Update (July 9th): This article has been amended to include more information on the unique characteristics of Win32/Diskcoder.C.
The latest global cyberattack, detected by ESET as Win32/Diskcoder.C, once again highlights the reality that outdated systems and insufficient security solutions are still widespread.
The damage caused by this attack has raised a number of questions, which we’ll answer for you here.
What are the characteristics of this threat?
- Encryption: It only encrypts files with a specific extension, but also attempts (usually successfully) to encrypt the MBR (Master Boot Record), which is the main boot record.
- Propagation: Like a worm, it can spread through the network, infecting new equipment.
- Exploits: It exploits vulnerabilities in both computers that have not been updated and/or in patches that have been installed. This is something that has been discussed a lot since the appearance of WannaCryptor.
Is it as powerful as WannaCryptor?
Both have the same impact. They prevent access to information stored in a system. However, Diskcoder.C not only encrypts the information that is on vulnerable computers, but, after the system is restarted, it leaves the operating system unusable, so victims are forced to perform a reinstallation.
Does it propagate in the same way as WannaCryptor?
Yes and no. Both use the NSA exploit called EternalBlue. However, Win32/Diskcoder.C implements other propagation techniques by abusing legitimate Microsoft Windows tools, such as PsExec, which is part of the Sysinternals suite of tools, and Windows Management Instrumentation Command-line (WMIC), a source for managing data and functionality on local and remote computers running Windows operating systems.
What similarities does it have with Mischa and Petya?
The main reason they are often grouped together is that these three malicious families make the operating system unusable by encrypting the MBR, as well as the data that is in the operating system.Other than this, they do not have much else in common, given that they implement different processes and use different techniques.
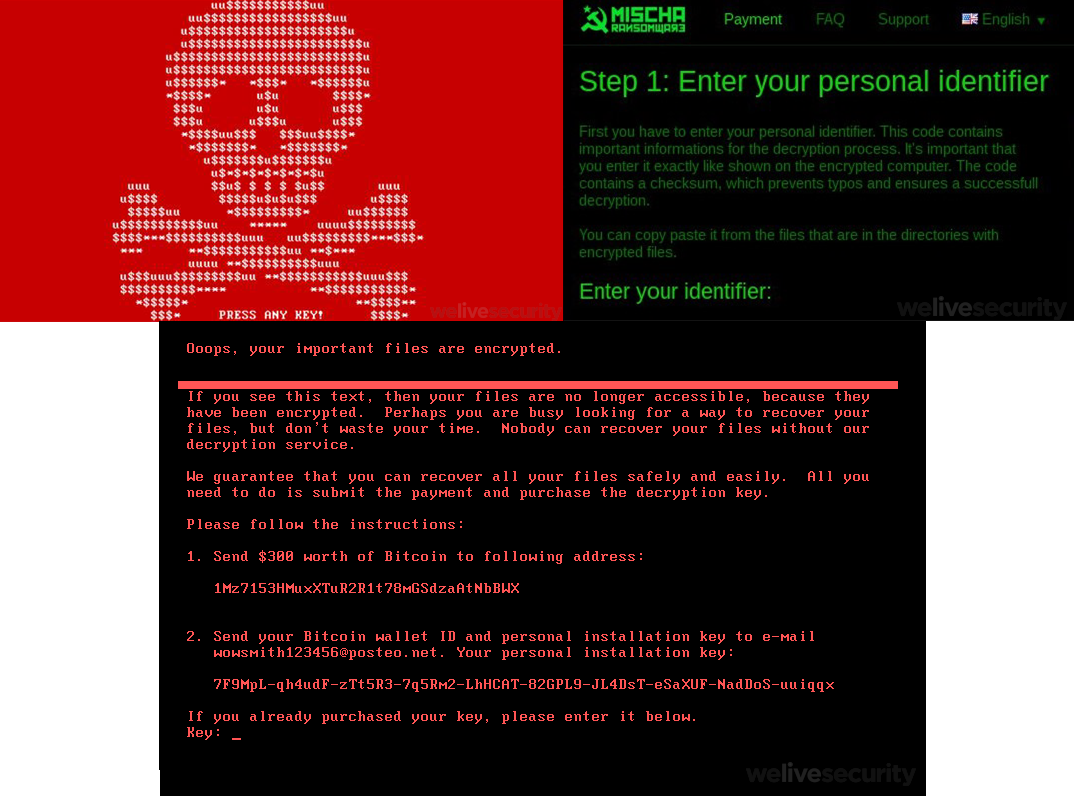
What exactly does this threat do?
