In the past year, Microsoft (MS) has fixed a large number of vulnerabilities for Windows and its components, as well as for Office. Some of these vulnerabilities were used by attackers to deliver malicious code before a patch was available for the targeted software, or in other words, what we call a 0-day attack. Most of these attacks were focused on flaws in Internet Explorer.
We can say that the year 2013 was notable for the appearance of 0-day vulnerabilities that were primarily used in targeted attacks. In this case, criminal hackers worked on developing exploits, only not for random propagation of malicious code, but rather for use in attacks on specific users while pursuing a certain set of goals, some of which may be known only to the attackers.
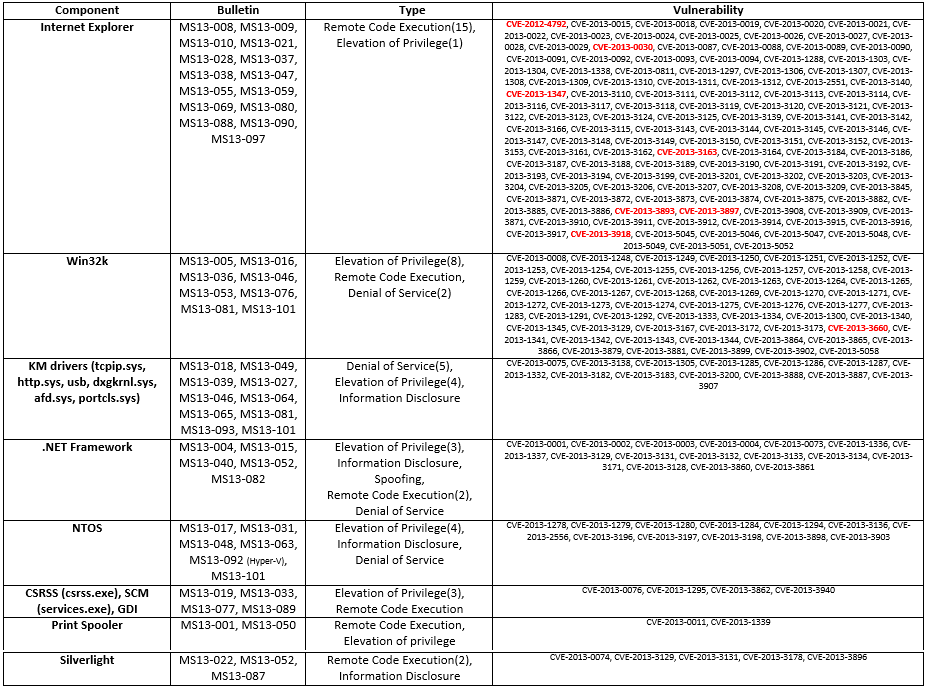
In the table below, you will find statistics on the vulnerabilities that Microsoft fixed within the past year.
Vulnerabilities shown in red were exploited in the wild; that is, they were used in actual attacks on end users before a patch became available.
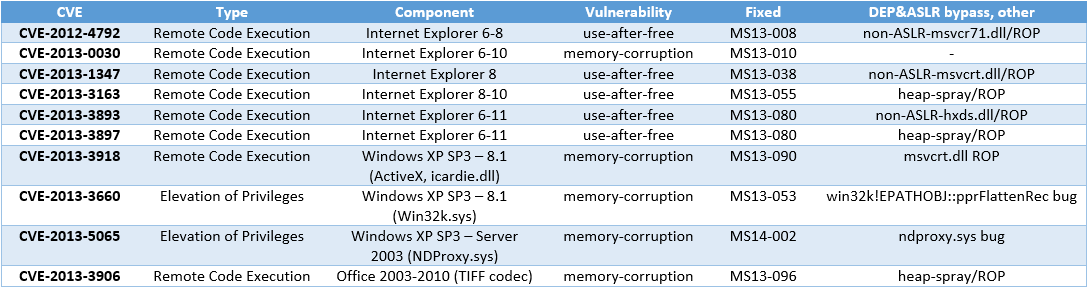
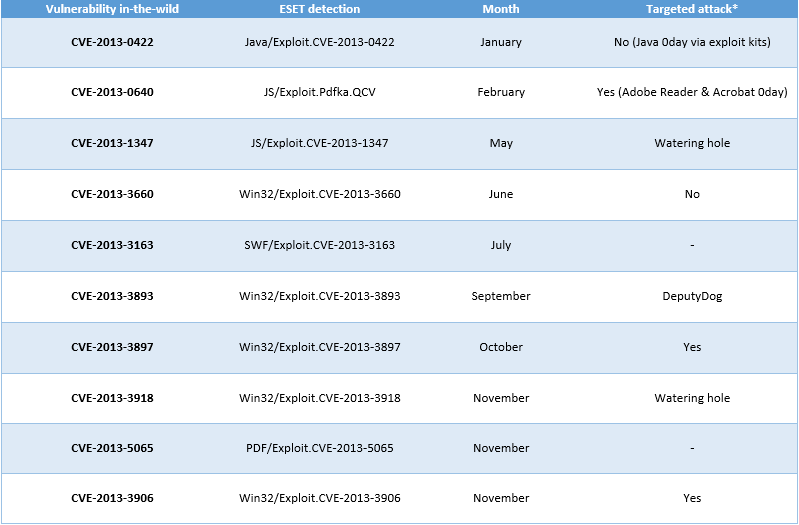
The following table gives more information about the vulnerabilities, for which there were in-the-wild exploits in the past year (before the appropriate patch appeared).
