Air-gapping is used to protect the most sensitive of networks. In the first half of 2020 alone, four previously unknown malicious frameworks designed to breach air-gapped networks emerged, bringing the total, by our count, to 17. ESET Research decided to revisit each framework known to date and to put them in perspective, side by side.
Key findings in this report:
- All the frameworks are designed to perform some form of espionage.
- All the frameworks used USB drives as the physical transmission medium to transfer data in and out of the targeted air-gapped networks.
- We have not found any case of actual or suspected use of covert physical transmission.
- Over 75% of all the frameworks used malicious LNK or autorun files on USB drives to either perform the initial air-gapped system compromise or to move laterally within the air-gapped network.
- More than 10 critical severity LNK-related remote code execution vulnerabilities in Windows have been discovered, then patched by Microsoft, in the last 10 years.
- All the frameworks were built to attack Windows systems. We have not found any evidence of actual or suspected malware components built to target other operating systems.
In our white paper, linked below, we describe how malware frameworks targeting air-gapped networks operate, and we provide a side-by-side comparison of their most important TTPs. We also propose a series of detection and mitigation techniques to protect air-gapped networks from the main techniques used by all the malicious frameworks publicly known to date.
Using the knowledge made public by more than 10 different organizations over the years, and some ad hoc analysis to clarify or confirm some technical details, we put the frameworks in perspective to see what history could teach us in order to improve air-gapped network security and our abilities to detect and mitigate future attacks.
This exhaustive study allowed us to isolate several major similarities in all of these frameworks, even those produced 15 years apart. Specifically, we focused our attention on the malware execution mechanisms used on both the connected and the air-gapped side of targeted networks and the malware functionalities within the air-gapped network (persistence, reconnaissance, propagation, espionage, and – at least in one case – sabotage activities), with a focus on the communication and exfiltration channels used to cross the air-gap barrier and control the components running on the isolated networks. This also resulted in a systematic analysis structure that may be reused to document air-gapped malware that is discovered in the future.
Despite some differences and nuances found across all frameworks studied, our analysis shows how most differ on many of those aspects only from an implementation perspective, mostly due to the severe constraints imposed by air-gapped environments. Armed with this information, we will highlight some detection opportunities specific to the actual techniques observed in the wild.
Our aim is to convince the reader of the importance of having all the proper defense mechanisms to mitigate the techniques used by virtually all of these frameworks that have been observed in the wild, before starting to look into the many theoretical air gap bypass techniques that have received a lot of attention in recent years despite none of them ever being used in a real, publicly disclosed attack.
Victimology, attacker profiles, timeline
An air-gapped network is one that is physically isolated from any other networks in order to increase its security. Air-gapping is a technique used to protect networks interconnecting the most sensitive and high-value systems within an organization, systems that are naturally of high interest to numerous attackers, including any and all APT groups.
We can state without fear of contradiction that threat actors behind the known malware frameworks designed to attack air-gapped networks all belong to the advanced persistent threat (APT) category. Despite the variety of threat actors behind these frameworks, all of them shared a common purpose: espionage.
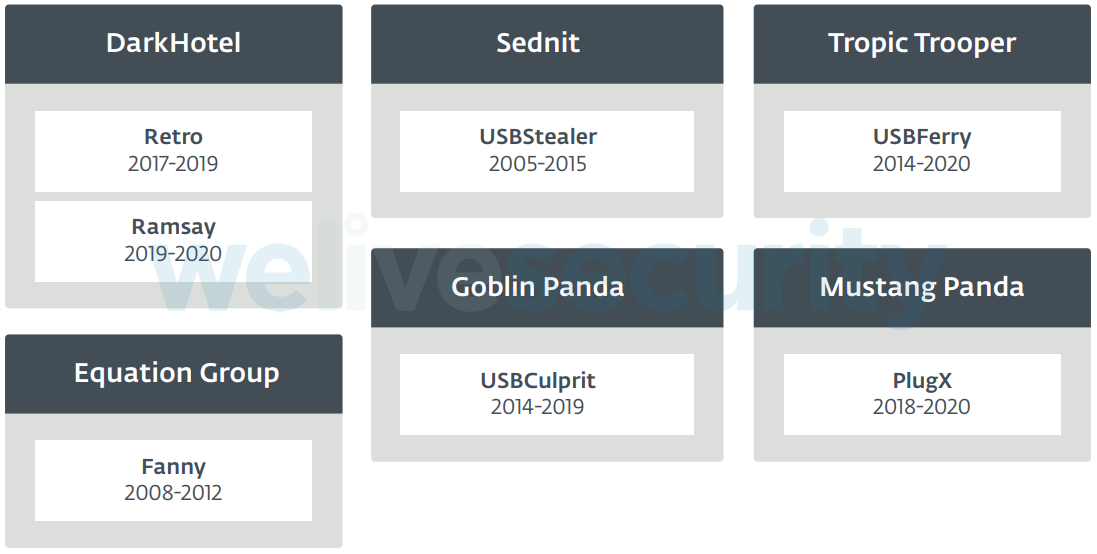
Some frameworks have been attributed to well-defined, well-known threat actors:
For others, the attribution has been less clear-cut, speculative or controversial. Agent.BTZ, for example, has been attributed to Turla, but other experts are not so convinced.
