UPDATE (November 13th, 2023): The website has removed the "DOWNLOAD APP" button, although the malicious app is still hosted on its servers.
ESET researchers have identified what appears to be a watering-hole attack on a regional news website that delivers news about Gilgit-Baltistan, a disputed region administered by Pakistan. When opened on a mobile device, the Urdu version of the Hunza News website offers readers the possibility to download the Hunza News Android app directly from the website, but the app has malicious espionage capabilities. We named this previously unknown spyware Kamran because of its package name com.kamran.hunzanews. Kamran is a common given name in Pakistan and other Urdu-speaking regions; in Farsi, which is spoken by some minorities in Gilgit-Baltistan, it means fortunate or lucky.
The Hunza News website has English and Urdu versions; the English mobile version doesn’t provide any app for download. However, the Urdu version on mobile offers to download the Android spyware. It is worth mentioning that both English and Urdu desktop versions also offer the Android spyware; although, it is not compatible with desktop operating systems. We reached out to the website concerning the Android malware. However, prior to the publication of our blogpost, we did not receive any response.
Key points of the report:
- Android spyware, which we named Kamran, has been distributed via a possible watering-hole attack on the Hunza News website.
- The malware targets only Urdu-speaking users in Gilgit-Baltistan, a region administered by Pakistan.
- The Kamran spyware displays the content of the Hunza News website and contains custom malicious code.
- Our research shows that at least 20 mobile devices were compromised.
Upon launching, the malicious app prompts the user to grant it permissions to access various data. If accepted, it gathers data about contacts, calendar events, call logs, location information, device files, SMS messages, images, etc. As this malicious app has never been offered through the Google Play store and is downloaded from an unidentified source referred to as Unknown by Google, to install this app, the user is requested to enable the option to install apps from unknown sources.
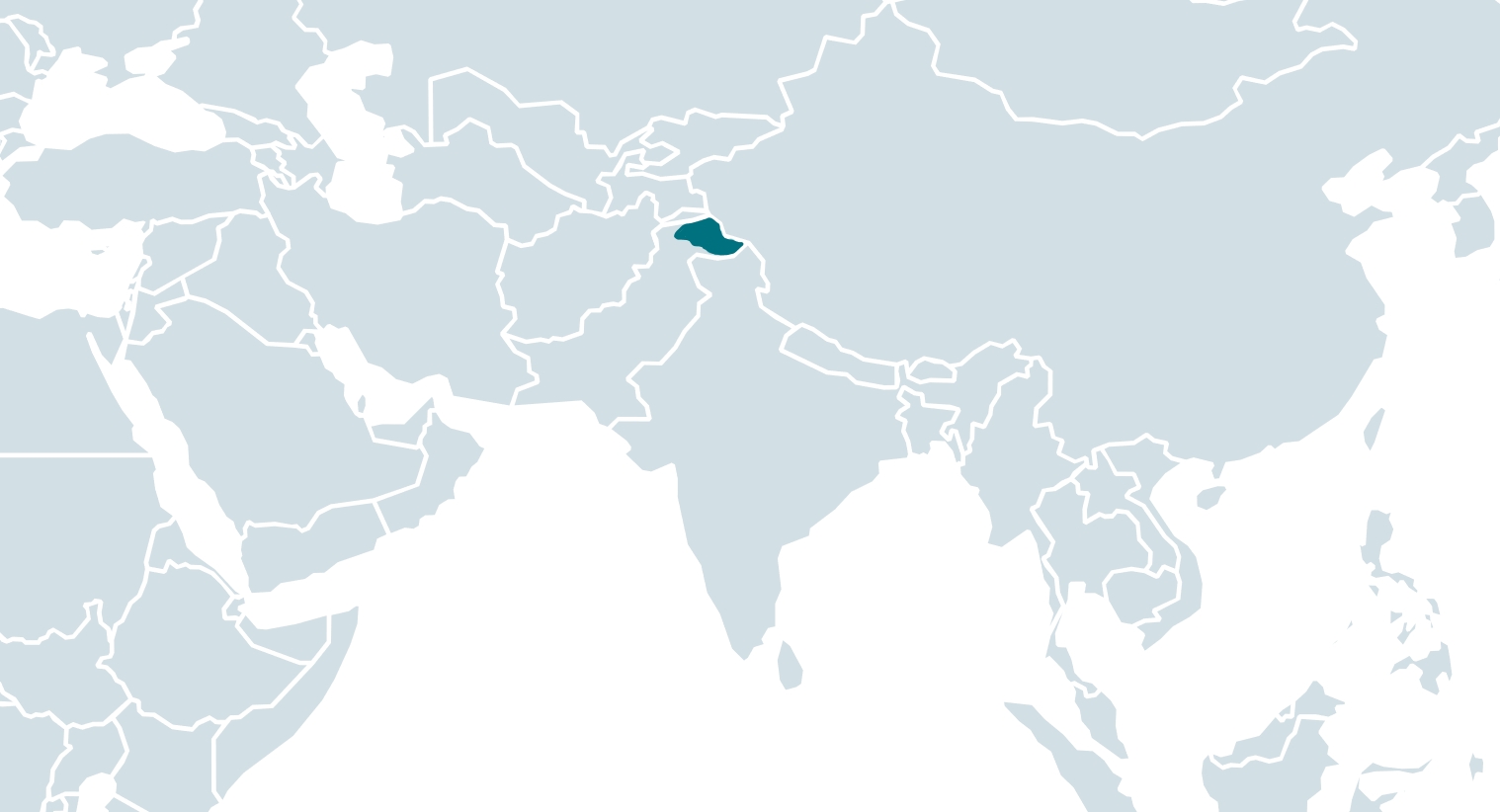
The malicious app appeared on the website sometime between January 7th, 2023, and March 21st, 2023; the developer certificate of the malicious app was issued on January 10, 2023. During that time, protests were being held in Gilgit-Baltistan for various reasons encompassing land rights, taxation concerns, prolonged power outages, and a decline in subsidized wheat provisions. The region, shown in the map in Figure 1, is under Pakistan’s administrative governance, consisting of the northern portion of the larger Kashmir region, which has been the subject of a dispute between India and Pakistan since 1947 and between India and China since 1959.
