In recent weeks, ESET researchers in Latin America have been working on the analysis of, and research into, and banking Trojan targeting Brazilian computer users. The criminals perpetrating this particular threat came up with an interesting structure to deceive users and modify their systems to stealing people's private data. In order to achieve its goal the malware uses a malicious Chrome plugin to sniff users’ activities and send the stolen credentials to the criminals via email using a Brazilian government website.
Banking Trojans are one of the most common threats in Brazil, and one of the most profitable kind of attacks that cybercriminals use in this country. The objective of this kind of malware is to steal users’ bank account credentials in order to get their money while remaining undetected by accessing them sparingly.
As one example of this kind of malware, the threat detected by ESET products as MSIL/Spy.Banker.AU was spread through a spam campaign, infecting users’ computer and installing a malicious Google Chrome Plugin to spy on the victim's Internet activities.
The main executable associated with the spam campaign acts as a dropper, installing a set of DLLs and JavaScript files at specific places inside the system, including the Google Chrome Plugin.
When the malicious plugin is installed, it will monitor all the websites visited by the potential victim and triggers its malicious payload if certain Brazilian financial entities are accessed. Once the user logs into her account the malware will log her banking credentials and send them to the attacker.
Some of the files dropped by the executable are detected as:
| File | Detection |
| Microsoft.js | JS/Spy.banker.G |
| Service.js | JS/Spy.banker.G |
| Skype.js | JS/Spy.banker.G |
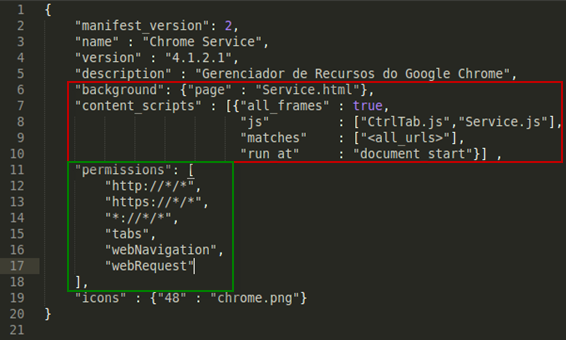
In order to achieve its goal sthe plugin requests certain kinds of permissions as listed in the plugin manifest file (Manifest.json), but as the user is not aware of this she will never find out that her activities are being tracked.
We note that use of this technique is on the rise because modifying the victim's browser or installing malicious plugins gives cybercriminals a better success rate when their goal is to steal private information including email, bank account or social network credentials. For additional insight into the capabilities of a malicious Google Chrome plugin I invite you to review Aleksandr Matrosov’s post about Win32/Theola using a Chrome plugin to commit bank fraud.
Once that the plugin is set, it will need to extract the stolen data and send the information to the attacker. In order to achieve this goal and remain anonymous the attackers came out with a rarely seen technique using a design flaw i in the configuration of a Brazilian government website.
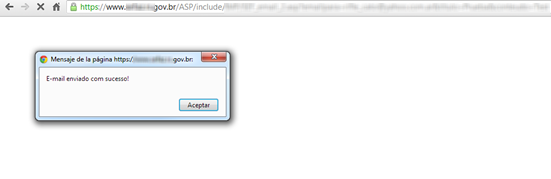
This misconfiguration allowed the attackers to use a gov.br email account to forward the data to two different email accounts hosted by one of the most commonly-used mail services.
Two different kinds of email were sent, the first email was triggered at every new infection and the second one would be sent when the victims logged into their bank accounts. For this purpose the malicious scripts are structured to query what URL the user is visiting and if it matches with the any of the targeted financial institutions it will grab the form's data and store them into a cookie in order to be sent lately.
As can be seen in the Manifest.json image, scripts are triggered every time that the users visits a URL: the common structure of Chrome plugins is such that on every tab the file called Service.js will be executed. The combination of the permissions requested and the method included in each of the JavaScript malicious files are responsible for parsing and fetching the form fields and user data.
Thanks to the collaboration of CERT.BR we have been able to disable this attack and block the email accounts related to this threat, having been able to inform the affected institutions and organizations about the attack. The affected web site has already been patched the vulnerability in their server invalidating any further attempt by the cybercriminals to use this government website for malicious activities using that vulnerability.
For a detailed explanation about the techniques used and analysis of this thread we suggest you read the white paper (.pdf).
Fernando Catoira, Security Analyst
Pablo Ramos, Security Researcher
Sebastian Bortnik, Education and Research Manager
| File | hash |
| MulheresPerdidas.exe | f7d63175ff8b4959c425ad945e8e596e |
| Microsoft.js | 6a944a7da3fc21b78f1a942ba96042a0 |
| Service.js | 6c1daaccd036cd602423f92af32cdc14 |
| Skype.js | 28174674f60ce4d3fb1ac8a74686b3ca |
| Vaio.dll | c9e20bdec9264bbb6de34c5dd7be0c79 |