Utilizing a trojanized version of an official Tor Browser package, the cybercriminals behind this campaign have been very successful – so far their pastebin.com accounts have had more than 500,000 views and they were able to steal US$40,000+ in bitcoins.
Malicious domains
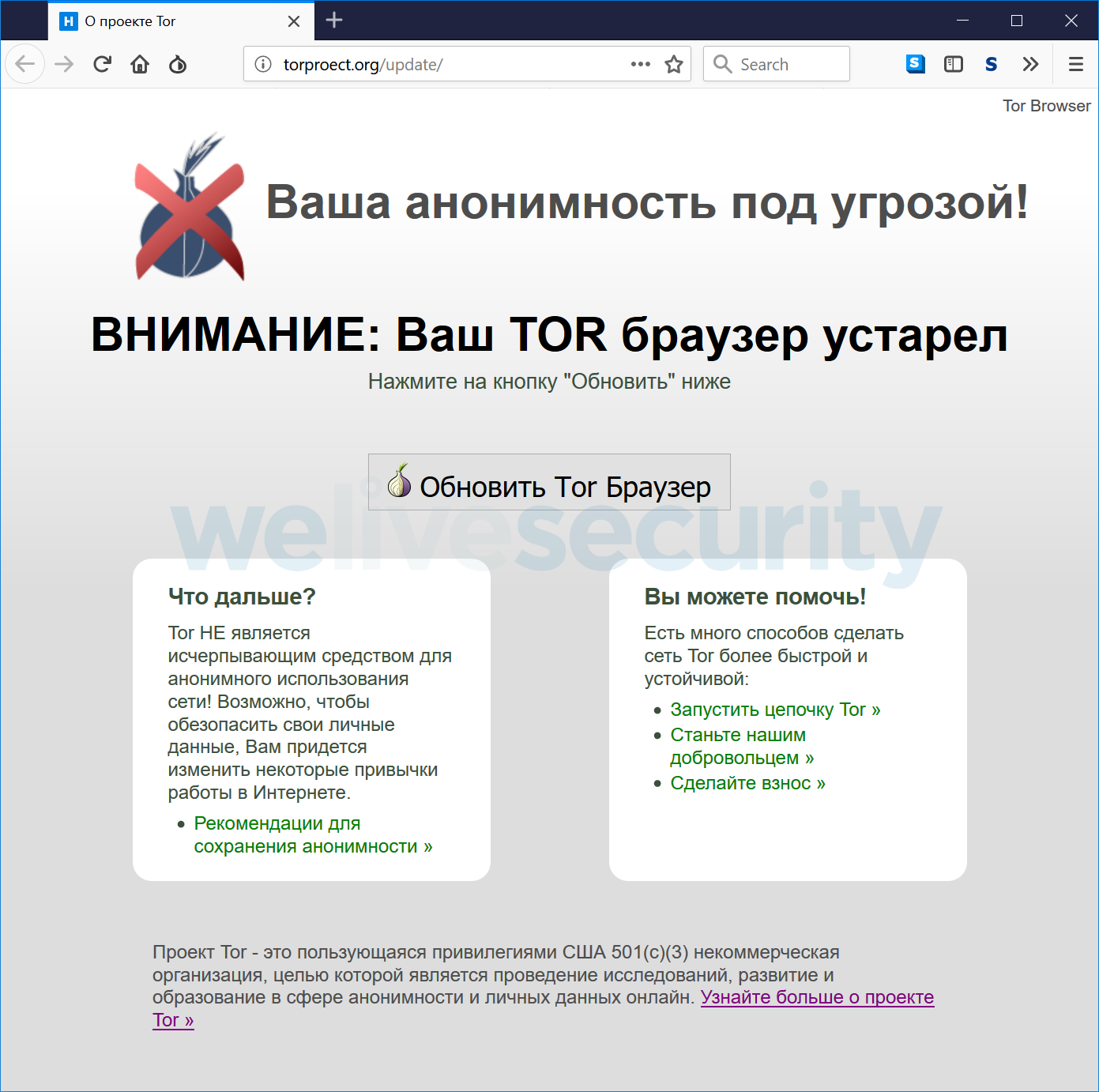
This newly discovered trojanized Tor Browser has been spreading using two websites that claimed that they distribute the official Russian language version of the Tor Browser. The first such website displays a message in Russian claiming that the visitor has an outdated Tor Browser. The message is displayed even if the visitor has the most up-to-date Tor Browser version.
