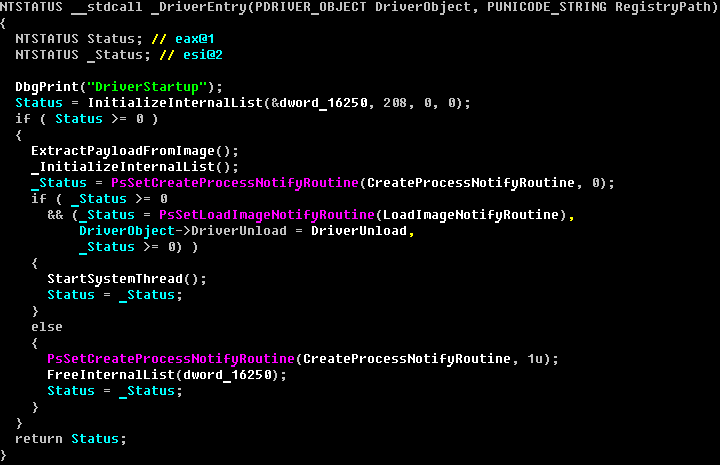
[More news from my colleagues in Russia on their analysis of an interesting item of bank-targeting malware.]
This month we discovered new information on a new modification in the Win32/TrojanDownloader.Carberp trojan family. This trojan is notorious as one of the most widely spread malicious programs in Russia, stealing money from remote banking systems and primarily targeting companies which perform a huge number of financial transactions a day. We already shed some light on this malware in our CARO 2011 presentation “Cybercrime in Russia: Trends and issues”. The cybercrime group behind this Trojan is very active in the territory of Russia and the former Soviet republics. We spotted the first cases related to the Carberp trojan around the end of 2010 and in the middle of the summer of 2011 we can see from the following graph that there was a big spike in the number of detections, a pattern which has been repeated at the beginning of the fall.
The Russian Federation is the country where the largest number of installations of Carberp has been seen, as confirmed by the statistics below:
The criminal gang behind Carberp is one of the biggest cybercrime groups engaged in banking fraud. The group’s average weekly income is estimated to be several million US dollars. Furthermore, these guys are heavily investing money in the development of malware technologies, as is confirmed for instance, by the evolution of the Hodprot dropper (http://go.eset.com/us/resources/white-papers/Hodprot-Report.pdf): this has been implicated in installations of Carberp, RDPdoor and Sheldor (https://www.welivesecurity.com/2011/01/14/sheldor-shocked). RDPdoor, by the way, installs Carberp to open a backdoor in the infected system and manually perform fraudulent banking transactions. We have ascertained that these examples of malicious software are products of single cybercrime group.
At the beginning of this year advertising appeared on some cybercrime forums for a new bootkit builder which wasn’t detected by antivirus software. The price of the builder was estimated to be tens of thousands of US dollars and seemed incredible compared with that of the SpyEye and Zeus Trojans.
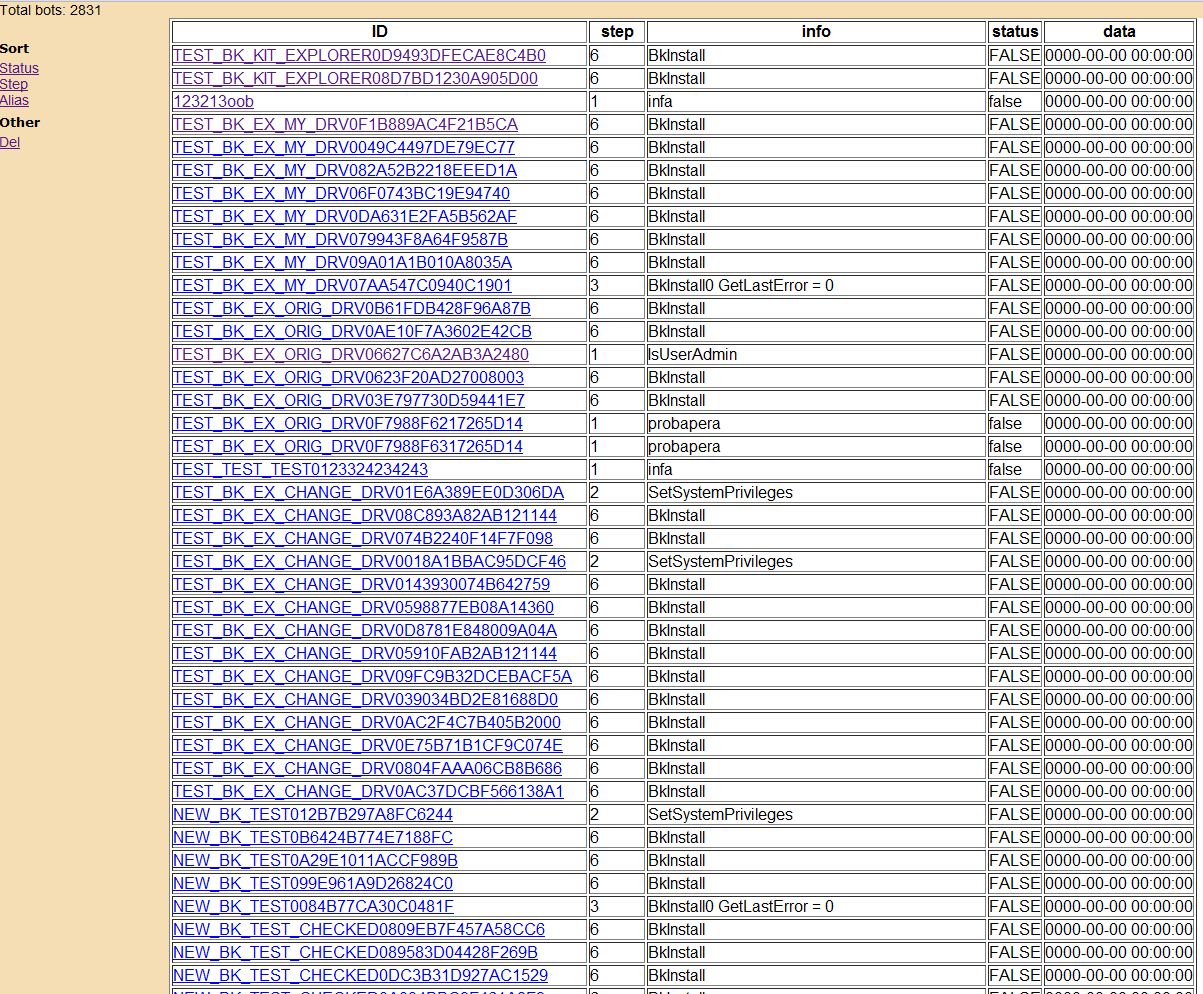
It isn’t known how many groups bought the builder. We managed to obtain a sample of the compiled dropper with the builder which loads a stub driver. The code in the sample is identical to those of some other examples of malicious software. At the time the only known malware utilizing the same bootkit component was the Rovnix bootkit (https://www.welivesecurity.com/2011/08/23/hasta-la-vista-bootkit-exploiting-the-vbr). Testing of the Carberp Trojan with bootkit functionality started early in the fall and during this period its distribution was very limited. There are two facts that suggest that the bot is working in the test mode. The first is that there is an abundance of debugging and tracing information relating to bot installation and the binary’s behavior. Secondly we managed to gain access to log files from the bot C&C server that also support the probability that Carberp was under test:
C&C for tested bot version
There is also a lot of debugging information to be found in the installer of the new version of Carberp:
String found in the unpacked Carberp module
The bootkit component of the new version remains the same and is almost identical to that of Rovnix bootkit. You can also find technical details of the Rovnix bookit in the slides of "Defeating x64: Modern Trends of Kernel-Mode Rootkits" talk given at the Ekoparty 2011 Security conference.
At the same time, its installer has been changed significantly. Besides installing the bootkit in the system it tries to exploit several vulnerabilities in the target system so as to escalate its privileges. Carberp utilizes these exploits as it requires administrative privileges in order to install the bootkit. Primarily, the Carberp Trojan targets corporate users using RBS (Remote Banking Systems) software which in many cases lack administrative privileges, so that a social engineering attack isn’t applicable or sufficient in this scenario. Therefore the installer exploits the following vulnerabilities in the system software in order to escalate privilege:
