You’ve just downloaded a new mobile game, cryptocurrency wallet, or fitness app, but something isn’t right. Your phone’s screen is swamped by annoying ads, the app is not doing what you would expect it do, and, God forbid, you found an unauthorized transaction on your bank account.
Chances are good that the app you downloaded has been after your money or sensitive information. Given the wealth of data we access via our smartphones, it’s little wonder that cybercriminals have their sights on these devices, with threats looming large especially in third-party app stores.
According to the ESET Threat Report T3 2022, the number of Android threats soared by 57% in the last few months of 2022, having been driven by a whopping 163% increase in adware and growth of 83% in HiddenApps detections,
Luckily, you can avoid both malware and potentially unwanted applications (PUAs) by being cautious and doing your diligence. Our tips below will help you to spot a potentially dodgy app from miles away, as well as get your phone back into shape if you downloaded such an app.
How to recognize a fake app
- Check the numbers
Say you’re looking for what you would reasonably expect to be an app with hundreds of millions of users but only come across an app that, while sounding like the real thing, hasn’t racked up nowhere near as many downloads. If that’s the case, chances are high you’re dealing with an imposter app.
Indeed, be cautious whenever you’re looking to download an app that has been the talk of the town lately. Cybercriminals are always eager to piggyback off a surge in the popularity of an app or service in order to push copycat apps to the market. One recent example is a slew of sketchy apps that attempt to ride the ChatGPT craze and that were rolled out even before the official app was released.