Translated to English:Your anonymity is in danger!
WARNING: Your Tor Browser is outdated
Click the button “Update”
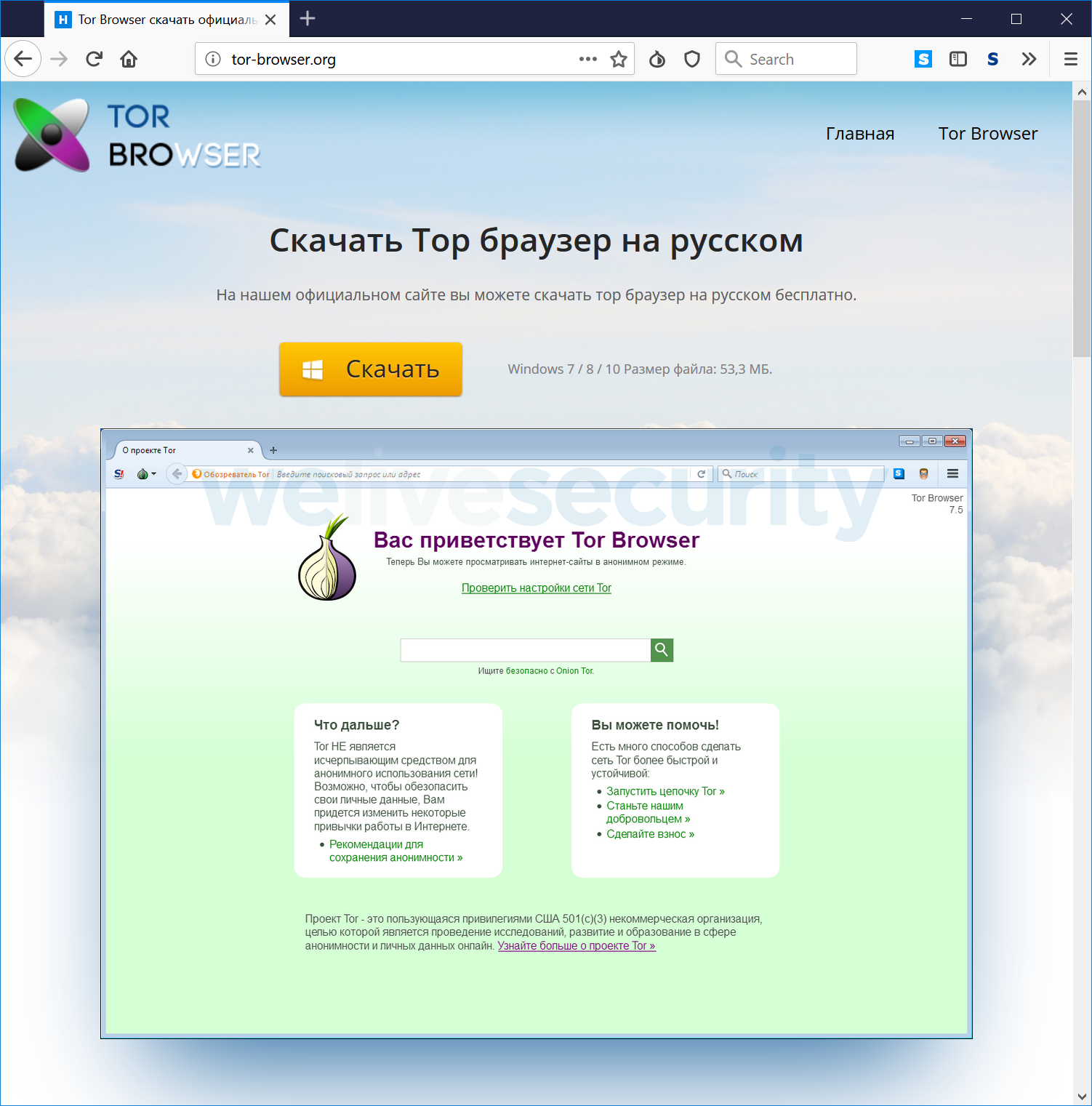
On clicking the “Update Tor Browser” button, the visitor is redirected to a second website with the possibility of downloading a Windows installer. There are no signs that the same website has distributed Linux, macOS or mobile versions.
