Edward Snowden's public revelations of mass surveillance conducted by the U.S. National Security Agency began one year ago today: June 5, 2103. Since then, the scope of the revelations has expanded to cover activities by the UK's GCHQ, efforts to weaken encryption, and the spread of malicious code by the NSA, including malware implanted in IT hardware as it being shipped to customers from manufacturers like Cisco. Revelations continued this past weekend with a look at how the NSA looks at people's faces.
Pre-Snowden and Post-Snowden

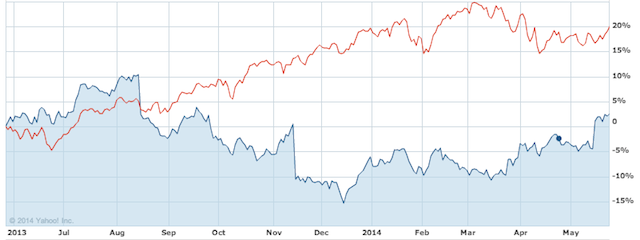
Photo from an NSA PowerPoint slide showing a Cisco product box being opened in preparation for an "implant" of malicious code, without the knowledge of Cisco or its customer. Read on for a chart of Cisco's stock since 6/5/13 compared to the NASDAQ
I don't think it's hyperbolic to predict that the history of computer security and data privacy will henceforth be referred to as two eras, pre-Snowden and post-Snowden. Frankly, the increase in general public awareness of, and interest in, a whole raft of security and privacy related issues over the last 12 months has been staggering.
As regular readers of these pages will know, we've been striving to raise security and privacy awareness for years, along with many of our colleagues in industry and non-profit organizations. Then suddenly, essentially through the actions of one person, people everywhere want to know more. Without making any value judgments about Snowden's actions it is hard to deny that he has done more to raise awareness of digital security and privacy issues than anyone else, ever.
Ironically, much of what Snowden revealed was not exactly news to folks who have been in the information security business for a while, people who have read the works of Jim Bamford, or met with earlier whistleblowers such as William Binney, or have friends who worked at NSA and related agencies like the NRO (historically more heavily funded than the NSA).
What had been lacking before Snowden was widespread interest in what these agenices were up to in the realm of mass surveillance, malware distribution, and weakening of encryption. Apparently, the world was waiting for convincing documentation, documents of a type and quantity that the government could not deny, namely a bunch of PowerPoint slides! (Again, the irony is not lost on those of us who have spent countless hours creating hundreds of security awareness slides of our own over the last 20 years -- yes, PowerPoint is that old.)
Something about seeing those slides, which often expressed the great enthusiasm with which the agency seemed to be pursuing "all personal data from everywhere", connected with many people who had previously preferred not to think about these things. However, powerful as they were, those slides were not the only pictures that made an impact. Consider this chart of the price of Cisco shares relative to the index of the NASDAQ on which it trades. Suspicion around the integrity of Cisco products, raised by revelations about several different NSA/GCHQ programs, took their toll.
Historic impacts
It was on June 5, 2013, that the Guardian newspaper put the first story online: NSA collecting phone records of millions of Verizon customers daily. As you can see from the date on that page, the story first appeared in print on June 6, but the paper's own NSA timeline records the June 5 electronic publication. The PRISM story, the one that showed surveillance cooperation with NSA by tech companies like Google, Apple, and Facebook, broke on the 6th. (If you want the hour-by-hour narrative of how the documents came to be published, read "No Place to Hide" by Glenn Greenwald, it's fascinating stuff.)
The effects of those articles, and the many others that followed, often illustrated with classified PowerPoint slides, are too numerous for one blog post to cover. However, a number of articles on We Live Security have addressed several different impacts, starting with changes in Internet behavior. ESET conducted a survey on this in the fall of 2013 and published the results:
- Is NSA Surveillance Affecting Online Behavior?