Overview
Hunza News, likely named after the Hunza District or the Hunza Valley, is an online newspaper delivering news related to the Gilgit-Baltistan region.
The region, with a population of around 1.5 million, is famous for the presence of some of the highest mountains globally, hosting five of the esteemed “eight-thousanders” (mountains that peak at more than 8,000 meters above sea level), most notably K2, and is therefore frequently visited by international tourists, trekkers, and mountaineers. Because of the protests in spring 2023, and additional ones happening in September 2023, the US and Canada have issued travel advisories for this region, and Germany suggested tourists should stay informed about the current situation.
Gilgit-Baltistan is also an important crossroad because of the Karakoram Highway, the only motorable road connecting Pakistan and China, as it allows China to facilitate trade and energy transit by accessing the Arabian Sea. The Pakistani portion of the highway is currently being reconstructed and upgraded; the efforts are financed by both Pakistan and China. The highway is frequently blocked by damage caused by weather or protests.
The Hunza News website provides content in two languages: English and Urdu. Alongside English, Urdu holds national language status in Pakistan, and in Gilgit-Baltistan, it serves as the common or bridge language for interethnic communications. The official domain of Hunza News is hunzanews.net, registered on May 22nd, 2017, and has been consistently publishing online articles since then, as evidenced by Internet Archive data for hunzanews.net.
Prior to 2022, this online newspaper also used another domain, hunzanews.com, as indicated in the page transparency information on the site’s Facebook page (see Figure 2) and the Internet Archive records of hunzanews.com, Internet Archive data also shows that hunzanews.com had been delivering news since 2013; therefore, for around five years, this online newspaper was publishing articles via two websites: hunzanews.net and hunzanews.com. This also means that this online newspaper has been active and gaining online readership for over 10 years.
In 2015, hunzanews.com started to provide a legitimate Android application, as shown in Figure 3, which was available on the Google Play store. Based on available data we believe two versions of this app were released, with neither containing any malicious functionality. The purpose of these apps was to present the website content to readers in a user-friendly way.