Much the same applies to bogus updates for legitimate and widely-used apps. One example is the curious case of WhatsApp Pink, a fake color theme for WhatsApp that was peddled via messages on the app in 2021.
- Read the reviews
If an app is rated poorly, you should probably give it a pass. On the other hand, tons of glowing reviews that all sound almost the same should also raise eyebrows. This is especially the case with apps that have not been downloaded millions of times – many of those recommendations may be the work of fake reviewers or even bots.
- Check the visuals
Something about the app’s color or logo used doesn’t feel right ... If you’re in doubt, compare the visuals to those on the website of the service provider. Malicious apps often their mimic legitimate counterparts and use similar, but not necessarily identical, logos.

The impostor is on the right (source: ESET Research)
However, don’t be lulled into a false sense of security just because you recognized the logo of a well-known bank, payment processor or cryptocurrency wallet. Some apps not only misuse the name of a legit service, but are also distributed via websites that are the spitting images of the legitimate sites. Keep your eyes peeled for details – a closer look, including at the URLs, often reveals some giveaways.
Legitimate website on the left, copycat on the right (Source: ESET Research)
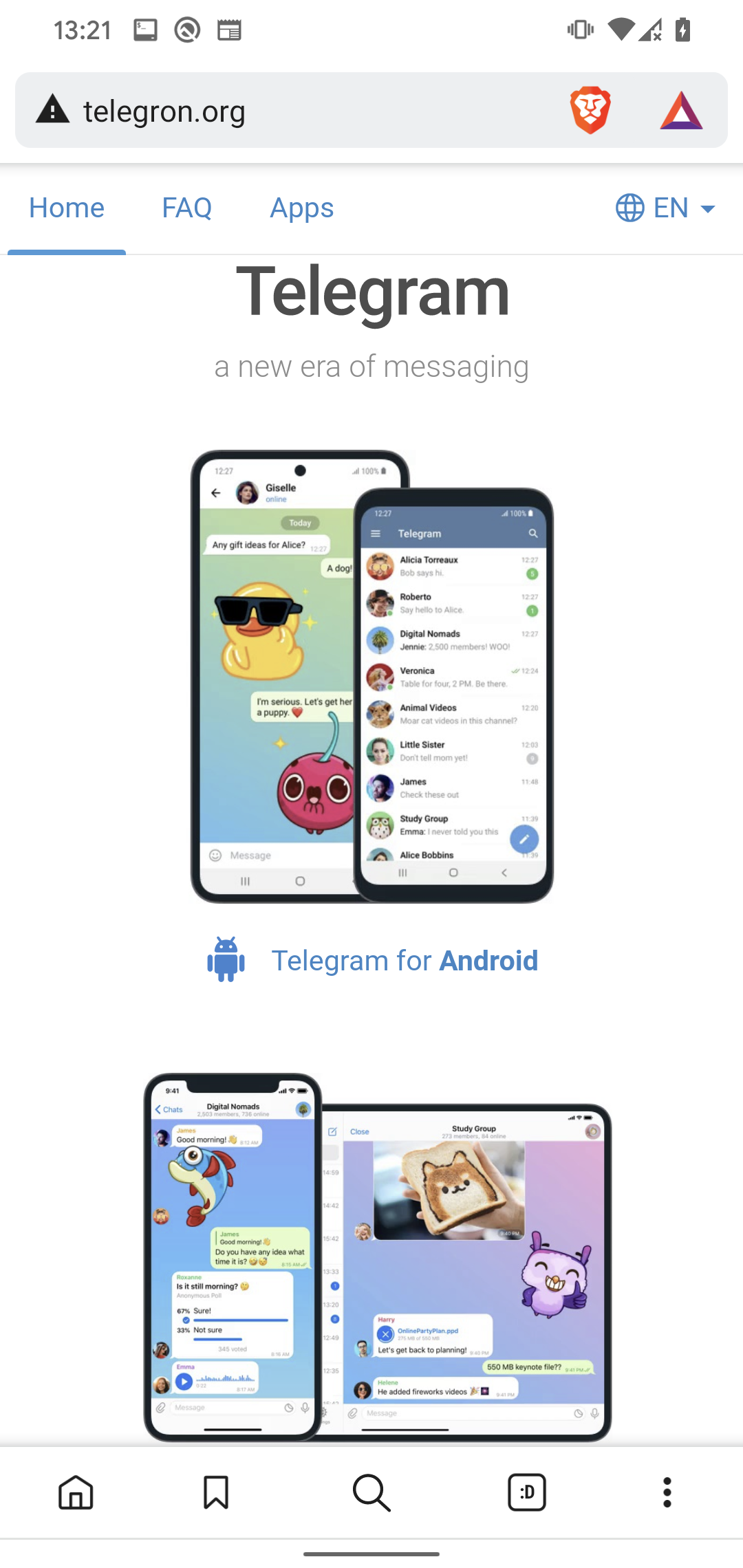
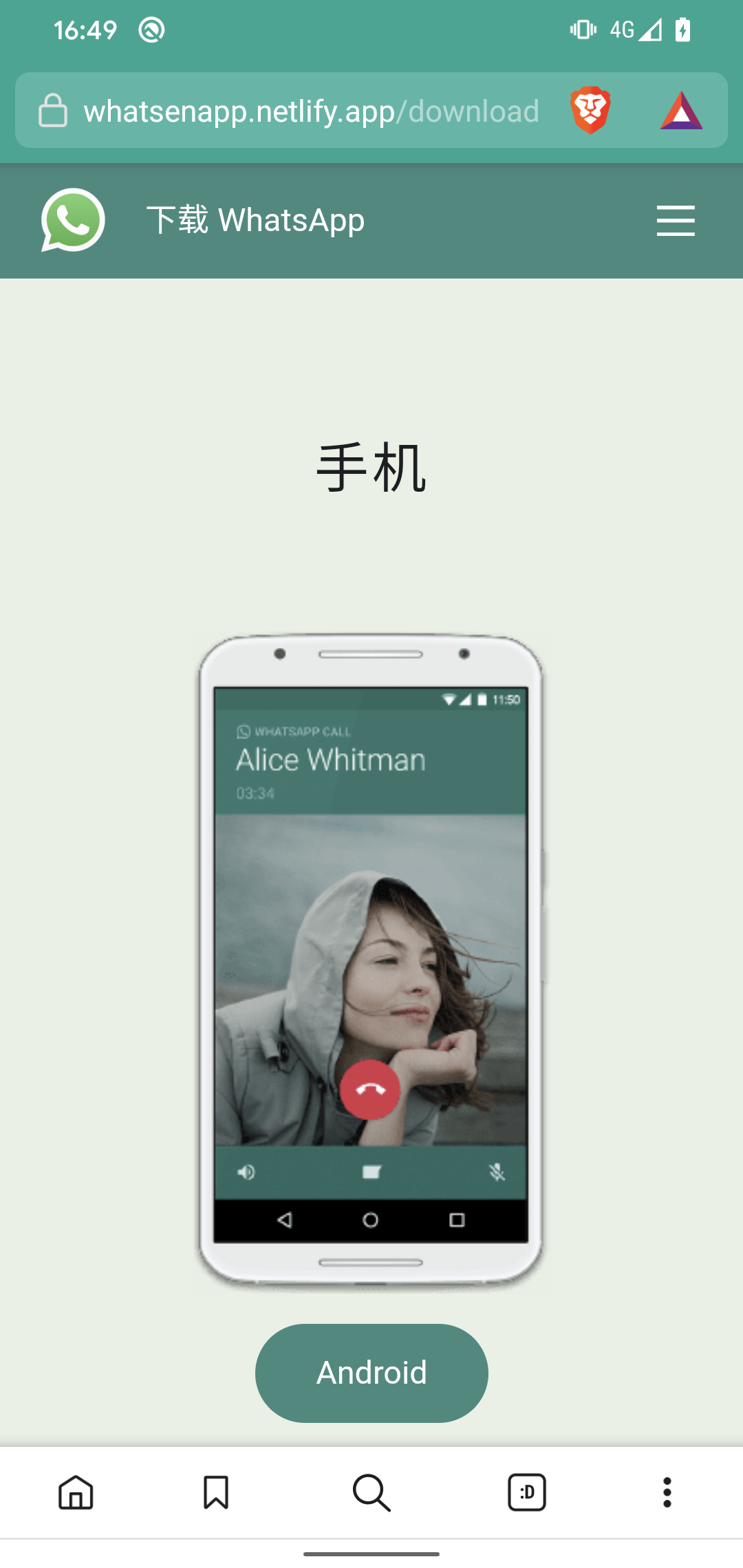
Websites impersonating Telegram and WhatsApp (Source: ESET Research)
- Doublecheck the “official app” claims
In one case documented by ESET research last year, cybercriminals distributed apps for online stores and banks that often didn’t even have an app available on Google Play.