After the malicious software is run, it creates a scheduled task to restart the computer within a certain timeframe, which is usually no more than 60 minutes.
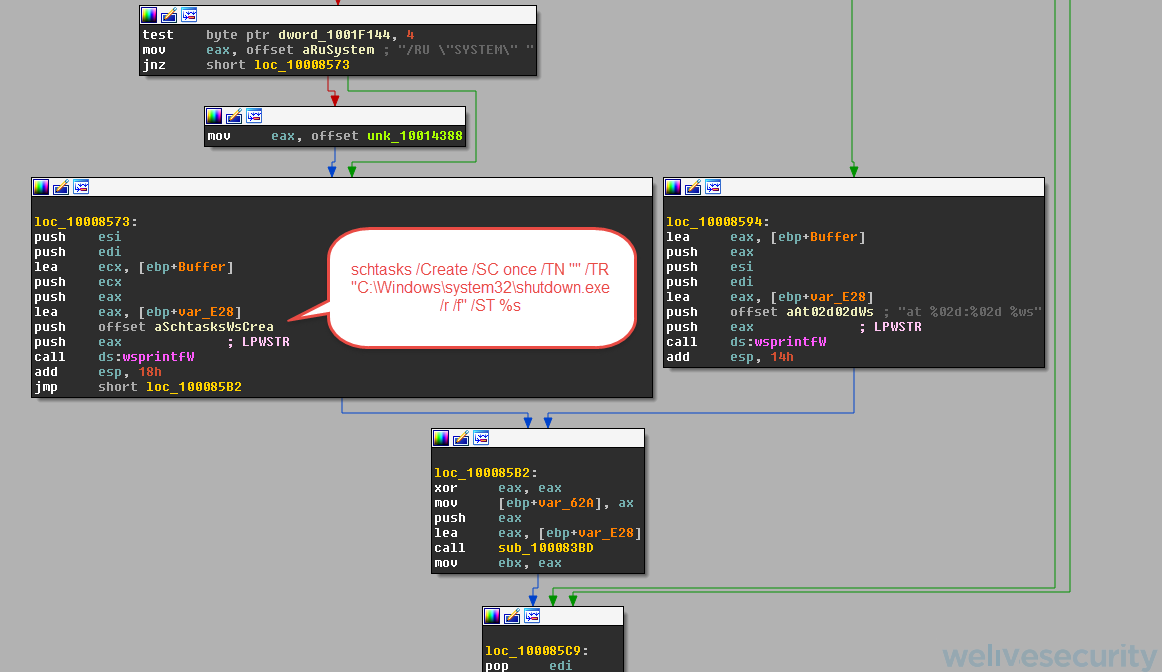
In addition, it verifies whether or not there are shared folders or disks to which the malware can propagate. If there are, it uses WMIC to run the malicious software on the remote machine.
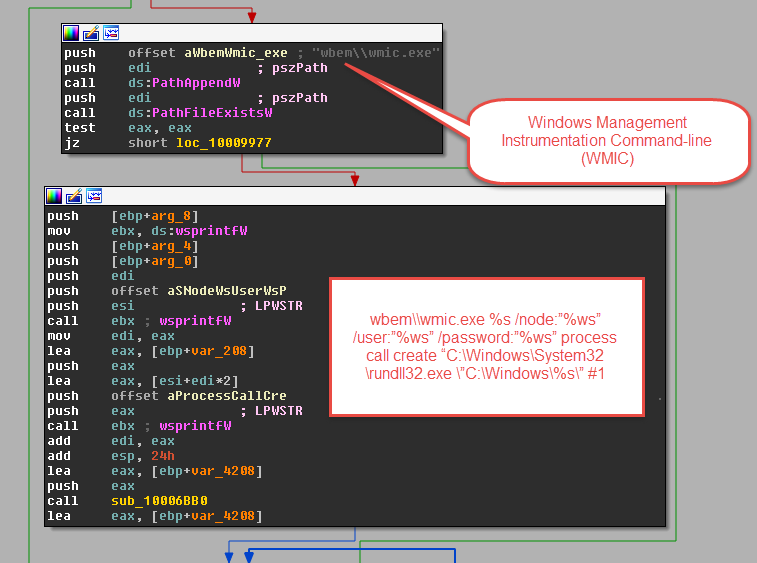
It then starts encrypting files that contain certain extensions. We should highlight that, unlike most ransomware, Win32/Diskcoder.C does not change or add a particular extension after encrypting each file, which is a technique widely used by attackers to distinguish infected files.