- Survey says 77% of Americans reject NSA mass electronic surveillance, of Americans
Many of our original findings were reinforced in 2014 when we ran a larger survey with Harris:
- NSA revelations shake faith in U.S. tech firms as Harris poll shows public conflicted
- New Harris poll shows NSA revelations impact online shopping, banking, and more
I discussed the survey findings in a pair of podcasts:
To find that a growing number of people are, because of the Snowden/NSA revelations, reluctant to bank or shop online, or even use email, points to a potentially serious erosion of trust in the technology that powers much of the world's economy. These trends spell trouble for many sectors, not just banking and retailing. Consider healthcare, where increased use of Internet-based communications is a key element in many cost control models. If people lose trust in the ability to communicate privately over the Internet, those models won't work.
The revelations about attempts by NSA and GCHQ to weaken encryption standards and technologies also merited a blog post. I felt compelled to urge people not to stop using encryption in: Encryption advice for companies in the wake of Snowden NSA revelations.
And of course, ESET responded to questions about how antivirus companies deal with government malware. When you read ESET response to Bits of Freedom open letter on detection of government malware, you may detect some frustration with the questions. That's because it really makes no business sense for an antivirus product to give a pass to any particular piece of malicious code, even "righteous malware" deployed for what someone considers to be a good cause. Not to mention that AV companies come in many different national flavors (for example, ESET is headquartered in Slovakia, but has a presence in more than 180 countries).
A different Snowden/NSA impact, one of potentially greater concern, was summed up a single word in a speech I heard yesterday about cyber conflict. (I'm currently attending CyCon, the annual conference of the NATO Cooperative Cyber Defence Centre of Excellence (CCD CoE) in Tallinn, Estonia.) That word was Suspicion, and the speaker was Dr. Jarno Limnéll, the Director of Cyber Security at Intel Security.
For Limnéll, a former career officer in the Finnish Defense Forces, suspicion is the largest single obstacle to cooperation between allies in cyber defense, cooperation that is essential as the threat of cyber conflict escalates (a threat that somehow feels very immediate when you're sitting in Estonia). It is fair to say that the Snowden revelations did nothing to lessen suspicion between allies, and probably a great deal to deepen it.
Facing the future
With apologies for the pun in my heading, I saved the latest revelations for last, namely the story about the NSA's use of facial recognition technology and the gathering of facial images, reported in the New York Times. Maybe it's me, but this was not at all surprising. You have to assume both law enforcement and intelligence agencies are working with facial recognition, particularly as there is no real case law or legislation governing such activities in the United States. What would be worrying is potential abuse of mass access to such facial databases as state drivers licenses.
Not surprisingly, the NSA responded with statements that were reported as denials in some publications, as in this headline: NSA says it's not collecting images of US citizens for facial recognition. Frankly that statement is not the NSA position, unless you qualify it. As Nextgov reported: "The National Security Agency collects and analyzes images of people's faces as part of its vast surveillance operation, the agency's director confirmed Tuesday." But you have to throw "intentionally" in there as a qualifier. The new head of the NSA, Admiral Mike Rogers "insisted that the NSA doesn't intentionally target facial images of Americans." Quote:
"We use facial recognition as a tool to help us understand these foreign intelligence targets."
Rogers also said that the NSA "does not have access to any vast databases of Americans' facial images, specifically denying that the agency collects pictures from state DMV offices." Of course, when you read these statements, you probably experience one of the other major impacts of the Snowden revelations and the government's responses to them: you look for what is not being said. In other words, you're suspicious. Is the reality that the NSA does not collect pictures from state DMV offices, because the FBI or DoJ does it for them? Does no "access to any vast databases of Americans' facial images" mean they don't consider their current access to be vast?
Sadly, unless the U.S. government somehow manages to achieve the right level of transparency and oversight for activities that fall within the NSA remit, crippling suspicion and erosion of trust may well be the legacy of the world learning, via Edward Snowden, about what the NSA and GCHQ have been spending so much taxpayer money on. For now we wait, wondering about the next revelation, which may be the names of Americans on whom the NSA has been spying. That's probably not going to make anybody feel any better.