Both these domains – tor-browser[.]org and torproect[.]org – were created in 2014. The malicious domain torproect[.]org domain is very similar to the real torproject.org; it is just missing one letter. For Russian-speaking victims, the missing letter might raise no suspicion due to the fact that "torproect" looks like a transliteration from the Cyrillic. However, it does not look like criminals relied on typosquatting, because they promoted these two websites on various resources.
Distribution
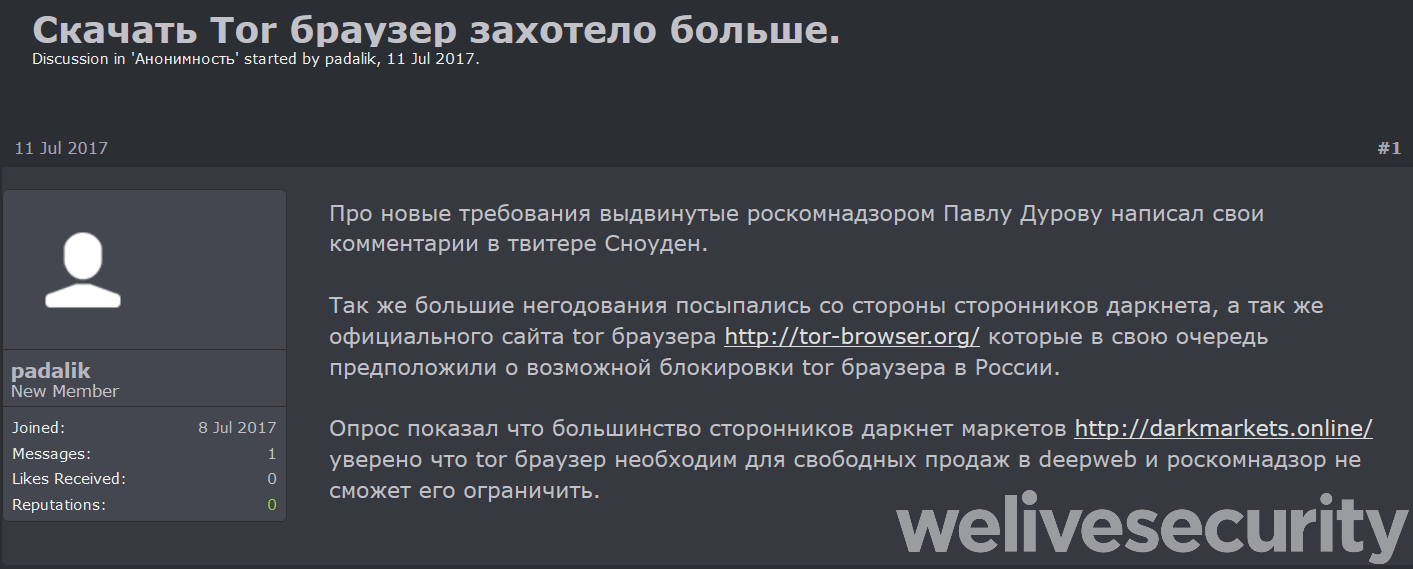
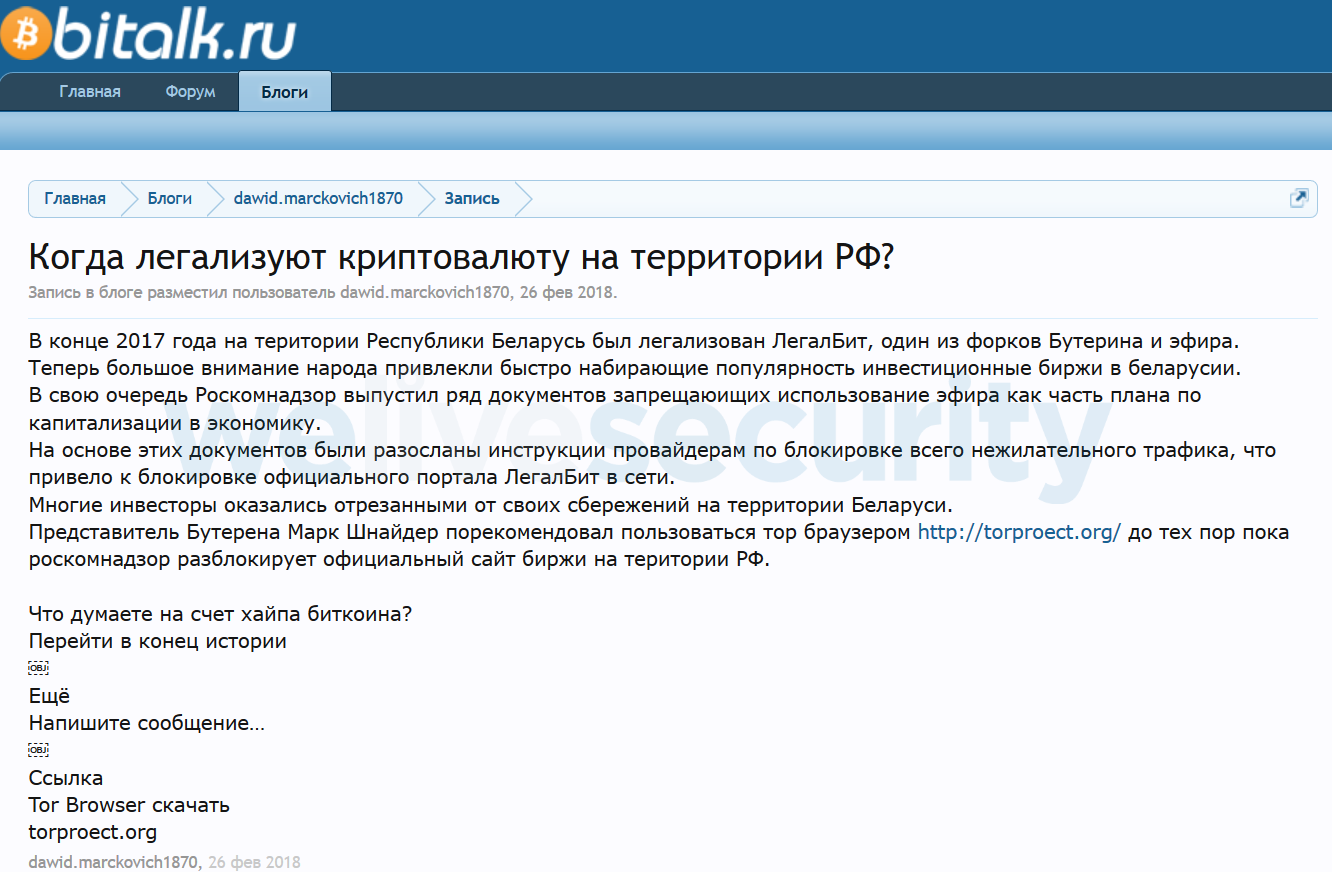
In 2017 and early 2018 cybercriminals promoted the webpages of the trojanized Tor Browser using spam messages on various Russian forums. These messages contain various topics, including darknet markets, cryptocurrencies, internet privacy and censorship bypass. Specifically, some of these messages mention Roskomnadzor, a Russian government entity for censorship in media and telecommunications.