- MS10-073 (win32k.sys KeyboardLayout vuln)
- MS10-092 (Task Scheduler vuln)
- MS11-011 (win32k.sys SystemDefaultEUDCFont vuln)
- .NET Runtime Optimization vuln (http://osvdb.org/show/osvdb/71013)
Yet another interesting feature of the installer of the new version of Carberp is that it removes various hooks from the following list of system routines just before installing the trojan or bootkit onto the system:
This is done with the intention of evading sandboxes and other monitoring software that employs user-mode hooks.
The bootkit itself is intended to load a kernel-mode driver which in turn injects a malicious DLL into address spaces of processes running on the system. In the new version of Carberp we found only a 32-bit kernel-mode driver, but the technology in use makes it possible to load a 64-bit unsigned kernel-mode driver on 64-bit operating systems.
After unpacking the injected kernel-mode driver we can find the compiler version and date of build:
Based on the data provided above the driver was built at the beginning of November and is being tested right now. The linker has left an interesting string in the driver binary containing the path to debugging symbols on the developer’s computers:
It seems that this is not the first and possibly not the last version of the malware to appear recently. Since there are only two known examples of malware (Carberp and Rovnix) employing this particular bootkit technique, the development of which requires highly qualified specialists, it is possible that the group which originally developed this bootkit is currently supporting it.
As was mentioned earlier in this article, the main task of the driver is to inject its payload into user-mode address space of the process in the system.
After unpacking the DLL injected by the kernel-mode driver we can see that the date of its compilation is different to that of kernel-mode driver.
Inside the binary we found a string pointing to another directory containing debugging symbols. We can see “GSVSoft” as the name of a root-level directory.
Since the dates of compilation and paths to debugging symbols directories are not the same it may be that there are two independent groups of people working on the malware. By the way, there is a real company with the name “GSVSoft” (gsvsoft.ru) but we don’t have enough information to draw any conclusions from that.
The main functionality of the injected library is very close to that of the previous version of Carberp. Its main task is to inject JS-scripts into internet banking webpages, downloading additional plugins and communicating with the C&C server.
Based on the information presented above we can conclude that the authors of the malware aren’t satisfied with current methods of concealing malware in the system, and so are investing money into developing their own techniques for bypassing antivirus software. The evolution of this malware led Carberp to become the number one malware attacking the clients of Russian banks (there also governmental organizations that became victims of this trojan). The new version of Carberp with bootkit can be compared to such advanced malware as TDL4 and Rovnix.
Even though Carberp is currently targeting only Russian banks, this situation might rapidly change as there are no obstacles to applying the same fraudulent techniques in order to target banks in other countries. A possible reason that the cybercrime group doesn’t attempt to target other regions is that it is satisfied with current conditions and revenue, at least until a new partnership draws them to spread to other parts of the world. In the last year we have noticed some Carberp activity in Europe, but this declined rapidly.
Aleksandr Matrosov, ESET
Eugene Rodionov, ESET
Dmitry Volkov, Group-IB
David Harley, ESET