ESET researchers have discovered a new exploit kit spreading via malicious ads on a number of reputable news websites, each with millions of visitors daily. Since at least the beginning of October 2016, the bad guys have been targeting users of Internet Explorer and scanning their computers for vulnerabilities in Flash Player. Exploiting these flaws in the code, they have been attempting to download and execute various types of malware.
The attacks fall into the category of so-called malvertising due to the fact that the malicious code has been distributed through advertising banners.
To make things worse, the attackers responsible are using stealthy, even paranoid, techniques, which makes analysis quite complicated and has thus necessitated an extensive research report.
I asked Robert Lipovsky, one of ESET’s senior malware researchers, to give us a less technical overview of the case.
What does your discovery mean for internet users?
It means that there are advertising banners with “poisoned pixels” leading to a new exploit kit, intended to enable the bad guys to remotely install malware onto victims’ computers. The victim doesn’t even need to click on the malicious ad content; all it takes is to visit a website displaying it. If the victim’s computer runs a vulnerable version of Flash Player, the machine will be compromised via an exploited vulnerability automatically.
After that, the bad guys have all they need to download and execute the malware of their choice. Some of the payloads we analyzed include banking trojans, backdoors and spyware, but the victims could end up facing a nasty ransomware attack, for example.
Once again this threat shows how important it is to have your software fully patched and to be protected by a reputable security solution. In this particular case, either of these measures fully protects you from this specific attack.
Where are the poisoned pixels in this?
Well, the name “Stegano” refers to steganography, which is a technique the bad guys used to hide parts of their malicious code in the pixels of the advertisements' banners. Specifically, they hide it in the parameters controlling the transparency of each pixel. This makes only minor changes to the (color) tone of the picture, making the changes effectively invisible to the naked eye and so unnoticed by the potential victim.
How does the attack work?
I believe the following scheme is the best way to explain what is happening in this case:
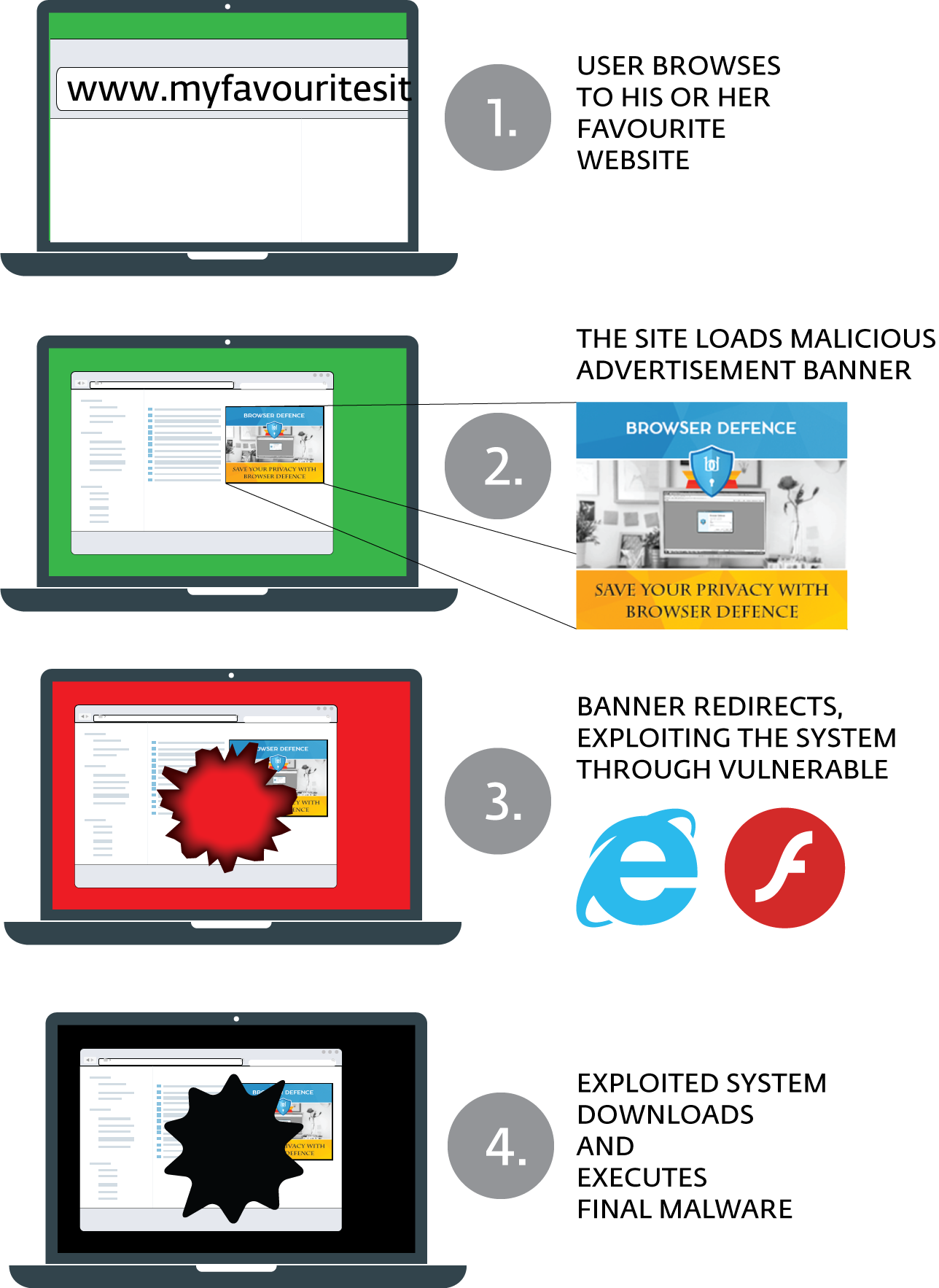
Your analysis shows that the creators of the Stegano exploit kit are trying hard to stay unseen. What makes them so paranoid?
Attackers have succeeded in circumventing the countermeasures designed to uncover and block malicious content on advertising platforms, which has resulted in legitimate websites unknowingly serving infected content to millions of potential victims.
