Yesterday, ESET announced the discovery of a new threat against the Apple Mac OS X platform. Today, we have found a new version of the same threat. The new version is similar to the previous version with two important differences. The first addition to this threat is that it now implements persistence on an infected system. It also has updated command and control information.
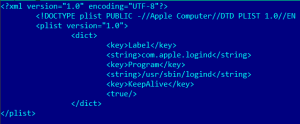
OSX/Tsunami.A adds an entry to LaunchDaemons, named /System/Library/LaunchDaemons/com.apple.logind.plist. This entry starts an executable, /usr/sbin/logind. The content of the LaunchDaemons entry is shown in the following screenshot.
 The second difference identified in the new binary is a new command and control IRC server and IRC channel. At the time of writing, neither IRC servers are responding.
The second difference identified in the new binary is a new command and control IRC server and IRC channel. At the time of writing, neither IRC servers are responding.
Although the samples we have received come from two different countries on two different continents, our telemetry data still indicates that there are very few hosts infected with this malware.
It is our belief that the people behind this threat are in the process of testing their creation. They are probably adapting the code, originally written for Linux, to the OS X platform. We are still unaware of any specific infection vector for this threat. It can be installed manually by an attacker or in an automated way.
This threat does not have the sophistication or complexity of TDL4 or Win32/Duqu, so we think the risk to Mac users is limited. We will continue to watch the situation closely.
MD5 hash of the analyzed binary: 3eb0744d73178a3e7bd070c862cd2c69
Pierre-Marc Bureau
Senior Malware Researcher