In the following screenshot you can see the file extensions that the malware will attempt to encrypt:
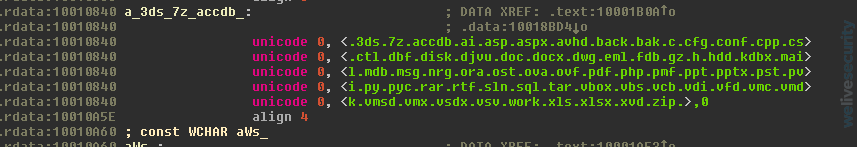
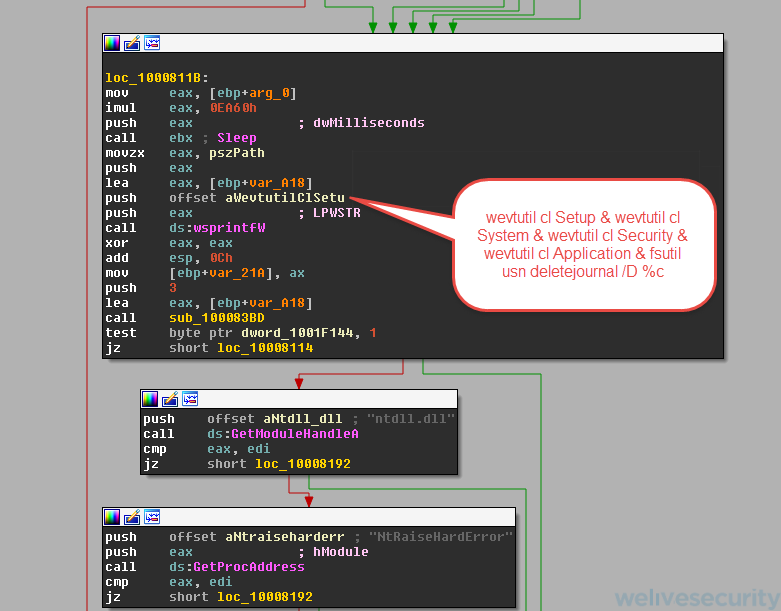
In addition, the malware will try to delete event logs to leave no trace, as well as hide their actions. The next screenshot shows the command that is executed using aforementioned technique:
How does it spread from one country to another?
As previously mentioned, propagation is a prominent characteristic of this threat. Once it manages to infect a computer, it attempts to extract the user's credentials and then use them with PsExec and WMIC to search for shared folders and disks. It then spreads via the computer network. In this way, it manages to infect computers located in different countries and regions.
In most cases, it was detected within teams of multinational companies that were connected to the same network with those of other subsidiaries in Europe or Asia. It then spread in the same manner as a worm.
What can I do to stay protected from this threat?
We recommend reading the related article in our Knowledge Base and taking into account the following tips:
Antivirus solution
Install an antivirus solution on your home and work computers and ensure your system is regularly updated.
It has to be properly configured in order to identify which ports are open and why - especially ports 135, 139, 445 and 1025-1035 TCP, which use WMI and PsExec.
Block EXE files
You should also block the execution of EXE files within % AppData% and %Temp%; Disable the default ADMIN$ accounts and/or communicate with Admin$ shares. And, if possible, disable SMB version 1.
Monitor your network
Ensure your network is well-configured and segmented, and constantly monitor traffic for any abnormal behavior.