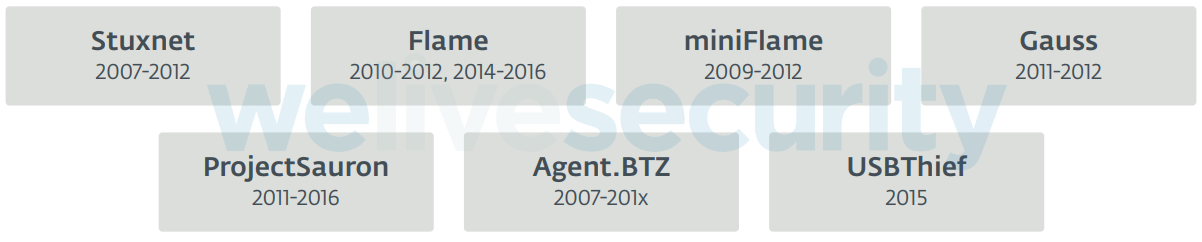
Finally, we have a trilogy of frameworks that constitute our special cases: these frameworks have been found in documentation from the Vault7 leaks and are described to have been in operation in a time range from 2013 to 2016; however, we haven’t found samples in the wild to analyze first hand.
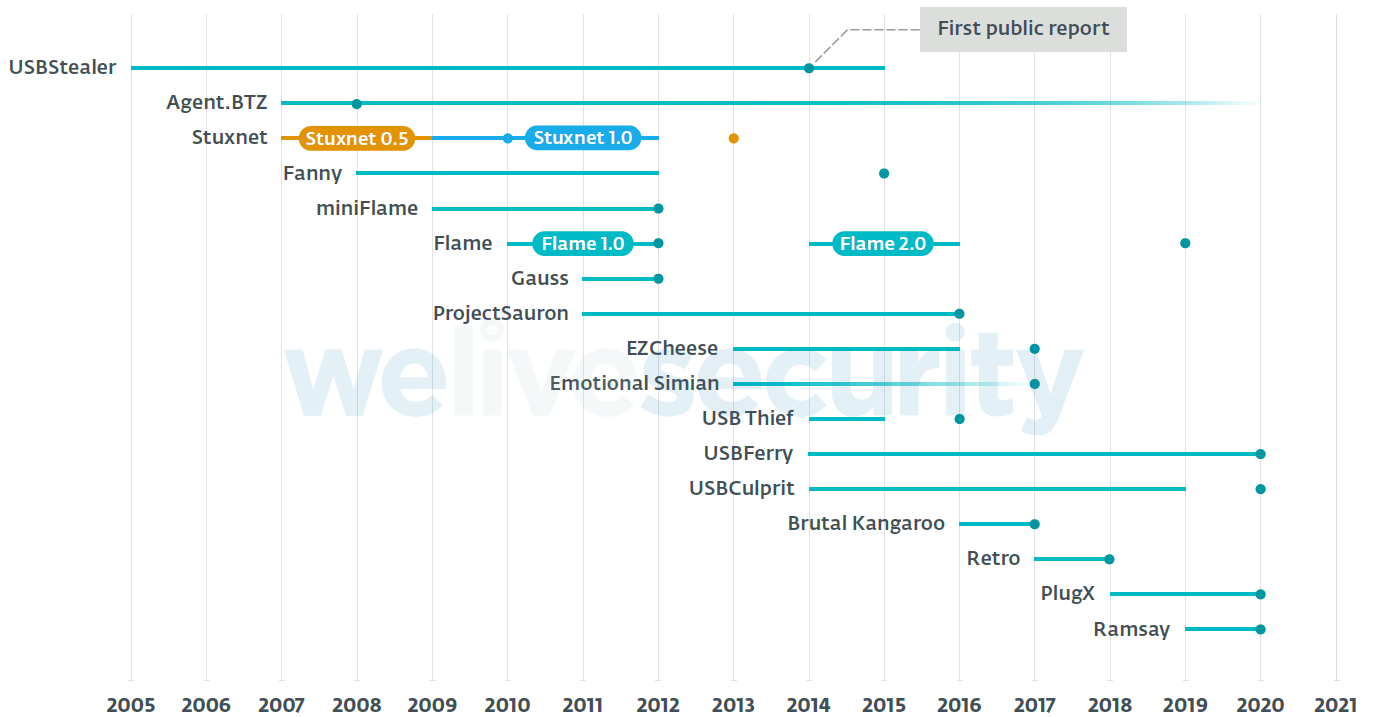
The figure below shows a historical view of the period of activity of each framework, along with the time of the first public report. This is also an indication of how difficult it is to detect this type of framework, several having been active for many years before getting exposed.