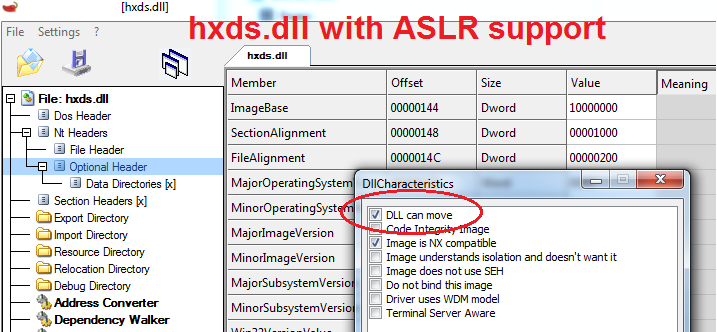
As we can see, the attackers were able to use some of Windows system executable files that were compiled without Address Space Layout Randomization (ASLR) support for the construction of stable Return-Oriented Programming (ROP) gadgets, and were thus able to bypass ASLR. One such example is the Microsoft Office 2007-2010 library hxds.dll, which was compiled without ASLR. As part of the December Patch Tuesday, the company closed this flaw (called Security Feature Bypass) with MS13-106, providing Windows users who work with this Office version with the appropriate level of protection.
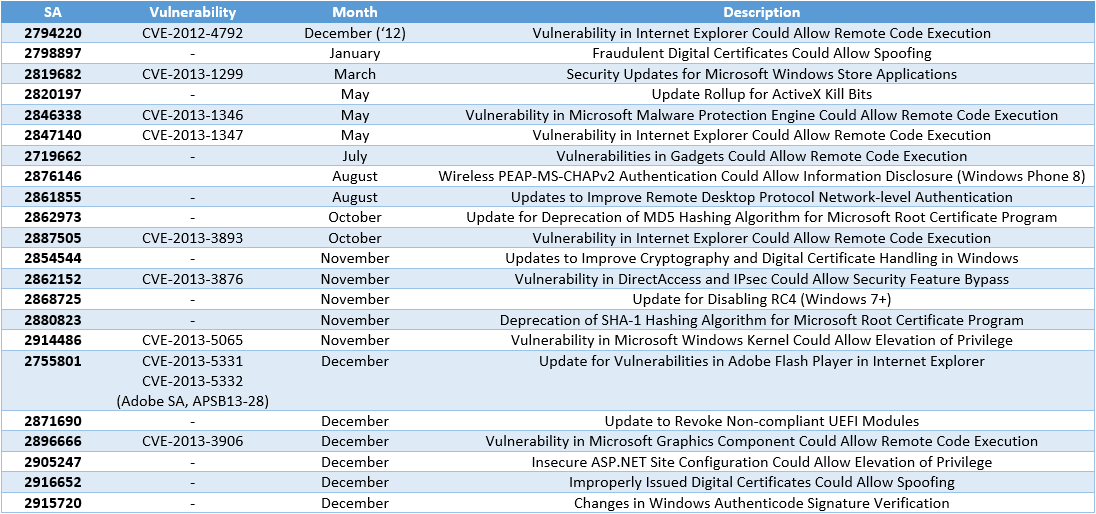
The next list contains information about security advisories (SA) issued in the past year.