When downloading a mobile app that should be associated with a popular online service, make sure that the service actually offers such an app. If that’s the case, its official website will contains links to the apps in Google Play Store and/or Apple App Store. The number and variety of malicious ChatGPT-themed apps is a handy example.
- Check the app’s name and description
Legitimate app developers typically go to great pains to avoid coming across as unprofessional. This also applies to things as mundane as app descriptions – read through them to see if you can spot poor grammar or inconsistent and incomplete details. These often provide a clue that an app isn’t what it’s claimed to be.
- Check the developer’s pedigree
Tread also carefully when dealing with an app from an unknown app developer with no track record in app development. Don’t be fooled by a name that rings a bell, either – shady app makers may be misusing the name of a legitimate and well-known entity. Doublecheck if the developer has other apps to their name and that the apps are reputable; if in doubt, search for the developer’s name in Google.
READ ALSO: Tracking down the developer of Android adware affecting millions of users
- Look out for excessive app permissions
Last but definitely not least, stay away from apps that require excessive user permissions – that is, the kinds of privileges that they don’t really need to do their job. A flashlight app hardly needs admin rights and access to core device functionality.
7 ways to tell that you downloaded a risky app
Here are a few signs that your newly-installed app could be sketchy:
- The app isn’t doing its job
As an example, back in 2018 ESET researchers analyzed a set of apps that posed as security solutions, but all they did was display unwanted ads and offer pseudo-security. They only mimicked basic security functions with very primitive security checkers that relied on a few trivial hardcoded rules. As a result, they often detected legitimate apps as malicious and created a false sense of security in the victims.
If your new “game” turns out to be a gambling platform, something isn’t right. Check again what it is that you’ve actually downloaded.
- It behaves strangely
Does the app exhibit weird behavior, such as starting up, closing, or failing altogether for no apparent reason? This is one of the most obvious signs that you may have downloaded a dodgy app.
- You incurred unexpected charges
If you’ve spotted unwanted charges on your credit card or phone bill, it could be due to an app you downloaded recently.
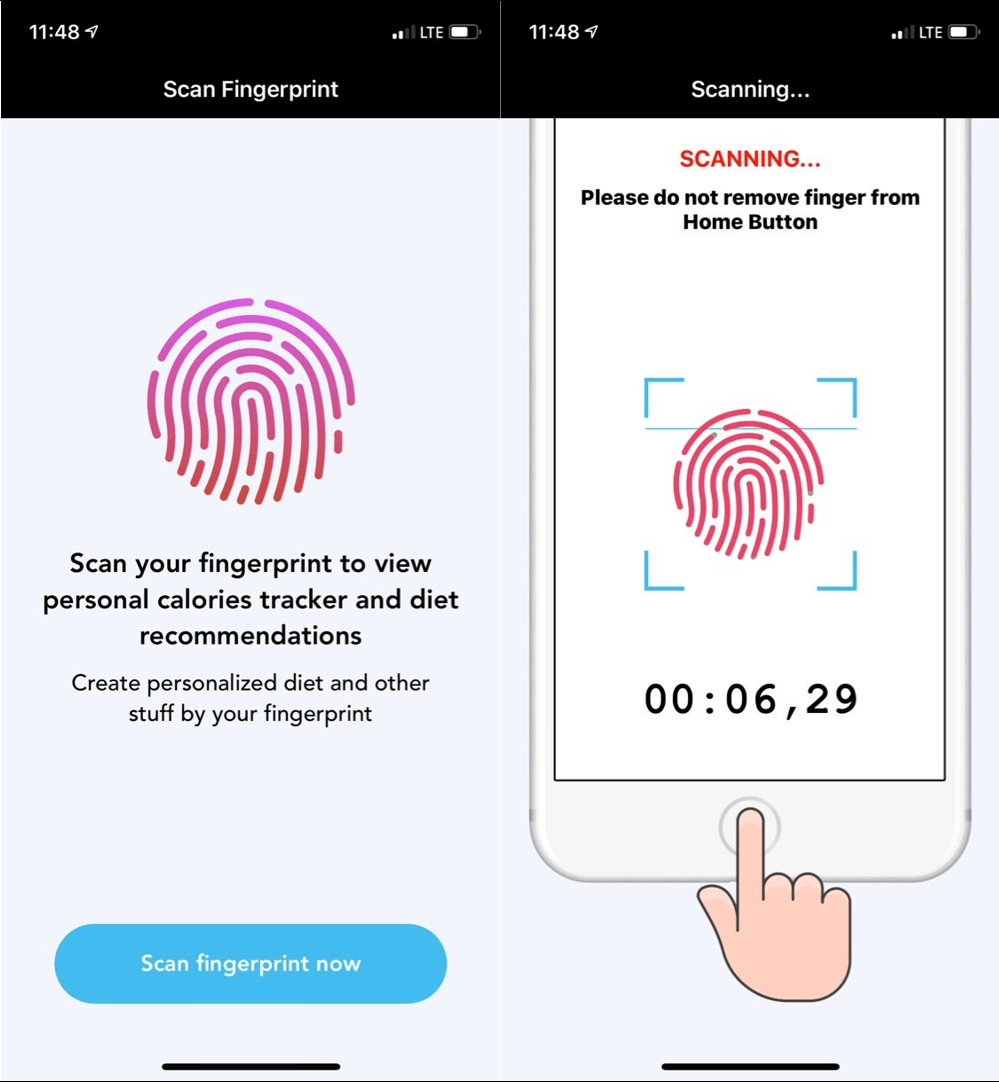
As an example, ESET researchers spotted multiple apps that posed as fitness-tracking tools and abused Apple’s Touch ID feature to steal money from iOS users. After a user launched one of the apps for the first time, it requested a fingerprint scan to “view their personalized calorie tracker and diet recommendations”. If the user had a credit or debit card directly connected to an Apple account, the malware would go on to steal money from the victims via fraudulent in-app payments.
Watch out for scams that involve downloading a peer-to-peer (P2P) payment service and offer fictitious products and services at fire sale prices. Because payments are often instant and cannot be canceled, you may lose money by paying for something you will never receive.