In the second half of 2022, the new website hunzanews.net underwent visual updates, including the removal of the option to download the Android app from Google Play. Additionally, the official app was taken down from the Google Play store, likely due to its incompatibility with the latest Android operating systems.
For a few weeks, from at least December 2022 until January 7th, 2023, the website provided no option to download the official mobile app, as shown in Figure 4.

Based on Internet Archive records, it is evident that at least since March 21st, 2023, the website reintroduced the option for users to download an Android app, accessible via the DOWNLOAD APP button, as depicted in Figure 5. There is no data for the period between January 7th and March 21st, 2023, which could help us pinpoint the exact date of the app’s reappearance on the website.

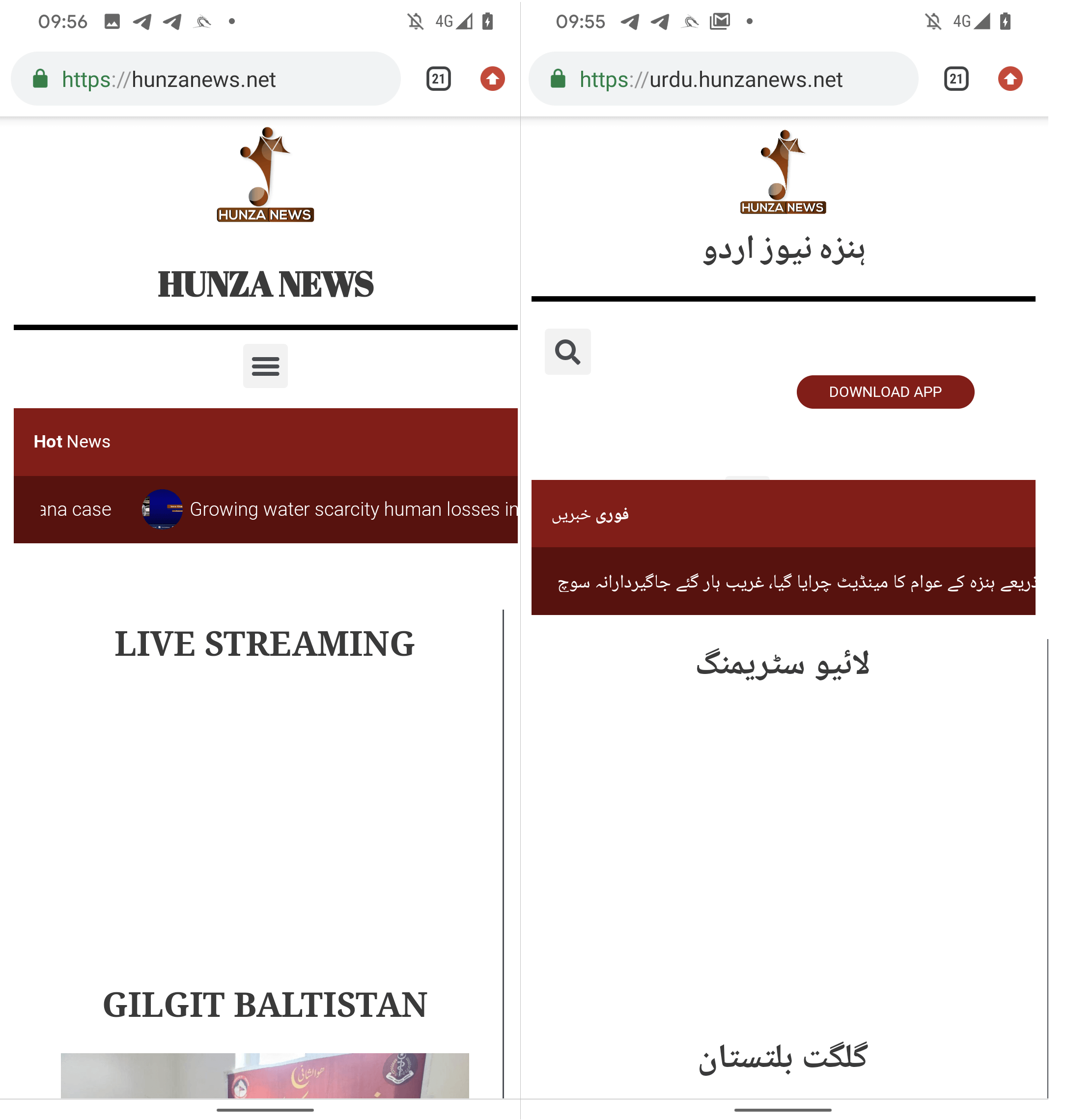
When analyzing several versions of the website, we came across something interesting: viewing the website in a desktop browser in either language version of Hunza News – English (hunzanews.net) or Urdu (urdu.hunzanews.net) – prominently displays the DOWNLOAD APP button at the top of the webpage. The downloaded app is a native Android application which cannot be installed on a desktop machine and compromise it.