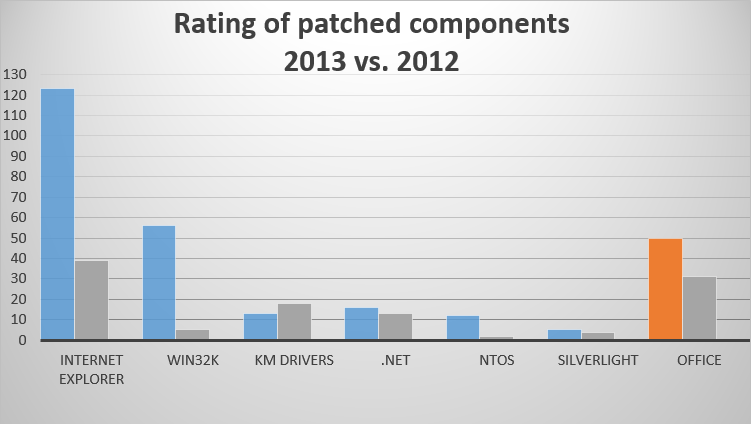
The rating comparison below shows the Windows components in 2013 that were most frequently patched. Note that the currently supported versions of Microsoft Windows ranged from Windows XP with Service Pack 3 to Windows 8.1 on desktops and from Windows Server 2003 to Windows Server 2012 R2 for servers.
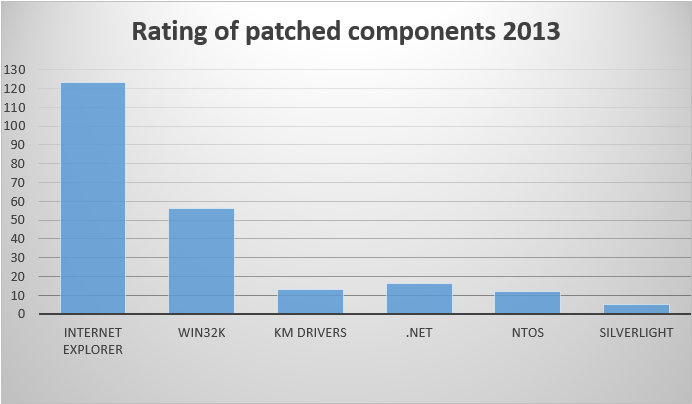
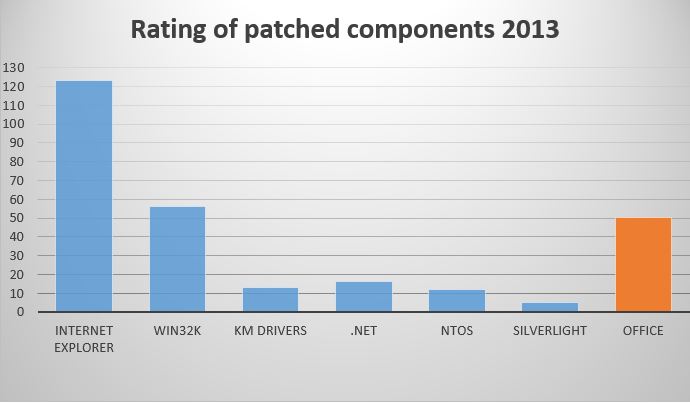
The same comparison ratings including Office (2003 - 2013 for Windows) are shown below.
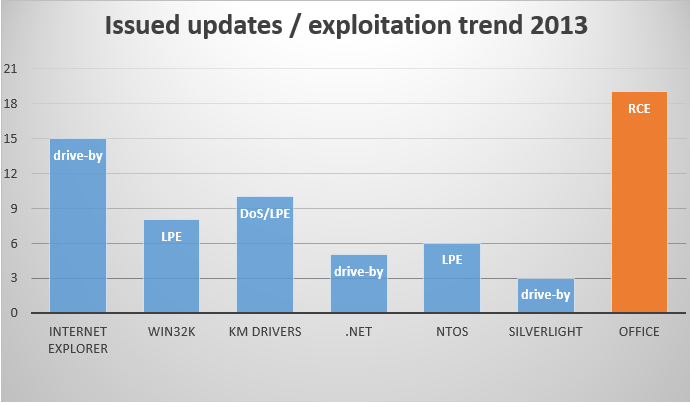
The next graph compares updates and the exploits they mostly addressed.
Drive-by download – this is the main method for delivering hidden code via redirection to exploit kits.
Local Privilege Escalation (LPE, Elevation of Privilege) – this is a way to gain maximum privileges in Windows, usually associated with the launch of kernel-mode code to bypass user-mode restrictions (aka user-mode restrictions escape).