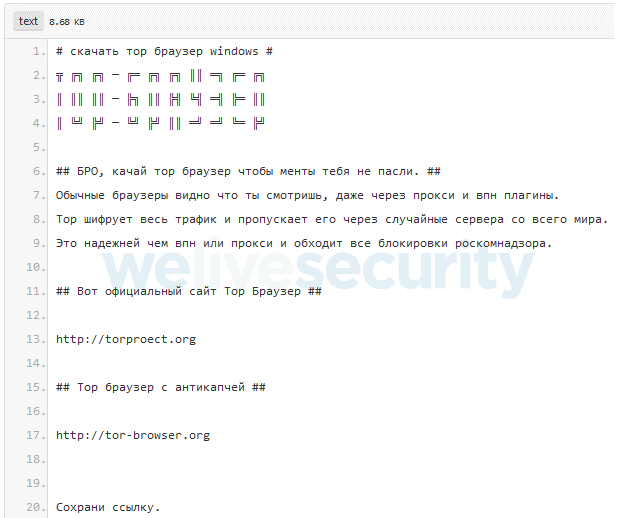
In April and March 2018, the criminals started to use the pastebin.com web service to promote both domains related to the fake Tor Browser webpage. Specifically, they created four accounts and generated a lot of pastes optimized for search engines to rank them high for words that cover topics like drugs, cryptocurrency, censorship bypass, and the names of Russian politicians.The idea behind this is that a potential victim would perform an online search for specific keywords and at some point visit a generated paste. Each such paste has a header that promotes the fake website.
This translates to English:
BRO, download Tor Browser so the cops won't watch you.
Regular browsers show what you are watching, even through proxies and VPN plug-ins.
Tor encrypts all traffic and passes it through random servers from around the world.
It is more reliable than VPN or proxy and bypasses all Roskomnadzor censorship.
Here is official Tor Browser website:
torproect[.]org
Tor Browser with anti-captcha:
tor-browser[.]org
Save the link
The criminals claim that this version of the Tor Browser has anti-captcha capability, but in fact this is not true.
All of the pastes from the four different accounts were viewed more than 500,000 times. However, it’s not possible for us to say how many viewers actually visited the websites and downloaded the trojanized version of the Tor Browser.
Analysis
This trojanized Tor Browser is a fully functional application. In fact, it is based on Tor Browser 7.5, which was released in January 2018. Thus, non-technically-savvy people probably won’t notice any difference between the original version and the trojanized one.
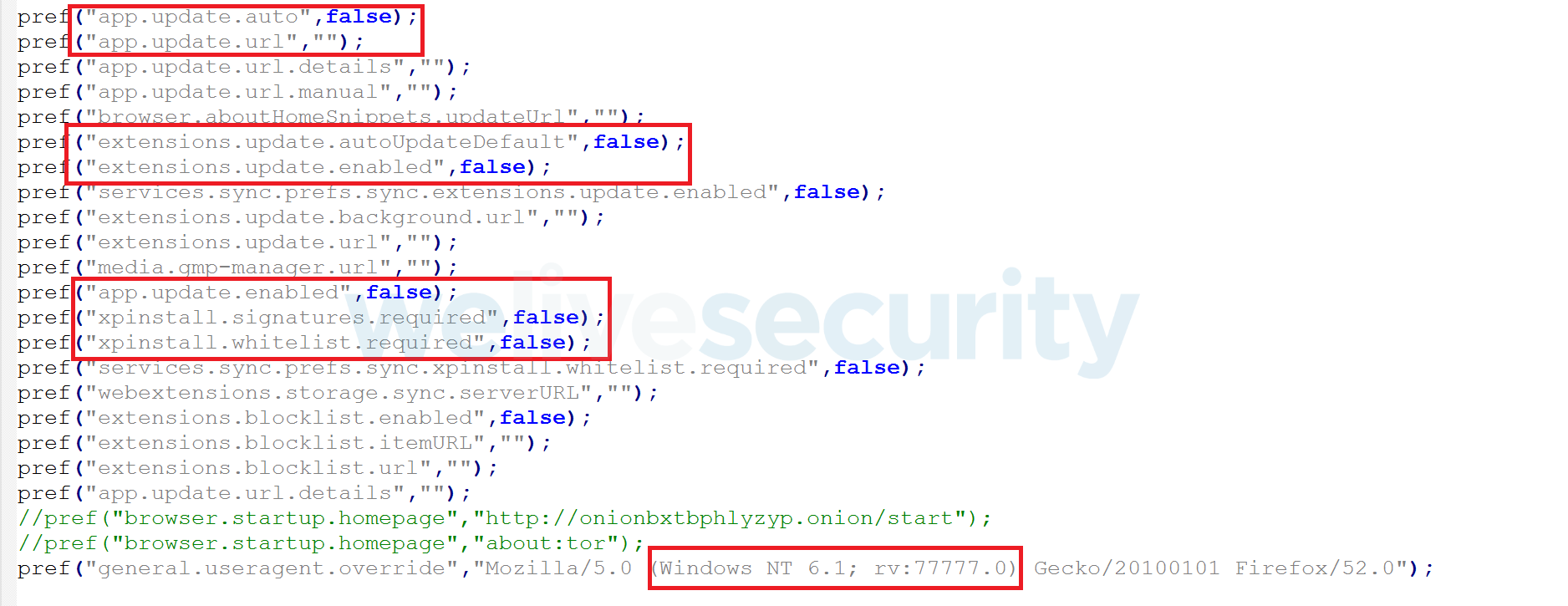
No changes were made to source code of the Tor Browser; all Windows binaries are exactly the same as in the original version. However, these criminals changed the default browser settings and some of the extensions.