Figure 4. Sketchy iOS apps asking users to scan their fingers for fitness tracking before showing dodgy payments
- Strange messages and calls
Another sign of trouble involves malware spamming out messages from your phone to your contacts (like FluBot does). In other cases, your call or text message history may contain unknown entries as malware attempts to make unauthorized calls or send messages to premium-rate numbers.
- Battery drain
Does your device battery get drained far faster than usual? It may be due to background activity that consumes the device’s resources and could ultimately indicate that your device has been compromised by malware.
- Spikes in data usage
If you experience a major and sudden surge in your internet data usage without any change in your browsing or phone usage habits, it could also be because of an app’s activity in the background.
- Random ad pop-ups and unknown apps
A malicious app may go on to install additional apps in the background and without your authorization. The same goes for pesky adware displaying unwanted ads on your device. If you spot any of this, chances are high you need to act fast.
What to do next?
After discovering what you suspect is a sketchy app, remove it or, even better, download reputable mobile security software that will scan your device and remove the app for you.
If you go the “manual” route instead, reset your phone to factory settings (prior to that, make sure you have your data backed up). Alternatively, you may sometimes have to boot up your device in Safe Mode and then remove the app. The video by ESET malware researcher Lukas Stefanko shows you how:
Also, do other potential victims a favor and report the app to the relevant app store from which you downloaded the app. You can also try to claim a refund.
Going forward, if you use apps from the Google Play Store, make sure to enable the Google Play Protect scanning on your device. You can also check the apps you’ve downloaded from outside of the Google Play Store. To do so, turn on “Improve harmful app detection”, which will send unknown apps to Google automatically.
What if you’re an iOS user? Contrary to what many people may think, downloading a dodgy app on iOS, even from Apple App Store, isn’t unheard of. For more on what to do if a bad app(le) slipped through the iOS safety net, head over to our recent deep dive into the topic:
Can your iPhone be hacked? What to know about iOS security
7 tips for staying safe
Finally, a few quick tips for staying safe while using your mobile device:
- Stick to Google Play and Apple App Store; i.e., avoid putting yourself at risk by installing apps from third-party stores.
- Don’t mindlessly click on links sent via social media messages or emails.
- Use two-factor authentication (2FA) on all your online accounts that offer it, especially on those that contain your valuable data.
- Keep your phone’s operating system and apps up-to-date.
- Stick to apps whose developers continue to improve their products and fix security vulnerabilities and performance bugs.
- Secure your device’s screen with a passcode sufficient length and complexity or a solid biometric feature such as a fingerprint – or, ideally, a combination of both!
- Use mobile security software.