Note that the periods of activity are based on what has been reported publicly; in some cases, the researchers were not able to determine a precise period of activity based on observable facts but are rather approximated or inferred by using some reasonable hypotheses.
Anatomy of air-gapped systems – a malware perspective
Attack and compromise of systems in air-gapped networks require the attackers to develop capabilities that enable their tools to communicate via channels that are not commonly required in normal operations. It’s obvious: they have to contend with the fact that these networks are isolated from the internet.
There is no precise definition of what “air-gapped malware” actually is from the purely technical perspective. This sparked some lively discussions internally, until we finally agreed upon—for the purpose of this paper—the following definition for air-gapped network malware:
Malware, or a set of malware components acting together (a framework), that implements an offline, covert communication mechanism between an air-gapped system and the attacker that can be either bi-directional (command and response) or unidirectional (data exfiltration only).
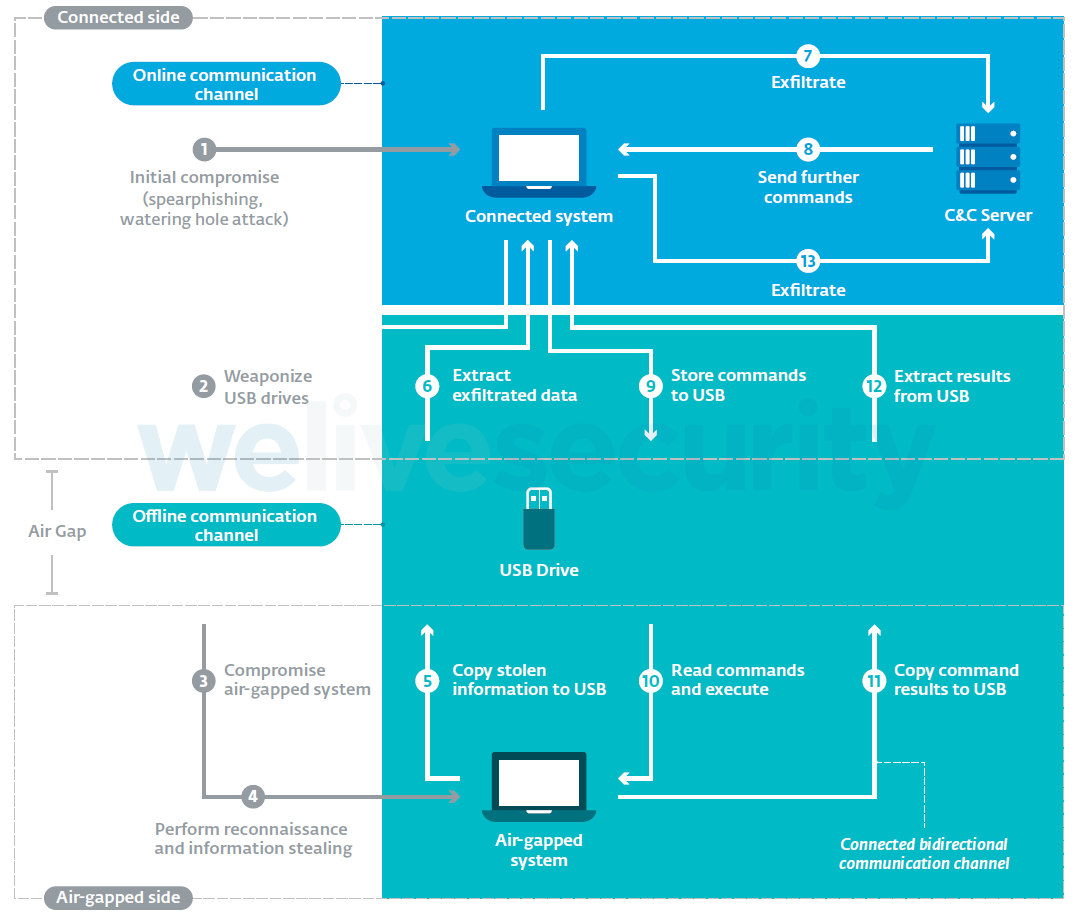
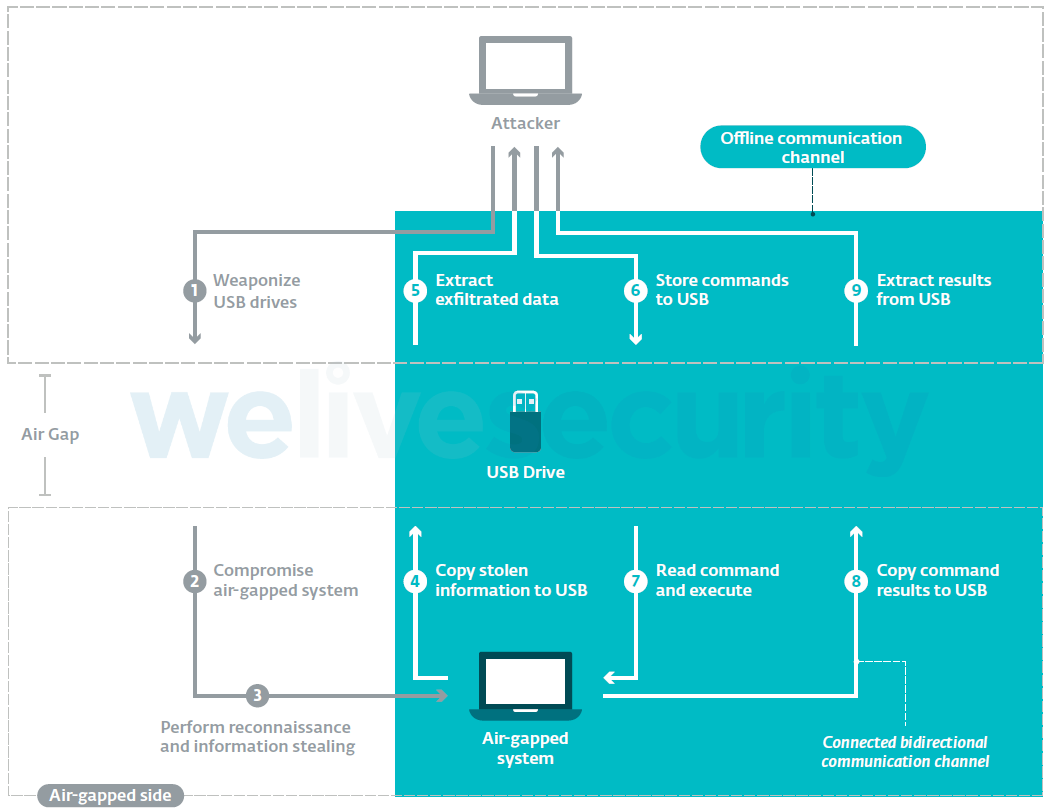
We decided to separate the frameworks into two broad categories: connected and offline. Most frameworks are built to provide fully remote end-to-end connectivity between the attacker and the compromised systems on the air-gapped side. We call these “connected frameworks”. The general operating schema looks like this:
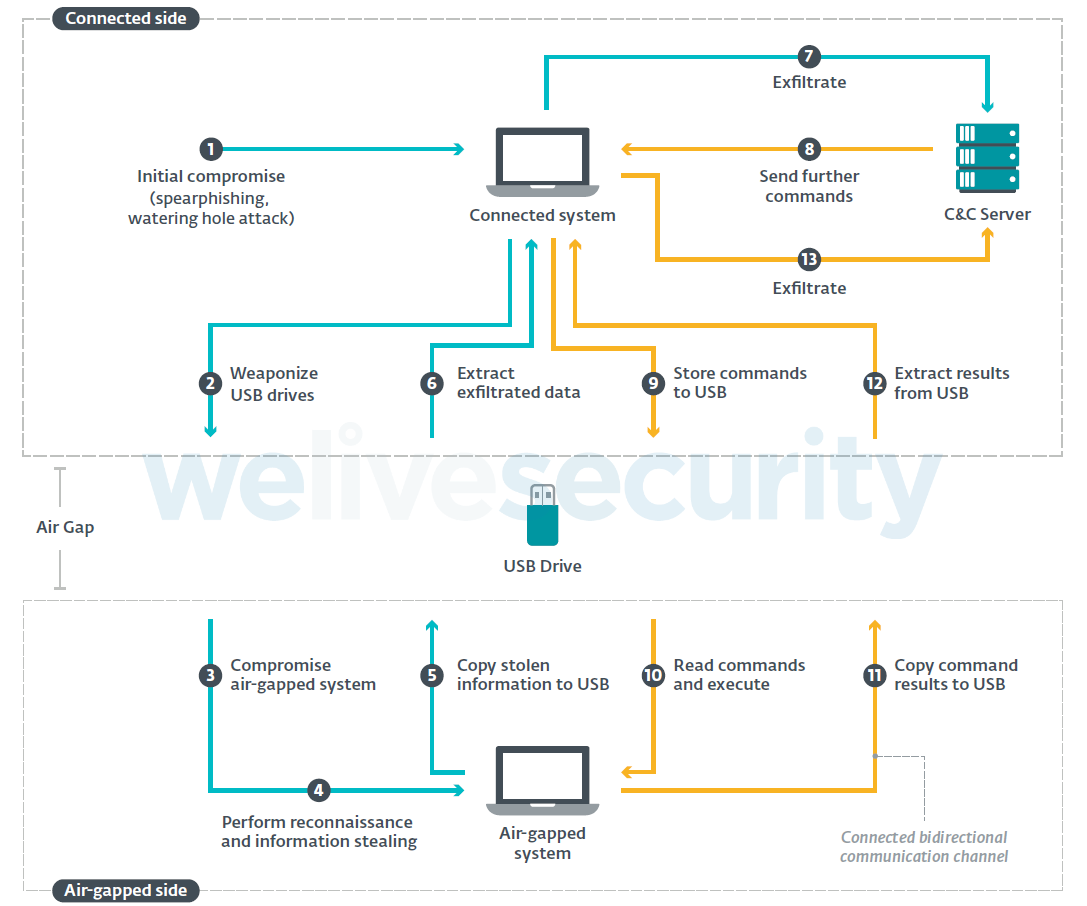
Figure 2. Overview of the components and actions of a connected framework designed to attack air-gapped networks
The most basic connected frameworks only have online connectivity with the attacker for data exfiltration purposes. The most powerful ones support a two-way communication protocol (represented by the yellow arrows). Through a compromised system on the connected side, the attacker sends commands to the malware placed on the