However, on a mobile device, this button is exclusively visible on the Urdu language variant (urdu.hunzanews.net), as shown in Figure 6.
With a high degree of confidence, we can affirm that the malicious app is specifically targeted at Urdu-speaking users who access the website via an Android device. The malicious app has been available on the website since the first quarter of 2023.
Clicking on the DOWNLOAD APP button triggers a download from https://hunzanews[.]net/wp-content/uploads/apk/app-release.apk. As this malicious app has never been offered through the Google Play store and is downloaded from a third-party site to install this app, the user is requested to enable the non-default, Android option to install apps from unknown sources.
The malicious app, called Hunza News, is previously unknown spyware that we named Kamran and that is analyzed in the Kamran section below.
ESET Research reached out to Hunza News regarding Kamran. Before the publication of our blogpost we did not receive any form of feedback or response from the website's side.
Victimology
Based on the findings from our research, we were able to identify at least 22 compromised smartphones, with five of them being located in Pakistan.
Kamran
Kamran is previously undocumented Android spyware characterized by its unique code composition, distinct from other, known spyware. ESET detects this spyware as Android/Spy.Kamran.
We identified only one version of a malicious app containing Kamran, which is the one available to download from the Hunza News website. As explained in the Overview section, we are unable to specify the exact date on which the app was placed on the Hunza News website. However, the associated developer certificate (SHA-1 fingerprint: DCC1A353A178ABF4F441A5587E15644A388C9D9C), used to sign the Android app, was issued on January 10th, 2023. This date provides a floor for the earliest time that the malicious app was built.
In contrast, legitimate applications from Hunza News that were formerly available on Google Play were signed with a different developer certificate (SHA-1 fingerprint: BC2B7C4DF3B895BE4C7378D056792664FCEEC591). These clean and legitimate apps exhibit no code similarities with the identified malicious app.
Upon launching, Kamran prompts the user to grant permissions for accessing various data stored on the victim’s device, such as contacts, calendar events, call logs, location information, device files, SMS messages, and images. It also presents a user interface window, offering options to visit Hunza News social media accounts, and to select either the English or Urdu language for loading the contents of hunzanews.net, as shown in Figure 7.