On top of that, the malicious version of the ad is served only to a specific target group, selected by the attackers’ server. The decision-making logic behind the choice of target is unknown and this helps the bad guys to go further in dodging suspicion on the advertising platforms’ side.
But those are not the only reasons why they try hard to stay stealthy – and that’s where the attackers get really paranoid.
The crooks behind the Stegano exploit kit are also trying to stay off the radar of experienced cybersecurity research teams hunting for malware. Hiding code in the pixels would not be enough to escape this kind of attention, so they have implemented a series of checks to detect whether the code is being surveilled. If any kind of surveillance is detected, the exploit kit’s activities simply stop and no malicious content is served.
How do they know when the code is being observed?
The exploit kit mainly tries to detect whether or not it is sitting in a sandbox, or if it is running on a virtual machine that was created for detection purposes. Also, the malware checks for any security software that might be present and sends this information to its operators.
Can you say how many users have already seen these banners with poisoned pixels?
Our detection systems show that in the last two months the malicious ads have been displayed to more than a million users on several very popular websites. Bear in mind, this is a rather conservative estimate based only on our own telemetry from users participating in ESET LiveGrid®. After all, the visitor counts of some of these websites are in the millions daily.
Can you be more specific? Which websites were affected?
The purpose of this research is to shed light on the activities of the bad guys and to make users safe from this threat. In this case, disclosure of the websites known to have been affected wouldn’t add any extra value in this regard. On the contrary, it could provide a false sense of security to those who have not visited these sites, as the banners could have appeared on practically any website that displays ads.
We should also mention the reputational harm this could inflict on victimized pages, especially since there is nothing they could have done to prevent these attacks, as the targeted ad space isn’t completely under their control.
What should I do to stay protected from exploit kit attacks?
First of all, let me highlight again that those who are diligent in protecting their computers, are safe from these specific attacks. Keeping both the system and all applications patched and using a reliable internet security solution are strong precautions that help prevent such attacks.
However, for unwary users, malvertising poses a serious threat, and their only hope is that malicious banners won’t make it onto websites they visit.