The criminals want to prevent victims from updating the trojanized Tor version to a newer version, because in this case it will be updated to a non-trojanized, legitimate version. That’s why they disabled all kinds of updates in the settings, and even renamed the updater tool from updater.exe to updater.exe0.
In addition to the changed update settings, the criminals changed the default User-Agent to the unique hardcoded value:
Mozilla/5.0 (Windows NT 6.1; rv:77777.0) Gecko/20100101 Firefox/52.0
All trojanized Tor Browser victims will use the same User-Agent; thus it can be used as a fingerprint by the criminals to detect, on the server-side, whether the victim is using this trojanized version.
The most important change is to the xpinstall.signatures.required settings, which disable a digital signature check for installed Tor Browser add-ons. Therefore, the attackers can modify any add-on and it will be loaded by the browser without any complaint about it failing its digital signature check.
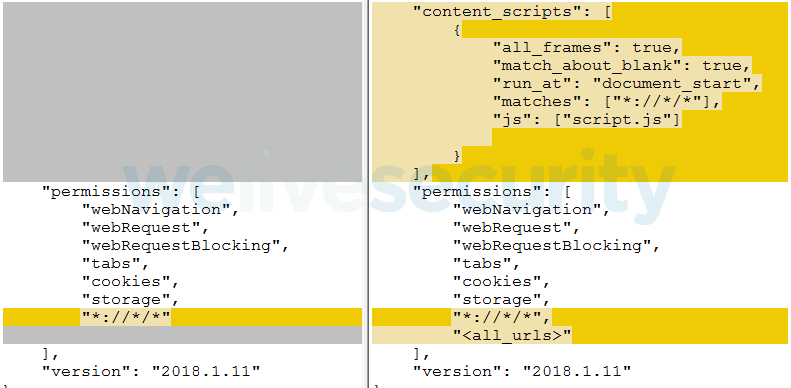
Furthermore, the criminals modified the HTTPS Everywhere add-on included with the browser, specifically its manifest.json file. The modification adds a content script (script.js) that will be executed on load in the context of every webpage.
This injected script notifies a C&C server about the current webpage address and downloads a JavaScript payload that will be executed in the context of the current page. The C&C server is located on an onion domain, which means it is accessible only through Tor.
As the criminals behind this campaign know what website the victim is currently visiting, they could serve different JavaScript payloads for different websites. However, that is not the case here: during our research, the JavaScript payload was always the same for all pages we visited.
The JavaScript payload works as a standard webinject, which means that it can interact with the website content and perform specific actions. For example, it can do a form grabbing, scrape, hide or inject content of a visited page, display fake messages, etc.