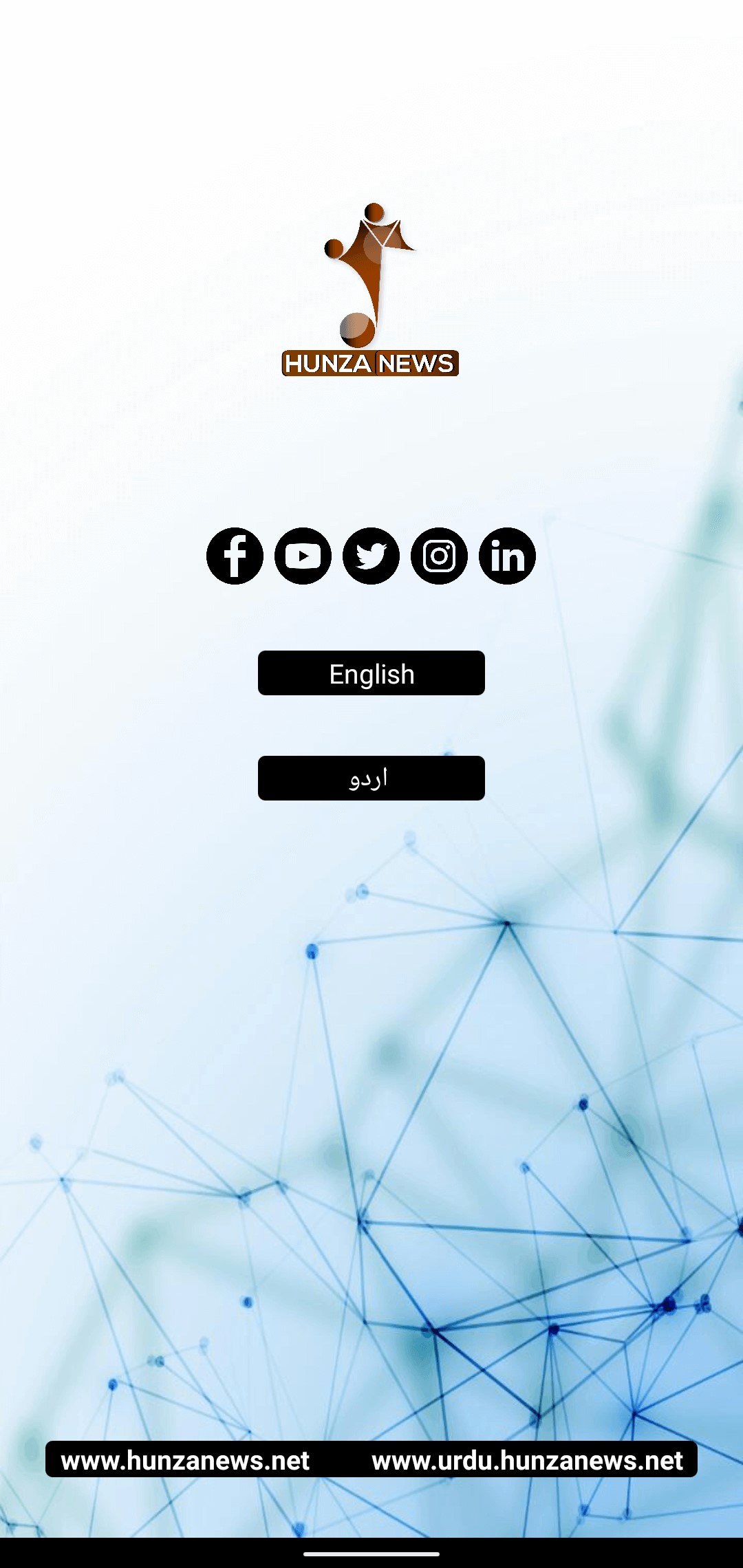
If the abovementioned permissions are granted, the Kamran spyware automatically gathers sensitive user data, including:
- SMS messages
- contacts list
- call logs
- calendar events
- device location
- list of installed apps
- received SMS messages
- device info
- images
Interestingly, Kamran identifies accessible image files on the device (as depicted in Figure 8), obtains the file paths for these images, and stores this data in an images_db database, as demonstrated in Figure 9. This database is stored in the malware’s internal storage.