Back up your data
Identify crucial data and information on your computer and make a backup of it—and keep the backup offline. This way, if your computer is attacked successfully by ransomware, there will be a way to restore it to a recent state.
Password management
It is essential to manage passwords carefully. If the same password is used across different management centers, even if only one of the infected machines possesses the credentials of administrator, this could infect the whole network.
To avoid this, it’s best to ensure that passwords should not be replicated across different teams and management centers.
It is also important to use two-factor authentication, since it adds an additional layer of protection to the credentials normally used for validating users. In case of infection, this would prevent lateral movement across your network should the malware try to gain remote Admin access to those other computers.
What do I do if I got infected and can’t access the system?
It’s possible to use forensic techniques to try to run another operating system in memory and thus access the encrypted files. However, there is not much that can be done other than to apply the backup, which would be crucial to avoid reinstalling the operating system.
Ultimately, if there is no backup, it may be tempting to pay the cybercriminals their demanded ransom but ESET would not recommend this for several reasons.
Ransom payment is particularly useless in this case. Recent research from ESET on TeleBots, the group that may have been behind this attack attack, suggests that Win32/Diskcoder.C is not typical ransomware.
Although it encrypts the files and demands a ransom equivalent to 300 dollars, the attackers actually wanted – as their primary goal – to cause damage. Accordingly, they did all that they could to make data decryption very unlikely.
Moreover, the malware has the ability to replace the Master Boot Record (MBR) with its own malicious code. However, this was implemented in such a way that recovery is not possible. The attackers cannot provide a decryption key and the decryption key cannot be typed in the ransom screen because the generated key contains non-acceptable characters.
How are the attackers operating and do they expect to receive a payment?
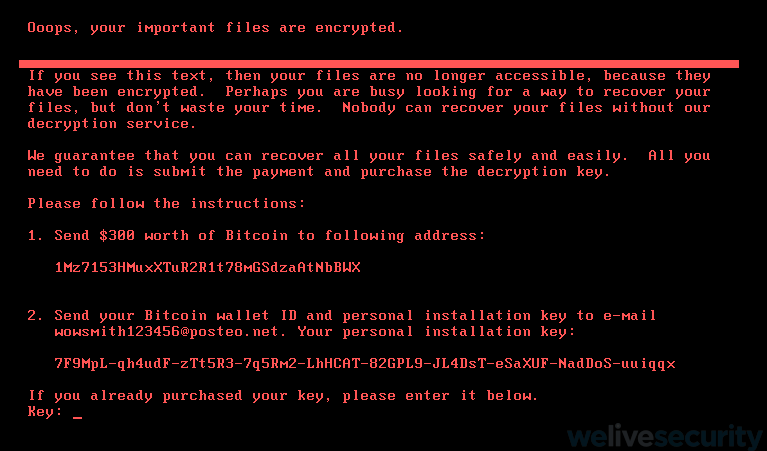
Once the encryption is completed, Win32/Diskcoder.C issues a set of instructions via which the attackers request a payment in bitcoins. The example below displays a ransom that is equivalent to 300 dollars.
Why has data hijacking become so common?
Lack of awareness, insufficient training at companies and the skills shortage are just some of the reasons hijacking has become so common. Unfortunately, many employees are still unaware of the potential impact a cyberattack can have on a business model until they themselves become victims and are facing a ransomware demand.
Based on the low defense levels they encounter, cybercriminals are both motivated and able to continue exploiting weaknesses, developing new ransomware and successfully carry out damaging attacks.
Was the attack carried out single-handedly?
It is hard to believe that one person alone could be behind this attack, given the highly technical nature of Win32/Diskcoder.C in terms of exploits, propagation and encryption, as well as the way in which it evaded security measures.
However, at this stage, we can’t rule out the possibility that a group was behind the attack - let alone predict its size.
Is it possible to locate the perpetrators of the attack?
Not for now. Unlike a botnet, for example, there is no C&C connected to the threat in order to trace it and find the perpetrators. And If there were, the likelihood is that it would be a foreign server that was attacked to take control and access from TOR, hence achieving anonymity.
In addition, the currency for the ransom payment is in bitcoins and, due to the characteristics of this cryptocurrency, it becomes practically impossible to trace its final destination.