However, it should be noted that the de-anonymization of a victim is a hard task because the JavaScript payload is running in the context of the Tor Browser and does not have access to the real IP address or other physical characteristics of the victim machine.
Darknet markets
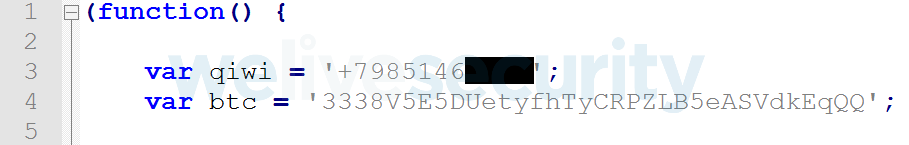
The only JavaScript payload we have seen targets three of the largest Russian-speaking darknet markets. This payload attempts to alter QIWI (a popular Russian money transfer service) or bitcoin wallets located on pages of these markets.
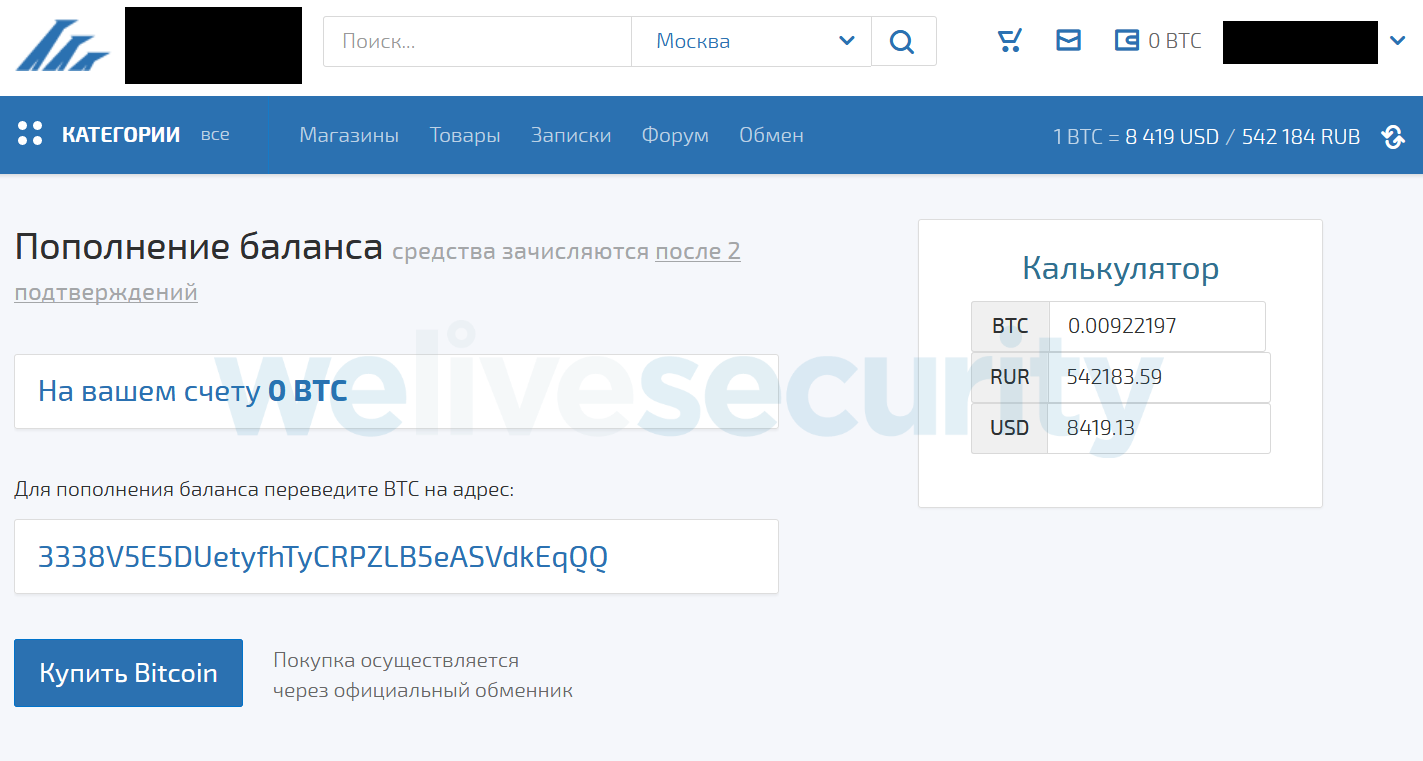
Once a victim visits their profile page in order to add funds to the account directly using bitcoin payment, the trojanized Tor Browser automatically swaps the original address to the address controlled by criminals.
