When ransomware attacks a healthcare establishment, it can have a devastating effect. This was witnessed in 2017, when WannaCryptor.D (aka WannaCry) hit multiple sites across the United Kingdom’s National Health Service, limiting their ability to provide services and causing nearly 20,000 appointments to be cancelled.
The COVID-19 pandemic is stretching the resources of health services to their maximum, across the globe. This includes not only the courageous frontline healthcare professionals but all the support teams that create the environment for them to work in, such as IT security teams. Those teams may be pleased, and amazed, to hear that one of their adversaries – the team behind Maze ransomware – has decided to stop activities that target medical organizations, at least until the current situation is stabilized.
A “press release” dated March 18 states that the Maze team is also willing to offer exclusive discounts to their partners due to economic conditions. I think their use of the word “partner” actually refers to victims, which is like arsonists calling the owners of the building they torched their “partners”.
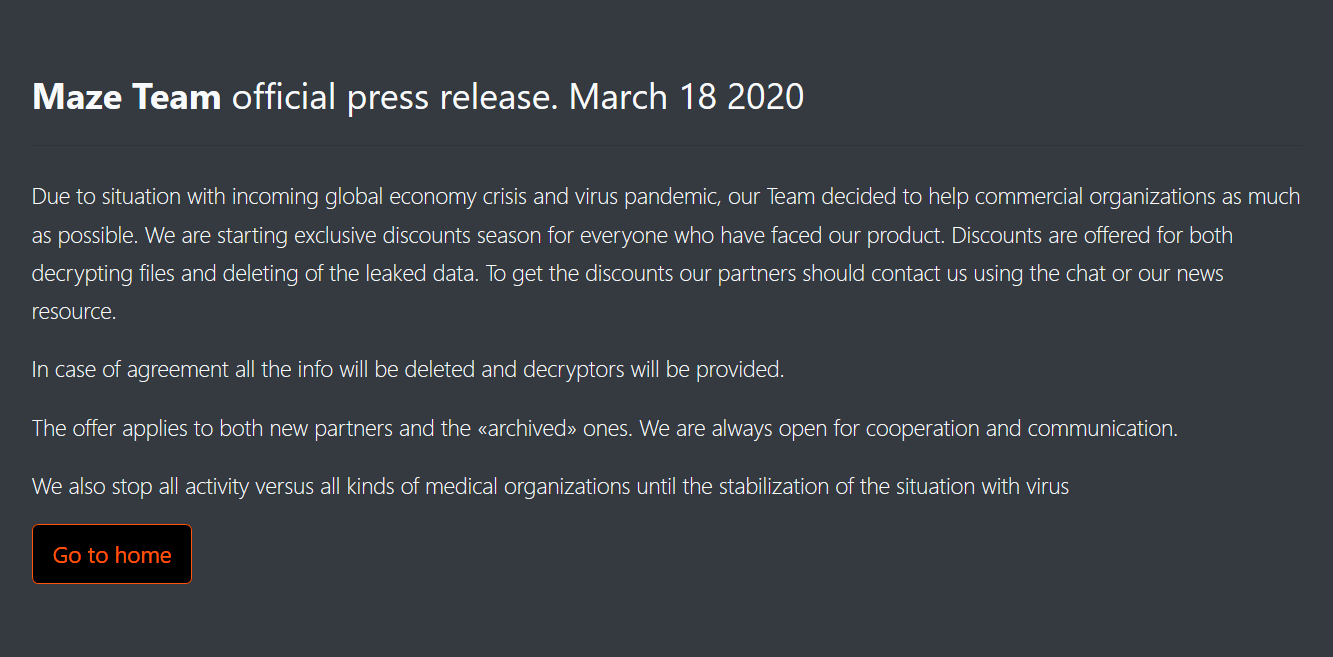
Maze Team “press release” – hat tip to malware researcher going by the Twitter handle CryptoInsane
The group has been responsible for a number of recent attacks including against both the City of Pensacola and manufacturing company Southwire. In both instances the victims refused to pay and the Maze operators released data that had been stolen.
Maze Team is also attributed with publishing medical data from a number of healthcare organizations that refused to pay, the largest organization being New Jersey’s Medical Diagnostics Laboratories (MD Lab). About 9.5 GB of MD Lab’s data was published by the Maze operators in an attempt to force negotiations for payment.
According to an article on CyberScoop, the FBI issued a flash alert in December 2019 about the dangers of Maze ransomware. The alert details how the threat actors behind Maze use several different methods to breach a network, including fake cryptocurrency sites and malspam campaigns to impersonate government agencies and security vendors.
These are cybercriminals with a history of disruption and destruction; isn’t it thoughtful of them, though, in this time of crisis to stop attacking medical organizations? I must invite them over for tea to say thank you.
Apologies; that is my British sarcasm getting the better of me!
Any attack on a healthcare institution at any time has the potential to be responsible for a degradation in patient care, the consequences of which could be fatal. Offering discounts and the willingness to stop attacks in the current situation should not distract from the fact these are cybercriminals who have a reputation and history of attacking healthcare systems with complete disregard for patient care.
And they need to be caught and brought to justice!
ESET has been here for you for over 30 years. We want to assure you that we will be here in order to protect your online activities during these uncertain times, too.
Protect yourself from threats to your security online with an extended trial of our award-winning software.
Try our extended 90-day trial for free.





