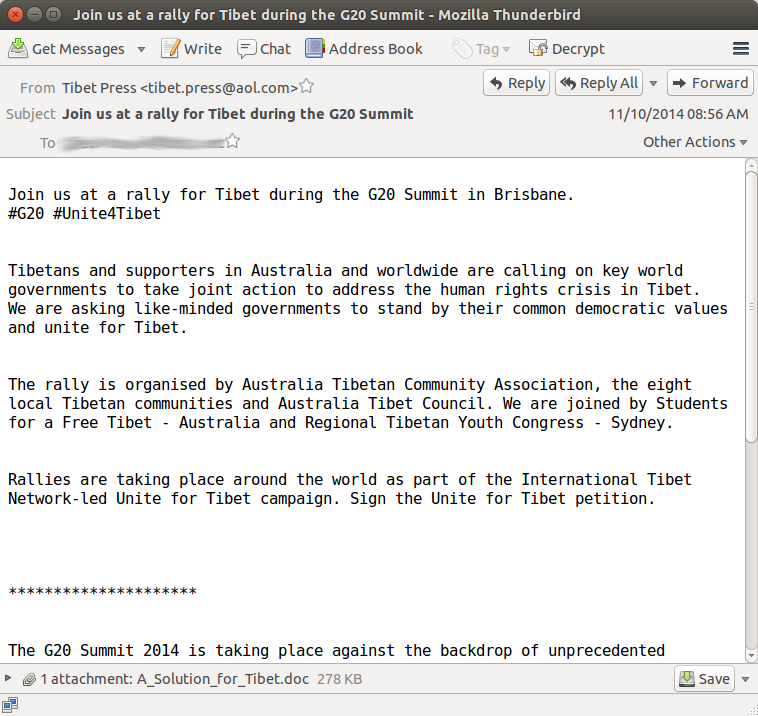
Digging a bit deeper, we were able to recover an email that delivered this threat on VirusTotal.
This is a pretty classic case of spear phishing email. The malicious actor is trying to lure the user into opening the infected attachment by using a rally that is organized by the Australian Tibet Council. In fact, the email text was taken directly off their website. This email was allegedly sent to the European Central Tibetan Administration.
After analysis, the word document, entitled “A_Solution_for_Tibet.doc”, is exploiting CVE-2012-0158, a very old exploit that is still reliably used by malicious actors to compromise systems around the world. If the document is opened, it will try to install Gh0st RAT in the following folder (on a Microsoft Windows XP system): C:\Documents and Settings\Administrator\Application Data\Micbt.
Once installed, the RAT will try to connect to the following two domains:
- mailindia.imbss.in
- godson355.vicp.cc
Interestingly, the second domain has been seen in targeted attacks before.
While we do not have enough information to make any serious attribution, this attack has several elements that are usually seen in targeted attacks. As these attacks are nowadays very common, a few words of caution are in order. It is important to remember to avoid opening email attachments sent by unknown senders and to keep software installed on its computer up-to-date. NGOs Members with a political, religious or environmental agenda have been targeted in the past and will most likely continue to undergo continuous attacks in the future. In the light of constant attacks against them, they should definitely be as cautious as one can be when these types of emails are received, especially when popular themes or news events are used as a lure.
Indicators of Compromise (IOCs)
- Sender: Tibet Press <tibet.press@aol.com>
- Subject: Join us at a rally for Tibet during the G20 Summit
Word Document
- Name: A_Solution_for_Tibet.doc
- SHA1: b16900da71052b4acf4afb8b1b230d500c99460a
Win32/Farfli
- Dropped in C:\Documents and Settings\Administrator\Application Data\Micbt on Microsoft Windows XP Systems
- Fiel name: RasTls.exe
- SHA1: 4ead7c11f81b101555b27a14e00ecdf7baa7d42f
- Domains contacted:
- mailindia.imbss.in
- godson355.vicp.cc