Remote Code Execution (RCE) – attackers use this method, for example, in drive-bys, but in many cases it can be activated not only via webpage but via e-mail, instant messaging, and so on.
As we can see from the chart above (Issued updates / exploitation trend) such products as the browser Internet Explorer, .NET Framework and the Silverlight plugin are used by attackers for remote code execution, and indeed in most cases this done via the browser. Attackers use a special crafted webpage with malicious content that exploited a vulnerability in the aforementioned software. Eventually, this page is used for malware delivery. The user can select a special option for Internet Explorer that mitigates exploits. This option called Enhanced Protection Mode (EPM) or sandbox mode.
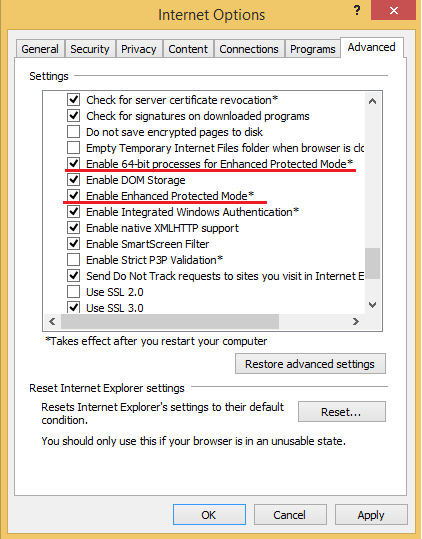
Internet Explorer 11 sandbox options for use on Windows 8 and later (64-bit editions only) are shown below.
The first option, called Enhanced Protected Mode (EPM), turns on AppContainer restriction mode for browser tab processes. The second option, called Enable 64-bit processes for Enhanced Protection Mode, turns on the use of native 64-bit processes for browser tabs. By default, on 64-bit versions of Windows 8 and later, Internet Explorer runs browser tab processes as 32-bit processes, making it more vulnerable to heap spraying. Spraying is used by attackers to bypass ASLR mitigation practice. The 64-bit virtual address space is much bigger than 32-bit address space and ASLR is more secure in the context of such a process.
Vulnerabilities in applications included in the Microsoft Office software package can also be used by attackers to install malicious code remotely. Looking at the updates issued for Office in the last year, we can see that most of them were aimed at eliminating vulnerabilities allowing Remote Code Execution. In such a scenario, attackers will create a specially crafted Office file, for example a .DOCX file for Microsoft Word, and send it in a phishing email to the victim. The message must be capable of convincing the user that he wants to open a malicious attachment. After opening the file in a vulnerable version of Office, the user’s PC will be infected with malicious software.
Note that the newest versions of Microsoft Word 2013 and Outlook 2013 contain special security features to mitigate exploitation. These features forbid the application to perform potentially unsafe functions. For example, Outlook starts the process of Word with low Integrity Level and with reduced privileges, restricting the capability of shellcode to execute system functions.
Operating system components that run in kernel mode (KM), Windows GUI-subsystem driver win32k.sys, system drivers (KM drivers), and ntoskrnl (NTOS, OS kernel), are used by attackers to raise their system privilege levels in order to execute code in kernel mode that bypasses Windows restrictions (user-mode restrictions escape). The win32k.sys driver was the most patched of these components in the past year. The colored bar represents 2013 patching levels, the adjacent grey bar represents 2012 levels.
As we can see, in 2013 Microsoft fixed many more vulnerabilities than it did in 2012. This trend is most obvious for the Windows GUI subsystem driver – win32k.sys – and the Internet Explorer browser. Note that in October the company released a new version of Windows – Windows 8.1 – and of the browser Internet Explorer 11. Internet Explorer 11 can also be installed on Windows 7.
The table below shows vulnerabilities (0-days at the time of exploitation) that attackers used for delivering malicious code. The past year can rightly be called the year of targeted attacks and watering hole attacks. For many of them the attackers specially researched vulnerabilities and used them exclusively for attacks on a specific region or a specific company. In particular, watering hole attacks were used to compromise websites that were actively visited by alleged victims in various regions of the world. We believe that in 2014 this trend will continue.
The asterisked (*) column denotes the month when the vulnerability was first exploited in targeted attack; a dash in that column signifies that no data are available.