air-gapped network; this is done via a covert communication channel often placed on a USB drive. This feature grants the attackers the ability to remotely run arbitrary code inside air-gapped networks.
In the other, rarer cases, the attack scenario does not involve any internet-connected systems at all. We call these “offline frameworks”. In these cases, everything indicates the presence of an operator or collaborator on the ground to perform the actions usually done by the connected part of connected frameworks, such as preparing the initial malicious USB drive responsible for the execution on the air-gapped side, executing the malware on the air-gapped system , extracting the exfiltrated data from the drive and sending additional commands to the air-gapped side.
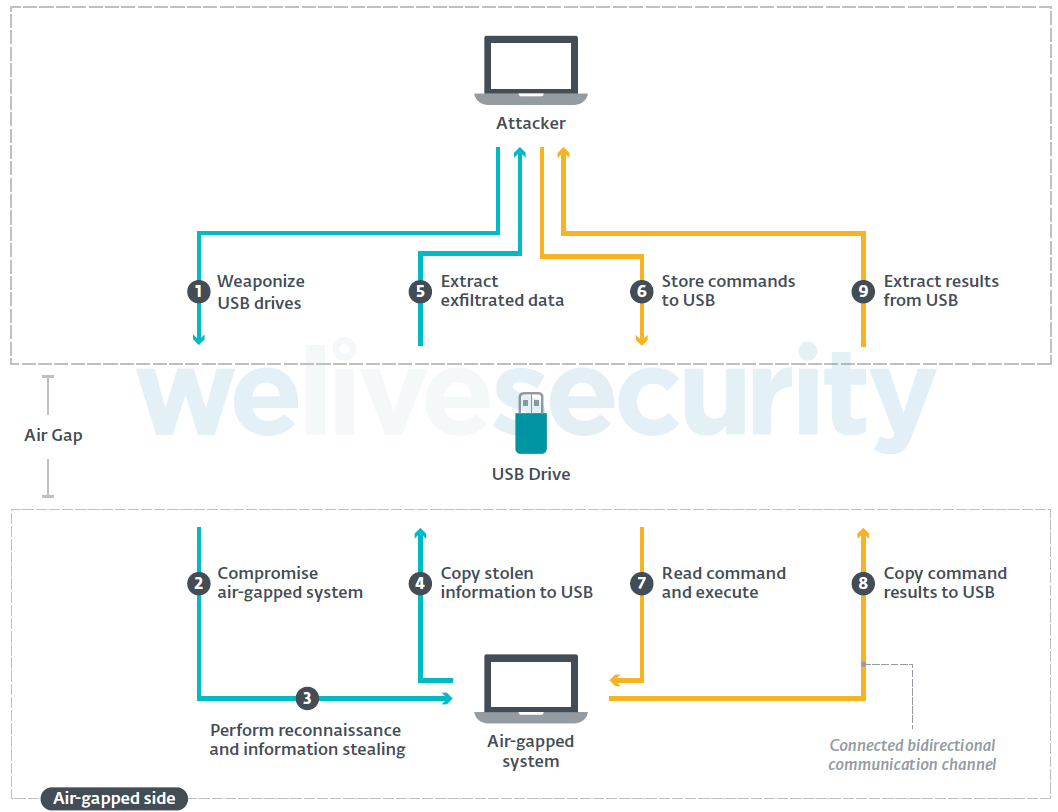
Figure 3. Overview of the components and actions of an offline framework designed to attack air-gapped networks
With those formal definitions established, we can compare the main characteristics shared by all frameworks.