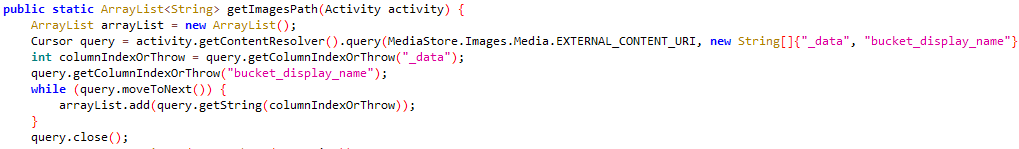
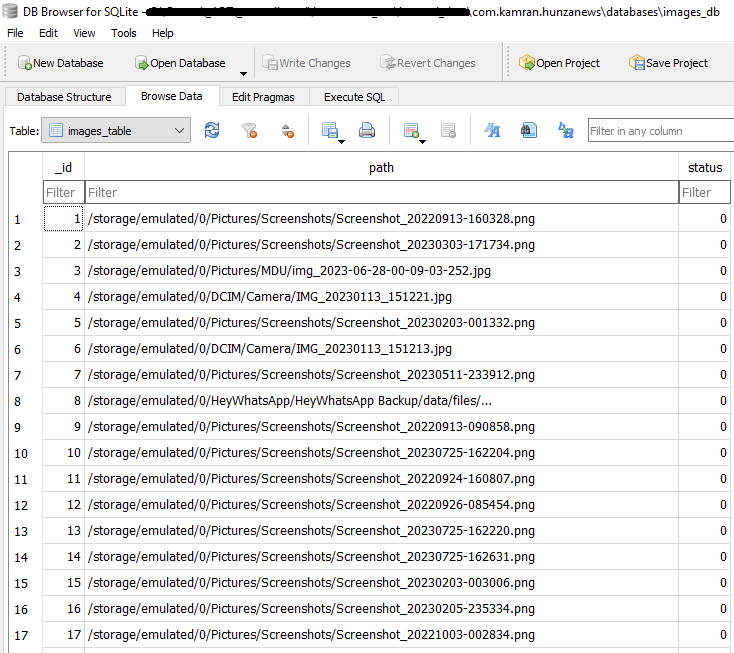
All types of data, including the image files, are uploaded to a hardcoded command and control (C&C) server. Interestingly, the operators opted to utilize Firebase, a web platform, as their C&C server: https://[REDACTED].firebaseio[.]com. The C&C server was reported to Google, as the platform is provided by this technology company.
It is important to note that the malware lacks remote control capabilities. As a result, user data is exfiltrated via HTTPS to the Firebase C&C server only when the user opens the app; data exfiltration cannot run in the background when the app is closed. Kamran has no mechanism tracking what data has been exfiltrated, so it repeatedly sends the same data, plus any new data meeting its search criteria, to its C&C.
Conclusion
Kamran is previously unknown Android spyware targeting Urdu-speaking people in the Gilgit-Baltistan region. Our research indicates that the malicious app containing Kamran has been distributed since at least 2023 via what probably is a watering-hole attack on a local, online newspaper named Hunza News.
Kamran demonstrates a unique codebase distinct from other Android spyware, preventing its attribution to any known advanced persistent threat (APT) group.
This research also shows that it is important to reiterate the significance of downloading apps exclusively from trusted and official sources.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
|
SHA-1 |
Package name |
Detection |
Description |
|
0F0259F288141EDBE4AB2B8032911C69E03817D2 |
com.kamran.hunzanews |
Android/Spy.Kamran.A |
Kamran spyware. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
34.120.160[.]131 |
[REDACTED].firebaseio[.]com |
Google LLC |
2023-07-26 |
C&C server. |
|
191.101.13[.]235 |
hunzanews[.]net |
Domain.com, LLC |
2017-05-22 |
Distribution website. |
MITRE ATT&CK techniques
This table was built using version 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Name |
Description |
|
Discovery |
Software Discovery |
Kamran spyware can obtain a list of installed applications. |
|
|
File and Directory Discovery |
Kamran spyware can list image files on external storage. |
||
|
System Information Discovery |
Kamran spyware can extract information about the device, including device model, OS version, and common system information. |
||
|
Collection |
Data from Local System |
Kamran spyware can exfiltrate image files from a device. |
|
|
Location Tracking |
Kamran spyware tracks device location. |
||
|
Protected User Data: Calendar Entries |
Kamran spyware can extract calendar entries. |
||
|
Protected User Data: Call Logs |
Kamran spyware can extract call logs. |
||
|
Protected User Data: Contact List |
Kamran spyware can extract the device’s contact list. |
||
|
Protected User Data: SMS Messages |
Kamran spyware can extract SMS messages and intercept received SMS. |
||
|
Command and Control |
Application Layer Protocol: Web Protocols |
Kamran spyware uses HTTPS to communicate with its C&C server. |
|
|
Web Service: One-Way Communication |
Kamran uses Google’s Firebase server as its C&C server. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
Kamran spyware exfiltrates data using HTTPS. |










