The rise in value of some digital currencies has led to a kind of “cryptocurrency rush” in which the mining is carried out not only by individuals trying to earn money legitimately, but also by cybercriminals who are developing threats and instigating attacks to hijack digital currencies, or otherwise using computer resources owned by regular internet users who then unwittingly contribute to mining on behalf of the attackers.
In this context, we are seeing campaigns that could turn out to be annoying, although not necessarily malicious. Specifically, we are talking about what is referred to as cryptojacking, the best example of which is the CoinHive tool, a potentially unwanted application that appeared on various websites a little while back.
Cryptojacking: malware or PUA?
With the increase in the number of websites observed to be hosting CoinHive, the mining service for the cryptocurrency Monero, which works via browsers (by inserting JavaScript code to use the processing power of visitors to the website), there has been a rise in the number of campaigns affecting users.
These campaigns could not, strictly speaking, be described as malicious, due to the characteristics of the mining method; therefore the security solutions offered by ESET identify it as a Potentially Unwanted Application (PUA).
"The issues surrounding the detection of PUAs are also rooted in other aspects beyond strictly technical matters"
Let's start with the definitions. As its name indicates, a Potentially Unwanted Application (PUA) is a program that could turn out to be troublesome to users, as it can affect systems, networks, and data confidentiality, although it is not necessarily offensive per se, as by its nature it can be used for legitimate purposes. A potentially unwanted application is a piece of software (generally commercial) that an attacker could make use of, as it could be employed to install further unwanted software, change the system's behavior, affect its performance, or run actions that are unwanted or unauthorized by the user. Its main purpose, however, is not to cause harm.
The last item on that list focuses on the actual act of cryptojacking. In other words, the unauthorized use of equipment owned by users who visit a web page that then helps attackers to carry out the mining of cryptocurrencies. Strictly speaking, this could not be described as malware, as many tools of this kind are developed for purposes of financial gain through legitimate means, i.e. with the consent of the users.
Let's imagine a case where in order to access a web page, the user has to accept the website's terms and conditions; among the provisions, there is a notification stating that when the user visits the page, their processor will be used for a period of time in order to mine for some cryptocurrency. If users read the terms and conditions but do not agree with them, they can simply not visit the website. If they decide to accept then they will know that their resources will be used for this purpose.
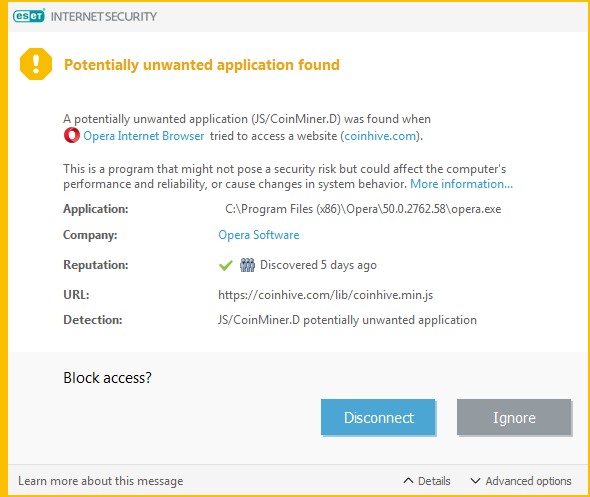
The issue with this type of service, therefore, relates to when the resources of a user's equipment are used to mine a cryptocurrency without the user's authorization or knowledge, all because a certain website was visited. For this reason, security solutions allow users to choose whether they would prefer to block access to the sites that host this application or whether to access them, as shown in the following image.
In this situation, the most important thing is that users can identify the vexatious activity on their computers and are sufficiently well informed to make what they consider as the appropriate decisions on the use of their computing resources.
Considerations regarding potentially unwanted applications
As we mentioned earlier, these types of programs tend to present behavior which is likely to be unwanted by the user, and generally speaking do not exhibit the actions typical of malware, as they require user consent prior to installation (User License Agreement).
"These campaigns could not, strictly speaking, be described as malicious, due to the characteristics of the mining method"
However, they may carry out other types of actions, such as installing additional applications, changing the behavior of the environment in which they are executed, installing some kind of adware without warning in order to display unwanted ads, changing browser settings, or installing toolbars. They may also be considered as tools for use in audits, such as in the case of those that allow sysadmins to check for weak passwords (which can then be replaced with strong ones), but which due to this functionality may be used to perform malicious actions.
The issues surrounding the detection of PUAs are also rooted in other aspects beyond strictly technical matters. For example, it is important to determine whether or not the application in question is really legitimate, on the basis of the intention of its developers, and the possible legal and ethical issues that these types of programs bring to light.
To be able to establish in a discerning manner just how malicious an application is and whether it has the necessary background to be placed in the category of PUAs, a wide range of factors needs to be considered, such as the functions and uses it offers the user, the distribution model or channel through which it is obtained, and the potential threat it could represent for a system's security and stability.
Tools for mining cryptocurrencies also fall into this category, as in many cases the websites cannot warn users since they have been compromised themselves, hence even the administrators may not be aware that they are contributing to mining for the benefit of an attacker.
Web mining services continue to grow in popularity with high levels of activity in recent weeks and months, which may mean that cryptojacking is a growing trend, resulting from the cryptocurrency rush.
Image credits: © vjkombajn/Pixabay.com