Connected side execution vector
For connected frameworks, the first step to successfully compromise the air-gapped network is to get a foothold on a system that has internet connectivity. When it comes to APTs, it’s not always possible to know exactly how this happened but for the cases that we do know, the methods observed do not differ much from what we see in general malware: emails with malicious attachments, links, or USB worms.
Air-gapped side initial execution vector
This is one of the most interesting elements we studied: how do attackers manage to execute malicious code on an air-gapped system in the first place? All frameworks have devised their own ways, but they all have one thing in common: with no exception, they all used weaponized USB drives. The main difference between connected and offline frameworks is how the drive is weaponized in the first place. Connected frameworks usually deploy a component on the connected system that will monitor the insertion of new USB drives and automatically place the malicious code needed to compromise the air-gapped system. Offline frameworks, on the other hand, rely on the attackers intentionally weaponizing their own USB drive. What is interesting here is the variety of techniques used over time by these frameworks to get their payload executed on the target system. We can place these into three large categories.
- Automated execution: the malicious code gets executed without any user intervention. This entails the exploitation of some vulnerability, the most famous one being CVE-2010-2568, aka the “Stuxnet LNK exploit”.
- Non-automated execution (unknowingly triggered): the malicious code execution depends on tricking an unsuspecting legitimate user into executing the malicious code on the target system. This can be performed by planting a compromised decoy document or a trojanized software installer on the USB drive, for example.
- Non-automated execution (deliberately performed): the malicious code is hidden on the USB drive and needs to be deliberately executed by a human actor with physical access to the target system.
Table 1. Techniques used to compromise the first air-gapped system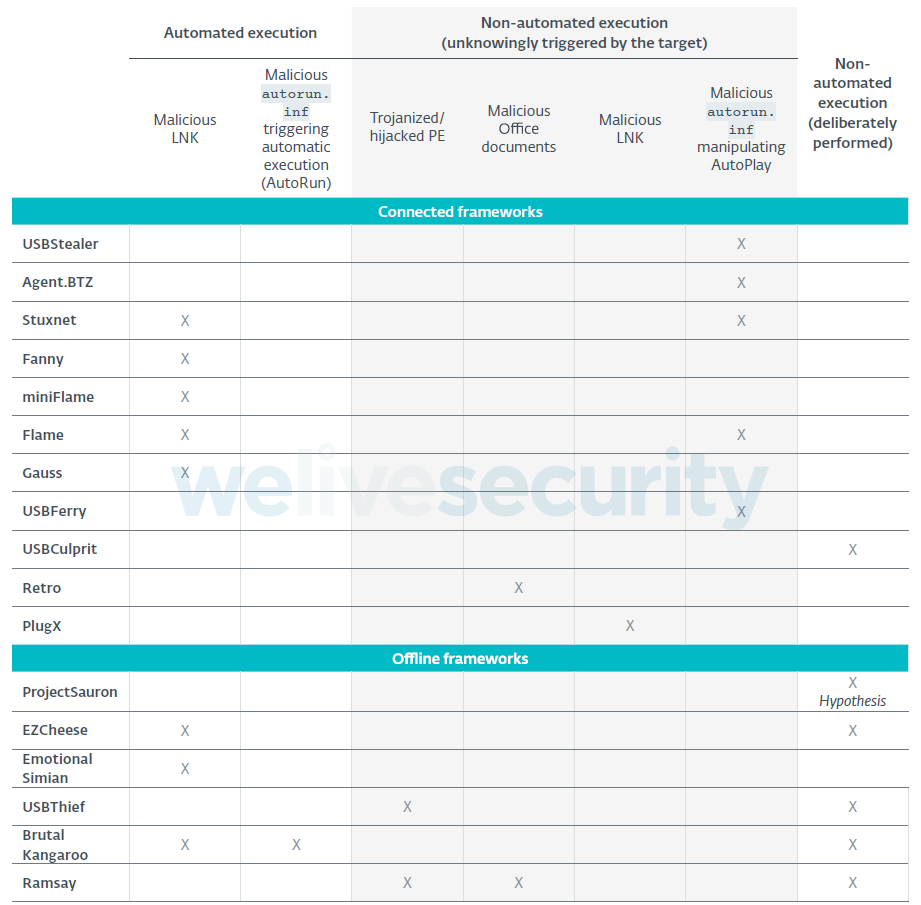
Air-gapped side functionalities
We looked at the three most important framework functionalities available on the air-gapped-side: persistence, reconnaissance & espionage activity, and propagation & lateral movement. This highlighted how frameworks vary greatly in terms of operational objectives and complexity: some are built for hit-and-run types of activity with hardcoded file-stealing tasks and no persistence, while others implement sophisticated and stealthy persistence mechanisms and effective propagation mechanisms within the air-gapped network. See Section 4.3 of the white paper for the full details.
