Today we are happy to announce our annual report called Windows exploitation in 2015. Readers who tracked our previous reports Windows exploitation in 2013 and Windows exploitation in 2014 may notice that in each new version of the report we try to highlight new security features introduced in Windows, web browsers and EMET. Along with this information, both previous reports contain information about vulnerabilities that have been fixed in various important Windows components, the .NET Framework and Microsoft Office. Our latest report is no exception.
Our main goal in writing these reports is to notify our customers, as well as other users, about the importance of installing updates to fix various unpatched (0day) vulnerabilities. We also provided information about ESET's detections of in-the-wild exploits of these vulnerabilities. Such exploits are used by attackers to implement notorious drive-by download attacks.
The two previous reports we mentioned above and another research paper called Exploit Protection for Microsoft Windows give a comprehensive overview of various aspects of defensive and offensive technologies in Microsoft Windows, Internet Explorer, Google Chrome, and EMET. This information is useful for end-users because it enables them to see, from a technical point of view, how attackers can achieve their goals and what methods have been introduced in Windows to help them to stay safe from such attacks. Below we list some of that content:
- Statistics about vulnerabilities that have been fixed in Microsoft Windows, .NET Framework, and Office, with information about the most common exploitation vectors.
- Description of so-called drive-by download and Local Privilege Escalation (LPE) attacks.
- Information about detection by ESET security products of 0days exploited by attackers in implementing drive-by and LPE attacks in malware or other vectors.
- Comprehensive information about security features in Internet Explorer and how the user can use those features to protect himself.
- Explanation of the infamous use-after-free (UAF) attacks.
- Detailed information on how to mitigate drive-by attacks with EMET.
- Information about the Google Chrome sandbox
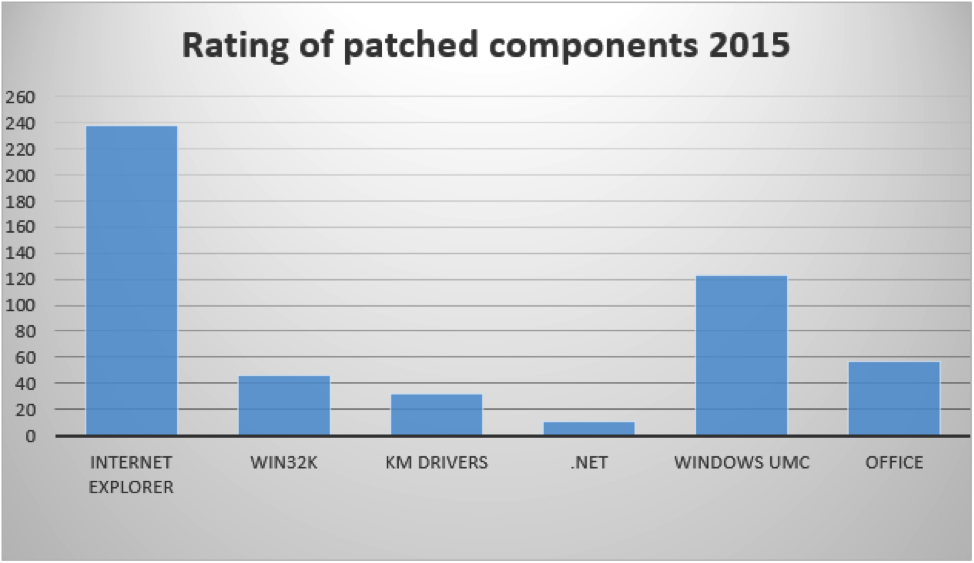
The new report includes the following information:
- Hacking Team exploits.
- New security features in Google Chrome.
- New security features in Microsoft EMET tool and Edge web browser.
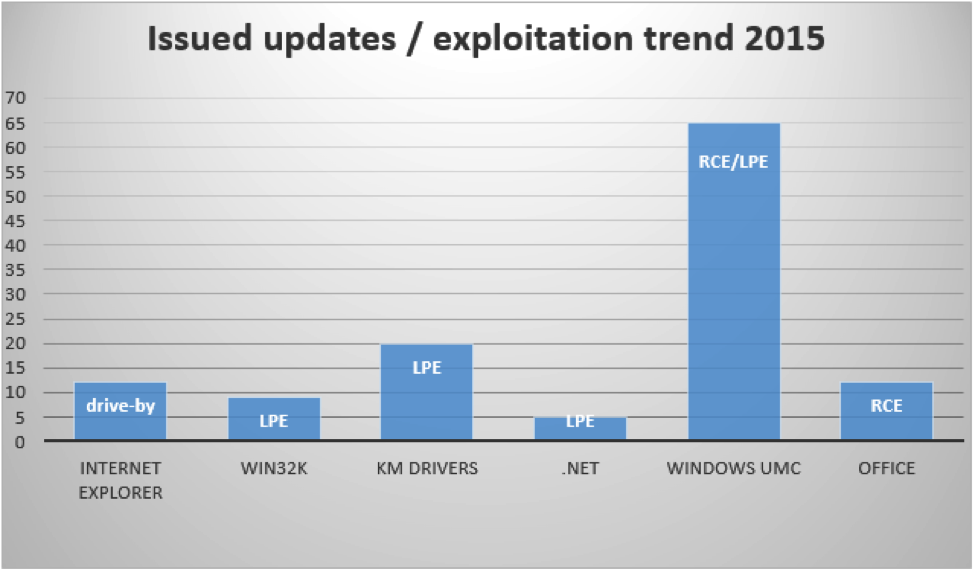
We didn't want to repeat information already provided in previous reports, and so in the new version of the report we concentrated on various security improvements in the listed products. The section about Hacking Team summarizes detections of our AV products for exploits used by this cybergroup, as well as for their backdoor DaVinci (Morcut). This was developed for almost all existing platforms, including Windows, Android, Linux, OS X, iOS.
Artem Baranov, malware researcher, ESET Russia