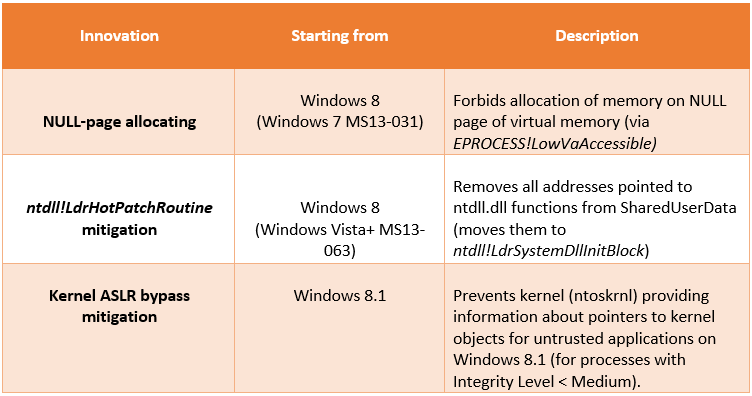
The past year demonstrated that Microsoft paid attention to protective technologies for counteracting exploits. Three major innovations were aimed at the protection of null page (memory allocation), removing pointers on ntdll functions from SharedUserData (ASLR bypass mitigation) and the prohibition of providing information about pointers to kernel objects for untrusted applications on Windows 8.1 (KASLR bypass mitigation).
Address 0 memory allocation (using ntdll!ZwAllocateVirtualMemory) makes the attackers life much easier, not least if they are interested in the privileges escalation. After attackers have allocated this memory region, they need to find a vulnerable driver that can execute code from this address via a bug.
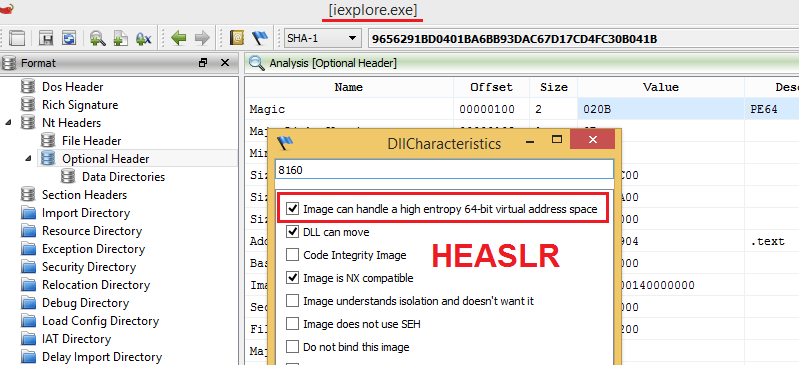
Another interesting improvement on Windows 8 is that all Microsoft-compiled files contain support of enhanced or stronger ASLR (High Entropy ASLR, HEASLR). HEASLR is a new feature that first appeared in Windows 8. It improves on the usual ASLR approach by using stronger address entropy for such memory operations as virtual memory allocation, image loading, stack allocation, and so on.
All Microsoft-compiled system files on Windows 8+ have support of HEASLR so as to enhance protection against potential exploitation (/HIGHENTROPYVA linker flag).
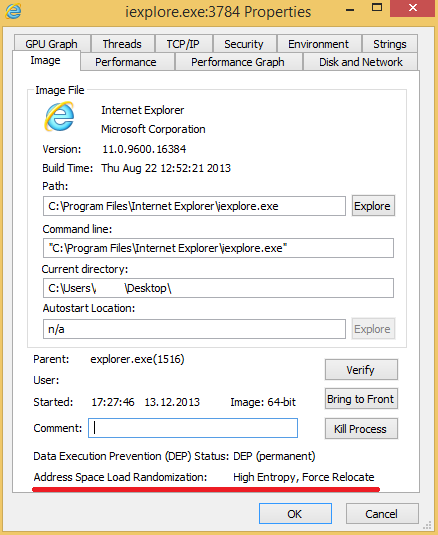
You can check active HEASLR using ProcExp tool.
Conclusion
As we can see, in the past year, Microsoft has fixed many vulnerabilities: most of them are related to unauthorized/remote code execution and allow attackers to compromise vulnerable systems. In addition, the company has introduced useful security features, which make the exploitation process more complicated. For these reasons, a lot of exploits that use such exploitation methods will no longer work on an up-to-date version of the Windows operating system (OS). This makes Windows 8 & 8.1 a good choice, for example, because Windows 8.* contains integral security features that are only available for other Microsoft OS versions if the user is able to install corresponding security update. We recommend that our customers install security updates as soon as possible after their release to help keep themselves safe.
Artem Baranov, Malware Researcher, ESET Russia