Communication and exfiltration channel
This is the most interesting characteristic to study when looking at malware attacking air-gapped networks. Earlier in this blog, we clarified our definition of “air-gapped malware” and split air-gapped frameworks in two categories: connected and offline.
The difference from the communication and exfiltration point of view is significant: online frameworks require an online, traditional C&C communication channel connecting the attacker to the connected-side compromised host, and a second, offline one connecting the connected-side compromised host and the air-gapped systems, as shown in the figure below.
On the other hand, the figure below shows how offline frameworks only require the offline communication channel.
The presence of an offline communication channel is the core part of our definition of what air-gapped malware is. This is how the malware bypasses the air gap defense layer to transfer information in and out, or sometimes just out, of the target network.
An offline channel can be seen as a specific communication protocol running over a certain physical transmission medium across the air gap.
One of the first things that comes to mind when talking about attacks against air-gapped networks is how the air gap can be bypassed. In fact, new research on covert physical transmission mediums is published on a regular basis. One of the most prolific researchers in that domain is certainly Mordechai Guri, lead cybersecurity researcher at Ben-Gurion University of the Negev. He and his team have demonstrated the feasibility of numerous techniques that allow information transfer across air gaps with various levels of attack deployment complexity and available bandwidth.
While there have been alleged sightings of in-the-wild attacks using such techniques, no peer-reviewed case has been publicly analyzed and disclosed. Practically all the malicious frameworks targeting air-gapped networks publicly known to date used USB drives as the physical transmission medium to transfer information across air gaps.
The table below illustrates how about half of the frameworks only implement unidirectional protocols. In these attack scenarios, the information can only flow from the compromised air-gapped system to the attacker, and not the other way around. This means the malware component running on the air-gapped side does not have any update mechanism or backdoor capabilities and is designed to perform specific, hardcoded tasks, usually reconnaissance and information stealing, and then exfiltrate the information back to the attacker via the USB drive. The attacker has no way at all to send updates or commands to control the compromised system.
Frameworks implementing bidirectional protocols are more flexible, as they allow the attacker to have much better control over the compromised air-gapped hosts. Interestingly, not all frameworks with bidirectional protocols make full use of this capability. In fact, most implement only a small, not very flexible set of commands, such as steal files matching specific patterns or run a specific executable file present on the USB drive.