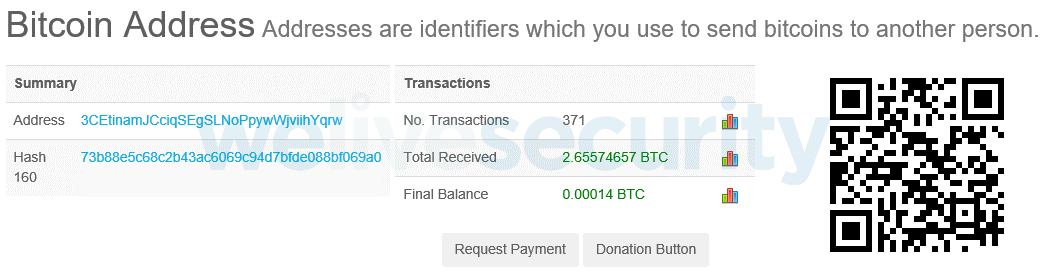
During our investigation we identified three bitcoin wallets that have been used in this campaign since 2017. Each such wallet contains relatively large numbers of small transactions; this suggests that these wallets were indeed used by the trojanized Tor Browser.
As of this writing, the total amount of received funds for all three wallets is 4.8 bitcoin, which corresponds to over US$40,000. It should be noted that the real amount of stolen money is higher because the trojanized Tor Browser also alters QIWI wallets.
Conclusion
This trojanized Tor Browser is a non-typical form of malware, designed to steal digital currency from visitors to darknet markets. Criminals didn’t modify binary components of the Tor Browser; instead, they introduced changes to settings and the HTTPS Everywhere extension. This has allowed them to steal digital money, unnoticed, for years.
Indicators of Compromise (IoCs)
ESET detection names
JS/Agent.OBW
JS/Agent.OBX
SHA-1
33E50586481D2CC9A5C7FB1AC6842E3282A99E08
Domains
torproect[.]org
tor-browser[.]org
onion4fh3ko2ncex[.]onion
Pastebin accounts
https://pastebin[.]com/u/antizapret
https://pastebin[.]com/u/roscomnadzor
https://pastebin[.]com/u/tor-browser-download
https://pastebin[.]com/u/alex-navalnii
https://pastebin[.]com/u/navalnii
https://pastebin[.]com/u/obhod-blokirovki
Bitcoin addresses
3338V5E5DUetyfhTyCRPZLB5eASVdkEqQQ
3CEtinamJCciqSEgSLNoPpywWjviihYqrw
1FUPnTZNBmTJrSTvJFweJvUKxRVcaMG8oS
MITRE ATT&CK techniques
| Tactic | ID | Name | Description |
|---|---|---|---|
| Execution | T1204 | User Execution | The trojanized Tor Browser relies on the victim to execute the initial infiltration. |
| Persistence | T1176 | Browser Extensions | The trojanized Tor Browser contains a modified HTTPS Everywhere extension. |
| Collection | T1185 | Man in the Browser | The trojanized Tor Browser is able to change content, modify behavior, and intercept information using man-in-the- browser techniques. |
| Command and Control | T1188 | Multi-hop Proxy | The trojanized Tor Browser uses Tor onion service in order to download its JavaScript payload. |
| T1079 | Multilayer Encryption | The trojanized Tor Browser uses Tor onion service in order to download its JavaScript payload. | |
| Impact | T1494 | Runtime Data Manipulation | The trojanized Tor Browser alters bitcoin and QIWI wallets on darknet market webpages. |