Table 2. Types of offline communication protocols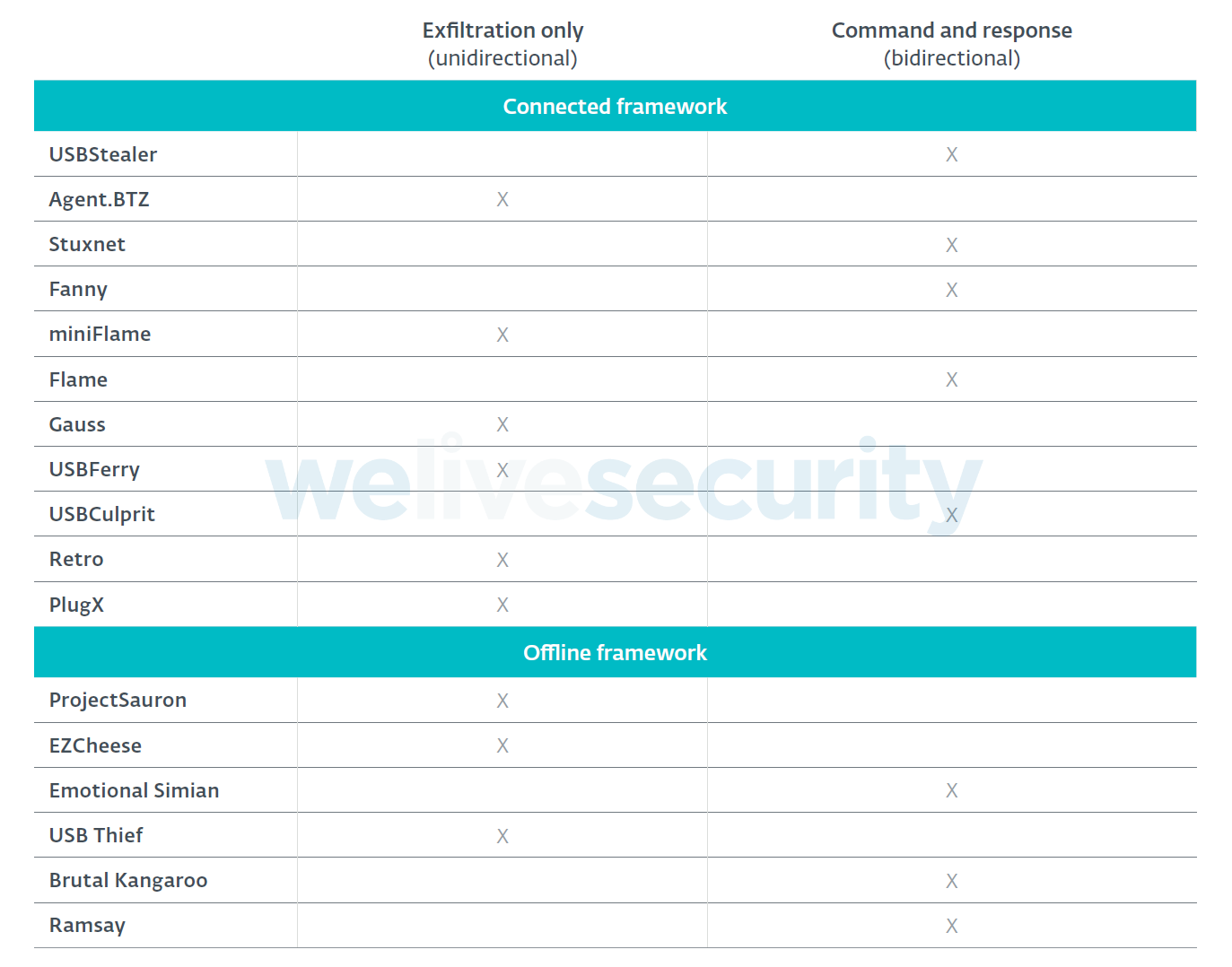
Defending air-gapped networks
It goes without saying that defending air-gapped networks against cyberattacks is a very complex topic that involves several disciplines. It is far from our intention to claim that we have a magical solution to this problem. That being said, there is value in understanding how known frameworks operate in air-gapped environments and deriving ways to detect and block common malicious activities.
Section 5 of our white paper presents ideas to detect and block malicious activities that are common to a significant portion of the studied frameworks. None of them are revolutionary, but we hope that our data-driven approach will help defenders prioritize their defense mechanisms. In other words, that defenders first implement defense mechanisms against what known malware has been doing so far, before trying to block techniques that have not been used yet.
Conclusion
We have seen how the frameworks can be split into two categories: connected frameworks, which are operated fully remotely, and offline frameworks, which rely on a human asset on the ground. Despite the use of various techniques to breach the initial air-gapped system, to propagate inside the network or to exfiltrate stolen information, all the frameworks share one common goal: spy on their target.
Discovering and analyzing this type of framework poses unique challenges. They sometimes are composed of multiple components that all have to be analyzed together in order to have the complete picture of how the attacks are really being carried out.
Also, security vendors such as ESET rely on telemetry to discover new threats on systems where their products are running. By definition, systems running within air-gapped networks do not send such telemetry, which creates a significant blind spot that contributes to increasing the time to discovery and detection of new malware targeting air-gapped networks.
Understanding how malware attacks air-gapped networks can help identify and prioritize detection and protection mechanisms. For example, we saw how all frameworks relied on USB drives one way or the other to spy on air-gapped systems, and none of them used any other type of covert communication channels against which TEMPEST restrictions would need to be implemented.